On April 18, 2024, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau 2025-11-18 19:53:44 Author: securityboulevard.com(查看原文) 阅读量:25 收藏
On April 18, 2024, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Netherlands’ National Cyber Security Centre (NCSC-NL) released a joint Cybersecurity Advisory (CSA) that disseminates known Tactics, Techniques, and Procedures (TTPs) and Indicators of Compromise (IOCs) associated with Akira ransomware, identified through FBI investigations and trusted third party reporting as recently as February 2024.
On November 13, 2025, CISA, the FBI, the Department of Defense Cyber Crime Center (DC3), the Department of Health and Human Services (HHS), Europol’s European Cybercrime Centre (EC3), France’s Office Anti-Cybercriminalité (OFAC), Germany’s Generalstaatsanwaltschaft (GStA)Karlsruhe,
This joint CSA is a continuation of CISA’s ongoing #StopRansomware effort to arm defenders with the intelligence they need to combat different ransomware variants and ransomware threat actors.
Akira is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model, enabling multiple adversaries to deploy it in exchange for a share of the proceeds from successful compromises. It emerged in March 2023 and is reportedly unrelated to a previous ransomware strain of the same name that was active in 2017, despite both appending the .akira extension to encrypted files.
According to a report published by the Arctic Wolf Labs Team in July 2023, Akira has been linked to Conti ransomware due to code similarities, including string obfuscation, file encryption routines, and the exclusion of specific file extensions. The report states that when Conti’s source code was leaked, multiple adversaries repurposed it to develop or tweak their ransomware code, rendering it even more challenging to trace ransomware families back to Conti’s operators.
Akira’s operators manage a TOR-based Dedicated Leak Site (DLS) (.onion domain), where victims are instructed to use a unique identifier from the ransom message to identify themselves and initiate negotiations. If ransom demands are not met, the group will use this leak site to list victims and any stolen information, as Akira exfiltrates sensitive information before encrypting files and devices. According to reports, Akira operators provide victims the option to pay for either file decryption or data deletion rather than being forced to pay for both. Reported ransom demands range from 200,000 USD to over 4 million USD.
AttackIQ has released an updated attack graph to include these new behaviors exhibited by Akira ransomware to help customers validate their security controls and their ability to defend against this determined adversary.
Validating your security program performance against these behaviors is vital to reducing risk. By using this updated attack graph in the AttackIQ Adversarial Exposure Validation (AEV) Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with Akira ransomware.
- Assess their security posture against an opportunistic adversary, which does not discriminate when it comes to selecting its targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the groups currently focused on ransomware activities.
[CISA AA24-109A] #StopRansomware: Akira Ransomware

This attack graph emulates the post-compromise Tactics, Techniques, and Procedures (TTPs) exhibited by Akira ransomware affiliates during their recent activities. It is based on the updated Cybersecurity Advisory (CSA) released by CISA on November 13, 2025, and supported by reporting from Darktrace (September 13, 2023), Trend Micro (October 5, 2023), and Trellix (November 29, 2023).
To highlight updates from the previous version of the emulation, newly introduced scenarios are labeled with the “Added!” prefix, ensuring clear and easy identification.
