
Every developer knows the scenario: you're deep in flow, building features, when a security tea 2025-11-17 10:25:29 Author: securityboulevard.com(查看原文) 阅读量:2 收藏

Every developer knows the scenario: you're deep in flow, building features, when a security team ticket with a critical alert lands in your backlog. A critical vulnerability has been discovered in your code. Now you need to stop your current task, dive back into the old code, and fix this critical vulnerability, rather than building your new feature and breaking your momentum entirely.
This happens several times weekly across development teams. The vulnerability can be exploited at any time by attackers, so the urgency is justified. But the hidden cost of context-switching is massive.
When a security alert arrives, developers face this workflow:
- Stop their current work
- Switch to the security team’s provided ticket. Understand the vulnerability context (which sometimes requires additional login into the security tool that found the vuln)
- Switch back to their IDE
- Hunt for the vulnerable code
- Research the fix
- Implement and test the remediation
This context-switching isn’t just annoying, it’s expensive. According to a study by the University of California, Irvine, it takes an average of 23 minutes and 15 seconds to get back to the task after an interruption.
The traditional workflow between security and engineering teams compounds this problem. Security teams identify vulnerabilities in dedicated platforms such as SAST tools, dependency scanners, and penetration testing reports. They file tickets in Jira, send emails, or post alerts in Slack. Each notification triggers the same disruptive cycle.
As Koen Hendrix, Director of Product Security at Zendesk, described the challenge:
“Engineers have a thousand things to do or a hundred things to do every week and they got time for one or two security things. How do we prioritize that? What do we throw on their plate? And how well are we able to support that and get a problem at the time solved? That's, yeah, that's our perpetual equation that we try to balance out every single day.”
This is the key issue of security work: engineers have many priorities on their plate, and security is just one of them. They must constantly juggle all these items. The question isn't whether developers can fix security issues; it's whether we're giving them a workflow that lets them do it efficiently.
What if we could eliminate context switching entirely? What if security data came directly to developers, in the tools they already use, with AI-powered guidance ready to implement? What if instead of 2 or 5 security fixes per week, it could be more, and all, without the frustration of developers in the environment where they “live”?
Escape MCP: Security Meets the Model Context Protocol
What if vulnerability data came to the developer, instead of the other way around? In 2025, most developers will have already built AI-coding assistants in their IDEs. So we built Escape MCP to help connect the dots between where developers live - in their already AI-powered IDE and security context.
What is Escape MCP?
Think of Escape MCP as a universal translator between two worlds:
- Security World: Your Escape platform, with all its scan results, vulnerability data, and security intelligence
- Developer World: AI coding assistants like Claude Code or Cursor, where developers actually write code
Escape MCP is the bridge between Security and the Developer world. It implements Anthropic's Model Context Protocol (MCP) , an open standard that lets AI assistants securely access external data sources. Instead of developers hunting through the dashboard, they simply ask:
- “Give me all the issues of the project”
- “How to fix the SQLi in the endpoint /XX/YY ?”
Escape MCP does three things: first, connect the Escape platform to an AI assistant; second, make vulnerability data instantly queryable via natural language; and third, enable AI to suggest fixes with full security context.
How to access the Escape MCP
The Escape MCP is deployed on https://mcp.escape.tech/mcp and you can easily access it using your Escape API key in your User Settings.
Setting up the environment
Let's set up the environment in Visual Studio Code.
💡
This process also works in many other IDEs, such as Cursor.
Step 1: Get your API Key
First, navigate to your User settings in the Escape dashboard and copy your API KEY.
