嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头,直接写描述就行。首先,我需要仔细阅读并理解这篇文章的内容。 文章主要讲的是研究人员发现了一个名为Lazarus的网络攻击组织,他们利用伪装成IT外包人员的方式,渗透到西方公司的内部。这个组织与朝鲜的Chollima APT有关联。研究人员通过设置受控的沙盒环境,诱使攻击者进入其中,并记录下了他们的整个攻击过程,包括使用的工具和策略。 接下来,我需要提取关键信息:Lazarus组织、IT外包人员、朝鲜Chollima APT、沙盒环境、攻击过程记录、工具和策略。然后把这些信息浓缩到100字以内。 要注意用词简洁明了,避免复杂的句子结构。同时,要确保所有关键点都被涵盖:谁(Lazarus)、做什么(伪装IT外包)、关联(朝鲜Chollima)、方法(沙盒)、结果(记录攻击过程)。 最后,检查字数是否符合要求,并确保语句通顺自然。 </think> 研究人员发现 Lazarus 组织利用伪装成 IT 外包人员的方式渗透西方公司,并与朝鲜 Chollima APT 集团相关联。通过设置受控沙盒环境诱使攻击者进入,完整记录了其攻击过程及工具策略。 2025-12-3 13:21:17 Author: securityaffairs.com(查看原文) 阅读量:20 收藏
Researchers spotted Lazarus’s remote IT workers in action
Pierluigi Paganini
December 03, 2025

Researchers exposed a Lazarus scheme using remote IT workers tied to North Korea’s Famous Chollima APT group in a joint investigation.
Researchers filmed Lazarus APT group’s remote-worker scheme in action, uncovering a North Korean network of IT contractors linked to the Famous Chollima unit, TheHackerNews reported.
Recently, multiple cybersecurity firms and government agencies observed North Korea-linked APT groups, such as Chollima, using IT workers to infiltrate organizations across finance, crypto, healthcare, and engineering sectors.
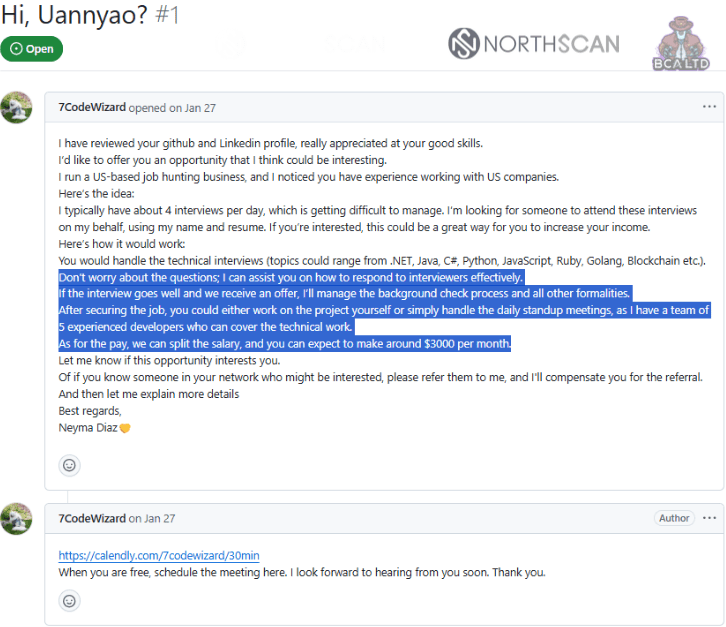
The joint investigation by the researcher Mauro Eldritch, NorthScan, and ANY.RUN uncovered one of North Korea’s most persistent infiltration schemes.
— BCA LTD (@BirminghamCyber) December 2, 2025🔥 After months inside #Lazarus’ fake hiring pipeline, we achieved something never seen before: the full Famous Chollima attack cycle captured on video, including their tools, tactics and targets.
🤝 This wouldn’t have been possible without our friends at ANY RUN (@anyrun_app)… pic.twitter.com/mDivdZdHfn
The researchers spotted Lazarus operators live for the first time by luring them into controlled sandbox environments disguised as real developer laptops. The operation began when NorthScan’s Heiner García posed as a U.S. developer targeted by a recruiter called “Aaron/Blaze,” who tried to hire him as a front to place North Korean IT workers inside Western companies.
— Mauro Eldritch 🏴☠️ (@MauroEldritch) December 2, 2025🇰🇵 Meet Aaron AKA Blaze, a #Lazarus recruiter.
💵 He offered 35% of a salary if we let his operators use our laptops "to work in" (infiltrate) Western companies.
▶️ We gave him ANYRUN sandboxes, recording everything they did.
⬇️ Full article below. Full disclosure on Dec 4. pic.twitter.com/iOjBVbBpWi

The scheme unfolded predictably: the operators grabbed or reused someone’s identity, used AI tools and shared answer sheets to pass interviews, worked remotely through the victim’s laptop, and sent all earnings back to North Korea. When Blaze pushed for full access, asking for the victim’s SSN, ID, LinkedIn, Gmail, and 24/7 control of the laptop, the team moved to phase two.
Instead of handing over a real machine, Mauro Eldritch from BCA LTD set up a “laptop farm” using ANY.RUN virtual machines. Each one looked like a genuine developer workstation, complete with browsing history, tools, and a U.S. residential proxy. The team could crash sessions, slow the connection, and capture every action the operators took, all without tipping them off.
Then the researchers analyzed the sandbox and found evidence of a simple but effective toolkit focused on stealing identities and taking over remote machines, not on planting malware. As soon as their Chrome profile synced, they began loading their usual tools.
They relied on AI job-automation apps like Simplify Copilot, AiApply, and Final Round AI to fill out applications and generate interview responses for them. They opened browser-based OTP generators (OTP.ee and Authenticator.cc) so they could handle the victim’s 2FA once they collected identity documents. They installed Google Remote Desktop and configured it through PowerShell with a fixed PIN, giving themselves ongoing control of the system.
They ran routine checks—dxdiag, systeminfo, whoami—to make sure the machine matched what they expected. Every connection traveled through Astrill VPN, a hallmark of earlier Lazarus operations.
In one session, the operator even typed a Notepad message asking the “developer” to upload their ID, SSN, and banking information, making their goal unmistakable: take over the victim’s identity and workstation without deploying any malware at all.
Building awareness and giving staff a safe way to report suspicious contacts helps stop threats early before they turn into full internal compromises.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, remote IT workers)
如有侵权请联系:admin#unsafe.sh