
React Server Components(RSC)中的Flight协议存在严重漏洞(CVE-2025-55182/CVE-2025-66478),允许未经身份验证的远程代码执行。该漏洞影响React 19.x和Next.js等框架,默认配置下易受攻击。建议立即升级至修复版本以消除风险。 2025-12-5 23:40:26 Author: horizon3.ai(查看原文) 阅读量:12 收藏
A maximum-severity vulnerability in the React Server Components (RSC) “Flight” protocol, widely referred to as React2Shell, allows unauthenticated remote code execution against servers running affected React 19, Next.js, and additional JavaScript frameworks and applications. React has assigned CVE-2025-55182 with a CVSS score of 10.0, and Next.js has tracked its downstream impact as CVE-2025-66478.
The NodeZero® Offensive Security Platform now includes a dedicated Rapid Response test so you can quickly verify whether these flaws are exploitable in your environment and validate that your patches and mitigations actually removed the risk.
What it is and why it matters
React Server Components use the Flight protocol to send serialized component trees from server to client. Frameworks and bundlers such as Next.js, Vite, Parcel, and React Router integrate these server packages to enable server functions and RSC endpoints.
CVE-2025-55182 is a logical deserialization vulnerability in how React decodes payloads sent to React Server Function endpoints. When a server receives a specially crafted RSC/Flight payload, it fails to properly validate the structure and ends up executing attacker-controlled inputs on the server, leading to remote code execution.
Stop Guessing, Start Proving
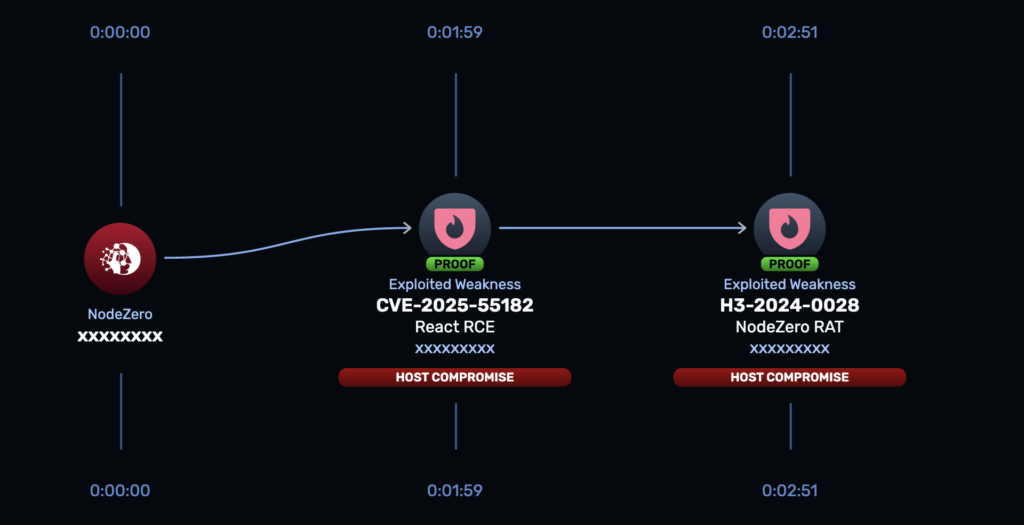
Key technical characteristics:
- CVSS 10.0, remote, unauthenticated RCE in React’s server components.
- Affects React 19.0, 19.1.0, 19.1.1, and 19.2.0, patched in 19.0.1, 19.1.2, and 19.2.1.
- Exploitable via specially crafted HTTP requests against React Server Function / RSC endpoints, including default configurations of popular frameworks.
CVE-2025-66478 tracks the downstream impact on Next.js: experimental canary builds starting with 14.3.0-canary.77, and 15.x and 16.x App Router releases below the patched versions, all inherit the same RCE issue through their use of React Server and Flight.
React powers millions of websites and sees over 55 million weekly downloads from npm, while Next.js counts more than 16 million weekly downloads. Analysis suggests roughly 39% of observed cloud environments contain vulnerable React or Next.js instances.
