安全数据管道市场的存在反映了SIEM供应商长期忽视数据摄入问题的缺陷。Cribl等公司填补了这一空白,并逐渐成为中立的数据抽象层,甚至可能演变为SIEM平台。历史表明,这类工具最终会被整合到更大的平台中。SIEM供应商需重新掌控数据摄入层以避免被边缘化。 2025-12-3 19:47:43 Author: raffy.ch(查看原文) 阅读量:12 收藏

Every few years in security, a category shows up that makes you think: “This market should have never existed.”
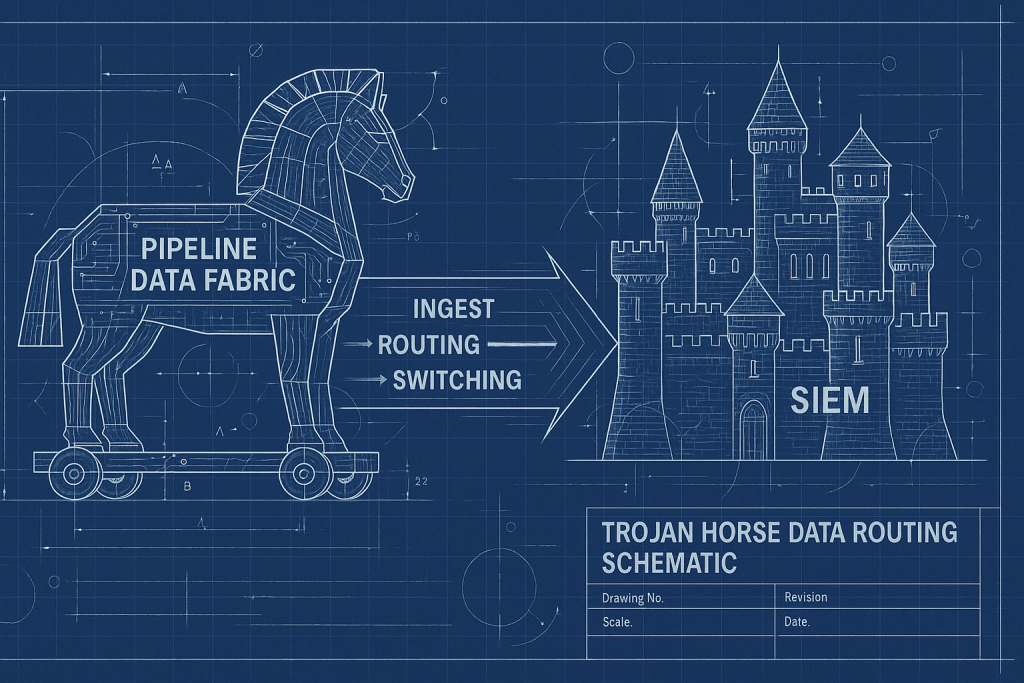
The “security data pipeline / data fabric / routing” universe is exactly that. Impressive companies in the space, smart founders, great execution and (thank you Observo!) great exists already. But the fact that there is a market here is the real indictment. This category is nothing more than a gap SIEM vendors left wide open. And the pipelines walked right in.
A Market That Shouldn’t Exist
Let’s be honest: Splunk, Elastic, Sentinel, Exabeam… they all ignored the ingest problem for too long. Cost, routing, shaping, tiering — none of it was solved cleanly. So Cribl et al solved it for them. But here’s the twist. By solving it, they also became the neutral abstraction layer. The thing sitting between customers and their SIEM. That layer is now the switching fabric. It isn’t just “optimize your Splunk bill.”
It’s:
- Reduce SIEM ingestion.
- Store everything in our “cheap” data lake.
- Oh, and here’s some lightweight analytics while you’re here.
- Or how about you go ahead and try out another SIEM? We can easily forward your data to multiple places while you evaluate moving away and then switching in a matter of hours.
That’s the Trojan Horse. You invite it in to help. And suddenly it controls the keys to the castle.
History Is Repeating Itself
We’ve seen this play before:
- UEBA -> first standalone products slowly morphed into adding data stores, analytics, and then became full SIEMs
- SOAR -> got absorbed into SIEM
- Ingest pipelines -> now becoming lakes -> and eventually a SIEM
Cribl already has Cribl Lake. Give it time and it becomes a SIEM-lite. Then a SIEM.
This is the cycle: Start as an add-on -> become indispensable -> become the platform.
We keep acting surprised. But it’s the same movie every time. And again, keep thinking about the switching costs. This layer enables every customer to easily evaluate new solutions and switch over fairly easily.
If You’re Splunk… I mean Cisco…
You’re one of the few players that can still turn this around — if you execute sharply and fast.
Here’s what Splunk must own again:
- Reclaim the ingest pipeline.
- Make cost the advantage, not the penalty.
- Federate search across data lakes natively. (I think you are almost there)
- Make tiering and reduction a first-class feature.
- Kill the routing layer through pure convenience.
- Figure out your real-time story. Crowdstrike is going strong on messaging how fast attackers act these days and a batch approach won’t work anymore.
If Splunk doesn’t own the control plane, Cribl will. And once you lose the control plane, you lose the customer. No matter how good your detection content is. Cisco gives Splunk a rare opportunity: distribution, integration leverage, and a chance to fix what was ignored for too long. But they can’t let another category grow unchecked. Not again.
My Take
Data pipeline products aren’t the problem. They are the symptom.
The problem is the complacency that let the ingest layer drift outside the SIEM in the first place. Because once a neutral fabric handles all your data, the SIEM becomes swappable. The next SIEM won’t start as a SIEM. It will start exactly where Cribl started; as a pipeline (Abstract Security, anyone)? That’s the Trojan Horse.
No comments yet.
如有侵权请联系:admin#unsafe.sh