Early on in 2025, I described how criminals used fake CAPTCHA sites and a clipboard hijacker to provide instructions for website visitors that would effectively infect their own machines with an information stealer known as the Lumma Stealer.
ClickFix is the name researchers have since given to this type of campaign—one that uses the clipboard and fake CAPTCHA sites to trick users into running malicious commands themselves.
Later, we found that the cybercriminals behind it seemed to be running some A/B tests to figure out which infection method worked best: ClickFix, or the more traditional file download that disguises malware as a useful application.
The criminals probably decided to go with ClickFix, because they soon came up with a campaign that targeted Mac users to spread the infamous Atomic Stealer.
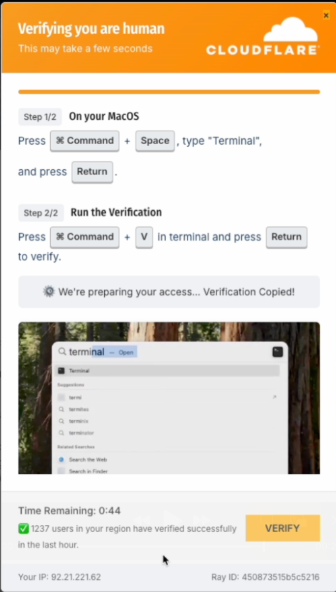
Now, as reported by researchers from Push Security, the attackers behind ClickFix have tried to make the campaign more “user-friendly.” The latest fake CAPTCHA pages include embedded video tutorials showing exactly how to run the malicious code.

The site automatically detects the visitor’s operating system and provides matching instructions, copying the right code for that OS straight to the clipboard—making typos less likely and infection more certain.
A countdown timer adds urgency, pressuring users to complete the “challenge” within a minute. When people rush instead of thinking things through, social engineering wins.
Unsurprisingly, most of these pages spread through SEO-poisoned Google search results, although they also circulate via email, social media, and in-app ads too.
How to stay safe
With ClickFix running rampant—and it doesn’t look like it’s going away anytime soon—it’s important to be aware, careful, and protected.
- Slow down. Don’t rush to follow instructions on a webpage or prompt, especially if it asks you to run commands on your device or copy-paste code. Attackers rely on urgency to bypass your critical thinking, so be cautious of pages urging immediate action. Sophisticated ClickFix pages add countdowns, user counters, or other pressure tactics to make you act quickly.
- Avoid running commands or scripts from untrusted sources. Never run code or commands copied from websites, emails, or messages unless you trust the source and understand the action’s purpose. Verify instructions independently. If a website tells you to execute a command or perform a technical action, check through official documentation or contact support before proceeding.
- Limit the use of copy-paste for commands. Manually typing commands instead of copy-pasting can reduce the risk of unknowingly running malicious payloads hidden in copied text.
- Secure your devices. Use an up-to-date real-time anti-malware solution with a web protection component.
- Educate yourself on evolving attack techniques. Understanding that attacks may come from unexpected vectors and evolve helps maintain vigilance. Keep reading our blog!
Pro tip: Did you know that the free Malwarebytes Browser Guard extension warns you when a website tries to copy something to your clipboard?
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.