
Want to take a peek at your fellow cybersecurity practitioners’ thoughts on topics such as exposure 2025-11-28 14:0:0 Author: www.tenable.com(查看原文) 阅读量:10 收藏
Want to take a peek at your fellow cybersecurity practitioners’ thoughts on topics such as exposure response, patch management, and security tool sprawl? In case you missed them, we’re revisiting some of our most insightful webinar polls of 2025. Check out what your peers had to say!
Key takeaways
- Security teams are increasingly moving beyond traditional vulnerability management toward unified exposure management. This shift is driven by a need to break down operational silos, gain deeper risk context, and translate technical data into language that resonates with the C-suite and the board.
- To cope with the relentless volume of vulnerabilities, cyber professionals are shifting toward AI-powered, context-rich prioritization methods that help teams cut through the noise and focus on addressing the most critical business risks.
- Effective exposure response is pivoting away from reactive measures toward predictive strategies that prioritize vulnerabilities based on their specific potential impact on business operations.
Over the past year, we engaged with thousands of cybersecurity professionals during our webinar series. We asked probing questions about their daily operational realities, from the friction of credentialed scanning to the strategic adoption of AI.
We know that getting clued into how your peers are tackling common challenges can be extremely valuable. That’s why in this special edition of the Cybersecurity Snapshot we’re looking back at some of the most interesting webinar polls about exposure management, patch management and remediation prioritization.
We inquired about practitioners’ exposure-response strategies. We asked about their preferred prioritization approaches, and whether they plan to automate their remediation workflows. We posed questions about the tool sprawl problem.
We hope the resulting data set we’ve curated into six key insights offers you a valuable, candid view of these topics, which are top-of-mind these days for many security practitioners.
1 - Gauging maturity in exposure management
Webinar: “Security Without Silos: How To Gain Real Risk Insights With Unified Exposure Management.”
Moving from conventional vulnerability management to unified exposure management is a journey that requires cultural and operational shifts. In June, we polled attendees about the pressing security challenges driving them towards exposure management. We also asked them about their familiarity with, and their concerns about, exposure management.



The bottom line: Interest in exposure management is high, as organizations look to improve their security posture through, for example, deeper cyber risk context; improved workflows among teams; better communications with the C-suite; and a more integrated security stack.
See how unified exposure management works in the real world. Watch this webinar on-demand.
2 - Strategies for exposure response
Webinar: “Tenable Vulnerability Management Customer Update, June 2025”
In June, we asked over 140 attendees about their specific strategies for reacting to new exposures, and the related challenges they face. Check out what they said.


