AI made it cheap to write code. Running it could cost you more than you think.
A consistent pattern and a new challenge are starting to emerge among development teams leveraging AI to generate code. Teams celebrate a bump in efficiency and then watch PR queues swell, security backlogs grow, and delivery slow.
The bottleneck is not keystrokes; it’s our ability to secure the code as fast as it’s being generated. If code quality and risk posture are decided after the commit, you pay a “rework tax” that multiplies as the volume of code rises.
This tax is why pre-commit agentic AI security is crucial: When AI is in the loop, helping write “live” code, Agentic AppSec AI doesn’t wait to comment on a pull request after a scan finishes, but rather, ‘sits’ together with the developer while code is being written to prevent mistakes and ship secure changes on the first try.
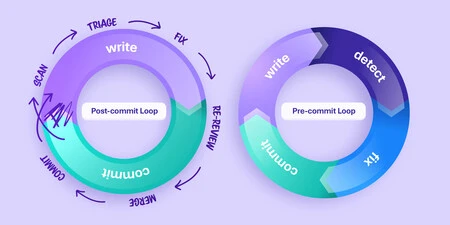
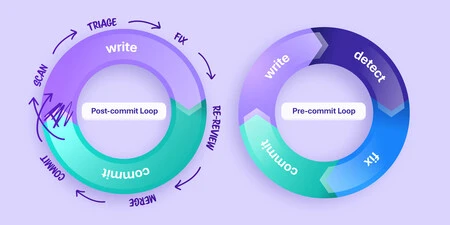
Why post-commit breaks down at AI speed
Post-commit assistance still has value, but it is reactive by design. DORA reports slower throughput and weaker stability as GenAI use climbs.
More unchecked code enters the pipeline without early prevention, which multiplies PR loops, review delays, and rework.
When issues show up in PRs or build results, you trigger a long chain of handoffs. The developer has already context-switched to the next task. Now they must jump back into the previous code, recreate the problem, debate fix approaches in comments, run again, and wait for another review. Multiply that by hundreds of generated code snippets, upgrades, and merges.
Four problems show up fast:
- Rework tax: Every hop in the loop adds time. A simple fix can take hours or days once you include triage and re-review.
- Context loss: The best moment to fix a bug is right when the developer wrote it. Minutes later is worse. Days later ancient history for the developer, and requires more resources and attention.
- Flooded PRs: Comment storms and scan noise delay merges and sap energy. Engineers start to treat security as a second inbox.
- Debt by default: If the team is judged by throughput, issues get deferred. Debt rises quietly until it is loud and costly.
What is pre-commit agentic security?
Think of an AI teammate that prevents risk before code ever leaves the developer’s workstation. It runs where the developer works, understands the file and project context, and gives fixes that are specific to the code that is being edited.
It also enforces a light gate at commit time, so obviously insecure changes do not enter the pipeline.
That is the job description for our Developer Assist agent inside Checkmarx One Assist. Here is how it maps to real developer moments:
- Real-time protection while typing. The agent detects vulnerabilities early and offers targeted fixes that fit the code style and framework in use. The fix cycle shrinks from weeks to minutes because the developer never needs to leave the IDE.
- Find and fix breaking changes during upgrades. The Agent automates dependency impact analysis, highlights API differences between versions, and suggests the code updates required. Upgrades move from risky all-hands moments to routine work.
- Smarter SCA in the IDE. The agent surfaces license and risk information for any chosen package, flags malicious or suspect options, and recommends safer alternatives before you import.
- Secrets detection and remediation. The agent catches leaked credentials as you write and guides safe rotation and handling.
- Context-aware fix suggestions. Not generic snippets, but fixes that align to the specific sink, source, and data flow in your codebase.
- Pre-commit protection. Lightweight checks at commit time stop insecure changes at the source so fewer issues hit CI.
