嗯,用户让我帮忙总结一篇文章,控制在一百个字以内,而且不需要用“文章内容总结”这样的开头。首先,我需要通读整篇文章,抓住主要信息。 文章讲的是一个叫做Broadside的僵尸网络,基于Mirai,攻击TBK DVR设备。这些设备被用于海运物流,所以威胁很大。Cydome的研究人员发现了这个活动,并且详细描述了它的功能和影响。 接下来,我需要提取关键点:Broadside是Mirai的变种,利用CVE-2024-3721漏洞攻击TBK DVR,影响海运物流。它具备DDoS攻击、窃取密码、隐藏模块等功能。此外,还提到多个地区的感染情况。 然后,我要把这些信息浓缩到100字以内。确保涵盖主要威胁、目标、功能和影响范围。 最后,检查一下是否符合用户的要求:中文总结,直接描述内容,不使用特定开头。 </think> Mirai变种Broadside僵尸网络利用CVE-2024-3721漏洞攻击TBK DVR设备,威胁海运物流行业。该僵尸网络具备DDoS攻击、窃取密码文件、隐藏模块等功能,并影响多个地区。 2025-12-9 15:10:59 Author: securityaffairs.com(查看原文) 阅读量:9 收藏
Broadside botnet hits TBK DVRs, raising alarms for maritime logistics
Pierluigi Paganini
December 09, 2025

Mirai-based Broadside botnet targets vulnerable TBK Vision DVRs, posing a potential threat to the maritime logistics sector, Cydome warns.
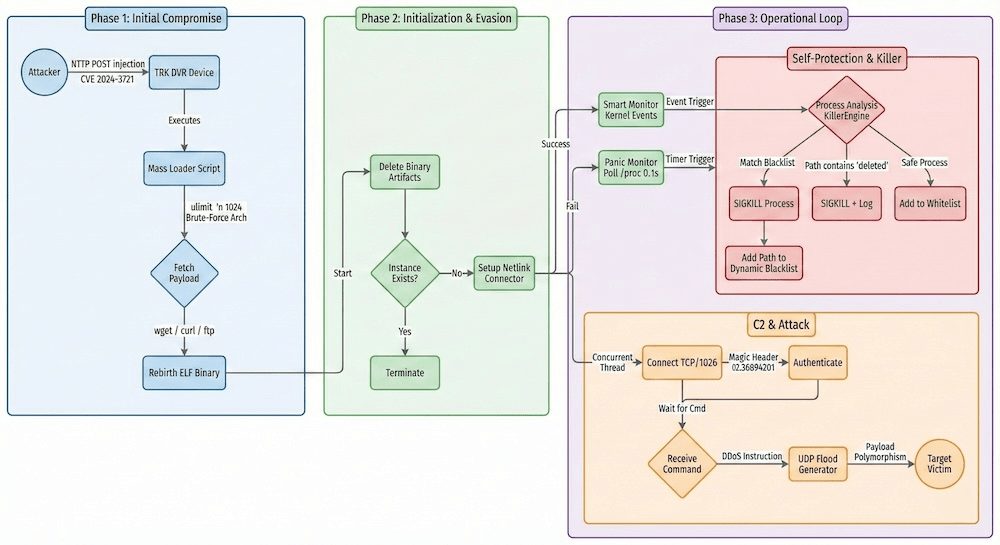
Cydome researchers have identified a new Mirai botnet variant dubbed Broadside that is targeting the maritime logistics sector by exploiting the command injection vulnerability CVE-2024-3721 in TBK DVR devices used on vessels.
“Cydome’s Cybersecurity Research Team has identified an active campaign of a new variant of the Mirai botnet, designated as “Broadside”.” reads the report published by Cydome. “This campaign was found to target the maritime logistics sector, exploiting a vulnerability (CVE-2024-3721) in TBK DVR (Digital Video Recorders) devices in use by shipping companies on vessels (among others).”
The flaw was disclosed in April 2024 with PoC code available, and it has been widely exploited by multiple DDoS botnets by mid-2025.
The Mirai botnet’s source code, made public nearly a decade ago, has since been widely reused and modified by cybercriminals to power large-scale botnets.
Cydome observed that the campaign’s infrastructure has been tracked for months, showing fluctuating activity. Broadside differs from typical Mirai through a custom C2 protocol over TCP/1026 (with fallback communications on TCP/6969), a unique Magic Header, and a “Judge, Jury, and Executioner” exclusivity module. The bot uses Netlink kernel sockets for stealthy monitoring and payload polymorphism to evade detection.
The Broadside botnet is using a mass loader that executes multi-architecture payloads in memory and wipes traces. Like other Mirai variants, it supports UDP-based DDoS attacks, however, beyond DDoS, it also steals /etc/passwd and /etc/shadow, enabling privilege escalation and lateral movement.
Broadside also includes a process-killer module that maintains control by terminating suspicious or hostile processes.
The researchers warn that TBK DVR flaw also impacts rebranded models sold as CeNova, Night Owl, QSee, and others.
Cydome warns the campaign poses serious risks to shipping firms, as the targeted DVRs are often installed on vessels. Compromised devices could enable access to CCTV feeds of the bridge, cargo areas, or engine room, disrupt satellite communications through flooding, or provide a foothold for lateral movement toward critical OT systems on the ship.
“Crucially, the threat extends beyond denial-of-service attacks; analysis confirms that Broadside actively attempts to harvest system credential files (/etc/passwd and /etc/shadow).” concludes the report. “This indicates a secondary objective of privilege escalation and lateral movement, transforming the compromised device from a simple bot into a strategic foothold.”
In June, researchers from Russian cybersecurity firm Kaspersky discovered another variant of the Mirai botnet that exploits a command injection vulnerability (CVE-2024-3721) in TBK DVR-4104 and DVR-4216 digital video recording devices. During a review of the logs in their Linux honeypot system, the researchers noticed a suspect POST request linked to the potential exploitation of CVE-2024-3721.
This Mirai variant uses a simple RC4 algorithm to decrypt strings and uses XOR to obfuscate the key. Once decrypted, strings are stored in a global list for use during execution. The malware also includes anti-VM and anti-emulation checks by scanning running processes for signs of VMware or QEMU.
The malware also verifies its execution path against a list of allowed directories to avoid detection. If all checks pass, it proceeds to prepare the infected device to receive commands.
Most infections are in China, India, Egypt, Ukraine, Russia, Turkey, and Brazil. While the exact number of infected devices is unclear, Kaspersky found over 50,000 exposed DVRs, which are potential targets.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Broadside botnet)
如有侵权请联系:admin#unsafe.sh
