React2Shell漏洞引发全球安全危机,超30组织受影响,黑客利用恶意软件窃取敏感信息。FBI敦促升级系统并监测入侵迹象。专家发现大量针对该漏洞的扫描活动。 2025-12-8 16:46:12 Author: therecord.media(查看原文) 阅读量:9 收藏
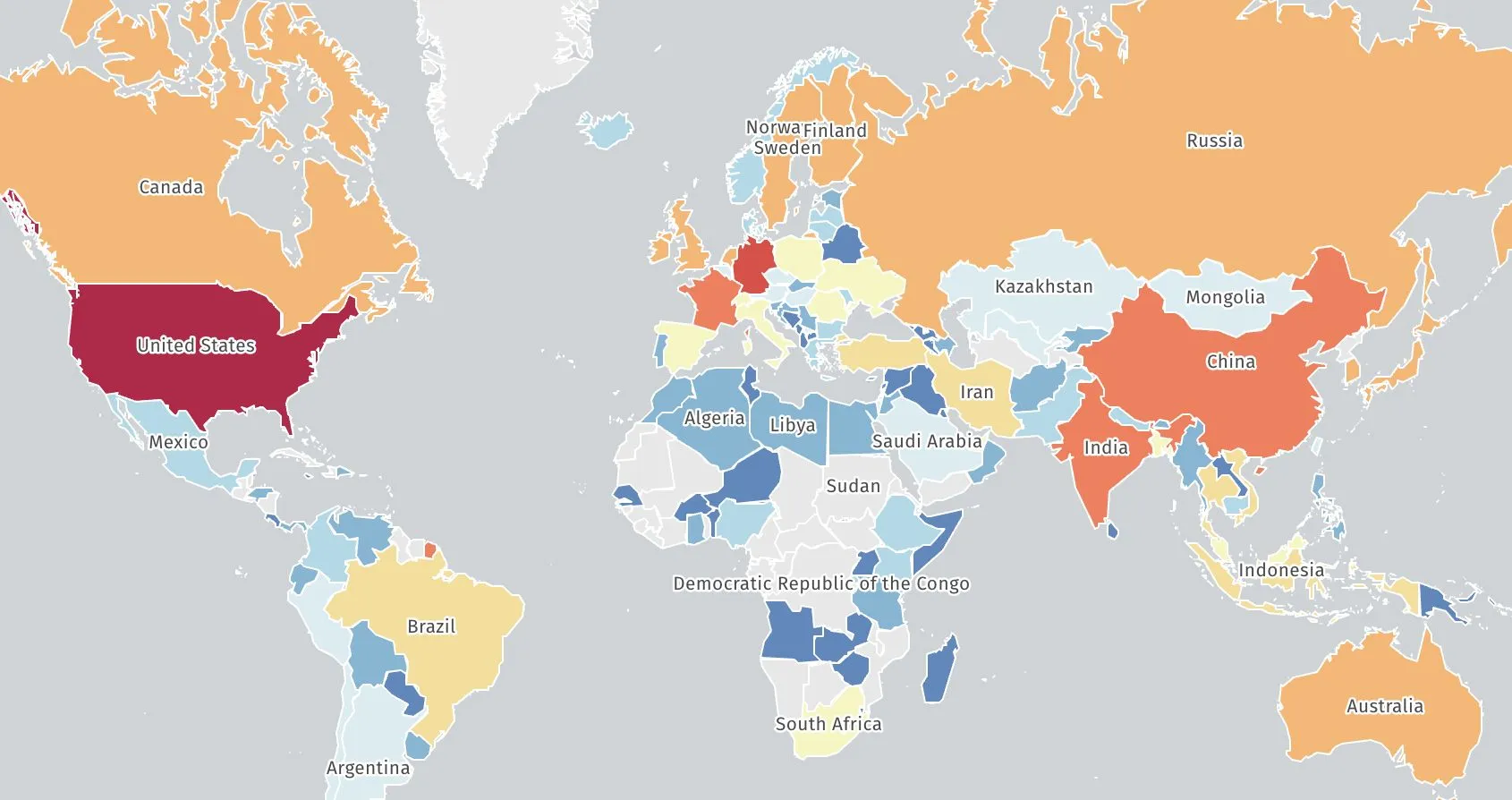
Organizations across multiple sectors are dealing with the fallout of the React2Shell bug that emerged last Wednesday and caused a global patching scramble. Justin Moore, a member of the threat intel research team at Palo Alto Networks’ Unit 42, told Recorded Future News this weekend that they have confirmed more than 30 affected organizations. “We have observed scanning for vulnerable RCE, reconnaissance activity, attempted theft of AWS configuration and credential files, as well installation of downloaders to retrieve payloads from attacker command and control infrastructure,” Moore said. Unit 42 attributed the activity to an initial access broker “with ties to the Chinese Ministry of State Security.” In the attacks tracked by Unit 42, the hackers used malware strains known as Snowlight and Vshell — malicious tools previously tied to a contractor for China's Ministry of State Security (MSS) by incident responders at Mandiant. The Trump administration recently announced plans to scupper sanctions on the MSS that were put in place following alleged hacks by the agency on at least nine of the largest telecommunications companies in the U.S. The hackers used their access to steal the correspondence of President Donald Trump and Vice President JD Vance last year. A map of the tools connected to the internet that are potentially vulnerable to CVE-2025-55182, with dark red representing over 10,000. Image: Shadowserver Foundation Unit 42’s findings come after experts from Amazon said last week that state-backed hackers in China are exploiting CVE-2025-55182 — a vulnerability impacting a popular open-source tool built into thousands of widely-used digital products. Referred to colloquially as React2Shell, the bug was reported by researcher Lachlan Davidson on November 29 and publicly disclosed on Wednesday, when a fix was rolled out. The vulnerability carries a “critical” severity