
一个新的网络钓鱼自动化平台Quantum Route Redirect利用约1,000个域名窃取Microsoft 365用户的凭证。该工具包预配置了钓鱼域名,使技术有限的攻击者也能轻松实施攻击。自8月以来,在全球范围内检测到该平台的活动,其中近四分之三位于美国。该平台可自动处理从流量重定向到受害者追踪的所有阶段,并通过伪装成合法请求的恶意邮件引导用户至凭证收集页面。研究人员建议采取URL过滤和账户监控等防御措施以应对威胁。 2025-11-10 21:30:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

A new phishing automation platform named Quantum Route Redirect is using around 1,000 domains to steal Microsoft 365 users' credentials.
The kit comes pre-configured with phishing domains to allow less skilled threat actors to achieve maximum results with the least effort.
Since August, analysts at security awareness company KnowBe4 have noticed Quantum Route Redirect (QRR) attacks in the wild across a wide geography, although nearly three-quarters are located in the U.S.
They say that the kit "is an advanced automation platform" that can cover all the stages of a phishing attack, from rerouting traffic to malicious domains to tracking victims.
Attacks start with a malicious email made to appear as a DocuSign request, a payment notification, a missed voicemail, or a QR code.
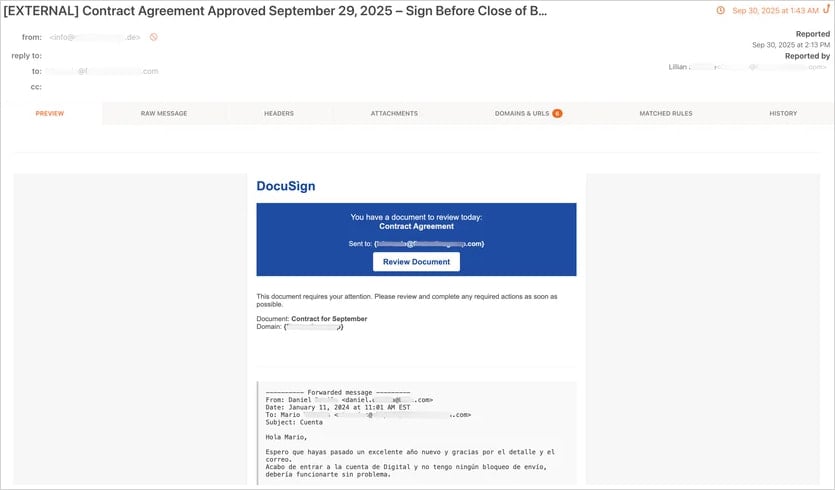
Source: KnowBe4
The emails direct targets to a credential harvesting page hosted on a URL that follows a specific pattern.
“Our researchers also observed that the domain URLs consistently follow the pattern “/([\w\d-]+\.){2}[\w]{,3}\/quantum.php/” and are typically hosted on parked or compromised domains,” explains KnowBe4.
“The choice to host on legitimate domains can help to socially engineer the human targets of these attacks.”
KnowBe4 says it has identified about 1,000 domains hosting QRR phishing pages.
A built-in filtering mechanism can distinguish between bots and human visitors, the researchers say, adding that QRR can redirect potential victims to a phishing page, while automated systems, such as email security tools, are sent to benign sites.
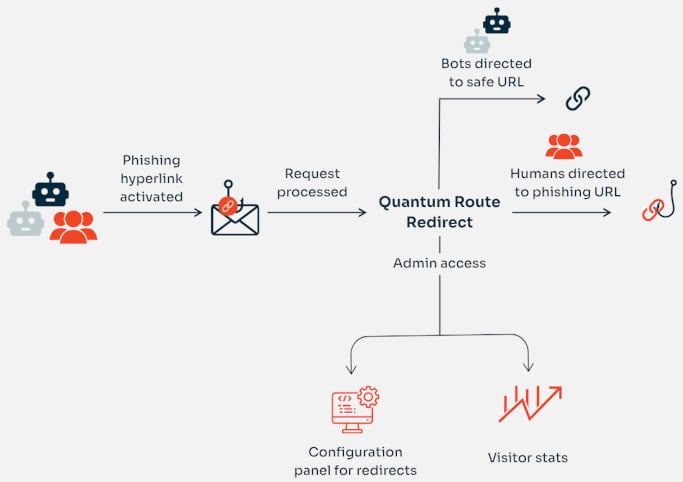
Source: KnowBe4
As the central traffic routing system on QRR performs its redirecting tasks automatically, operators can view the related statistics on the dashboard, where the number of real versus non-human visitors is logged in real-time.