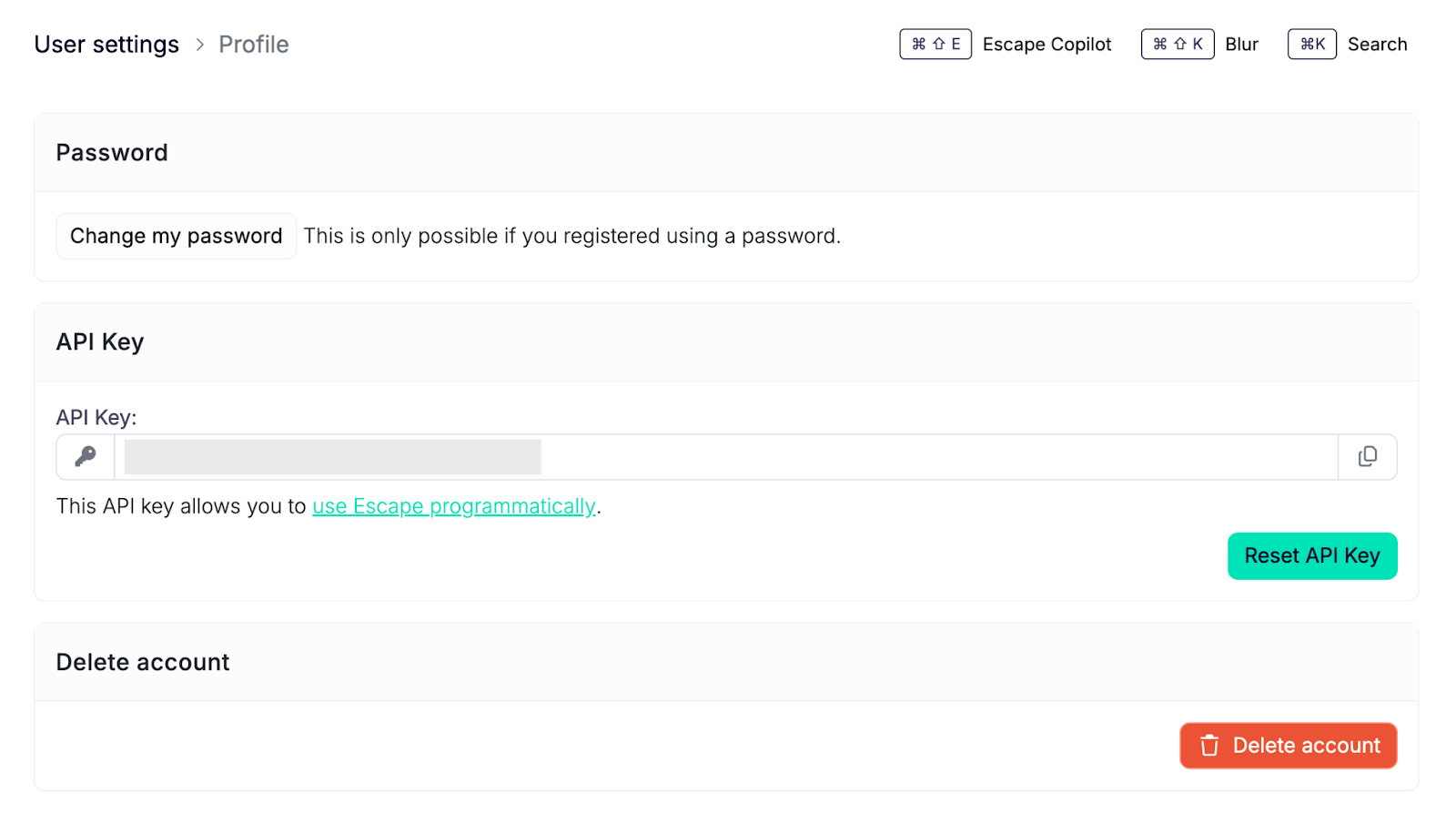
⚠️
Keep this API KEY secure.
Step 2: Configure the MCP Server in VS Code
Visual Studio Code’s documentation provides clear instructions for adding an MCP server.
To connect VS Code to Escape MCP, you need to add the MCP server configuration to your workspace.
Create or edit .vscode/mcp.json in your workspace:
{
"servers": {
"escape-mcp": {
"type": "http",
"url": "https://mcp.escape.tech/mcp",
"headers" : {
"X-ESCAPE-API-KEY":"your_api_key"
}
}
}
}
Replace your_api_key with the API key you copied in step 1.
