
好的,我现在需要帮用户总结一篇文章,控制在100字以内。用户的要求很明确,直接写文章描述,不需要开头。首先,我得通读整篇文章,抓住主要信息。 文章讲的是Intellexa公司的Predator间谍软件使用了一种零点击感染机制“Aladdin”。这种机制通过恶意广告传播,用户只要查看广告就会被感染,不需要点击。广告通过DSP平台投放在各种网站上,比如新闻网站或移动应用。这个机制隐藏在多个国家的壳公司背后,最近被Inside Story、Haaretz和WAV Research Collective联合调查揭露。 还有提到内部泄露的文件显示,广告网络涉及爱尔兰、德国等多个国家的公司。此外,Predator还利用三星Exynos芯片的漏洞进行攻击,并且Intellexa是零日漏洞的主要供应商之一。 总结时需要涵盖:Predator使用零点击广告传播、通过恶意广告感染、隐藏在壳公司中、涉及多个国家和公司、以及利用零日漏洞等关键点。控制在100字以内,确保信息准确且简洁。 </think> Intellexa's Predator spyware uses a zero-click mechanism called "Aladdin," infecting targets by viewing malicious ads. The ads are delivered via mobile advertising networks, leveraging public IP addresses and other identifiers. The investigation reveals a complex network of shell companies across multiple countries and confirms Intellexa's role in zero-day exploits targeting devices, including Samsung Exynos. Users are advised to enhance mobile security to protect against such threats. 2025-12-4 21:0:22 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

The Predator spyware from surveillance company Intellexa has been using a zero-click infection mechanism dubbed “Aladdin,” which compromised specific targets by simply viewing a malicious advertisement.
This powerful and previously unknown infection vector is meticulously hidden behind shell companies spread across multiple countries, now uncovered in a new joint investigation by Inside Story, Haaretz, and WAV Research Collective.
The investigation is based on 'Intellexa Leaks' - a collection of leaked internal company documents and marketing material, and is corroborated by technical research from forensic and security experts at Amnesty International, Google, and Recorded Future.
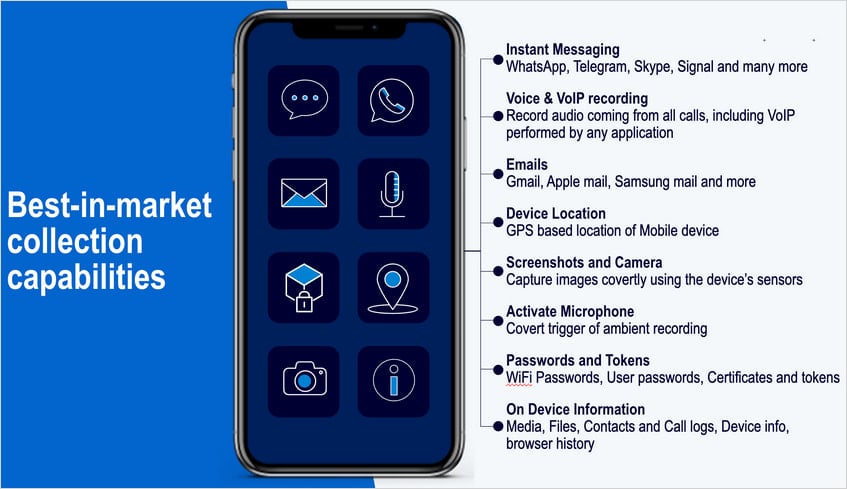
Source: Amnesty International
Ad-based spyware delivery
First deployed in 2024 and believed to still be operational and actively developed, Aladdin leverages the commercial mobile advertising system to deliver malware.
The mechanism forces weaponized ads onto specific targets identified by their public IP address and other identifiers, instructing the platforms via the Demand Side Platform (DSP) to serve it on any website participating in the ad network.
