嗯,用户让我用中文总结这篇文章,控制在100字以内,而且不需要用“文章内容总结”之类的开头。我得先仔细阅读一下文章内容。 文章讲的是黑客从12月2日开始攻击Palo Alto的GlobalProtect登录界面,并扫描SonicWall的API端点。攻击者来自德国的3xK GmbH公司的7000多个IP地址。GreyNoise的报告提到这些活动使用了之前在9月底到10月中旬攻击中见过的三个客户端指纹,显示攻击者工具的一致性。此外,12月3日针对SonicWall的API扫描也使用了相同的指纹,尽管基础设施和目标不同。 所以,我需要把这些关键点浓缩到100字以内。包括时间、攻击目标、IP来源、指纹重复以及攻击者工具的一致性。 可能的结构:黑客从12月2日起攻击GlobalProtect和SonicWall API,使用德国公司的IP,指纹与之前攻击相同,显示工具一致。 检查字数是否在限制内,并确保信息准确。 </think> 黑客自12月2日起针对Palo Alto GlobalProtect登录界面和SonicWall API发起攻击,利用德国3xK GmbH公司的7,000多个IP地址进行尝试。攻击行为与9月至10月的活动使用相同客户端指纹,显示工具一致性。 2025-12-6 16:8:52 Author: securityaffairs.com(查看原文) 阅读量:10 收藏
Attackers launch dual campaign on GlobalProtect portals and SonicWall APIs
Pierluigi Paganini
December 06, 2025

A hacking campaign is targeting GlobalProtect logins and scannig SonicWall APIs since December 2, 2025.
A campaign began on December 2 targeting Palo Alto GlobalProtect portals with login attempts and scanning SonicWall SonicOS API endpoints. The activity came from over 7,000 IPs tied to German hosting provider 3xK GmbH, which operates its own BGP network (AS200373).
“On 2 December 2025, GreyNoise observed a concentrated spike of 7,000+ IPs attempting to log into Palo Alto Networks GlobalProtect portals. All activity originated from infrastructure operated by 3xK GmbH and targeted two Palo Alto profiles in GreyNoise’s Global Observation Grid (GOG).” reads the report published by the threat intelligence firm GreyNoise.
GlobalProtect is Palo Alto Networks’ VPN and secure remote-access solution. It gives users a protected connection to their organization’s network by routing their traffic through a Palo Alto firewall, which applies the same security controls used inside the corporate environment. According to the threat intelligence firm GreyNoise, the campaign targeted two Palo Alto profiles.
The December traffic reuses three client fingerprints previously seen in a late-September to mid-October wave. That earlier surge came from four typically non-malicious ASNs (NForce Entertainment, Data Campus, Flyservers, and Internet Solutions & Innovations) which generated over 9 million legitimate HTTP sessions, mostly hitting GlobalProtect portals and authentication endpoints. The reappearance of identical fingerprints on new infrastructure signals consistent tooling across seemingly separate events.
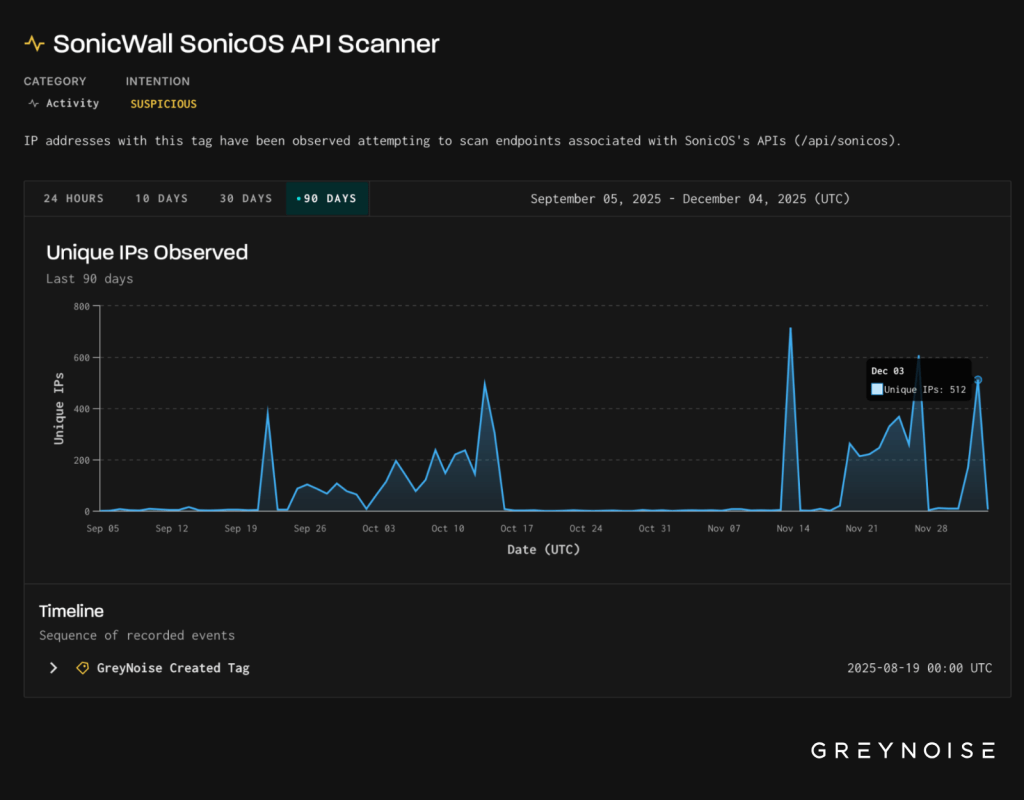
GreyNoise saw a major spike in scans against SonicWall SonicOS APIs on December 3, showing the same three client fingerprints tied to the December 2 GlobalProtect login surge and the September-October brute-force wave.
Despite shifting infrastructure and different targets, the identical fingerprints point to the same underlying tooling.
GreyNoise also observed that a surge of scans against SonicWall SonicOS API endpoints on 3 December carried the same three client fingerprints previously seen in the 2 December GlobalProtect login spike and in the large September–October brute-forcing campaign. The researchers pointed out that although the infrastructure and targeted vendors are different, the identical fingerprints reveal continuity in the attacker’s tooling. Telemetry shows a clear rhythm: intense login and brute-force activity from clean ASNs between late September and mid-October, a slowdown through late November, then the same client resurfacing on 3xK’s infrastructure on 2 December to probe Palo Alto portals, followed the next day by SonicWall API scans. GreyNoise Block users can automatically block all associated IPs through provided templates for Palo Alto and SonicWall activity, with enterprise customers able to apply more granular blocklists based on ASNs, JA4, and geography.
“defenders should:
- Monitor authentication surfaces for abnormal velocity or repeated failures.
- Track recurring client fingerprints to surface campaign continuity.
- Apply dynamic, context-aware blocking rather than static reputation lists.” concludes the report.
“Fingerprint-level telemetry exposes cross-infrastructure relationships that defenders might otherwise miss.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, GlobalProtect)
如有侵权请联系:admin#unsafe.sh