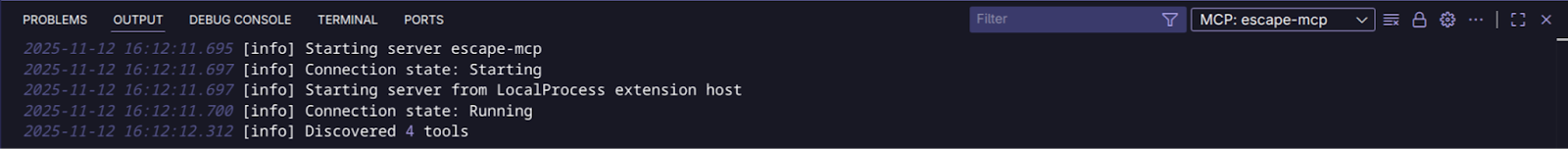
Step 3: Verify the connection
Once configured, restart VS Code or reload your window. You should see Escape MCP available in your AI assistant’s tool list.
Fixing Vulnerabilities in an Open-Source Application: Using OWASP Juice Shop as a Target
For the purpose of this guide, we chose one application so we could show exactly how to implement this workflow to fix real-world vulnerabilities.
Our choice fell on Juice Shop, an OWASP modern and sophisticated insecure web application. According to OWASP, Juice Shop encompasses vulnerabilities from the entire OWASP Top Ten, along with many other security flaws found in real-world applications.
Step-by-step workflow for fixing vulnerabilities
Once the MCP and the AI assistant tool are connected, we can ask for the list of all issues:
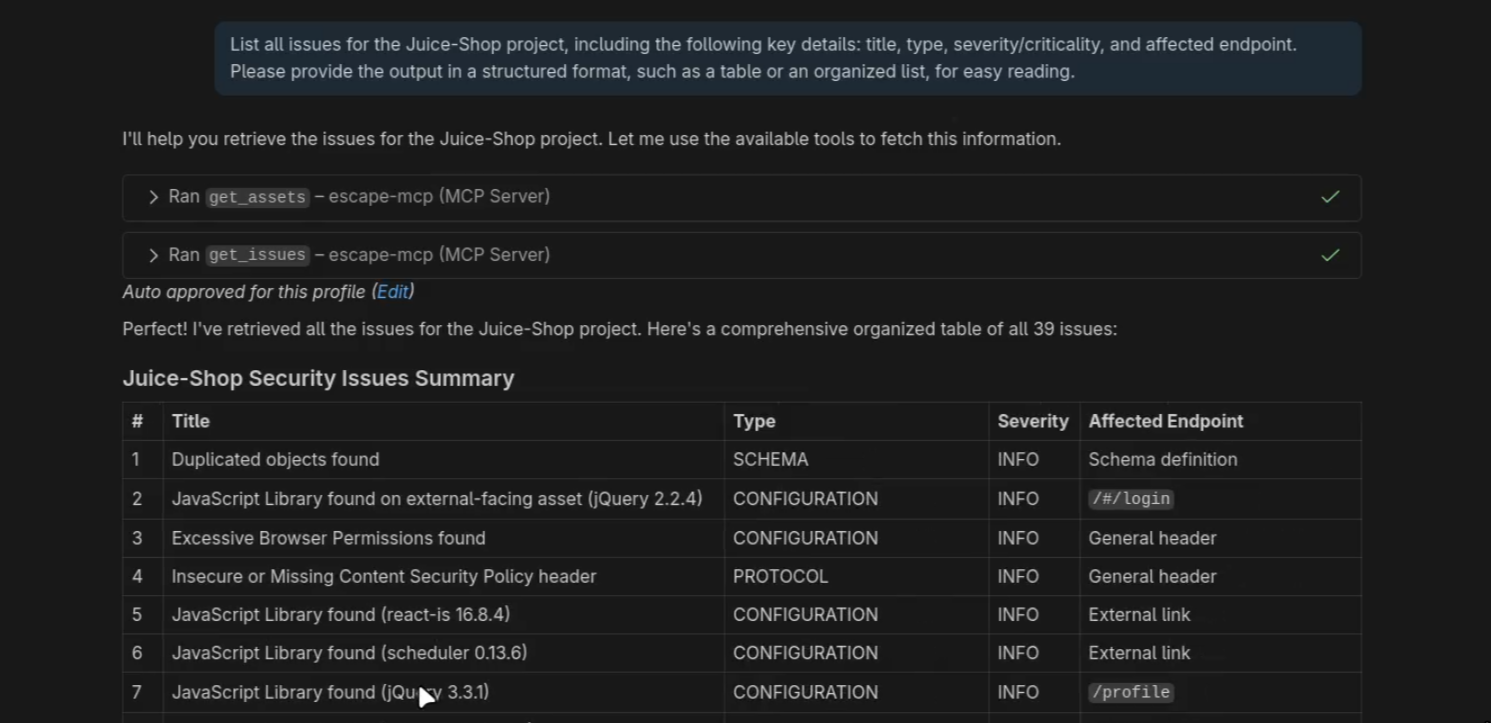
