Near-record ransomware attacks and the rise of new threats like Sinobi highlight the need for 2025-11-13 08:46:8 Author: cyble.com(查看原文) 阅读量:9 收藏
Near-record ransomware attacks and the rise of new threats like Sinobi highlight the need for rapid detection and response.
Ransomware attacks soared to the second-highest total on record in October 2025.
October’s 623 ransomware attacks were up more than 30% from September, and below only February 2025’s record totals (chart below). It was the sixth consecutive monthly increase in ransomware attacks.

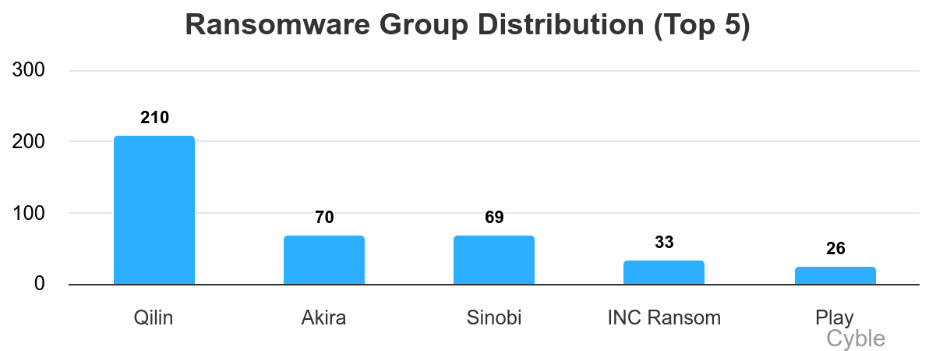
Qilin was the most active ransomware group for the sixth time in the last seven months, its 210 claimed victims, three times higher than second-place Akira (chart below). Also of note is the third-place showing of Sinobi with 69 victims claimed, a rapid ascendance for a group that first emerged in July 2025. We include high-confidence Qilin indicators of compromise (IoCs) from October 2025 in an appendix below.

Construction, Professional Services, Healthcare, Manufacturing, IT and Energy/Utilities were the most attacked sectors (chart below).

In October, 31 incidents potentially impacted critical infrastructure, and 26 incidents had possible supply chain implications.
The U.S. was by far the most attacked country once again, its 361 attacks 10 times more than second-place Canada (chart below). Of concern is the emergence of Australia as a top-five target, as the country’s rich resources and high per-capita GDP have made the country a rich target for threat actors.

Year-to-date, ransomware attacks are up 50% from the first 10 months of 2024 to 5,194 ransomware attacks through October 31, as new leaders like Qilin, Sinobi, and The Gentlemen have more than made up for the decline of former leaders such as LockBit and RansomHub.
Vulnerabilities Weaponized by Ransomware Groups in October
Fueling the increase in both ransomware and supply chain attacks this year has been a steady supply of critical IT vulnerabilities, as well as a large number of unpatched internet-facing assets. Among the vulnerabilities targeted in October were:
- Oracle E-Business Suite remote SSRF/XSL RCE (CVE-2025-61882) – targeted by Cl0p
- GoAnywhere MFT deserialization RCE (CVE-2025-10035) – Medusa
- Microsoft Windows Privilege Escalation Vulnerability (CVE-2021-43226) – Unknown ransomware groups (CISA advisory)
- Velociraptor Incorrect Default Permissions (CVE-2025-6264) – Warlock ransomware operators
- Linux kernel’s netfilter :nf_tables module (CVE‑2024‑1086) – Unknown ransomware groups (CISA advisory)
Ransomware Attacks and Key Developments
Below are some of the most important ransomware developments in October 2025, culled from Cyble and OSINT sources.
The Cl0p ransomware group exploited a critical vulnerability (CVE-2025-61882) in Oracle EBusiness Suite versions 12.2.3–12.2.14 to achieve remote code execution (RCE) via a server-side request-forgery (SSRF) that forces the application to fetch and execute a malicious XSL payload. The group sent extortion emails and appears to be leveraging this exploit as an entry point for data theft and ransomware deployment.
