Key FindingsRecord fragmentation and decentralization: The number of active extortion g 2025-11-13 14:34:51 Author: research.checkpoint.com(查看原文) 阅读量:5 收藏
Key Findings
- Record fragmentation and decentralization: The number of active extortion groups in Q3 2025 rose to a record of 85 groups, the highest number observed to date. The top 10 groups accounted only for 56% of all published victims, down from 71% in Q1.
- Stable high activity: Ransomware victim postings stabilized at an average of 535 victims per month, up from 420 year-over-year (YoY) in Q2–Q3 2024, but below the Q1 2025 peak.
- LockBit’s return: Lockbit’s reappearance with the release of LockBit 5.0 in September 2025 potentially signals affiliate re-centralization under a major brand
- Emerging dominance: Qilin became the most active group, averaging 75 victims per month, followed by Akira, INC Ransom, and Play.
- Regional concentration shifts: South Korea entered the top 10 list of most attacked countries following a focused campaign by Qilin targeting its financial sector.
- Sector impact: Manufacturing and business services remained the most affected sectors. Healthcare held steady at 8% of total victims, despite selective avoidance by major actors like Play.
Ransomware in Q3 2025: RaaS fragmentation increases and Lockbit is back
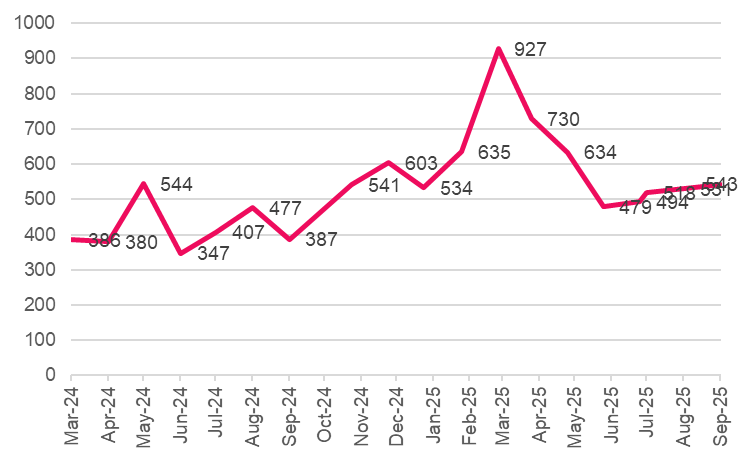
During the third quarter of 2025, we monitored more than 85 active data leak sites (DLS) that collectively listed 1,592 new victims. Compared to the 1,607 victims reported in Q2 2025, the publication rate remained stable though it is still notably higher than the 1,270 victims recorded in Q3 2024 (a 25% increase YoY). Overall, there are approximately 520 to 540 new victims per month, indicating that ransomware activity has plateaued albeit at historically high levels.