“This malicious ad could be served on any website that displays ads, such as a trusted news website or mobile app, and would appear like any other ad that the target is likely to see,” explains Amnesty International’s Security Lab.
“Internal company materials explain that simply viewing the advertisement is enough to trigger the infection on the target’s device, without any need to click on the advertisement itself.”
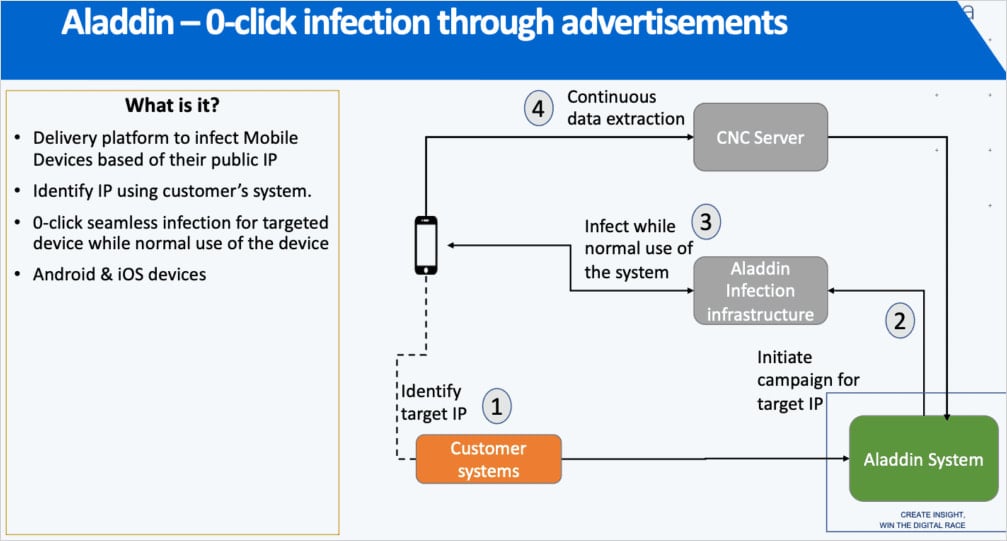
Source: Amnesty International
Although no details are available on how the infection works, Google mentions that the ads trigger redirections to Intellexa’s exploit delivery servers.
The ads are funneled through a complex network of advertising firms spread across multiple countries, including Ireland, Germany, Switzerland, Greece, Cyprus, the UAE, and Hungary.
Recorded Future dug deeper into the advertising network, connecting the dots between key people, firms, and infrastructure, and naming some of those companies in its report.
Defending against those malicious ads is complex, but blocking ads on the browser would be a good starting point.
Another potential defense measure would be to set the browser to hide the public IP from trackers.
However, the leaked documents show that Intellexa can still obtain the information from domestic mobile operators in their client’s country.