From a risk standpoint, successful exploitation gives an attacker code execution on the application server handling page rendering and server functions. As your internal GTM guide already notes, this can enable theft of secrets such as API keys and database credentials, installation of backdoors, and potential pivoting deeper into backend services.
Quick actions — do these now
- Run the NodeZero Rapid Response test for React Server RCE
For React2Shell, the Rapid Response test safely determines whether CVE-2025-55182 / CVE-2025-66478 are actually exploitable in your internal and external environments, so you can prioritize real risk over theoretical exposure. - Patch React, Next.js, and related frameworks immediately
- Upgrade React to a fixed release: 19.0.1, 19.1.2, or 19.2.1.
- For Next.js App Router apps, upgrade to the patched versions published by Vercel, including 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, and 16.0.7 (or newer).
- Review any use of other RSC integrations such as Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku, and follow their specific guidance.
- Your internal GTM doc also notes that additional fixes may still roll out across the ecosystem; track the React and Next.js advisories for updates.
- Re-run the Rapid Response test to validate remediation
After applying patches or interim mitigations, re-run the React Server RCE Rapid Response test. NodeZero will confirm whether the attack paths that were previously exploitable have been eliminated, giving your team evidence that the risk is actually removed rather than assumed to be fixed.
Indicators of compromise
Public reporting to date focuses on vulnerable versions, exploit mechanics, and patch guidance, not on concrete, vendor-supplied IoCs for this specific bug.
However, because this is an unauthenticated RCE in a web server context, defenders can use generic RCE hunting patterns while waiting for more specific IoCs from React, Vercel, or their security vendors. Examples include:
- Unusual POST requests or spikes in traffic to RSC / Server Function endpoints that handle Flight payloads.
- Unexpected errors or logs related to deserialization or malformed RSC payloads on React / Next.js servers.
- Creation of unfamiliar temporary files or modules near your application code following suspicious requests.
- New outbound connections from app servers to untrusted IPs shortly after anomalous requests.
- Execution of common attacker recon commands or OS-level activity originating from the app server process.
These are generic behavioral indicators, not official IoCs supplied by React, Vercel, or Horizon3.ai. They should complement, not replace, vendor-specific signatures and WAF rules as they become available. es as they become available.
Affected versions and patch
React
- Affected:
- 19.0
- 19.1.0
- 19.1.1
- 19.2.0
- Patched:
- 19.0.1
- 19.1.2
- 19.2.1
The issue resides in how React decodes payloads sent to React Server Function endpoints in the RSC Flight protocol. Even applications that do not implement explicit server function endpoints may still be vulnerable if React Server Components are enabled.
Other frameworks and integrations
Wiz and other researchers have highlighted that additional frameworks implementing React Server and Flight may be vulnerable, including: React Router RSC, Vite RSC plugin, Parcel RSC plugin, RedwoodSDK, and Waku. Confirm guidance from each project’s advisory and upgrade to their recommended patched versions.
Timeline
- November 29, 2025 — Researcher Lachlan Davidson reports the vulnerability to React.
- December 3, 2025 — React publishes an advisory and patches for CVE-2025-55182, covering React 19.0, 19.1.0, 19.1.1, and 19.2.0, and fixing them in 19.0.1, 19.1.2, and 19.2.1.
- December 3–4, 2025 — SecurityWeek, Dark Reading, The Hacker News, and BleepingComputer publish analyses of React2Shell, confirming unauthenticated RCE, CVSS 10, and significant cloud-scale exposure.
- December 5, 2025 — NodeZero React Server RCE Rapid Response test becomes generally available to customers.
- December 5, 2025 — CVE-2025-5582 assigned to CISA KEV.
References
🔗 React advisory for CVE-2025-55182 (React Server Components / Flight RCE)
🔗 SecurityWeek — “React2Shell: In-the-Wild Exploitation Expected for Critical React Vulnerability”
🔗 BleepingComputer — “Critical React, Next.js flaw lets hackers execute code on servers”
🔗 Dark Reading — “Critical React Flaw Triggers Calls for Immediate Action”
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
