
JWTs (JSON Web Tokens) are at the heart of modern authentication systems — powering Single Sign- 2025-11-17 07:59:20 Author: securityboulevard.com(查看原文) 阅读量:11 收藏
JWTs (JSON Web Tokens) are at the heart of modern authentication systems — powering Single Sign-On (SSO), OpenID Connect, and API authorization.
But as organizations scale, so does the need to govern JWTs properly to maintain compliance with frameworks like SOC 2, ISO 27001, and GDPR.
In this guide, we’ll explore what JWT governance really means, how it maps to major compliance frameworks, and why it’s essential for building trust and audit-ready systems.
What Is JWT Governance?
JWT Governance refers to the policy-driven management of JWTs throughout their lifecycle — from issuance and validation to rotation, revocation, and logging.
Instead of treating tokens as just a way to log in, governance ensures every token aligns with your organization’s security, privacy, and compliance policies.
Key components of JWT governance:
-
Token lifespan and rotation policies
-
Secure key management (KMS or HSM)
-
Payload protection and encryption (JWS/JWE)
-
Centralized logging and auditability
-
Revocation and introspection endpoints
-
Policy documentation and monitoring
Why JWT Governance Matters for Compliance
Poor token governance can lead to data leaks, unauthorized access, and audit failures.
Each major compliance framework — SOC 2, ISO 27001, and GDPR — expects organizations to manage access tokens with strict security and accountability.
JWTs often contain user data, timestamps, and permissions — all of which can become personally identifiable information (PII) or sensitive audit evidence if not handled properly.
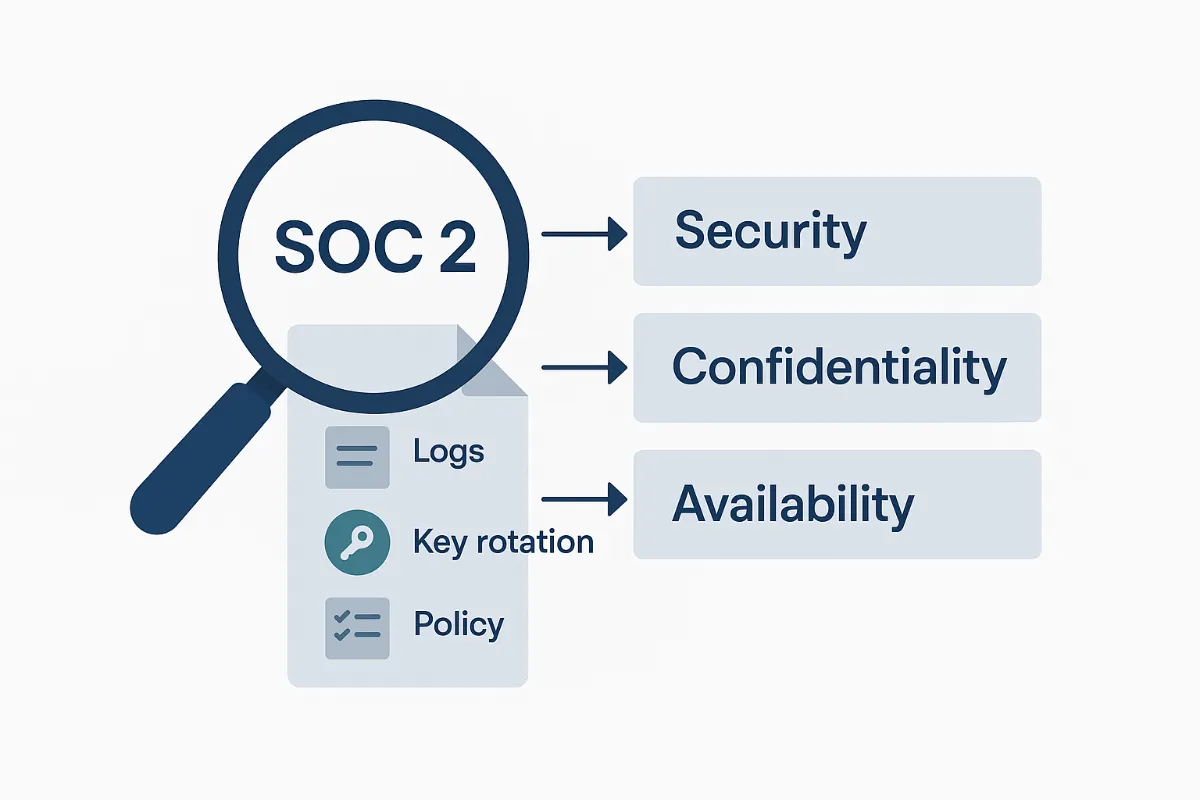
JWT Governance for SOC 2 Compliance
SOC 2 focuses on trust principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
JWT governance supports these principles through:
Security Controls
-
Rotate signing keys periodically
-
Use strong algorithms like
RS256orES256 -
Avoid storing secrets in token payloads
Audit Logging
-
Record token issuance, validation, and revocation
-
Link token activity with user sessions for traceability
Availability & Monitoring
-
Detect token misuse or unusual access patterns
-
Implement alerts for excessive token reissues
Example SOC 2 Control Mapping:
| SOC 2 Principle | JWT Governance Control |
|---|---|
| Security | Key rotation and token signature validation |
| Confidentiality | Encrypted JWTs and payload minimization |
| Privacy | Consent-based token issuance |
| Availability | Monitoring token usage and refresh cycles |
JWT Governance for ISO 27001
ISO 27001 defines controls under its Information Security Management System (ISMS).