Persistence & Discovery – Local and Network Reconnaissance
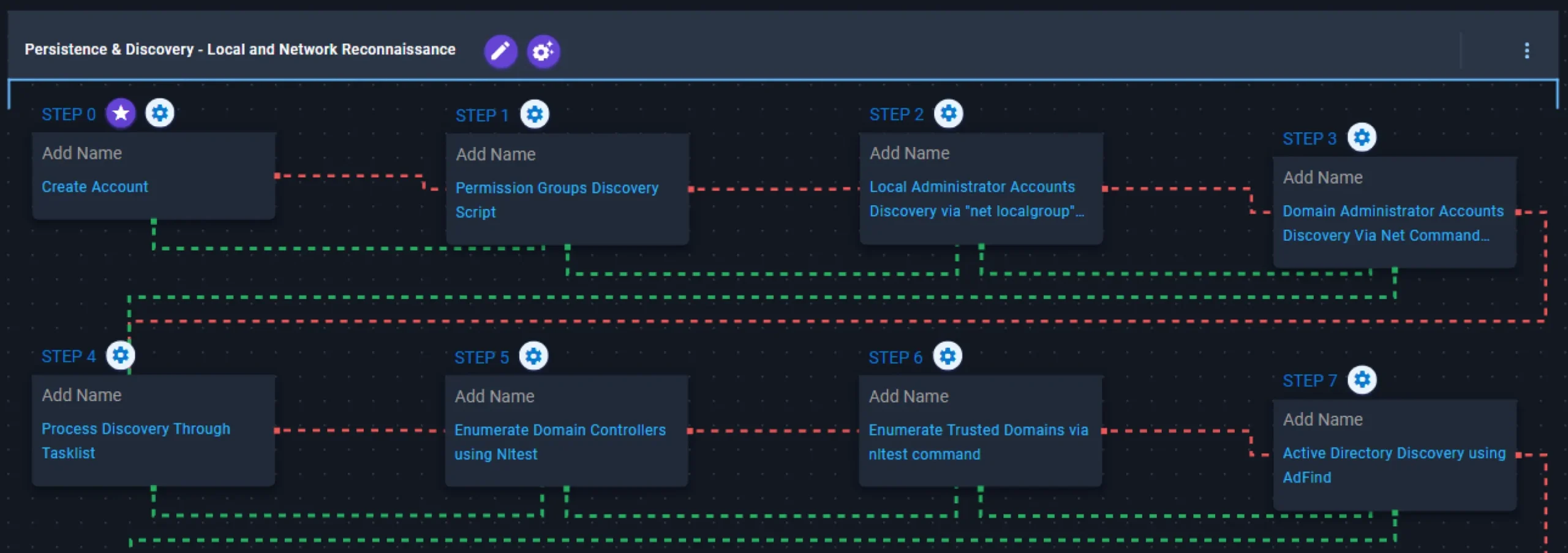
This stage begins immediately after the adversary gains access via a brute-force attack over Remote Desktop Protocol (RDP). Once accomplished, it attempts to establish persistence by creating a local account named itadm.
Subsequently, it collects information on permission groups as well as local and domain administrative accounts using the net utility. It then enumerates running processes via the tasklist command, identifies domain controllers and trusted domains using nltest, and conducts Active Directory reconnaissance through the AdFind utility.
Create Account: Local Account (T1136.001): This scenario will create a new account with the name itadm using net user.
Added! Permission Groups Discovery Script (T1069): This scenario will enumerate permission groups using the net localgroup and net group /domain commands.
Local Administrator Accounts Discovery via “net localgroup” Command (T1069.001): This scenario executes the net localgroup administrators command to enumerate a set of users with administration privileges.
Local Administrator Accounts Discovery via “net localgroup” Command (T1069.001): This scenario executes the net group "Domain Admins" /domain and net group "Enterprise Admins" /domain commands to enumerate a set of privileged domain system accounts.
Process Discovery Through Tasklist (T1057): This scenario executes the Window’s built-in tasklist command to enumerate running processes.
Enumerate Domain Controllers using Nltest (T1018): This scenario executes the nltest /parentdomain and nltest /dclist commands to gather a list of domain controllers associated with a domain.
Enumerate Trusted Domains via nltest command (T1482): This scenario executes the nltest /trusted_domains command to retrieve a list of trusted Active Directory domains associated with the host.
Active Directory Discovery using AdFind (T1018): This scenario leverages the AdFind utility to discover details about the Active Directory configuration including accounts, groups, computers, and subnets.
