
嗯,用户让我用中文总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我需要理解文章的内容。文章讲的是Post SMTP插件的一个严重漏洞,影响超过40万WordPress站点。攻击者可以利用这个漏洞劫持管理员账户,完全控制网站。 接下来,我得找出关键点:漏洞名称CVE-2025-11833,评分9.8分,影响版本3.6.0及以下。问题出在构造函数缺少权限检查,导致未认证攻击者读取任意日志邮件,包括密码重置链接,进而接管账户。 修复版本是3.6.1,但仍有21万站点未更新。黑客从11月1日开始利用这个漏洞,Wordfence已经阻止了4500次攻击。 现在要将这些信息浓缩到100字以内。要包括漏洞名称、影响范围、评分、攻击后果、修复措施和当前状态。 可能的结构:Post SMTP插件存在严重漏洞(CVE-2025-11833),影响超40万WordPress站点。该漏洞允许攻击者读取邮件日志并接管管理员账户。修复版本已发布(3.6.1),但仍有大量站点未更新。黑客已开始利用此漏洞进行攻击。 </think> Post SMTP插件存在严重漏洞(CVE-2025-11833),影响超40万WordPress站点。该漏洞允许攻击者读取邮件日志并接管管理员账户。修复版本已发布(3.6.1),但仍有大量站点未更新。黑客已开始利用此漏洞进行攻击。 2025-11-4 22:0:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:42 收藏

Threat actors are actively exploiting a critical vulnerability in the Post SMTP plugin installed on more than 400,000 WordPress sites, to take complete control by hijacking administrator accounts.
Post SMTP is a popular email delivery solution marketed as a feature-rich and more reliable replacement of the default ‘wp_mail()’ function.
On October 11, WordPress security firm Wordfence received a report from researcher ‘netranger’ about an email log disclosure issue that could be leveraged for account takeover attacks.
The issue, tracked as CVE-2025-11833, received a critical-severity score of 9.8 and impacts all versions of Post SMTP from 3.6.0 and older.
The vulnerability stems from the lack of authorization checks in the ‘_construct’ function of the plugin’s ‘PostmanEmailLogs’ flow.
That constructor directly renders logged email content when it is requested without performing capability checks, allowing unauthenticated attackers to read arbitrary logged emails.
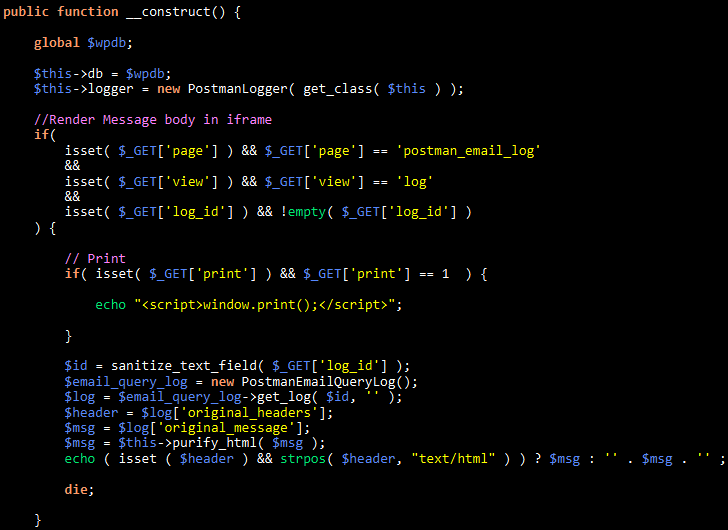
Source: Wordfence
The exposure includes password reset messages with links that allow changing an administrator’s password without the need of a legitimate account holder, potentially leading to account takeover and full site compromise.
Wordfence validated the researcher’s exploit on October 15 and fully disclosed the issue to the vendor, Saad Iqbal, on the same day.
A patch arrived on October 29, with Post SMTP version 3.6.1. Based on WordPress.org data, roughly half of the plugin’s users have downloaded it since the release of the patch, leaving at least 210,000 sites vulnerable to admin takeover attacks.
According to Wordfence, hackers started exploiting CVE-2025-11833 on November 1. Since then, the security firm has blocked over 4,500 exploit attempts on its customers.
Given the active exploitation status, website owners using Post SMTP are advised to move to version 3.6.1 immediately or disable the plugin.
In July, PatchStack revealed that Post SMTP was vulnerable to a flaw that allowed hackers to access email logs containing full message content, even from a subscriber level.
That flaw, tracked as CVE-2025-24000, had the same repercussions as CVE-2025-11833, allowing unauthorized users to trigger password resets, intercept messages, and take control of administrator accounts.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

