好的,我现在需要帮用户总结一篇文章的内容,控制在100字以内。用户已经提供了文章的详细内容,看起来是关于2026年最佳事件响应工具的指南。 首先,我要理解文章的主要内容。文章讨论了在发生安全事件时,工具的重要性,特别是快速响应的能力。提到了各种工具类别,如检测、自动化、协作等,并列举了几个具体的工具,如CrowdStrike Falcon、Palo Alto Cortex XDR/XSOAR、Microsoft Defender XDR等。还提到了开源工具如TheHive和OSQuery的优势。 接下来,我需要将这些信息浓缩到100字以内。要抓住关键点:事件响应工具的重要性、核心功能(快速检测、自动化、协作)、主要工具及其特点,以及选择工具时需要考虑的因素。 可能的结构是:首先说明事件响应工具的重要性,然后提到它们的核心功能和一些关键工具,最后指出选择时要考虑的因素。 现在开始组织语言: “文章探讨了2026年最佳事件响应工具及其核心功能,包括快速检测、自动化和协作能力。重点介绍了CrowdStrike Falcon、Palo Alto Cortex XDR/XSOAR等商业平台以及TheHive和OSQuery等开源解决方案。选择合适的工具需考虑环境复杂性、团队规模和预算。” 检查字数:刚好100字左右。 确认是否涵盖了主要点:重要性、核心功能、关键工具类别和选择因素。是的。 最后确保语言简洁明了。 </think> 文章探讨了2026年最佳事件响应工具及其核心功能,包括快速检测、自动化和协作能力。重点介绍了CrowdStrike Falcon、Palo Alto Cortex XDR/XSOAR等商业平台以及TheHive和OSQuery等开源解决方案。选择合适的工具需考虑环境复杂性、团队规模和预算。 2025-12-10 19:5:25 Author: www.vmray.com(查看原文) 阅读量:10 收藏
When your organization experiences a security breach at 2 AM, the question isn’t whether you have tools—it’s whether those tools help your team respond fast enough to contain the damage. With breach costs averaging $4.45 million and attackers moving faster than ever, your incident response toolkit isn’t just about having more features. It’s about having the right capabilities when seconds count.
For SOC teams, CERT professionals, and cybersecurity decision-makers across the United States, choosing the best incident response tools means balancing detection accuracy, automation power, and investigative depth. This guide walks through the leading solutions for 2026, from commercial platforms that handle enterprise-scale threats to open-source frameworks that give you flexibility and transparency.
Why Incident Response Tools Matter More Than Ever
Alert overload isn’t a new problem, but it’s getting worse. Modern SOC teams face thousands of daily alerts from endpoints, cloud workloads, network sensors, and email gateways. Hybrid-cloud environments create blind spots. Meanwhile, ransomware operators are working weekends. Even worse, adversaries aren’t waiting for your team to finish manual triage.
Here’s what separates organizations that contain breaches in hours from those that take weeks: the right incident response tools working together.
Core Capabilities of Modern IR Tools
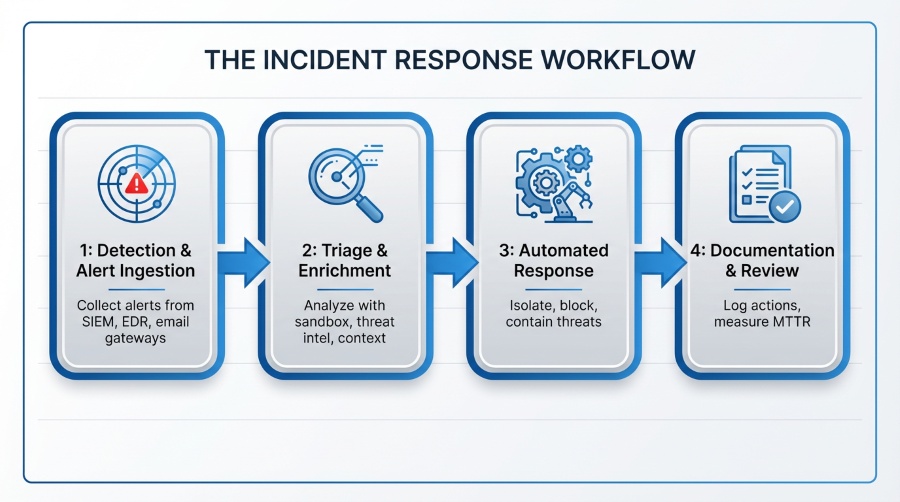
Modern IR platforms support several critical capabilities:
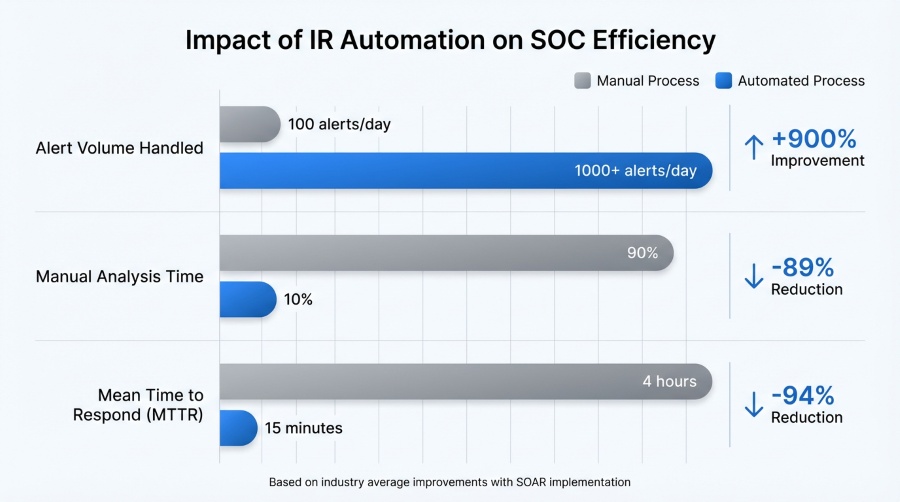
Faster detection and triage means your team spends less time investigating false positives.