JWT governance aligns naturally with many of them.
| ISO 27001 Control | JWT Governance Practice |
|---|---|
| A.9 Access Control | Restrict who can issue or validate tokens |
| A.10 Cryptography | Use strong algorithms and secure key storage |
| A.12 Operations Security | Monitor token activity and enforce revocation |
| A.16 Incident Management | Log token misuse and link with SIEM alerts |
Log token misuse and link with SIEM alerts
Implementation Tips:
-
Document JWT issuance and validation processes
-
Integrate key rotation with your ISMS procedures
-
Use automation to expire tokens after short intervals
JWT Governance for GDPR
Under GDPR, JWTs may contain personal data (like email, user ID, or session identifiers).
That means they must follow privacy principles like data minimization, storage limitation, and consent-based processing.
GDPR Implications for JWTs
-
Data Minimization: Include only essential user attributes in tokens.
-
Right to Erasure: Invalidate all tokens when a user deletes their account.
-
Data Retention: Set clear expiry times to limit how long personal data persists.
-
Consent Management: Ensure tokens are only issued after lawful consent.
Best Practices for JWT Governance
Follow these actionable best practices to make JWTs both secure and compliance-ready:
-
Keep token lifetimes short — 15–30 minutes for access tokens.
-
Store refresh tokens securely — use
HttpOnlyandSameSitecookies. -
Rotate signing keys automatically — use managed KMS services.
-
Avoid sensitive data in payloads — user IDs are fine; passwords are not.
-
Log every issuance and revocation event.
-
Encrypt JWTs (JWE) when containing sensitive claims.
-
Establish token revocation endpoints for session termination.
-
Document policies and review them quarterly for audit readiness.
How SSOJet Simplifies JWT Governance
At SSOJet, we help organizations govern JWTs with built-in compliance support — making your security audits smoother and your identity layer stronger.
With SSOJet, you get:
-
Automated JWT lifecycle management
-
Audit-ready logging for SOC 2 and ISO 27001
-
Key rotation and encryption enforcement
-
GDPR-aligned token retention and deletion
-
Real-time token introspection API
By combining token security and compliance automation, SSOJet makes JWT governance effortless — ensuring every token you issue meets your internal and regulatory standards.
Conclusion
JWTs are small, but their compliance impact is massive.
As authentication systems evolve, organizations must treat JWTs like any other security asset — governed, monitored, and aligned with compliance frameworks.
With JWT governance, you:
-
Strengthen trust and audit readiness
-
Protect sensitive data under GDPR
-
Meet SOC 2 and ISO 27001 security expectations
And with SSOJet, you don’t just issue tokens —
you govern them with confidence.
Related Resources
*** This is a Security Bloggers Network syndicated blog from SSOJet - Enterprise SSO & Identity Solutions authored by SSOJet - Enterprise SSO & Identity Solutions. Read the original post at: https://ssojet.com/blog/jwt-governance-for-soc-2-iso-27001-and-gdpr-a-complete-guide
如有侵权请联系:admin#unsafe.sh
