ANY.RUN’s malware analysis and threat intelligence products are used by 15K SOCs and 500K analysts. Thanks to flexible API/SDK and read-made connectors, they seamlessly integrate with security teams’ existing software to expand threat coverage, reduce MTTR, and streamline performance.
Here’s how ANY.RUN’s solutions can transform your security.
Interactive Sandbox: Detect Evasive Phishing & Malware
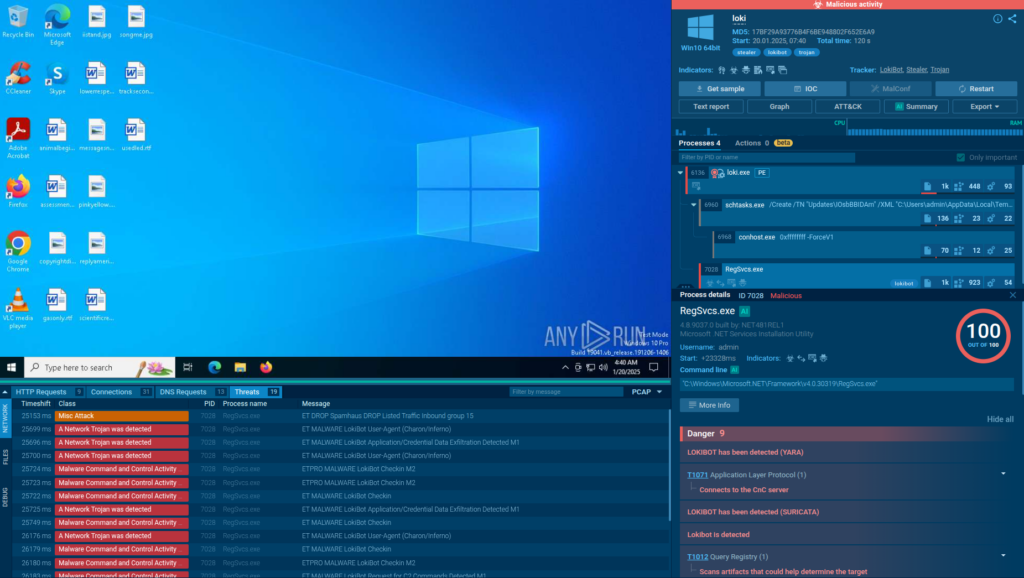
ANY.RUN’s Interactive Sandbox provides a real-time, cloud-based environment for detonating and analyzing suspicious files, URLs, and scripts across Windows, Linux, and Android systems. It lets analysts perform user actions like launching executables or opening links needed to trigger kill chains and force hidden payloads to reveal themselves, enabling faster detection and response.
The sandbox integrates with other solutions like SOAR platforms in an automated mode, which means it can fully detonate complex phishing and malware attacks on its own, including by solving CAPTCHAs and scanning QR codes.
The sandbox delivers immediate, actionable insights into the most evasive threats without risking production systems.
- Real-Time Threat Visibility: Observe attack chains as they unfold, with 90% of threats detected within 60 seconds, accelerating mean time to detect (MTTD).
- Higher Detection Rates: Uncover low-detection attacks (e.g., multi-stage malware, CAPTCHA-protected phishing) with up to 58% more threats identified, reducing missed incidents.
- Automated Efficiency: Cut manual analysis time with automated interactivity, reducing Tier 1 workload by 20% and enabling junior analysts to handle complex cases independently.
Connectors and integrations for Interactive Sandbox
If your solution is not on the list, you can easily set up a custom integration using ANY.RUN’s API or Python-based SDK (see docs on GitHub or PyPi).
Threat Intelligence Feeds: Expand Threat Coverage

Threat Intelligence Feeds deliver real-time, high-confidence malicious indicators (IPs, domains, URLs) supplied in STIX/TAXII. The indicators are sourced from analyses of the latest malware and phishing attacks performed by 15,000 organizations and 500,000 analysts in ANY.RUN’s Interactive Sandbox.