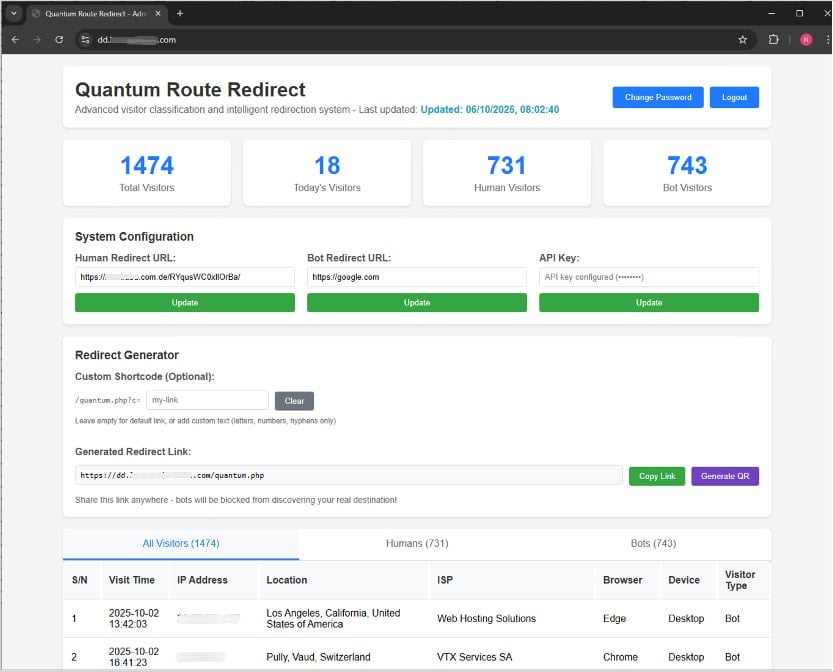
Source: KnowBe4
KnowBe4 has observed the QRR phishing kit targeting Microsoft 365 accounts across 90 countries, but 76% of the attacks were directed at users in the U.S.
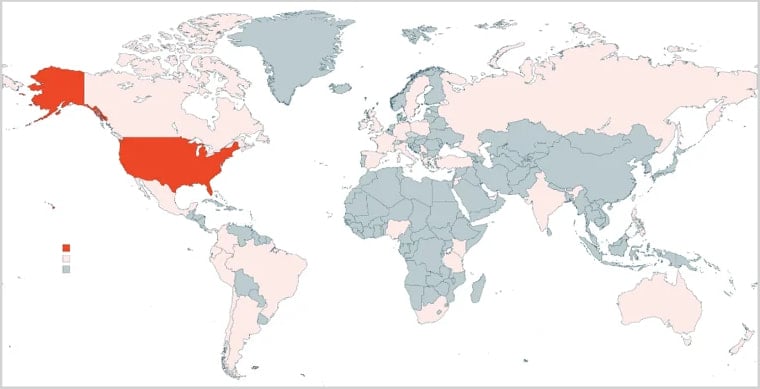
Source: KnowBe4
The researchers expect the use of Quantum Route Redirect to increase due to the methods used to evade URL scanning technologies.
Similar services that gained prominence earlier this year include VoidProxy, Darcula, Morphing Meerkat, and Tycoon2FA.
However, there are defense methods that can protect against this threat.
KnowBe4 analysts recommend implementing robust URL filtering that can detect phishing attempts, along with tools that can monitor accounts for signs of compromise if a user's credentials are stolen.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