Medusa ransomware chained an unauthenticated deserialization RCE in GoAnywhere MFT (CVE-2025-10035) to gain initial access, then maintained persistence and remote control by abusing RMM tooling (SimpleHelp and MeshAgent), dropping RMM binaries directly under the GoAnywhere process and creating .jsp web shells in MFT directories. They performed user/system discovery and network scans (e.g., netscan), moved laterally using mstsc.exe (RDP), and used the RMM infrastructure (plus a Cloudflare tunnel) for command and control (C2). Data theft was performed with Rclone in at least one incident, and Medusa ransomware was later deployed in at least one confirmed environment.
Ransomware operators are increasingly hijacking or silently installing legitimate remote access tools (AnyDesk, RustDesk, Splashtop, TightVNC, etc.) after credential compromise to gain persistent, stealthy access, using these trusted channels for file transfer, interactive control, antivirus neutralization, and ransomware delivery. Attack paths include credential theft/brute force, modifying existing tool configs or using silent install flags, escalating to SYSTEM, disabling defenses, and propagating the tools to support lateral movement and final encryption.
Warlock operators installed an outdated version of the open-source Velociraptor on multiple servers to establish stealthy persistence and remote control, then used it alongside a pre-existing vulnerability (CVE-2025-6264) and GPO modifications to disable defenses. They later deployed Warlock, LockBit and Babuk ransomware variants within the same engagement, while also exfiltrating data and encrypting virtual machine environments.
Recent BlackSuit campaigns employed Vishing to steal VPN credentials for initial access and performed DCSync on a domain controller for high-privilege credentials. In addition, the group deployed AnyDesk and a custom RAT for persistence. Other measures included wiping forensic traces with CCleaner, and using Ansible to deploy BlackSuit ransomware across ESXi hosts, encrypting hundreds of VMs and causing major operational disruption.
The threat actor Vanilla Tempest conducted a campaign that distributed fake Microsoft Teams installers hosted on look-alike domains. The installers used fraudulently signed certificates, delivering the Oyster backdoor and ultimately Rhysida ransomware. Microsoft disrupted the operation in early October by revoking more than 200 certificates.
Qilin affiliates deployed a Linux-based ransomware binary on Windows machines by abusing legitimate remote-management tools (WinSCP, Splashtop, AnyDesk, ScreenConnect) and leveraging BYOVD (Bring Your Own Vulnerable Driver) attacks. In addition, other affiliates used a staged toolkit (SharpDecryptPwd, Mimikatz, NirSoft utilities) plus a WDigest registry tweak to harvest credentials, and exfiltrate data via abused cloud tools like Cyberduck (multipart uploads to Backblaze).
Trigona ransomware operators brute-forced exposed MS-SQL servers, embedding malware inside database tables and exporting it to disk via bcp.exe to install payloads (e.g., AnyDesk, Teramind). The actor also deployed Rust-based RDP/MS-SQL scanners, a Go SQL-injection tester (“StressTester”), and custom delete/replace binaries—an automated, SQL-centric intrusion chain that weaponizes legitimate DB tooling for initial access and payload delivery.
On October 9, DragonForce posted on the RAMP forum that it is opening its partner program to the public. New affiliates can register and immediately access a suite of free “partner services,” including professional file analysis/audit, hash decryption, call support, and free victim storage. Registration requires a $500 non-refundable fee; payments accepted in XMR and BTC. The group warned affiliates to follow its rules or face account blocking or free decryptor distribution.
On October 18, threat actor Zeta88 — alleged operator of The Gentlemen ransomware — announced on RAMP updates to their Windows, Linux and ESXi lockers, adding automatic self-restart and run-on-boot, a silent mode for Windows that encrypts without renaming files and preserves timestamps, and self-spread capabilities across networks/domains using WMI/WMIC, SCHTASKS, SC (Service Control) and PowerShell Remoting. The release also introduced flexible encryption-speed modes, multiple Windows operating modes, and a universal decryptor covering all operating modes.
