Four distinct threat activity clusters have been observed leveraging a malware loader known as CastleLoader, strengthening the previous assessment that the tool is offered to other threat actors under a malware-as-a-service (MaaS) model.
The threat actor behind CastleLoader has been assigned the name GrayBravo by Recorded Future's Insikt Group, which was previously tracking it as TAG-150.
GrayBravo is "characterized by rapid development cycles, technical sophistication, responsiveness to public reporting, and an expansive, evolving infrastructure," the Mastercard-owned company said in an analysis published today.
Some of the notable tools in the threat actor's toolset include a remote access trojan called CastleRAT and a malware framework referred to as CastleBot, which comprises three components: a shellcode stager/downloader, a loader, and a core backdoor.
The CastleBot loader is responsible for injecting the core module, which is equipped to contact its command-and-control (C2) server to retrieve tasks that enable it to download and execute DLL, EXE, and PE (portable executable) payloads. Some of the malware families distributed via this framework are DeerStealer, RedLine Stealer, StealC Stealer, NetSupport RAT, SectopRAT, MonsterV2, WARMCOOKIE, and even other loaders like Hijack Loader.
Recorded Future's latest analysis has uncovered four clusters of activity, each operating with distinct tactics -
- Cluster 1 (TAG-160), which targets the logistics sector using phishing and ClickFix techniques to distribute CastleLoader (Active since at least March 2025)
- Cluster 2 (TAG-161), which uses Booking.com-themed ClickFix campaigns to distribute CastleLoader and Matanbuchus 3.0 (Active since at least June 2025)
- Cluster 3, which uses infrastructure impersonating Booking.com in conjunction with ClickFix and Steam Community pages as a dead drop resolver to deliver CastleRAT via CastleLoader (Active since at least March 2025)
- Cluster 4, which uses malvertising and fake software update lures masquerading as Zabbix and RVTools to distribute CastleLoader and NetSupport RAT (Active since at least April 2025)
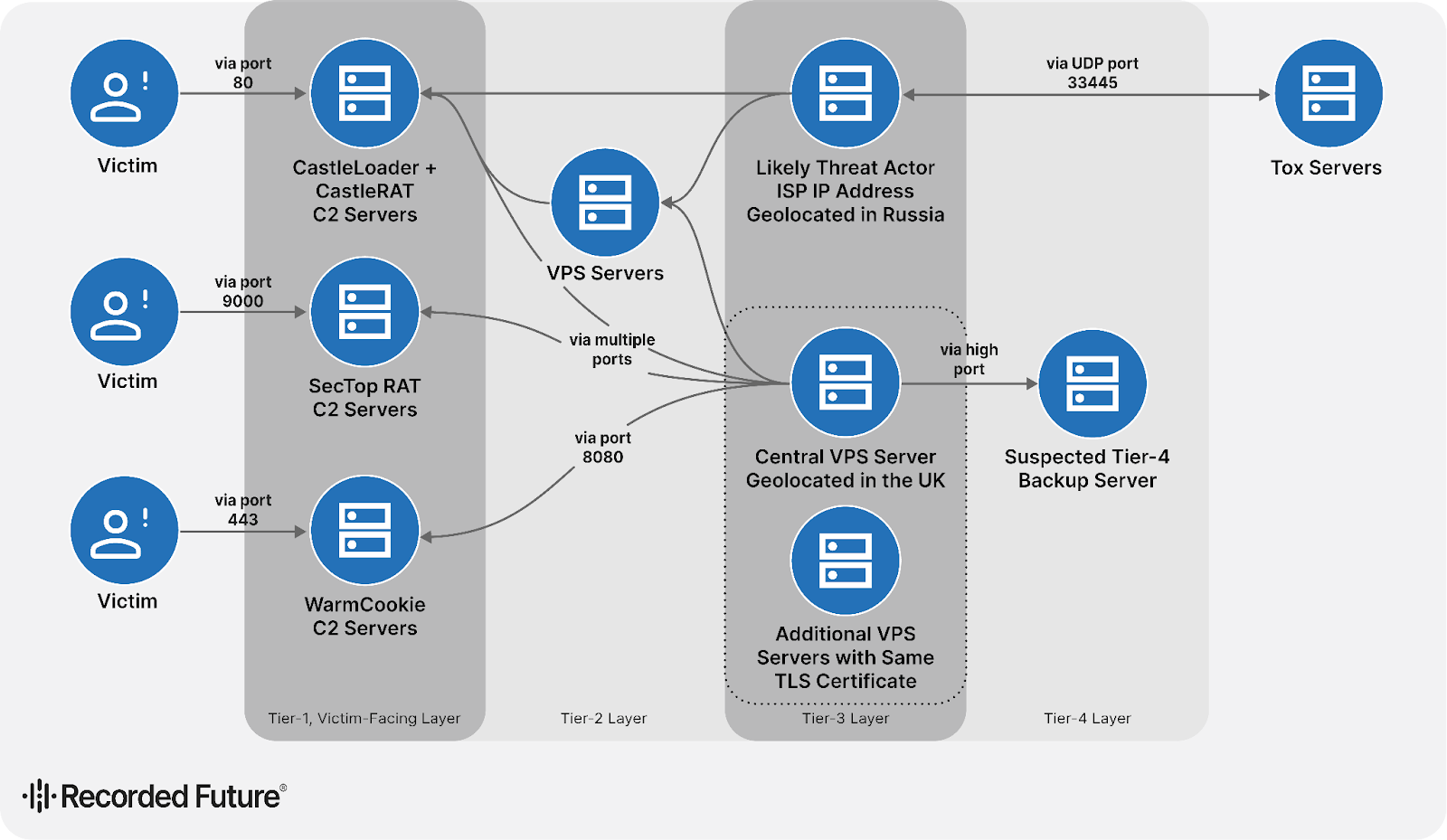
GrayBravo has been found to leverage a multi-tiered infrastructure to support its operations. This includes Tier 1 victim-facing C2 servers associated with malware families like CastleLoader, CastleRAT, SectopRAT, and WARMCOOKIE, as well as multiple VPS servers that likely operate as backups.
The attacks mounted by TAG-160 are also notable for using fraudulent or compromised accounts created on freight-matching platforms like DAT Freight & Analytics and Loadlink Technologies to enhance the credibility of its phishing campaigns. The activity, Recorded Future added, illustrates a deep understanding of industry operations, impersonating legitimate logistics firms, exploiting freight-matching platforms, and mirroring authentic communications to enhance its deception and impact.
It's been assessed with low confidence that the activity could be related to another unattributed cluster that targeted transportation and logistics companies in North America last year to distribute various malware families.
"GrayBravo has significantly expanded its user base, evidenced by the growing number of threat actors and operational clusters leveraging its CastleLoader malware," Recorded Future said. "This trend highlights how technically advanced and adaptive tooling, particularly from a threat actor with GrayBravo's reputation, can rapidly proliferate within the cybercriminal ecosystem once proven effective."
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.