Secondly, you can ask for more details about a specific issue:
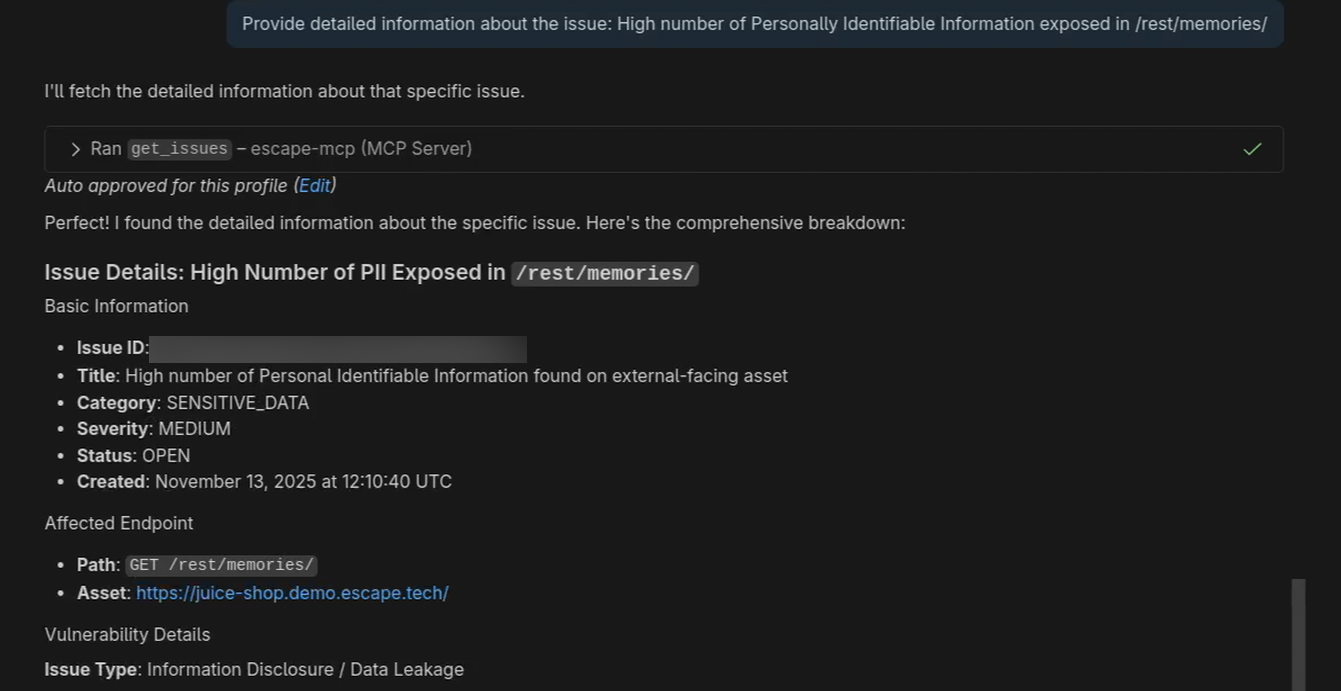
In this example, we chose to address a common issue: the exposure of Personally Identifiable Information (PII) directly on a website. This vulnerability is widespread across various types of websites. For instance, in our annual research State of API Exposure, we found more than 17,000 phone numbers exposed.
Next, we ask the assistant to pull a remediation code:

💡
Here is an example of prompt we suggest to use: Generate a minimal code fix to prevent {ISSUE_NAME} in the {ENDPOINT} endpoint. Do not change any other functionality. Focus only on the {ISSUE_NAME}. Include technical best practices and security considerations in the code comments
AI assistant analyzes the codebase to find the required endpoint, understands the code structure, and creates a minimal fix in the appropriate file.