Conclusion
The alarming increase in ransomware attacks in October – and the continual investment in upgrades and innovations by ransomware groups – highlights the need for security teams to respond with equal vigilance. Basic cybersecurity best practices that can help protect against a wide range of cyber threats include:
- Prioritizing vulnerabilities based on risk.
- Protecting web-facing assets.
- Segmenting networks and critical assets.
- Hardening endpoints and infrastructure.
- Strong access controls, allowing no more access than is required, with frequent verification.
- A strong source of user identity and authentication, including multi-factor. authentication and biometrics, as well as machine authentication with device compliance and health checks.
- Encryption of data at rest and in transit.
- Ransomware-resistant backups that are immutable, air-gapped, and isolated as much as possible.
- Honeypots that lure attackers to fake assets for early breach detection.
- Proper configuration of APIs and cloud service connections.
- Monitoring for unusual and anomalous activity with SIEM, Active Directory monitoring, endpoint security, and data loss prevention (DLP) tools.
- Routinely assessing and confirming controls through audits, vulnerability scanning, and penetration tests.
Cyble’s comprehensive attack surface management solutions can help by scanning network and cloud assets for exposures and prioritizing fixes, in addition to monitoring for leaked credentials and other early warning signs of major cyberattacks.
Appendix: IoCs Associated with Qilin Ransomware Group, October 2025
| IoC | Type |
| 15E5BF0082FBB1036D39FC279293F0799F2AB5B2B0AF47D9F3C3FDC4AA93DE67 | FileHash-SHA256 |
| 16F83F056177C4EC24C7E99D01CA9D9D6713BD0497EEEDB777A3FFEFA99C97F0 | FileHash-SHA256 |
| 331D136101B286C2F7198FD41E5018FCADEF720CA0E74B282C1A44310A792E7F | FileHash-SHA256 |
| 3DBA9BA8E265FAEFCE024960B69C1F472AB7A898E7C224145740F1886D97119F | FileHash-SHA256 |
| 454E398869E189874C796133F68A837C9B7F2190B949A8222453884F84CF4A1B | FileHash-SHA256 |
| 549A1AE688EDFCB2E7A254AC3ADED866B378B2E829F1BB8AF42276B902F475E6 | FileHash-SHA256 |
| 5F0253F959D65C45A11B7436301EE5A851266614F811C753231D684EB5083782 | FileHash-SHA256 |
| 5FFF877789223FA9810A365DFDEAFE982C92F346ECD20E003319C3067BECD8BA | FileHash-SHA256 |
| E14BA0FB92E16BB7DB3B1EFAC4B13AEE178542C6994543E7535D8EFAA589870C | FileHash-SHA256 |
| E38D4140FCE467BFD145A8F6299FC76B8851A62555B5C0F825B9A2200F85017C | FileHash-SHA256 |
| E46BDE83B8A3A7492FC79C22B337950FC49843A42020C41C615B24579C0C3251 | FileHash-SHA256 |
| F488861F8D3D013C3EEF88983DE8F5F37BB014AE13DC13007B26EBBD559E356E | FileHash-SHA256 |
| http://104.164.55.7/231/means.d | URL |
| http://185.141.216.127/tr.e | URL |
| http://45.221.64.245/mot/ | URL |
| https://chatgptitalia.net/ | URL |
| https://pub-2149a070e76f4ccabd67228f754768dc.r2.dev/I-Google-Captcha-Continue-Latest-27-L-1.html | URL |
| https://pub-959ff112c2eb41ce8f7b24e38c9b4f94.r2.dev/Google-Captcha-Continue-Latest-J-KL-3.html | URL |
| 31C3574456573C89D444478772597DB40F075E25C67B8DE39926D2FAA63CA1D8 | FileHash-SHA256 |
如有侵权请联系:admin#unsafe.sh