score of 10 out of 10. On Sunday, FBI Assistant Director Brett Leatherman urged IT teams to “prioritize an immediate upgrade to the latest patched versions, and consider targeted threat hunting for signs of compromise.” “In many environments, teams inherit this exposure simply by adopting modern framework defaults - without explicitly enabling any special “server function” features. That means customer portals, SaaS front-ends, developer/admin consoles, and third-party services built on these stacks may all be in scope,” he explained. “Where there are indications of successful exploitation - particularly in environments affecting critical services or large populations - please consider engaging your local FBI cyber team.:” He urged defenders to look at advisories from Censys and GreyNoise for more technical guidance on how hackers are exploiting the bug. According to Leatherman, current incident data shows “high-volume, automated exploitation attempts” and other evidence that gives defenders “concrete signals to monitor.” Multiple organizations said they saw scanning by cybercriminals and nation-state actors growing as concern about the vulnerability evolved throughout the week. The U.K.-based Shadowserver Foundation as well as Censys and GreyNoise all tracked widespread scanning and targeting of the bug. Shadowsever explained that more than 10,000 tools connected to the internet in the U.S. are vulnerable to CVE-2025-55182, with thousands more across Brazil, Russia, Germany, France, India and China. Censys said it observed more than 2.15 million instances of internet facing services that may be affected by the vulnerability. GreyNoise found much of the targeting to be “opportunistic and automated.” The Cybersecurity and Infrastructure Security Agency added the bug to its Known Exploited Vulnerabilities catalog on Friday, giving federal agencies until December 26 to patch it. 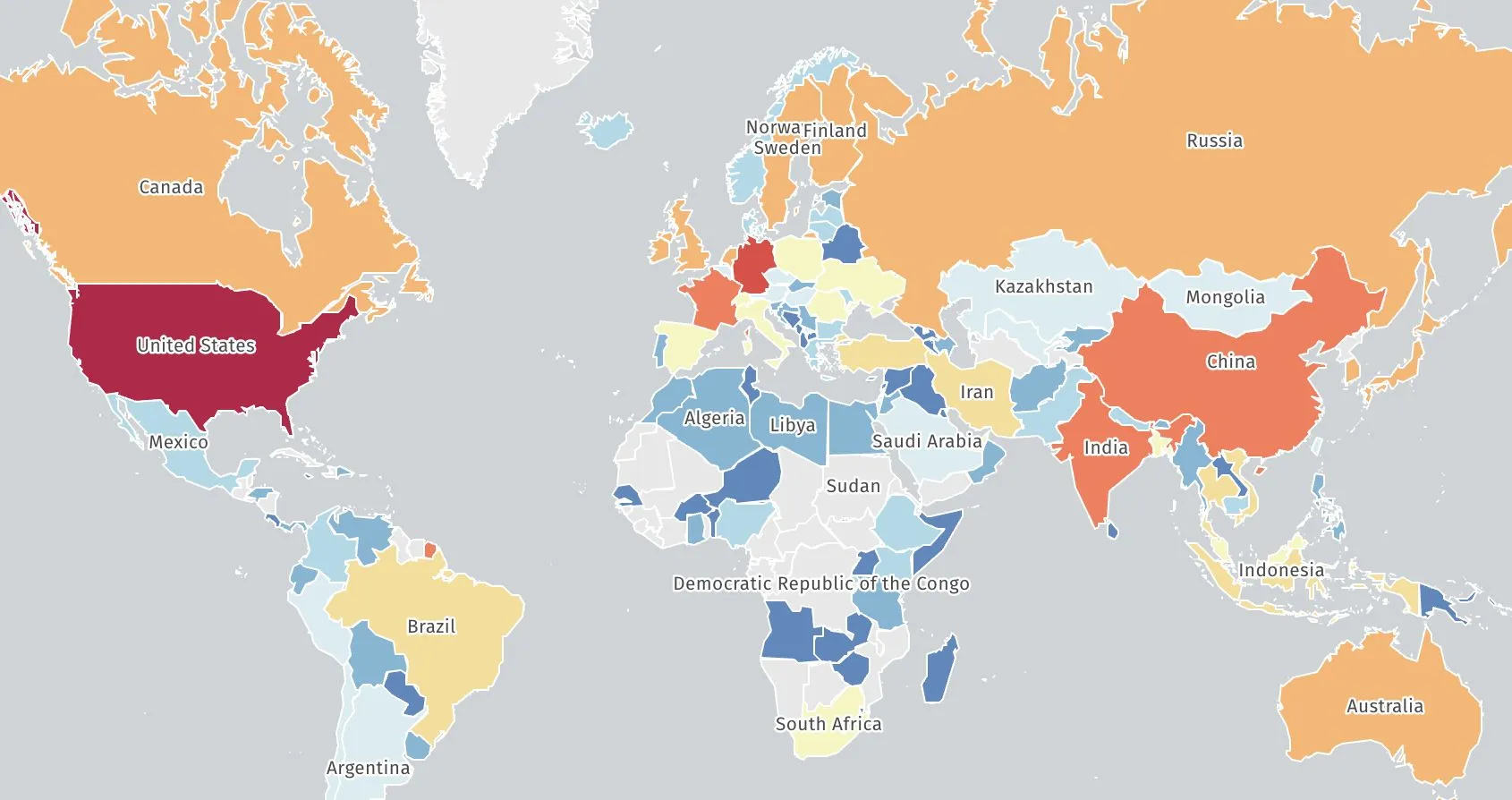
Widespread scanning
Get more insights with the
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.
如有侵权请联系:admin#unsafe.sh

