Researchers have discovered a new attack targeting Mac users. It lures them to a fake job websi 2025-11-26 14:11:26 Author: www.malwarebytes.com(查看原文) 阅读量:9 收藏
Researchers have discovered a new attack targeting Mac users. It lures them to a fake job website, then tricks them into downloading malware via a bogus software update.
The attackers pose as recruiters and contact people via LinkedIn, encouraging them to apply for a role. As part of the application process, victims are required to record a video introduction and upload it to a special website.
On that website, visitors are tricked into installing a so-called update for FFmpeg media file-processing software which is, in reality, a backdoor. This method, known as the Contagious Interview campaign, points to the Democratic People’s Republic of Korea (DPRK).
Contagious Interview is an illicit job-platform campaign that targets job seekers with social engineering tactics. The actors impersonate well-known brands and actively recruit software developers, artificial intelligence researchers, cryptocurrency professionals, and candidates for both technical and non-technical roles.
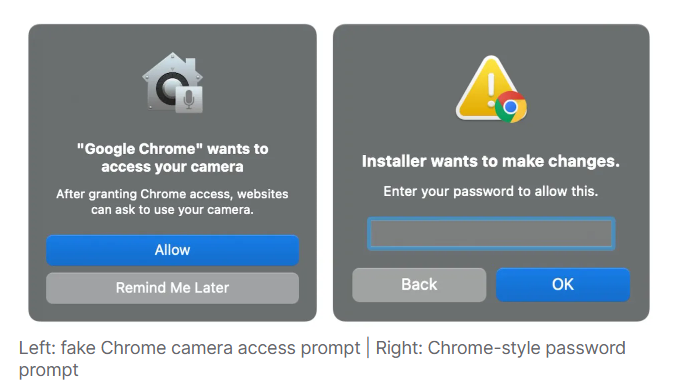
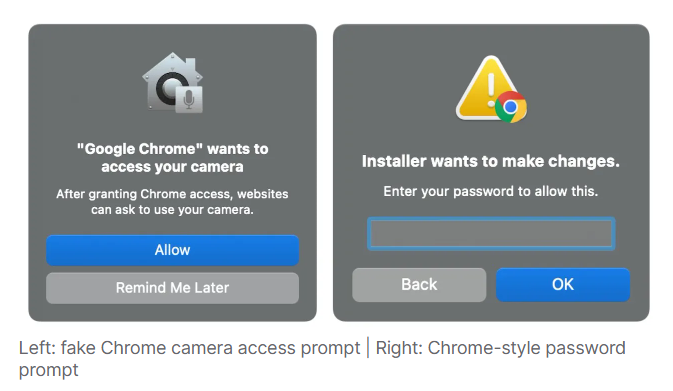
The malicious website first asks the victim to complete a “job assessment.” When the applicant tries to record a video, the site claims that access to the camera or microphone is blocked. To “fix” it, the site prompts the user to download an “update” for FFmpeg.
Much like in ClickFix attacks, victims are given a curl command to run in their Terminal. That command downloads a script which ultimately installs a backdoor onto their system. A “decoy” application then appears with a window styled to look like Chrome, telling the user Chrome needs camera access. Next, a window prompts for the user’s password, which, once entered, is sent to the attackers via Dropbox.
The end-goal of the attackers is Flexible Ferret, a multi-stage macOS malware chain active since early 2025. Here’s what it does and why it’s dangerous for affected Macs and users:
After stealing the password, the malware immediately establishes persistence by creating a LaunchAgent. This ensures it reloads every time the user logs in, giving attackers long-term, covert access to the infected Mac.
FlexibleFerret’s core payload is a Go-based backdoor. It enables attackers to:
- Collect detailed information about the victim’s device and environment
- Upload and download files
- Execute shell commands (providing full system control)
- Extract Chrome browser profile data
- Automate additional credential and data theft
Basically, this means the infected Mac becomes part of a remote-controlled botnet with direct access for cybercriminals.
How to stay safe
While this campaign targets Mac users, that doesn’t mean Windows users are safe. The same lure is used, but the attacker is known to use the information stealer InvisibleFerret against Windows users.
The best way to stay safe is to be able to recognize attacks like these, but there are some other things you can do.
- Always keep your operating system, software, and security tools updated regularly with the latest patches to close vulnerabilities.
- Do not follow instructions to execute code on your machine that you don’t fully understand. Never run code or commands copied from websites, emails, or messages unless you trust the source and understand the action’s purpose. Verify instructions independently. If a website tells you to execute a command or perform a technical action, check through official documentation or contact support before proceeding.
- Use a real-time anti-malware solution with a web protection component.
- Be extremely cautious with unsolicited communications, especially those inviting you to meetings or requesting software installs or updates; verify the sender and context independently.
- Avoid clicking on links or downloading attachments from unknown or unexpected sources. Verify their authenticity first.
- Compare the URL in the browser’s address bar to what you’re expecting.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
如有侵权请联系:admin#unsafe.sh