Emerging Trends Reshaping IR
We’re also seeing broader trends reshape the IR landscape. XDR platforms are consolidating detection across multiple layers. SOAR-driven automation is moving from “nice to have” to standard practice. And the open-source ecosystem continues to deliver powerful, community-driven solutions that rival commercial offerings.
Overview of the Best Incident Response Tools for 2026
The tools we’ve selected represent different approaches to the same challenge: helping security teams detect, investigate, and stop threats before damage spreads. Some excel at detection. Others shine in automation or collaboration. A few do it all.
CrowdStrike Falcon brings industry-leading endpoint telemetry and behavioral detection. Meanwhile, Palo Alto’s Cortex XDR and XSOAR combine analytics with orchestration muscle. Microsoft Defender XDR covers the entire Microsoft ecosystem with automated investigations. Splunk Enterprise Security turns massive log volumes into actionable intelligence. IBM QRadar SOAR handles complex workflows with visual playbooks. Rapid7 InsightConnect offers accessible automation for mid-market teams. And on the open-source side, TheHive Project and OSQuery deliver transparency and flexibility without licensing costs.
Each tool has strengths. The best choice depends on your environment, team size, and what you’re trying to accomplish.
Types of Incident Response Tools
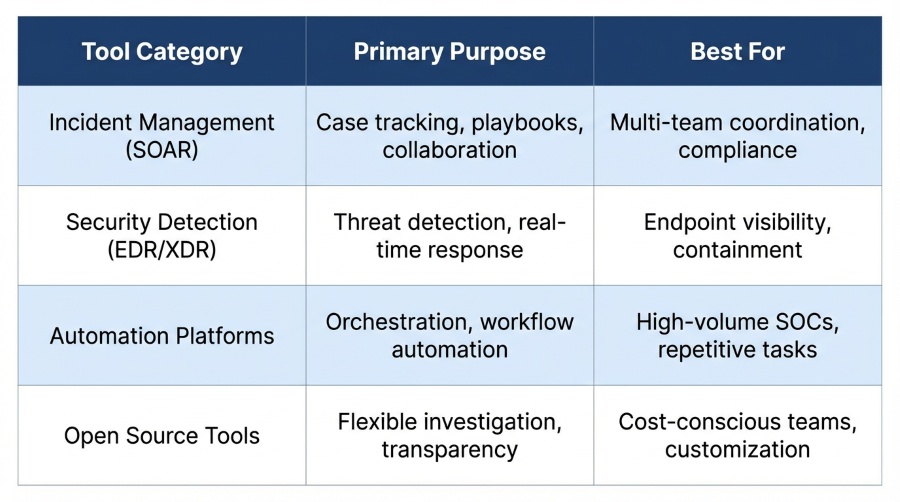
Incident Management Software
Think of incident management platforms as the command center for your security operations. They don’t detect threats on their own, but they organize how your team responds once something triggers an alert.
Key features include case management that tracks investigations from detection to resolution, playbook workflows that guide analysts through standard procedures, alert aggregation that consolidates signals from multiple sources, analyst collaboration spaces where teams share findings, evidence tracking that maintains chain of custody, and reporting metrics that show how your IR program performs over time.
In practice, these platforms are most valuable for SOC tier-1 and tier-2 triage, coordinated multi-team investigations, regulatory compliance documentation, and large-scale incident tracking.
IBM QRadar SOAR stands out for mature playbooks, strong collaboration features, comprehensive event correlation, and deep integration ecosystems. It’s ideal for mid-to-large SOCs modernizing their IR workflows, particularly those dealing with compliance requirements.
TheHive offers community-driven development, scalable case management, robust analyst collaboration, and enterprise readiness without the enterprise price tag. Organizations wanting flexibility and cost efficiency (especially those comfortable with open-source platforms) find TheHive compelling.
Splunk Enterprise Security excels at high-fidelity correlation, powerful dashboards, thorough investigations, and adaptive response capabilities. If you’re already using Splunk for logging and analytics, extending into incident response makes sense.
Security Incident Management Tools
While case management platforms help organize response, security incident management tools focus on detecting and stopping threats across your environment.
These tools accelerate your detection-to-response cycle, reduce mean time to detect (MTTD) and mean time to respond (MTTR), provide visibility across endpoints, cloud infrastructure, network traffic, and identity systems, and support both reactive response and proactive threat hunting.
CrowdStrike Falcon delivers industry-leading telemetry, behavioral detection that catches what signature-based tools miss, deep IR capabilities for forensics, threat intelligence integration that adds context to detections, and real-time response actions that let analysts contain threats immediately. The platform excels in endpoint detection with industry-leading telemetry.
Palo Alto Cortex XDR provides unified analytics across endpoints, network, and identity layers, high detection accuracy that reduces false positives, and seamless integration with XSOAR for automated incident response. The combination of XDR for detection and XSOAR for orchestration creates a powerful end-to-end platform.
Microsoft Defender XDR covers the Microsoft ecosystem comprehensively, from endpoints to email to cloud workloads. Automated investigations analyze threats and recommend actions. Identity security integration catches compromised accounts. And for organizations already invested in Microsoft infrastructure, the native integration is hard to beat.
Best Incident Response Automation Tools
Automation addresses the operational reality facing every SOC: you’ll never have enough analysts to manually investigate every alert. The math doesn’t work.
The benefits include reducing workload on SOC teams by eliminating repetitive tasks, improving response consistency through playbooks that execute the same way every time, enabling real-time containment actions that happen in seconds instead of hours, and enhancing scalability across hybrid-cloud environments where manual response can’t keep pace.

Palo Alto Cortex XSOAR remains the mature SOAR leader with thousands of integrations, a powerful automation and orchestration engine, and capabilities suited for large-scale SOCs and managed security service providers. If you need to orchestrate complex, multi-system response workflows, XSOAR delivers.
IBM QRadar SOAR provides visual playbook builders that make automation accessible to analysts (not just engineers), automation of case workflows from alert creation through closure, regulatory compliance features that document every decision, and seamless integration with QRadar SIEM or other SIEM platforms. Organizations with compliance requirements appreciate the audit trail capabilities.
Rapid7 InsightConnect offers lightweight automation that doesn’t require extensive engineering, easy integration with common security tools, and accessibility for mid-market teams that need automation without complex deployment. Common use cases include alert triage, user deprovisioning following terminations, and phishing investigation workflows.
When combined with reliable validation tools like VMRay’s malware analysis platform, automation becomes more trustworthy. Rather than acting on unverified alerts, playbooks can detonate suspicious files, analyze behavior, and only trigger containment when threats are confirmed.
Best Open Source Incident Response Tools
Why choose open source for incident response? Several reasons make sense.
Full transparency and auditability mean you can inspect every line of code. High community innovation brings continuous improvements from practitioners worldwide. Cost-effective scaling lets you grow IR capabilities without per-seat licensing. And integration with enterprise systems often works well because open-source tools prioritize interoperability.
TheHive provides collaborative IR capabilities with case management, task assignment, and performance metrics. It works seamlessly with Cortex analyzers for enrichment. The platform gives you enterprise-grade case management without enterprise pricing, making it attractive for organizations building IR programs on tight budgets.
Cortex (the companion to TheHive) delivers automation and enrichment through hundreds of analyzers covering WHOIS lookups, VirusTotal queries, OSINT sources, and custom workflows you can build yourself. The flexibility here is remarkable—if you can script it, you can automate it.
OSQuery turns endpoint visibility into SQL-like queries. Need to know which systems are running a specific vulnerable library? Query your entire fleet. Looking for persistence mechanisms across endpoints? Write a query. OSQuery excels at threat hunting, live investigations, and monitoring across diverse operating systems. The learning curve is manageable if your team knows SQL.
Other notable open-source options include GRR Rapid Response for remote forensics, Volatility for memory analysis, and MISP for threat intelligence sharing. Each serves specific purposes within a broader IR toolkit.