Finally, don't forget that you should always check the remediation code:
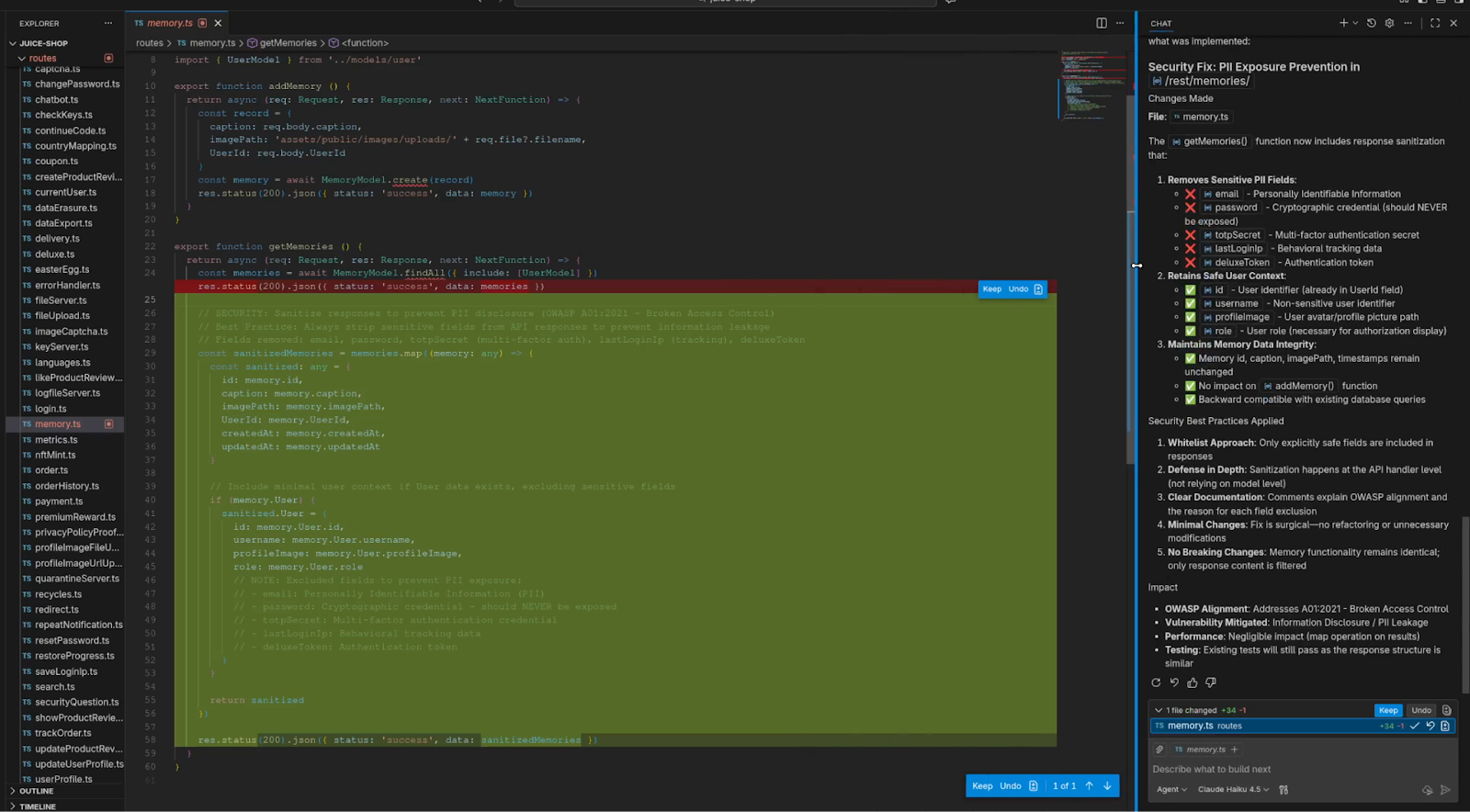
In the example above, we see that the AI assistant was able to
- Identify the route file where the vulnerable code was located
- Correctly identify the part of the code that needs to be fixed.
- Explain which sensitive fields (e.g., Email, password, TOTP secret, LastLoginIp, deluxeToken) should be removed from API responses and why, providing guidance on how to handle them safely.
