
嗯,用户让我总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”之类的开头,直接写描述。好的,我先看看文章讲的是什么。 文章提到微软在2025年12月的补丁星期二发布了56个CVE修复,其中有三个是关键级别的,53个是重要的。里面包括了两个公开披露的漏洞和一个被利用的零日漏洞。这些漏洞涉及多个产品,比如Windows、Office、Azure等。 漏洞类型主要是权限提升(EoP)占了50%,其次是远程代码执行(RCE)占33.9%。具体的漏洞包括Windows Cloud Files Mini Filter Driver的几个EoP漏洞,GitHub Copilot的一个RCE漏洞,PowerShell的一个RCE漏洞,Win32k的EoP漏洞,以及Office的两个RCE漏洞。 用户可能需要的是一个简洁明了的摘要,重点突出关键信息:补丁数量、严重性评分、涉及的产品和主要漏洞类型。所以我要把这些信息浓缩到100字以内。 首先确定主要点:微软修复了56个CVE,其中三个关键级,涉及多个产品;主要类型是EoP和RCE;特别提到了零日漏洞和一些关键漏洞。 然后组织语言:微软在2025年12月修复了56个CVE,包括两个公开披露和一个零日。这些影响Windows、Office等产品。其中三个是关键级,53个重要级。主要问题是权限提升(占一半)和远程代码执行(约三分之一)。特别提到了GitHub Copilot、PowerShell、Win32k和Office的高危漏洞。 这样大概控制在100字左右。 </think> 微软在2025年12月修复了56个安全漏洞(包括两个公开披露和一个零日),影响Windows、Office、Azure等产品。其中三个被评为"关键"级,其余为"重要"级。主要问题包括权限提升(占一半)和远程代码执行(约三分之一)。GitHub Copilot、PowerShell、Win32k和Office存在高危漏洞。 2025-12-9 18:52:29 Author: www.tenable.com(查看原文) 阅读量:9 收藏
December 9, 2025
5 Min Read

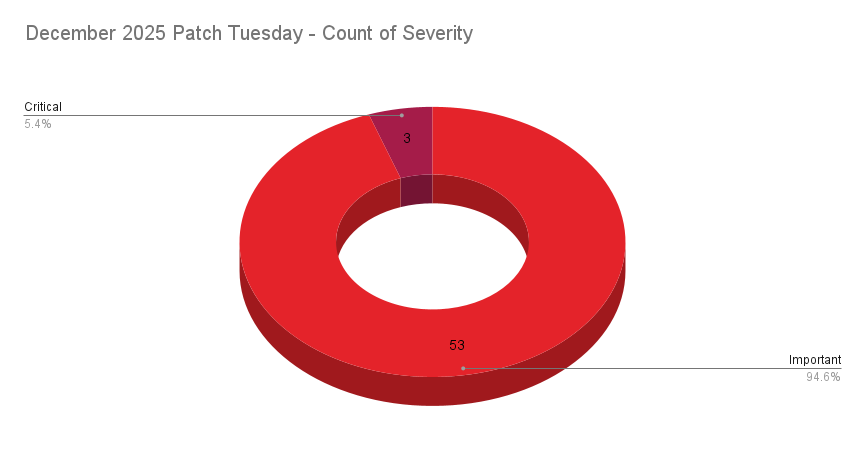
- 3Critical
- 53Important
- 0Moderate
- 0Low
Microsoft addresses 56 CVEs, including two publicly disclosed vulnerabilities and one zero-day that was exploited in the wild to close out the final Patch Tuesday of 2025
Microsoft patched 56 CVEs in its December 2025 Patch Tuesday release, with three rated critical, and 53 rated as important.
This month’s update includes patches for:
- Application Information Services
- Azure Monitor Agent
- Copilot
- Microsoft Brokering File System
- Microsoft Edge for iOS
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Word
- Storvsp.sys Driver
- Windows Camera Frame Server Monitor
- Windows Client-Side Caching (CSC) Service
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows DWM Core Library
- Windows Defender Firewall Service
- Windows DirectX
- Windows Hyper-V
- Windows Installer
- Windows Message Queuing
- Windows PowerShell
- Windows Projected File System
- Windows Projected File System Filter Driver
- Windows Remote Access Connection Manager
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Shell
- Windows Storage VSP Driver
- Windows Win32K - GRFX
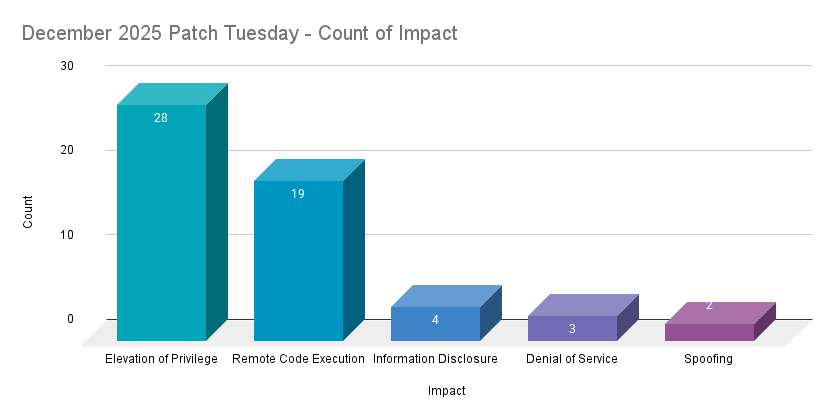
Elevation of privilege (EoP) vulnerabilities accounted for 50% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 33.9%.
CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2025-62221 is an EoP vulnerability in the Windows Cloud Files Mini Filter Driver. It was assigned a CVSSv3 score of 7.8 and rated as important. A local, authenticated attacker could exploit this vulnerability to elevate to SYSTEM privileges. According to Microsoft, this vulnerability was exploited in the wild as a zero-day.
Microsoft also patched two additional EoP vulnerabilities in the Windows Cloud Files Mini Filter Driver, CVE-2025-62454 and CVE-2025-62457. Both were assigned the same CVSSv3 score of 7.8 and rated important. However, CVE-2025-62454 was assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index while CVE-2025-62457 was assessed as “Exploitation Unlikely.”
CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability
CVE-2025-64671 is a RCE vulnerability in the GitHub Copilot Plugin for JetBrains Integrated Development Environments (IDEs). It was assigned a CVSSv3 score of 8.4, rated important and assessed as “Exploitation Less Likely” The issue stems from a command injection vulnerability in GitHub Copilot. An attacker could leverage a “malicious Cross Prompt Inject” either through an MCP Server or untrusted files. Successful exploitation would grant an attacker the ability to append unapproved commands onto existing allowed commands due to the ‘auto-approve’ setting in the terminal.
This vulnerability has been dubbed IDEsaster by security researcher, Ari Marzuk who is credited for reporting this vulnerability to Microsoft.
CVE-2025-54100 | PowerShell Remote Code Execution Vulnerability
CVE-2025-54100 is a RCE vulnerability in Windows PowerShell. This vulnerability was assigned a CVSSv3 score of 7.8 and is rated as important. According to the advisory, this RCE was publicly disclosed prior to a patch being made available. The advisory notes that after installing the update, a warning prompt will be displayed anytime the Invoke-WebRequest command is used.
This vulnerability was attributed to several researchers including Justin Necke, DeadOverflow, Pēteris Hermanis Osipovs, Anonymous, Melih Kaan Yıldız and Osman Eren. The researcher known as DeadOverflow has a YouTube video demonstrating how this flaw can be abused and links to a HackerOne report opened with the curl project by another researcher. According to the HackerOne report, the issue was not related to curl, but rather appeared to be related to the PowerShell curl alias that utilizes Invoke-WebRequest.
CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability
CVE-2025-62458 is an EoP vulnerability affecting Microsoft’s Win32k, a core kernel-side driver used in Windows. This vulnerability received a CVSSv3 score of 7.8, was rated as important and assessed as “Exploitation More Likely.” Successful exploitation of this vulnerability would allow an attacker to gain SYSTEM level privileges on an affected host.
Including CVE-2025-62458, this is the ninth EoP vulnerability affecting Win32k addressed by Microsoft in 2025, with 14 EoP flaws addressed in the driver throughout 2024.
CVE-2025-62554 and CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability
CVE-2025-62554 and CVE-2025-62557 are RCE vulnerabilities affecting Microsoft Office. Both received CVSSv3 scores of 8.4 and were rated as critical. An attacker could exploit these flaws through social engineering by sending the malicious Microsoft Office document file to an intended target. Successful exploitation would grant code execution privileges to the attacker.
Despite being flagged as “Less Likely” to be exploited, Microsoft notes that the Preview Pane is an attack vector for both vulnerabilities, which means exploitation does not require the target to open the file. According to the advisories from Microsoft, security updates for Microsoft Office LTSC for Mac are not yet available and will be released as soon as they are ready.
Tenable Solutions
A list of all the plugins released for Microsoft’s December 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's December 2025 Security Updates
- Tenable plugins for Microsoft December 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on Tenable Connect and engage with us in the Threat Roundtable group for further discussions on the latest cyber threats.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

Research Special Operations
The Research Special Operations (RSO) team serves as Tenable’s Forward Logistics Element in the threat landscape, providing customers with the analyses and contextualized exposure intelligence required to manage risks to critical business assets. With over 150 years of collective expertise, this hand-picked group of world-class security researchers is united with one mission: to cut through the noise and deliver critical intelligence about the most dangerous cyber threats emerging right now. Uniting the missions of the Tenable Security Response, Zero-Day Research, and Decision Science Operations teams, RSO disseminates timely, accurate, and actionable information about the latest threats and exposures.
- Exposure Management
- Vulnerability Management
Cybersecurity news you can use
Enter your email and never miss timely alerts and security guidance from the experts at Tenable.
如有侵权请联系:admin#unsafe.sh