
2025-11-24 17:15:23 Author: securityboulevard.com(查看原文) 阅读量:6 收藏
👉
TL;DR: A new wave of the Shai-Hulud supply chain attack targeting NPM packages, dubbed “The Second Coming” by the threat actors.
Key Numbers:
– 621 unique NPM packages infected
– 14,206 secrets exposed across 487 GitHub organizations
– 2,485 secrets still valid and publicly exposed
– 20% of compromised machines are GitHub runners (CI/CD infrastructure)

Two months after the initial Shai-Hulud supply chain attack in September, the threat actors have returned with a new, updated campaign they refer to as "The Second Coming". It leverages the same worm-like propagation mechanism observed previously, but with updated tactics, probably learnt from their initial mistakes.
Shai-Hulud: A Persistent Secret Leaking Campaign
On September 15, a new supply chain attack was identified that targeted the @ctrl/tinycolor and 150 other NPM packages. The attack scenario was similar to the one used in the s1ngularity and GhostActions campaigns. The threat actors combined a local environment secrets extraction with a malicious GitHub actions workflow
 GitGuardian Blog – Take Control of Your Secrets SecurityGaetan Ferry
GitGuardian Blog – Take Control of Your Secrets SecurityGaetan Ferry

As of November 24th, 17:30 pm CET, 621 unique NPM packages have been infected by the worm.
In the first campaign, CI/CD secrets were exfiltrated to a public internet endpoint that quickly got rate-limited. In this new iteration, they are directly exfiltrated to GitHub repositories created using the stolen credentials.
These GitHub repositories could be identified using several patterns:
- the description is Sha1-Hulud: The Second Coming
- the name is a randomly generated string of 18 characters such as zl8cgwrxf1ufhiufxq or bq1g6jmnju2xpuii6u
- the filename cloud.json, containing a JSON document with the detected AWS, Azure, and GCP secrets
- the filename contents.json, containing a JSON document with system information, the token GitHub used for exfiltration, and its associated metadata such as the login or the email
- the filename environment.json, containing a JSON document with environment variables
- the filename actionsSecrets.json, containing a JSON document with the secrets stolen from GitHub actions
- the filename truffleSecrets.json, containing a JSON document with the secrets stolen locally
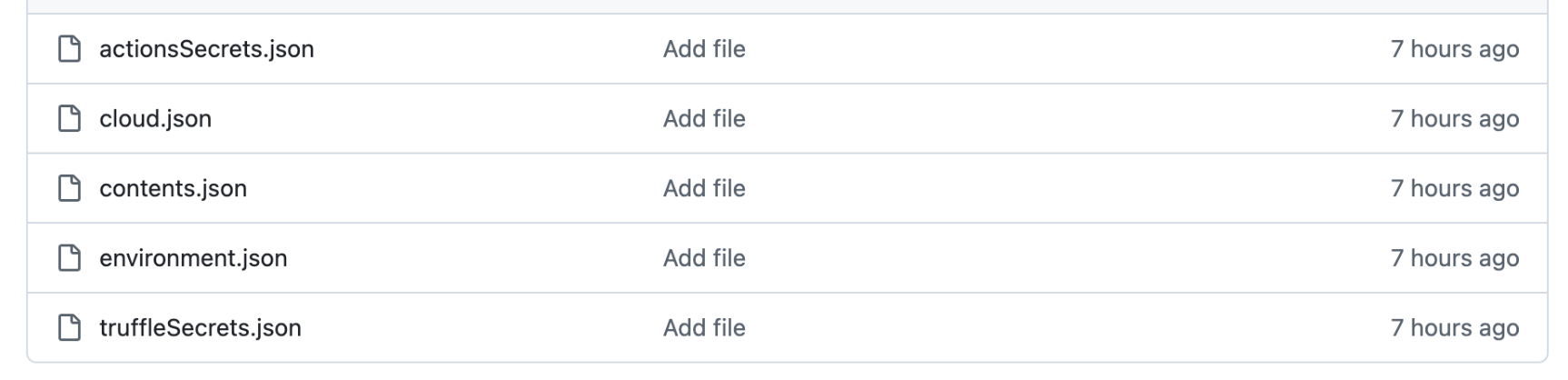
These files are added in different commits that happen one after another. Note that actionsSecrets.json and truffleSecrets.json might not exist depending on the detected secrets. On the contrary, the environment.json file, containing the dump of the victim’s machine environment, is present in all observed repositories.
This file is particularly interesting as it provides important information about the environments that were affected. For example, the variables named GITLAB_CI or RUNNER_TAG indicate that not only developers were targeted but also CI infrastructures, exposing private internal services.
From the data we observed in the environment.json file, about 20% of the compromised machines are GitHub runners. This would indicate the payload was executed during the build of a project using a compromised package as a dependency.
At the time of writing, 487 GitHub organizations were leaking 17,853 unique repositories containing either actionsSecrets.json or truffleSecrets.json, 824 contained both, and 16,265 only contained truffleSecrets.json.
In total, we identified 14,206 secrets among which 2,485 were still valid and publicly exposed on GitHub. The most leaked valid secrets are GitHub tokens, Slack Webhooks, Claude API Keys, and cloud-related credentials such as AWS or Azure.

We are currently monitoring the situation where more GitHub repositories are being created and exposing more secrets. Following this initial investigation, we began identifying the affected companies, and started to alert them individually.
However, building on our knowledge of the recent campaigns, we can expect more to happen in this campaign in the coming days. Especially, a lot of recent campaigns included a second phase where private repositories turned public, exposing more secrets. We should stay alert in case such a second phase occurs in this new campaign.
The evolution from the initial Shai-Hulud campaign to "The Second Coming" shows how supply chain attacks are getting smarter. Threat actors are learning from past campaigns – their own and others' – and adapting their tactics accordingly. Moving from easily blocked endpoints to using stolen credentials for exfiltration through legitimate GitHub repositories is a clear example of this learning in action.
This campaign also confirms what we already know: secrets are the weakest link in modern software supply chains. With over 14,000 secrets exposed and 2,485 still valid and 20% of compromised machines being GitHub runners, the attack hit both developer workstations and CI/CD pipelines. As supply chains become more interconnected, effective secrets management isn't just a security best practice anymore. It's a necessity.
*** This is a Security Bloggers Network syndicated blog from GitGuardian Blog - Take Control of Your Secrets Security authored by Guillaume Valadon. Read the original post at: https://blog.gitguardian.com/shai-hulud-2/
如有侵权请联系:admin#unsafe.sh