Figure 1 – Total Number of Reported Ransomware Victims in DLS, per month.
Despite the termination of several prominent ransomware groups, the overall number of active threat actors continues to grow, with new ones appearing every month.
During Q3 2025, we observed a steady expansion of double-extortion activity, driven mostly by small and emerging operators. Of the 85 data leak sites tracked this quarter, 47 groups published fewer than ten victims, suggesting a growing number of affiliates moving beyond established ransomware-as-a-service (RaaS) programs to conduct attacks independently.
This fragmentation follows the closure or dormancy of several major RaaS brands during the year, including RansomHub, 8Base, BianLian, Cactus, and others. In Q3 alone, 14 new groups began publishing victims, bringing the total number of newly observed actors in 2025 to 45. In Q1, the ten most active groups accounted for 71% of all DLS postings. In Q2, their share fell to 63%, and by Q3, to just 56%.
These findings illustrate the limited long-term impact of law-enforcement operations on the overall number of ransomware victims. Despite several high-profile takedowns during the past year—most of them directed at large RaaS operations such as LockBit, 8Base, and Blacksuit—the total volume of attacks did not significantly decline. Instead, the attacks continue a gradual upward trend, from an average of approximately 420 victims per month in Q2–Q3 2024 to about 535 per month in the same period of 2025.
This limited effect appears to stem from the focus of enforcement efforts: takedown operations primarily target RaaS infrastructure and administrators, which does not affect the affiliate operators who conduct the intrusions and drive the operational execution. When a major RaaS platform is disrupted, these affiliates typically migrate to alternative programs or establish their own data-leak sites, resulting in only short-term interruptions to overall activity levels.
The effects of affiliate mobility are evident both in the proliferation of new leak sites and in the rising activity of existing groups. Qilin, the most active actor in Q3 2025—and one of the most aggressive in recruiting former RansomHub affiliates—averaged around 75 victims per month, up from 36 in Q1 prior to RansomHub’s closure in April. INC Ransomware increased its monthly total from 23 to 39 victims, and Play went from 28 to 33 during the same period.
This ongoing fragmentation of the ecosystem may further erode ransomware operators’ reliability. Victims traditionally rely on attackers reputation to supply decryption keys after payment. Large RaaS brands have a commercial incentive to maintain credibility and provide the keys, but smaller, short-lived groups do not, leading to reduced payment rates which are currently estimated at 25–40% of total attacks.
In this context, the re-centralization of affiliates around major, recognizable brands remains strategically significant. Large RaaS programs preserve their market advantage through stability, reputation, and structured affiliate infrastructure. The re-emergence of LockBit, discussed in the following section, may represent precisely such a re-consolidation of affiliates under a stable and trusted brand identity.

Figure 2 – Ransomware Groups by Publicly Claimed Victims – Q3 2025.
Qilin, Akira, INC Ransom, Play, and Safepay maintained their positions among the most active groups in Q3. Warlock and The Gentlemen emerged more recently, both demonstrating rapid early activity: Warlock began posting victims in June 2025 and reached 43 total listings in Q3, while The Gentlemen claimed 38 victims during a single month of operation in September 2025.
Lockbit 5.0 is here – is LockBit truly back?
Until its disruption during Operation Cronos in early 2024, LockBit dominated the RaaS ecosystem, accounting for 20–30% of all published victims. Following the takedown, several arrests were announced, and successor groups — first RansomHub, then Qilin — attempted to inherit its affiliate base. However, the group’s core administrator, known as LockBitSupp, was never apprehended and in underground forums continued to hint at an eventual comeback.
The release of LockBit 5.0 in September 2025 marks the group’s return to active operations, reigniting questions about whether the RaaS landscape may again consolidate around this long-standing brand.

Figure 3 – LockBit’s share of all DLS-published victims.
LockBit had long promised a comeback. In May 2025, following the latest in a series of public setbacks, the group’s administrator, LockBitSupp, responded on the RAMP underground forum, declaring that they would “always rise up after being hacked.”

Figure 4 – LockBit administrator vowing to return on the RAMP forum.

Figure 5 – LockBit administrator announcing the group’s return on RAMP chat.
The XSS Russian-language cybercriminal forum previously banned LockBitSupp following a dispute with another user and reaffirmed that “explicit advertising of RaaS will remain prohibited.” RaaS programs depend on affiliate recruitment for their business model and maintaining visibility on prominent criminal forums such as XSS or RAMP is essential to their work.
By early September, the XSS administrator reported that LockBitSupp requested to be reinstated and opened the decision to a community vote.

Figure 6 – XSS forum administrator polling members on whether to reinstate LockBitSupp.
Despite this effort, the vote ultimately failed, and LockBit remains banned from XSS.

Figure 7 – Voting results on LockBitSupp’s proposed return to XSS.
In early September 2025, LockBit announced on RAMP the official launch of LockBit 5.0, coinciding with the sixth anniversary of the operation. New affiliates were asked to provide a Bitcoin deposit of roughly US $500 for access to a new encryptor and an updated control panel.

Figure 8 – LockBit 5.0 affiliate registration screen.
Since that announcement, we identified more than 15 distinct victims affected by LockBit 5.0, which replaced the earlier 4.0 builds that were still active until April 2025. LockBit continues to enforce strict operational security: all affiliate interfaces require individualized credentials, and no victims have been publicly listed on the group’s data-leak site.