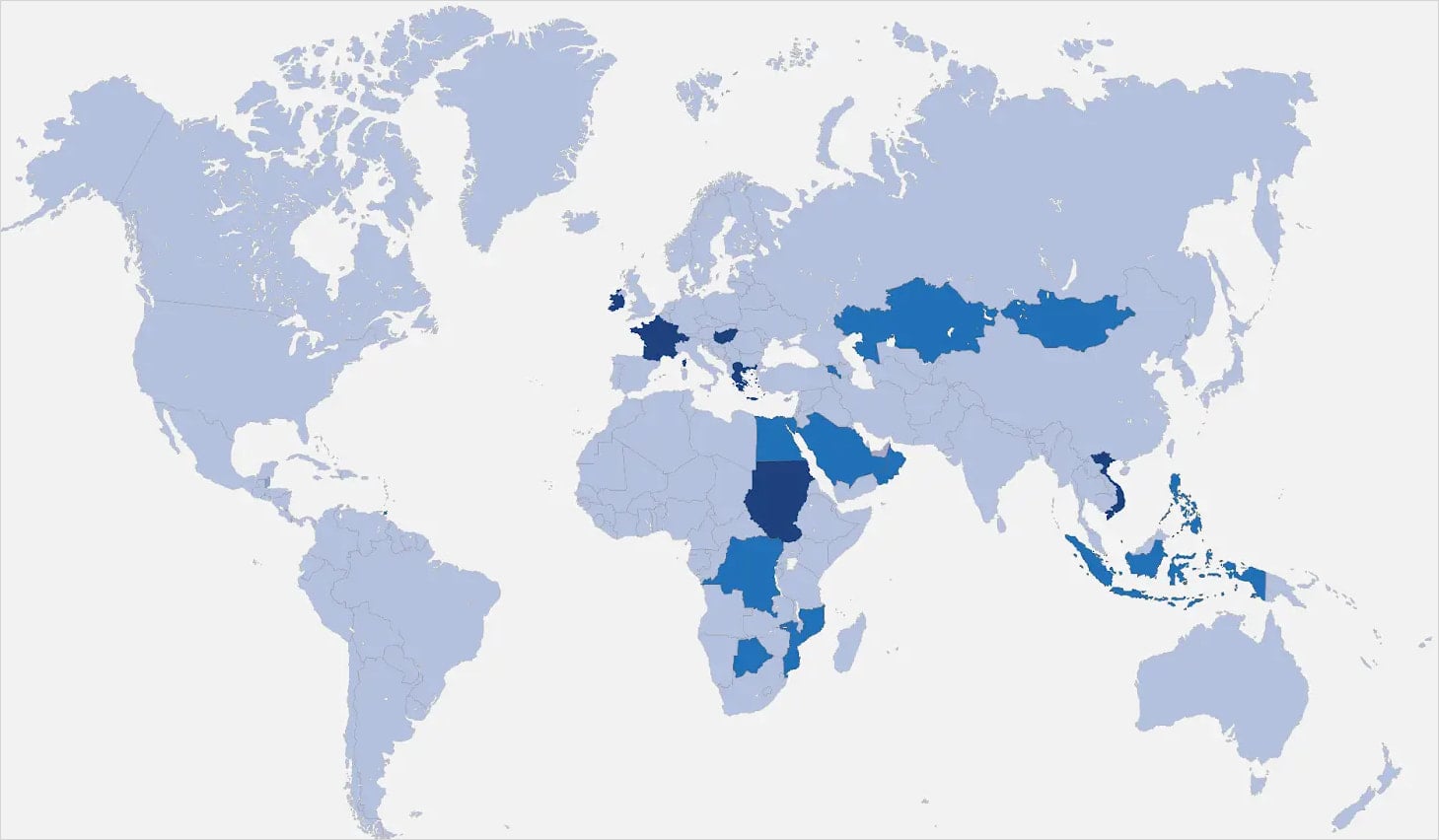
Source: Recorded Future
Samsung Exynos and zero-day exploits
Another key finding in the leak is confirmation of the existence of another delivery vector called 'Triton', which can target devices with Samsung Exynos with baseband exploits, forcing 2G downgrades to lay the ground for infection.
Amnesty International’s analysts are unsure whether this vector is still used and note that there are two other, possibly similar delivery mechanisms, codenamed 'Thor' and 'Oberon', believed to involve radio communications or physical access attacks.
Google’s researchers name Intellexa as one of the most prolific commercial spyware vendors in terms of zero-day exploitation, responsible for 15 out of the 70 cases of zero-day exploitation TAG discovered and documented since 2021.
Google says Intellexa develops its own exploits and also purchases exploit chains from external entities to cover the full spectrum of required targeting.
Despite sanctions and ongoing investigations against Intellexa in Greece, the spyware operator is as active as ever, according to Amnesty International.
As Predator evolves into becoming stealthier and harder to trace, users are recommended to consider enabling extra protection on their mobile devices, like Advanced Protection on Android and Lockdown Mode on iOS.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