💡
We suggest that this workflow is used mainly by engineers who already have a certain level of experience to understand the AI output.
Real-World Workflow: From Alert to Fix in Minutes
The Traditional Remediation Process
Before Escape MCP, vulnerability remediation typically followed this sequence:
- Alert Reception: Security alert delivered through existing notification channels (tickets, Slack..)
- Dashboard Access: Developer navigates to the Escape platform
- Context Gathering: Review scan results
- IDE: Switch back to the development environment
- Code Location: Search the codebase for vulnerable components
- Research: Consult documentation and remediation guidelines
- Implementation: Apply the fix and write tests
- Validation: Verify resolution
Each vulnerability is resolved in over one hour with several context switches.
Traditional workflow compounds inefficiency across teams. Organizations handling dozens of vulnerabilities per sprint lose substantial engineering capacity to context-switching overhead rather than actual remediation work.
Using Escape MCP: Remediation Process
With Escape MCP integrated into the development environment, the process simplifies to three steps:
- Alert Reception: Security alert delivered through existing notification channels
- In-IDE Query, the Developer remains in their IDE and queries their AI assistant to retrieve details about the vulnerability.
- Remediation Implementation: Developer requests remediation guidance from the AI assistant and adapts the suggestions as needed.
Each vulnerability is resolved in under thirty minutes without any context switching!
Why This Matters for Enterprise Teams
Some enterprises tried to ban AI-assisted coding due to concerns about code quality and security risks. But here’s the reality: developers are using it anyway, often with unsanctioned tools. The smart approach isn’t to ban AI, it’s to provide secure, context-aware AI that actually improves your security posture.
This is where measurable impact becomes critical. The Mean Time To Remediation (MTTR) is one of the key performance indicators for security teams. It measures the average time between the report of the vulnerability until the problem is completely resolved. According to a study from Intigriti, nearly 75% of businesses fail to respond to critical vulnerabilities within 24 hours, and 39% fail to apply any mitigation within the first 15 days.
While modern automated pentesting tools (e.g. Escape) help identify exploitable issues faster, the real bottleneck is often the communication gap between security and development teams. Security reports get lost in translation, developers struggle to understand the context, and remediation gets delayed.
Escape MCP bridges this gap by bringing security context directly into the developer’s workflow. Instead of juggling between security reports and code, developers get clear, actionable guidance right where they work, enabling them to fix vulnerabilities faster and more accurately.
The result? MTTR is reduced from days to hours, and developers spend less time researching fixes and more time building features. But there’s a deeper impact: when fixing vulnerabilities becomes faster and less frustrating, developers stop seeing security as a chore. They start understanding the “why” behind each fix, building security intuition over time. This leads to a real collaboration between developers and the security team, and gradually turns more developers into security champions who proactively consider security in their daily work.
Conclusion
The problem in application security isn't that developers don't care about vulnerabilities. They do. The key problem is that our tooling forces them to leave their workflow to address them. Escape MCP eliminates this friction by bringing security data directly into the IDE.
AI handles the context-switching: fetching vulnerability data, researching fixes, and understanding security context. Developers handle the critical thinking: evaluating suggestions, adapting solutions, making architectural decisions.
For teams struggling with slow remediation times or developer frustration with security workflows, Escape MCP offers a practical solution that works within the existing toolchain.
Does it sound like you? We’re here to help.
Escape MCP is a part of Escape AI-powered pentesting solution, which is
- ✅ Built for modern applications: SPAs and APIs
- ✅ Helps to find and fix even complex business logic security vulnerabilities
- ✅ Provides AI-powered exploit validation and remediation code snippets
- ✅ Smartly handles even complex authentication scenarios
💡 Check out more about what you can do with Escape's features below:
- Reproduce complex exploits from Bug Bounty reports in Escape
- Automate offensive security with AI (webinar guide)
- Multi-User Testing with Natural Language Queries
*** This is a Security Bloggers Network syndicated blog from Escape DAST - Application Security Blog authored by Gwendal Mognier. Read the original post at: https://escape.tech/blog/fixing-vulnerabilities-directly-in-your-ide/
如有侵权请联系:admin#unsafe.sh