Figure 9 – LockBit 5.0 ransom note from an attack in mid-September 2025
Updated ransom notes now explicitly identify themselves as “LockBit 5.0” and include a unique personal identifier that allows each victim to access a private negotiation portal. Victims are typically granted a 30-day grace period before the stolen data is published.

Figure 10 – Screenshot of LockBit 5.0 negotiations with a victim, mid-September 2025.
Analysis of the initial campaign shows that approximately 65 percent of identified attacks targeted organizations in the United States, with the remainder affecting Mexico, Indonesia, and several European countries.
LockBit 5.0 represents an upgraded evolution of the previous 4.0 version, incorporating Windows, Linux, and ESXi variants. The new build introduces enhanced evasion and anti-analysis mechanisms, faster encryption routines, and the use of a randomized 16-character file extension to disrupt signature-based detection. Most confirmed infections were deployed on Windows systems, while roughly 20 percent targeted ESXi virtual infrastructure.
Historically, LockBit has been among the most active and disruptive RaaS programs. With its extensive experience and the lower entry barrier for new affiliates, the re-emergence of the group poses a renewed risk to organizations across many sectors. The actions observed in September likely represent only the leading edge of a larger campaign, and the October victim postings on LockBit’s data-leak site are expected to confirm its full operational return.
DragonForce’s marketing efforts
DragonForce distinguishes itself among emerging ransomware groups through its heavy emphasis on public relations and coalition branding, frequently issuing high-profile statements and partnership claims on criminal forums. In September 2025, it announced on RAMP a supposed “coalition” with Qilin and LockBit, presented as a unified affiliate initiative.
However, these declarations appear largely symbolic, with no verified evidence of shared infrastructure or joint operations. The announcements likely serve to attract affiliates and project influence within a fragmented RaaS market. This reflects DragonForce’s broader strategy to maintain visibility and credibility in an increasingly competitive underground ecosystem.

Figure 11 – DragonForce announcing updates and coalition with LockBit and Qilin.
DragonForce roughly tripled its monthly victim count since the shutdown of RansomHub and claimed 56 victims in Q3 2025. This is still fewer than Qilin and Akira but shows steady growth. DragonForce continues to actively recruit affiliates and promote new features in its RaaS program and recently announced on RAMP a data-driven extortion service that offers affiliates tailored analysis of stolen data to maximize ransom leverage.

Figure 12 – DragonForce’s “data audit” services.
Under this model, an affiliate that accessed a large dataset (typically over 300 GB) from a company with annual revenues above US $15 million can submit it for analysis and maximize the extortion impact. In a recent showcased example, DragonForce reviewed stolen files from a gold mining company and highlighted the most valuable commercial and financial information, accompanied by a customized extortion letter.

Figure 13 – DragonForce Audit example.
Qilin – The Dominant RaaS Operation of 2025
Qilin remains the most active ransomware group in 2025, increasing its monthly victim rate to an average of 75 victims in Q3, up from 36 in Q1.
Although the group presents itself as ideologically motivated, its operations appear entirely financially driven. In a June 2024 interview published on its WikiLeaksV2 blog, Qilin’s operators described themselves as “idealists who love our country.” This statement, however, contrasts sharply with the group’s broad and opportunistic targeting across sectors and geographies.

Figure 14 – Qilin interview from June 2024 on their official blog.
In a separate interview on SuspectFile, a Qilin affiliate characterized the program as profit-focused and flexible, with affiliates responsible for intrusion and exfiltration while Qilin manages infrastructure, leak-site operations, and negotiations. Reported affiliate share ranges between 80% and 85%, which is among the highest in the market. This has attracted numerous operators previously active under RansomHub and BianLian.
Qilin’s open affiliate framework accommodates actors with diverse motivations and capabilities. In one recent case, the group’s data-leak site briefly listed Israel’s Shamir Medical Center among its victims.