Pre-commit Assistant Translated into Numbers: Time and Efficiency
Here is a simple back-of-the-napkin example. Say your team upgrades a core package from v3 to v4. It is referenced in 12 files with about 30 call sites. Here is what that looks like three different ways.
Manual path
- Find every usage with code search, confirm each reference, and map the blast radius. About 45 minutes.
- Read release notes and migration guides, compare old and new APIs, and sketch the refactor plan. About 60 minutes.
- Update imports, fix each call si te, re-run tests, and chase compile errors. About 150 minutes.
- Open a PR, wait on CI, address comments, and re-run. About 90 minutes.
Total time about 5.75 hours. At 100 dollars per hour that is roughly 575 dollars for one upgrade.
Post-commit assistant path
- Commit the upgrade, let your build pipeline flag breakages, then accept suggested fixes and iterate in the PR.
- You still pay the triage and re-review tax, but some edits go faster.
Total time about 3.5 hours. About 350 dollars.
Pre-commit with Developer Assist and Safe Refactor
- Select the target version in the IDE. Safe Refactor analyzes the codebase, lists breaking changes across the 12 files, and proposes concrete edits at each call site.
- Apply edits, compile locally, run tests, and commit once.
Total time about 1.5 hours. About 150 dollars.
Numbers will vary by repo and library, but the pattern is consistent. Prevention compresses loops. Short loops keep throughput and stability. Long loops add risk, noise, and cost.
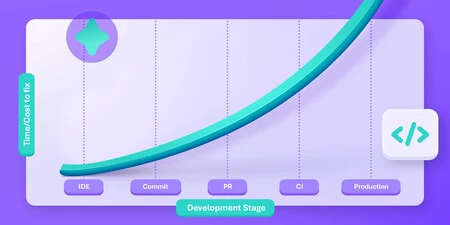
Where post-commit still matters
Pre-commit should be the first line of defense, not the only line. You still want pipeline and PR scans as a fail-safe and as proof that standards were met. You still need portfolio-level visibility so AppSec and engineering leaders can decide what matters most across applications, not just inside one IDE session.
In our world, this is where ASPM comes in. It aggregates and correlates findings, applies organizational risk logic, and feeds those priorities back to developers so the pre-commit agent is guided by what the business cares about.
A quick tour of developer workflows that benefit immediately
- Writing new code: Real-time detection and context-aware fixes keep issues from ever leaving the editor.
- Adding or upgrading a dependency: SCA capabilities in the IDE allow developers to evaluate the package choice in the moment and helps avoid license and security landmines. If you do upgrade, the Safe Refactor feature analyzes blast radius, highlights breaking API changes, and proposes code edits that compile.
- Handling credentials: Catch and remove 170+ types of exposed credentials (API keys, tokens, SSH keys, encryption keys, etc.) before commit.
- Hitting commit: The agent enforces a light, fast gate that prevents known bad changes. Your pipelines see less noise. PRs merge faster.
What to look for if you are a CISO or head of engineering
If you are comparing agentic approaches, use a checklist that prioritizes prevention and adoption.
- Does the agent work pre-commit in the IDE, not only after scans finish?
- Are fixes context aware and specific to the codebase, not generic snippets?
- Does it bring ASPM priorities into the IDE, so developers fix what matters most?
- Can it automate package upgrade remediation by analyzing dependency impact? and suggesting code changes
- What is the false positive rate and how quickly can developers accept or dismiss results?
- Does pre-commit protection reduce PR noise and shorten time to merge in real projects?

What changes when prevention becomes the default
Teams that move security left in a meaningful way report quieter PRs, faster merges, and fewer fire drills. Developers keep the efficiency they were promised by AI because they spend less time reworking code that already landed. AppSec shifts from traffic cop to coach. Leaders get cleaner telemetry and a risk posture that improves as output scales.
That is the outcome we are aiming for with Checkmarx One Assist and the Developer Assist agent. Keep the second line of defense strong but win the battle where it starts. At the keyboard. Before the commit.