Thanks to being powered by one of the largest malware analysis communities, these feeds provide 99% unique IOCs, not found in other sources, that are updated in real time.
As a result, they give SOCs up-to-date visibility into threats almost as soon as they emerge. With TI Feeds, security teams can:
- Catch new attacks early: Live intel is streamed soon after the sandbox detection.
- Respond faster: IOCs come with sandbox reports with full context.
- Reduce workload: Filtering ensures only high-risk indicators are added.
Connectors and integrations for TI Feeds
If your solution is not on the list, you can easily set up a custom integration using ANY.RUN’s API or Python-based SDK (see docs on GitHub or PyPi).
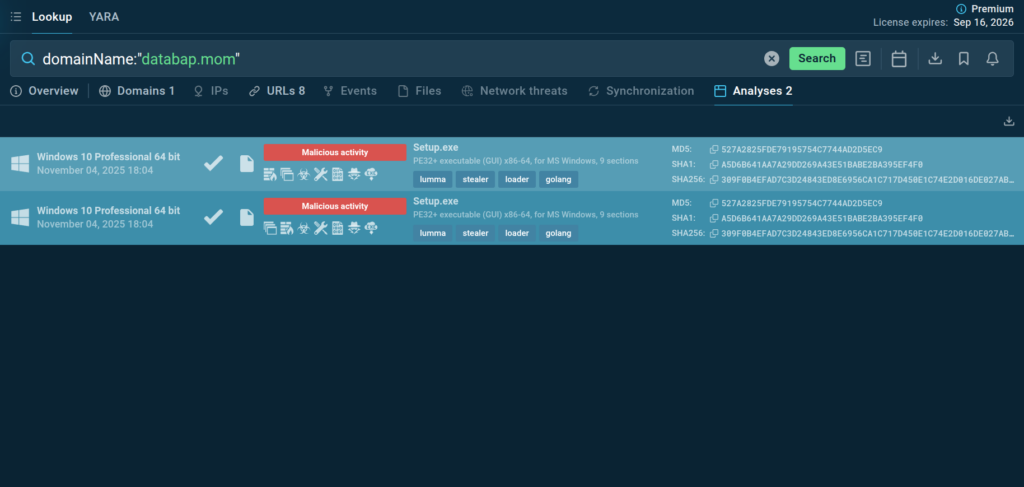
Threat Intelligence Lookup: Contextualize Alerts
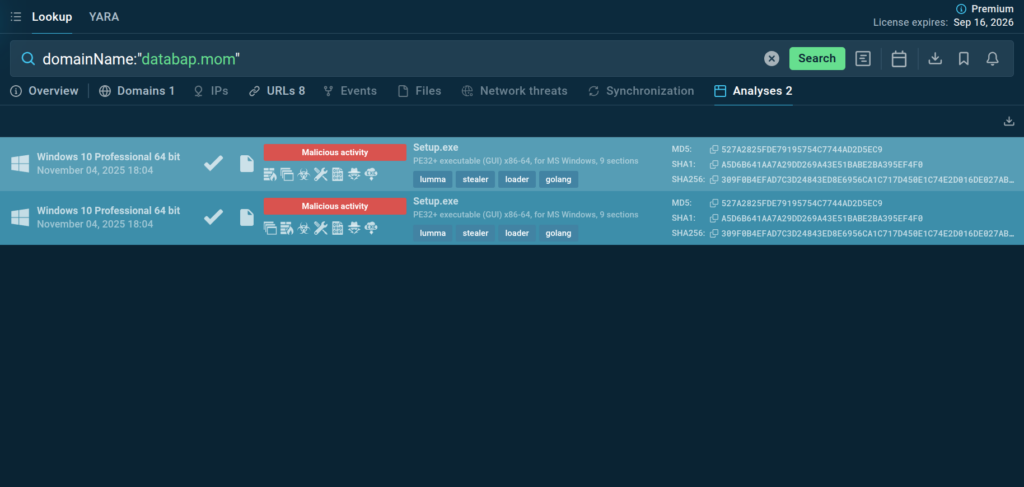
Threat Intelligence Lookup is a powerful solution designed to streamline and accelerate malware investigations, from proactive monitoring to incident response.