The key takeaway here is that reaction speed is irrelevant if you are focused on the wrong things. To properly respond to exposures, you need to filter out the noise and prioritize the vulnerabilities that pose the biggest business cyber risk to your organization. The data suggests that many teams are looking to move from a reactive "hair-on-fire" stance to a precise, predictive approach.
To learn about assessing this level of business cyber risk with a predictive prioritization approach, watch this on-demand webinar.
3 - Going from tool sprawl to an integrated security stack
Webinar: “Security Beyond Silos with Tenable + Vulcan Cyber: Unified Exposure Management”
Security tool sprawl is a known foe to efficiency. Filling up your stack with point tools that don’t play well with each other often leads to fragmented data rather than better visibility. In this February session, we dug into the number of security tools teams are juggling for tasks like asset discovery and, crucially, how integrated those tools actually are. Check out how they responded.
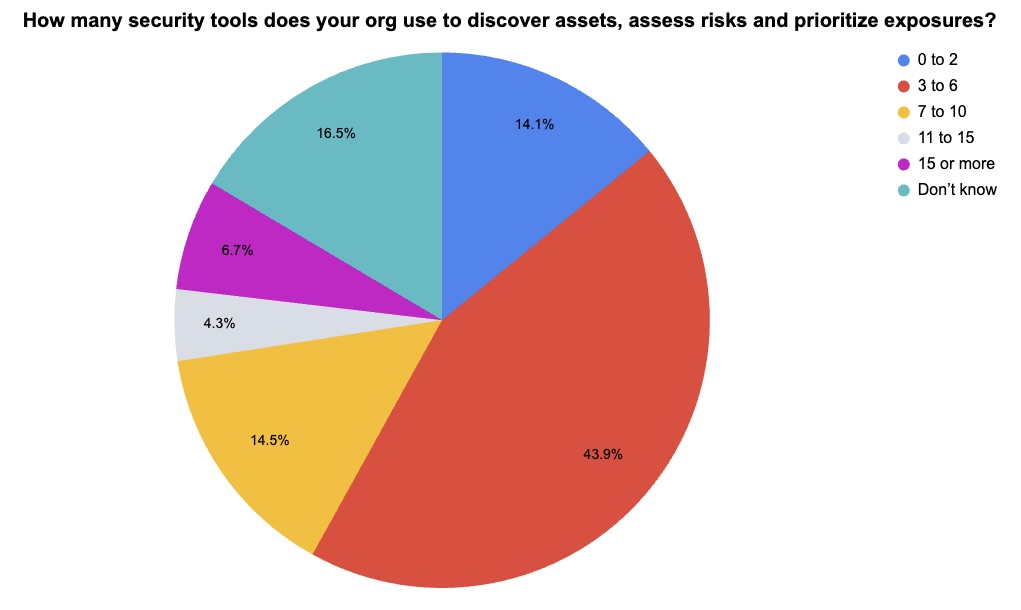

The results paint a picture of the "Frankenstein" stack. Many teams are struggling to get a single source of truth because their data is scattered across too many disjointed security products. This validates the industry's push toward consolidation. CISOs are hungry for unified visibility and enriched intelligence that can aggregate data from disparate sources into a coherent risk picture.
Interested in learning more about how to prioritize and address critical threats with unified visibility and enriched intelligence? Want to learn more about unified exposure management? Watch this webinar on-demand.
4 - How your peers prioritize vulnerabilities
Webinar: “Tenable Announces AI-Powered Breakthrough in Vulnerability Prioritization”
With the volume of CVEs growing daily, prioritization is critical. We asked attendees which criteria matter most to them and which AI-driven capabilities in Tenable’s Vulnerability Priority Rating (VPR) they expect to leverage.


Clearly, the security industry is ready for AI assistance. The days of relying solely on CVSS scores are fading. Context-rich approaches are transforming risk scoring, helping teams cut through the noise to focus on what actually matters.
Watch the on-demand webinar to learn how Tenable Vulnerability Management’s AI-powered, context-rich approach transforms risk scoring, enhances prioritization, improves efficiency and boosts clarity.
5 - The great debate: Credentialed vs. uncredentialed scanning
Webinar: “Tenable Vulnerability Management Customer Update, July 2025”
A persistent operational dilemma in vulnerability management is the trade-off between scan depth and administrative overhead. In July, we asked more than 100 attendees to weigh in on the pros and cons of authenticated scanning.


These results highlight the central issue at hand: Practitioners acknowledge that credentialed scans provide deeper, more accurate data, unlocking visibility into issues that uncredentialed scans simply miss. However, the overhead of managing credentials securely can be a major burden.
But there’s a way to bridge this gap: managed credentials. By centralizing and encrypting sensitive information, teams can significantly enhance security and reduce friction, removing the need to store credentials directly within scan policies.
Want to find out when and how to use managed credentials to get the best of both worlds? Watch this webinar on-demand.
6 - Fixing exposures: Patch management and remediation
Webinars: “Tenable Security Center Customer Update, December 2024” and “Tenable Vulnerability Management Customer Update, December 2024”
And, finally, there’s the "last mile" of security: remediating issues. We polled over 200 attendees on their direct involvement with patch management and their appetite for automating remediation.


This is often where friction is highest between security and IT operations. The good news is that the desire to improve efficiency through automation is high.
Watch the on-demand webinars to learn more about patch management, and about Tenable Vulnerability Management and Tenable Security Center.

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh