托管安全服务提供商市场整合加剧,预计到2028年前200家将减少至120家。Morpehus AI通过自动化处理安全警报和优化运营流程,帮助提供商降低成本并提升服务质量。其功能包括统一数据模型、智能分析和高效响应机制,推动业务从线性增长转向指数收益。 2025-11-8 00:23:46 Author: securityboulevard.com(查看原文) 阅读量:24 收藏
The MSSP market is growing, but the number of players is shrinking. Industry analysis forecasts the top 200 MSSPs consolidating down to about 120 by 2028. Mid-tier players are getting acquired. Regional firms are merging. The survivors will be those that scale efficiently without proportional headcount increases.
Every security alert represents two possibilities: a threat to contain or an opportunity to prove value. For managed security service providers, the challenge has always been doing both at scale. More customers mean more alerts. More alerts mean more analysts. More analysts mean thinner margins.
Morpheus changes that equation.
The platform investigates every alert autonomously, triages 95% in under two minutes, and handles routine incidents end-to-end. Your analysts stop chasing false positives. They start hunting real threats. Your MSSP stops scaling linearly. It starts scaling profitably.
This shift changes the economics of managed security. Round-the-clock coverage becomes standard, not expensive. Customer onboarding takes days, not months. Per-customer costs drop while service quality rises. The result: you can serve more clients with the same team, or serve the same clients better with higher-margin offerings like MDR, MXDR, or managed SIEM.
Morpheus was built for multi-tenant operations. Each customer gets isolated incident data, custom workflows, and dedicated response logic. You get centralized management, unified reporting, and global deployment options. Data centers span continents to match your footprint. The platform adapts to how you work, not the other way around.
Below, we map specific Morpheus capabilities to measurable business outcomes. Each feature translates directly to margin improvement, service differentiation, or operational efficiency. This is how you turn alert volume into revenue growth.
800+ Integrations: Maximize Potential Customers, Minimize Integration Costs
Every prospect brings a different stack. Splunk or Microsoft Sentinel. CrowdStrike or SentinelOne. Okta, Entra, Fortinet, or dozens of other tools. Saying “we support your environment” used to mean weeks of custom integration work.
Morpheus supports over 800 products out of the box. New customers go live in days. Integration complexity drops to near zero for most deployments. SOC engineers can focus on revenue-generating work instead of API troubleshooting.
This changes your sales motion. You can say yes to more deals, expand into verticals you previously avoided because their toolsets were too custom, and acquire smaller MSSPs without retooling your platform. Their customer base folds into your operations immediately.
Lower integration costs mean higher gross margins on every new client. Faster onboarding accelerates time to revenue. Broader compatibility expands your market.
Alert Ingestion: Reduce Training and Complexity Costs with Unified Data Model
Training a new analyst to work across multiple customer environments used to mean teaching them how each security tool structures its data. CrowdStrike formats alerts one way. Microsoft Defender formats them another. Splunk logs look different from Sentinel logs. Before anyone can investigate, they need to understand what they’re looking at.
Morpheus normalizes every alert automatically. It converts data from 800+ security tools into a consistent format. Analysts see the same fields, the same structure, and the same terminology regardless of which tool generated the alert.
New hires become productive faster. They learn to read Morpheus data once and apply that knowledge to every customer. No need to master different SIEM query languages or memorize product-specific field names. Junior analysts become productive in days, not months.
Consistency reduces errors. When alerts look the same across all sources, analysts make fewer mistakes. When investigations don’t require toil, they move faster, enabling operational efficiency without sacrificing flexibility.

AI SOC Analyst: Achieve 100% Alert Coverage, Around the Clock
Customers expect 24/7 monitoring, but staffing 24/7 SOCs are expensive. Night shifts cost more. Weekend shifts cost more. Holidays cost even more. And you still have gaps when analysts are sick, on vacation, or between training cycles.
Morpheus investigates every alert autonomously, any time of day. It pulls context from the customer’s entire stack, hunts for related indicators, checks threat intelligence feeds, and determines whether the alert represents real risk. It does this in seconds or minutes, not hours.
Your analysts wake up to triaged queues. High-priority incidents are flagged and investigated. Up to 95% of low-priority Tier 1 alerts are closed with documented reasoning. Gaps in coverage disappear. Customer SLAs become easier to meet.
This changes staffing economics. 24/7coverage stops being a cost center. It becomes table stakes, delivered at a fraction of the traditional expense. You need fewer personnel on night-shifts. You can cover more customers with the same headcount. Or you can redeploy analysts from triage to higher-value work: threat hunting, incident response, or customer advisory services.
Analyst Workspace: User-Configured Workspaces to Match Role and Needs
Different team members need different views. Tier 1 analysts need triage queues. Tier 3 analysts need investigation timelines. SOC managers need metrics like incidents closed, average time to resolution, resolution rate, etc.
Morpheus delivers operational intelligence in real time through configurable dashboards. The dashboard surfaces incident backlog trends, automation coverage rates, resolution times, and false positive percentages. Each metric shows direction. You see problems forming, not problems that already cost you money.
SOC managers see cross-customer workload distribution. Which analysts are overloaded. Which customers generate excessive false positives. Which threat types consume the most time.
For MSSPs, this changes capacity planning. You know exactly how much overhead each customer creates. Price services on actual workload data, not guesswork.
IR Priority Score: At-a-Glance Management, Zero Time Wasted on Noise
Not all alerts matter equally. Some represent active breaches. Others are benign configuration changes. Sorting the two used to require reading through each alert individually.
Morpheus calculates an Incident Response Priority Score for every alert. The score weighs severity, confidence, context, and existing mitigations. High scores rise to the top of the queue. Low scores get closed automatically if they fall below your threshold, with full audit trails for review.
Your analysts see the most urgent incidents first. Critical alerts surface immediately. False positives stay buried. The queue reflects actual risk, not raw volume.
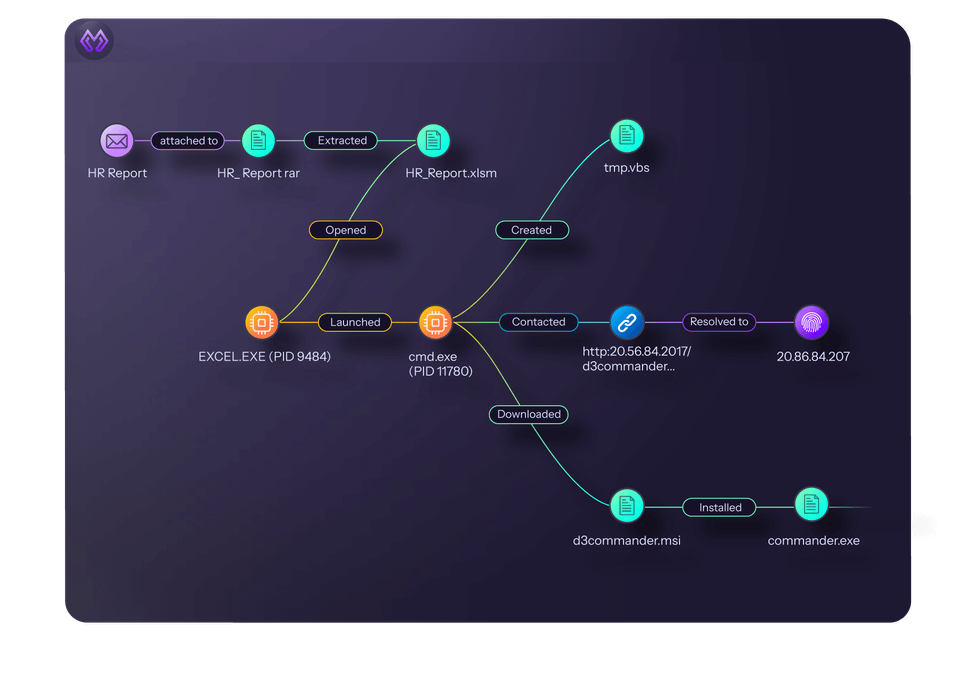
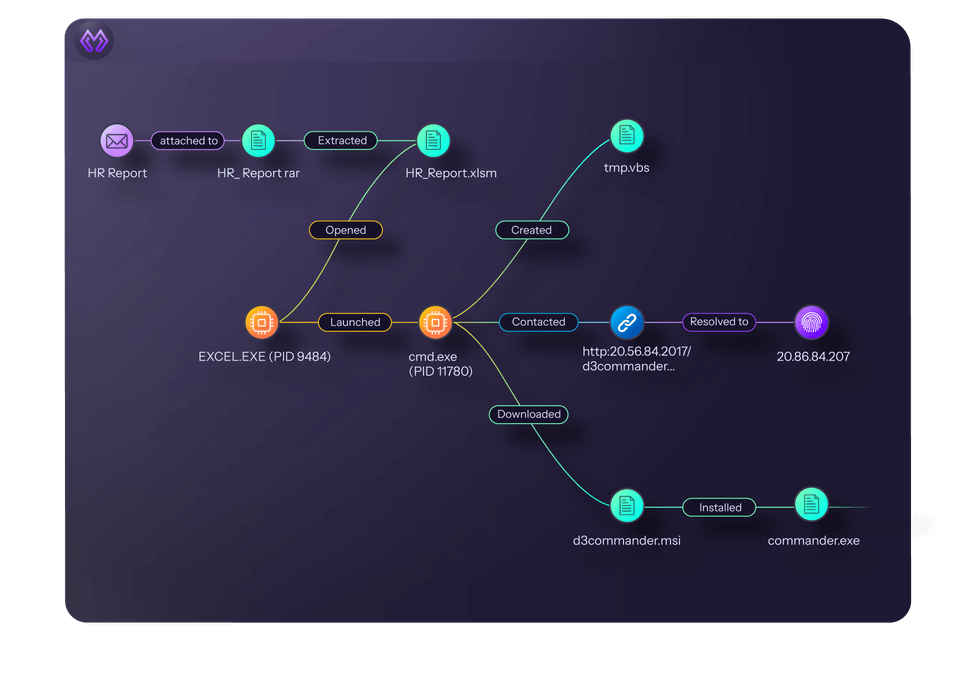
Link Analysis: Enables Higher-Value Investigations Within the Platform
Cyber attacks span multiple systems. An attacker compromises one endpoint, moves laterally through the network, escalates privileges in Active Directory, and exfiltrates data through a cloud service. Each step generates alerts in different tools.
Morpheus maps relationships between alerts, users, devices, and indicators. It shows which events are connected, how they relate, and what the attack path looks like. Analysts see the full picture without jumping between consoles or piecing together timelines manually.
This enables deeper investigations without requiring Tier 3 expertise. Junior analysts can follow the graph and understand what happened. Senior analysts can find root causes faster. Your MSSP can offer advanced investigation services that used to require dedicated forensics teams.
Forensic Timeline: Assists Analysts in Understanding Full Scope of Event
Incident response requires knowing what happened, when, and in what order. Reconstructing timelines manually means pulling logs from a dozen sources, correlating timestamps, and building a narrative from fragments.
Morpheus generates chronological timelines automatically. It stitches together alerts, ATT&CK TTPs, IOCs, user actions, and system events into a single view. Analysts see the attack unfold step by step. The platform handles log correlation and timeline assembly. Analysts focus on analysis and response.
Forensic timelines also improve post-incident reporting. You can show customers exactly what happened, when the breach started, how far it spread, and what actions were taken.
Remediation Recommendations: Pass Value to Clients or Guide MSSP Analysts
After identifying a threat, the next question is always: what do we do about it? Less experienced analysts need guidance. Customers want clear action plans. Delivering both used to require escalating every incident to senior staff.
Morpheus recommends specific remediation steps based on the incident. Isolate the host. Reset credentials. Block the domain. Patch the vulnerability. Each recommendation is tailored to the environment and the threat.
You can pass these recommendations directly to customers as part of your service. Or you can use them to guide your own analysts through response actions. Either way, you accelerate resolution and reduce the expertise required to handle complex incidents.
Remediation Workflows: Enables High-Value, End-to-End Service Offering
Most MSSPs sell monitoring and alerting. Customers get notified when something is wrong, then scramble to fix it themselves or hire a separate IR firm. You lose the most profitable part of the engagement.
Morpheus lets you bundle remediation into your service contracts. The platform generates response playbooks customers can execute themselves, or you can offer white-glove remediation as a premium tier. Either way, you’re selling the complete security lifecycle, not just the detection phase.
This changes your revenue model. Monitoring contracts turn into MDR contracts. One-time incident response becomes recurring monthly revenue. Customers who might churn when their IT team matures stay because you’re handling response, not just reporting problems.
You can also tier your offerings. Basic customers get self-service remediation playbooks. Premium customers get analyst-executed response. Enterprise customers get proactive threat hunting plus response.
From Linear Costs to Exponential Returns
Traditional cost savings follow a predictable pattern. Cut 10% from headcount, reduce 15% from infrastructure, and margins improve by exactly that amount. The math is linear. The outcomes are linear. The growth is linear.
Morpheus breaks that model.
You’re not trimming expenses proportionally. You’re decoupling revenue growth from cost growth entirely. A 50% increase in customers, or a 200% surge in alert volume no longer forces you to double your SOC team.
This creates exponential business impact. Your valuation multiples rise to match software economics, not labor-intensive service models.
The market will reprice this gap. MSSPs that demonstrate SaaS-like unit economics will trade at software multiples. Traditional labor-intensive MSSPs will stay trapped in services valuations. Early adopters are already seeing these valuation shifts. The only question is whether you’re positioned correctly when it accelerates.
Transform your MSSP economics. Book a demo and see how Morpheus delivers exponential business impact.
The post How MSSPs Turn Security Alerts Into Exponential Revenue With Morpheus AI appeared first on D3 Security.
*** This is a Security Bloggers Network syndicated blog from D3 Security authored by Shriram Sharma. Read the original post at: https://d3security.com/blog/mssps-security-alerts-revenue-morpheus-ai/
如有侵权请联系:admin#unsafe.sh