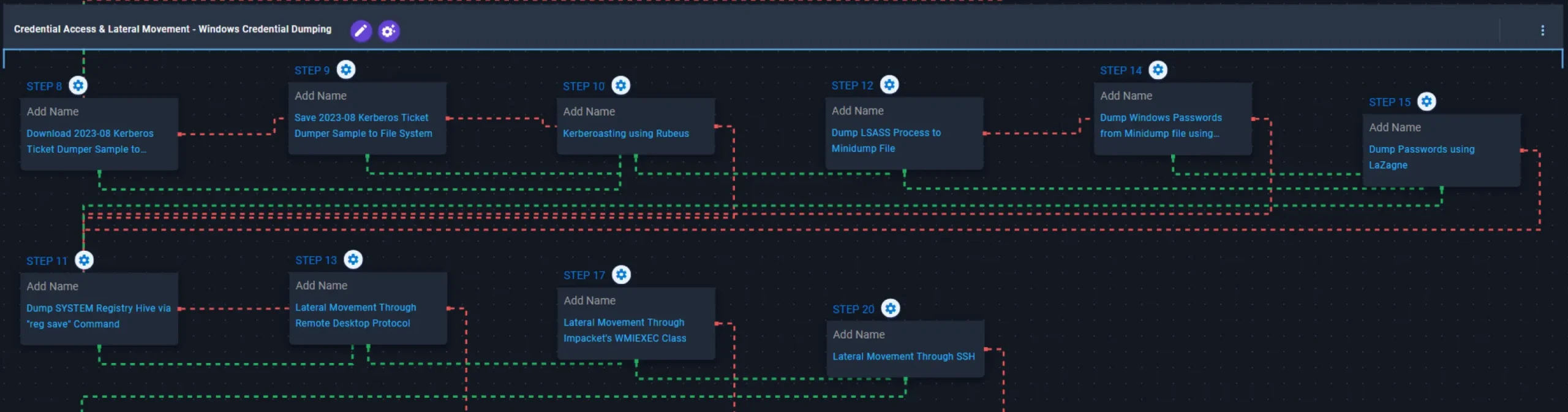
Credential Access & Lateral Movement – Windows Credential Dumping

This stage begins with the deployment of a Kerberos ticket dumper to perform Kerberoasting in an attempt to escalate privileges. If Kerberoasting fails, it attempts to dump the Windows Local Security Authority Subsystem Service (LSASS) process memory into a Minidump file using the comsvcs.dll library, subsequently leveraging Mimikatz to extract credentials from it. If Mimikatz fails, it falls back to credential extraction via the LaZagne utility. Once completed, it proceeds to export the SYSTEM registry hive through the reg save command.
With the acquired credentials, it attempts to move laterally to previously identified remotely accessible systems via Remote Desktop Protocol (RDP). If RDP communication is blocked, it switches to Impacket’s WMIEXEC for remote command execution. If this method also fails, it ultimately resorts to lateral movement through Secure Shell (SSH).
2023-08 Kerberos Ticket Dumper (T1105): The Kerberos Ticket Dumper Sample (SHA256: 5e1e3bf6999126ae4aa52146280fdb913912632e8bac4f54e98c58821a307d32) is downloaded and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Kerberoasting using Rubeus (T1558.003): This scenario will implement the Kerberoasting technique using the Rubeus utility, which allows an attacker to attempt to extract password hashes for accounts using their Service Principal Name (SPN) ticket.
Dump LSASS Process to Minidump File (T1003.001): This scenario executes rundll32.exe with comsvcs.dll to call the MiniDump export that will dump the LSASS process memory to disk. This process is used for enforcing security policy on the system and contains many privileged tokens and accounts.
OS Credential Dumping: LSASS Memory (T1003.001): This scenario executes the Mimikatz utility to extract credentials from a specified MiniDump file.
OS Credential Dumping (T1003): This scenario employs the open-source tool LaZagne to extract all available credentials from the compromised environment.
Added! Dump SYSTEM Registry Hive via “reg save” Command (T1003.002): This scenario attempts to save a copy of the HKLM\SYSTEM registry hive to a temporary file by executing the reg save command.
Lateral Movement Through Remote Desktop Protocol (T1021.001): This scenario attempts to remotely connect to an accessible system via Remote Desktop Protocol (RDP), a built-in remote access Windows utility.
Added! Lateral Movement Through Impacket’s WMIEXEC Class (T1047): This scenario employs the Impacket utility to execute the WMIEXEC class, to remotely connect to an accessible system via the WMI protocol.
Added! Lateral Movement Through SSH (T1021.004): This scenario attempts to remotely connect to an accessible system via Secure Shell (SSH).
Discovery – Akira Ransomware Deployment and System Reconnaissance

This stage begins with the deployment of the Akira ransomware, which, once operational, performs initial environment reconnaissance to gather information regarding the underlying hardware, operating system version, and the system’s Globally Unique Identifier (GUID) of the system. Following reconnaissance, it proceeds to collect files from the system using the esentutl.exe utility, leveraging its database extraction capabilities to access and copy targeted data.