Figure 15 – Shamir Medical Center announcement on Qilin’s DLS.
According to Israeli researcher Erez Dassa, the responsible affiliate was likely an Iranian-linked threat actor. Dassa reported that following direct communication, Qilin’s administrators agreed that public association with terrorism or politically motivated activity could expose the group to additional pressure and subsequently removed the listing.

Figure 16- Erez Dassa’s Telegram post explaining the Shamir incident.
This incident illustrates the range of motivations operating within large RaaS ecosystems. While affiliates enjoy broad autonomy, Qilin demonstrates a degree of central oversight and reputational management, removing politically sensitive cases that may jeopardize its long-term operations. The group continues to balance open recruitment and strategic control, maintaining its position as a leading and resilient RaaS brand.
Geographic Distribution of Victims – Q3 2025
The geographic distribution of ransomware victims in Q3 2025 continues to follow established trends in the global ransomware ecosystem. The United States accounted for roughly half of all reported cases, reaffirming its position as the primary target for financially motivated threat actors. Most publicly listed victims remain concentrated in Western, developed economies, where organizations are perceived as having greater financial resources and a higher likelihood of paying ransom.

Figure 14 – Ransomware Groups by Publicly Claimed Victims – Q3 2025.
An unusual concentration of attacks in South Korea elevated the country to seventh place on the list of most affected nations this quarter. This spike is linked almost entirely to Qilin, which listed 30 South Korean victims, 28 of them between August and September 2025. Of these, 23 belonged to the financial services sector. While the cause of this focused campaign remains uncertain, the Korea Herald newspaper attributed it to a compromised cloud server operated by an IT contractor serving multiple mid-sized private equity funds.
Safepay maintained a strong focus on Germany and the United Kingdom, with each accounting for approximately 10% of its total victims in Q3. Together with INC Ransom, which also recorded 11 British victims, these two groups were the most active in the UK, followed closely by Qilin with 10.
Twenty percent of DragonForce’s victims were based in Germany, making it the most active ransomware group in the country.
INC Ransom reported a notably high proportion of Canadian victims (8%), the largest share of any group targeting Canadian organizations this quarter.

Figure 15 – Canadian Victims by Actor, Q3 2025.
Ransomware Attacks by Industry – Q3 2025 Analysis
The industry distribution of ransomware victims in Q3 2025 shows a consistent cross-sector impact, largely unchanged from previous quarters. Profit-oriented organizations with high downtime costs, such as industrial manufacturing, and those holding sensitive or regulated data, such as business services, remained the most targeted sectors, each representing approximately 10% of all extortion attempts.
Healthcare and medical organizations continue to face steady targeting due to the critical nature of their operations and the sensitivity of stored information. Interestingly, threat actors view these victims as high-risk targets because of the attention such incidents attract from law enforcement. In Q2 2025, healthcare accounted for approximately 8% of all publicly listed victims, a figure that remained stable through Q3.
While some groups, such as Play Ransomware, appear to enforce an internal policy against attacking healthcare institutions, others such as Qilin, INC Ransomware, and KillSec continue to list healthcare providers among their victims, disregarding the informal ethical boundaries observed by larger RaaS brands.

Figure 16 – Ransomware Victims by Industry, Q3 2025.
Conclusion
The ransomware ecosystem in Q3 2025 remains highly active and structurally fragmented, while at the same time increasingly adaptive. The dissolution of major RaaS programs did not reduce the overall volume of attacks but instead redistributed the load among numerous smaller and more agile actors. Groups such as Qilin and DragonForce have capitalized on this trend, expanding through aggressive affiliate recruitment and service innovation. LockBit’s re-emergence signals a potential trend toward re-centralization around trusted brands.
Despite periodic law-enforcement disruptions, the fundamental dynamics of the ransomware market, using affiliate-driven operations, data extortion models, and cross-platform tooling, remain intact. Continued monitoring of affiliate migration patterns and emerging extortion techniques are essential to understanding how this decentralized ecosystem evolves through the remainder of 2025.
如有侵权请联系:admin#unsafe.sh