SOC teams can use it to quickly get actionable context for over 40 different types of Indicators of Compromise (IOCs), Attack (IOAs), and Behavior (IOBs), from an IP address and a domain to a mutex and a process name.
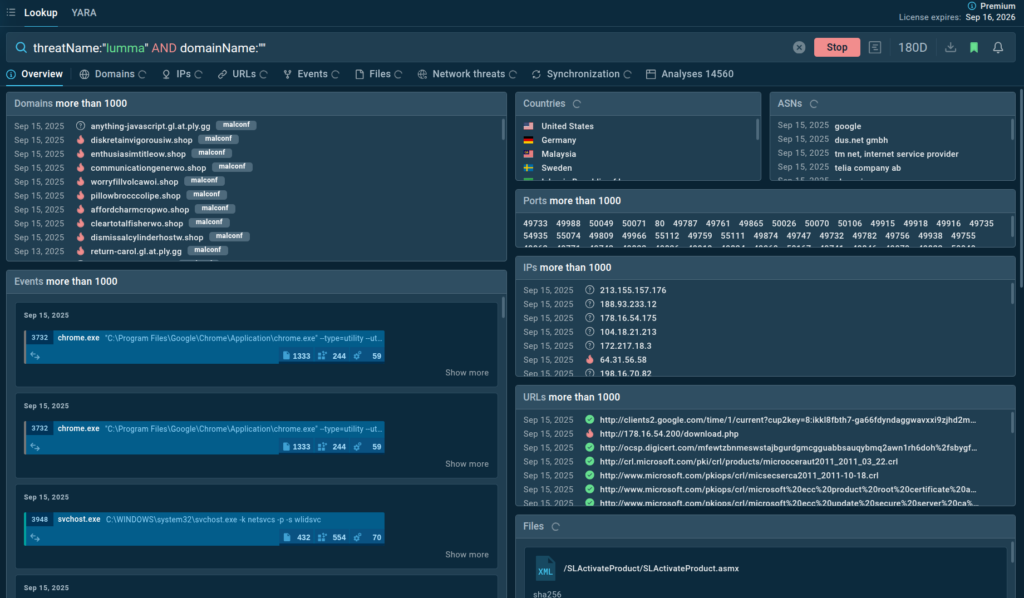
Each indicator in TI Lookup’s database is linked to a sandbox session, where it was observed, providing analysts with a complete view of the attack, including its TTPs.
- Triage alerts faster: Two-second access to millions of past analyses confirms if an IOC belongs to a threat, cutting triage time.
- Shorten response time: Indicator enrichment with behavioral context and TTPs guide precise containment strategies.
- Reduce unnecessary escalations: Provides Tier 1 analysts with the info to make decisions independently, reducing escalations to Tier 2.
Connectors and integrations for TI Lookup
If your solution is not on the list, you can easily set up a custom integration using ANY.RUN’s API or Python-based SDK (see docs on GitHub or PyPi).
Integrate ANY.RUN’s Solutions in Your SOC
Whether you want to uncover hidden threats in seconds, catch emerging attacks, or enrich alerts with actionable context, ANY.RUN equips your SOC with the visibility, speed, and efficiency needed to stay ahead.
With flexible API/SDK and ready-made connectors for leading platforms, implementation is smooth, and the impact is immediate: faster MTTR, higher detection rates, and a stronger defense posture.
Feel free to reach out to us about integrating ANY.RUN’s products in your SOC at [email protected].
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Ready to see the difference?