2024-02 Akira Ransomware (T1105): The 2024-02 Akira Ransomware Sample (SHA256: 2727c73f3069457e9ad2197b3cda25aec864a2ab8da3c2790264d06e13d45c3d) is downloaded and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows API call to retrieve information associated to the system.
Added! Process Discovery via Native API (T1057): This scenario uses Windows API to receive a list of running processes by calling CreateToolhelp32Snapshot and iterating through each process object with Process32FirstW and Process32NextW.
Added! Obtain MachineGUID from Cryptography Registry Key using “reg query” Command (T1012): This scenario queries the MachineGUID value located within the HKLM\SOFTWARE\Microsoft\Cryptography registry key which contains the unique identifier of the system.
Copy a file using “esentutl.exe” Script (T1005): This scenario executes the esentutl.exe utility to collect files from the system, leveraging its database extraction capabilities to access and copy targeted data.
Discovery & Impact – Akira Ransomware Encryption
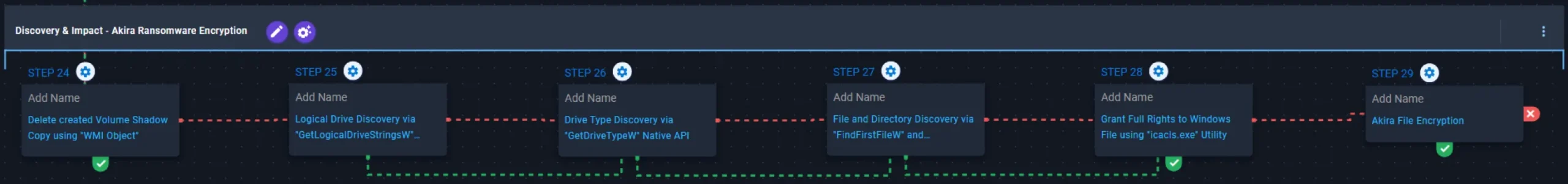
This stage begins with the deletion of Volume Shadow Copies through Windows Management Instrumentation (WMI) objects. It then identifies available drives using the GetLogicalDriveStringsW API and determines their types via GetDriveTypeW, followed by filesystem traversal and file enumeration through the FindFirstFileW and FindNextFileW APIs. After enumeration, it leverages icacls.exe to grant full access rights to Windows files, ensuring they can be successfully processed during encryption. Finally, Akira encrypts the identified files using a combination of ChaCha20 for file encryption with RSA-4096 for key encryption.
Delete created Volume Shadow Copy using “WMI Object” (T1490): This scenario executes the Get-WMIObject Win32_ShadowCopy PowerShell command to delete a Volume Shadow Copy created by the emulation.
Added! Logical Drive Discovery via “GetLogicalDriveStringsW” Native API (T1680): This scenario executes the GetLogicalDriveStringsW Windows API call to retrieve information regarding the system’s physical drives.
Added! Drive Type Discovery via “GetDriveTypeW” Native API (T1680): This scenario retrieves information about the system’s physical disks by executing the GetDriveTypeW Windows API call.
Added! File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Added! Windows File and Directory Permissions Modification (T1222.001): This scenario employs the icacls.exe utility to modify file permissions to grant explicit Full (F) rights on a generated temporary file.
Added! Akira File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Akira ransomware.
Opportunities to Expand Emulation Capabilities
In addition to the updated attack graph, AttackIQ recommends the following scenarios to extend the emulation of the capabilities exhibited by Akira ransomware:
- Password Brute-Force (T1110): This scenario can be configured to attempt to brute login using Remote Desktop Protocol (RDP) on remote systems with a username and password dictionary.
- Dump Active Directory Database using ntdsutil.exe (T1003.003): This scenario attempts to access or create a copy of the Active Directory domain database (
NTDS.dit) by leveraging the built-inntdsutil.exeWindows utility. This database enables the adversary to extract credential material and gather extensive information about domain members, including devices, user accounts, group memberships, and associated access rights.
Wrap-up
In summary, this updated attack graph will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by Akira ransomware operators. With data generated from continuous testing and use of these assessment templates, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.
如有侵权请联系:admin#unsafe.sh