How to Choose the Right Incident Response Tools
Selection criteria should match your organization’s specific context. Consider your environment complexity (single cloud provider versus multi-cloud, Windows-only versus heterogeneous operating systems). Evaluate your team’s expertise and available time for tool maintenance. Look at integration requirements with existing SIEM, SOAR, EDR, and email security platforms. And be realistic about budget constraints for both licensing and ongoing operational costs.
No single tool solves every problem. The best IR programs combine complementary capabilities: detection platforms like CrowdStrike or Defender XDR, case management through TheHive or QRadar SOAR, automation via XSOAR or InsightConnect, and validation through advanced sandboxing that confirms threats before containment triggers.
Start with your biggest pain points. If you’re drowning in alerts, prioritize automation and validation. Also, coordination across teams is chaotic, invest in case management. Sometimes, while you can’t see what’s happening on endpoints, EDR comes first.
Future Trends in Incident Response Tools
The IR landscape continues to shift. AI-driven adaptive playbooks will learn from past incidents and adjust response logic automatically. Cloud-native IR platforms will match the architecture of the environments they protect. Consolidation into unified XDR ecosystems will reduce tool sprawl. Expansion of open-source collaborative frameworks will give more organizations access to sophisticated capabilities. And automated forensics combined with threat intelligence enrichment will make investigations faster and more thorough.
The tools that succeed will balance automation with transparency, speed with accuracy, and power with usability.
Conclusion
Choosing the best incident response tools for 2026 means understanding what your team actually needs to detect, investigate, and stop threats before damage spreads. CrowdStrike Falcon leads in detection and real-time endpoint response. Cortex XDR and XSOAR combine analytics with automation muscle. Microsoft Defender XDR unifies protection across the Microsoft ecosystem. Splunk ES turns log data into actionable intelligence. IBM QRadar SOAR orchestrates complex workflows with compliance-ready documentation. Rapid7 InsightConnect brings automation to mid-market teams. And TheHive plus OSQuery deliver community-driven flexibility for organizations that value transparency.
No tool works in isolation. The strongest IR programs combine detection, case management, automation, and validation into coordinated workflows where each component strengthens the others. When alert validation for EDR confirms a threat before containment triggers, automation becomes far more reliable. Sandboxing then adds behavioral evidence that helps investigations close faster. And when open-source tools integrate smoothly with commercial platforms, teams get both flexibility and enterprise-grade support.
The threats your organization faces in 2026 won’t wait for manual triage. The question is whether your IR toolkit helps your team respond in seconds, or whether it adds to the noise.
FAQs
What is the best incident response tool for large enterprises?
CrowdStrike Falcon, Palo Alto Cortex XDR/XSOAR, and Splunk Enterprise Security consistently rank as top choices for large enterprises. CrowdStrike excels in endpoint detection with industry-leading telemetry. Cortex XDR/XSOAR combines detection accuracy with powerful automation. Splunk ES leverages existing log infrastructure for deep investigations. The “best” choice depends on your existing security stack and whether you prioritize detection, automation, or analytics.
What is the best tool for IR automation?
Palo Alto Cortex XSOAR and IBM QRadar SOAR lead the automation category. XSOAR offers thousands of integrations and suits large-scale SOCs or MSSPs managing complex environments. QRadar SOAR provides visual playbook builders and compliance-friendly audit trails, making it ideal for regulated industries. For mid-market teams, Rapid7 InsightConnect offers accessible automation without extensive engineering requirements.
What is the best open-source IR tool?
TheHive Project, Cortex, and OSQuery form a powerful open-source IR stack. TheHive handles case management and analyst collaboration. Cortex automates enrichment through hundreds of analyzers. OSQuery provides endpoint visibility through SQL-like queries. Together, they deliver enterprise-grade capabilities without licensing costs, though you’ll need internal expertise to deploy and maintain them.
Are incident response tools necessary if I already use a SIEM?
Yes. SIEM platforms provide visibility by aggregating and correlating log data, but they don’t handle the response workflow. IR tools add case management, playbook automation, coordinated investigations, and evidence tracking. SIEM tells you what happened; IR tools help you organize and execute the response. Most mature security programs use both, often integrated so SIEM alerts automatically create cases in your IR platform.
What features should I prioritize when selecting an IR tool?
Prioritize automation capabilities that reduce manual work, integration ecosystem compatibility with your existing security tools, case management features for organizing investigations, investigative capabilities like forensics and threat hunting, and scalability to handle growing alert volumes. Also consider whether your team has the expertise to maintain open-source solutions or whether commercial support makes sense. The right balance depends on your environment, team size, and budget constraints.
如有侵权请联系:admin#unsafe.sh