好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读全文,抓住主要信息。 文章讲的是Trustwave SpiderLabs的威胁情报团队发现三个知名网络犯罪团伙Scattered Spider、ShinyHunters和LAPSUS$合并成一个联盟,称为Scattered LAPSUS$ Hunters(SLH)。他们使用Telegram作为主要平台,提供勒索服务(EaaS),利用各自的名字制造恐惧以获取更高收益。SLH还结合了其他团伙的资源,展示了技术上的多样性和成熟的操作模式。 接下来,我需要将这些要点浓缩到100字以内。重点包括:三个团伙合并、使用Telegram、提供EaaS、利用品牌制造恐惧、技术能力以及作为威胁集体的代表。 最后,确保语言简洁明了,不使用任何开头词如“这篇文章”或“内容总结”。直接描述即可。 </think> 三个知名网络犯罪团伙Scattered Spider、ShinyHunters和LAPSUS$合并为Scattered LAPSUS$ Hunters(SLH),通过Telegram提供勒索服务(EaaS),利用品牌制造恐惧以获取更高收益。该联盟结合了多个团伙的资源和技术能力,展示了网络犯罪威胁集体的专业化趋势。 2025-11-4 14:0:6 Author: www.trustwave.com(查看原文) 阅读量:16 收藏
6 Minute Read
Trustwave SpiderLabs’ Cyber Threat Intelligence team is tracking the recent emergence of what appears to be the consolidation of three well-known threat groups into a “federated alliance” that offers, among its activities, Extortion-as-a-Service (EaaS). The collective comprises Scattered Spider, ShinyHunters, and LAPSUS$. The group heavily uses a public encryption communication service as its primary operating base and allows its EaaS affiliates to use the member’s very well-known names to create fear, which it claims will generate a higher financial return. Emerging in early August 2025, this federated alliance first appeared on Telegram, presenting itself as a hybrid entity blending reputational and operational traits from three of the most recognized The Com-linked collectives of recent years - The Com being an informal cybercriminal milieu known for fluid collaboration and brand-sharing - Scattered Spider, ShinyHunters, and LAPSUS$. Over time, its associations expanded, displaying affiliations with other The Com-adjacent clusters such as CryptoChameleon and Crimson Collective, suggesting a deliberate attempt to merge established names into a new, unified narrative. The first verified channel linked to the group appeared on August 8, 2025, under the handle “scattered lapsu$ hunters – The Com HQ SCATTERED SP1D3R HUNTERS.” From inception, Telegram functioned as the primary operational environment and the nucleus of brand identity. While the group intermittently hosted clear-web and onion-based data leak sites to stage limited proof-of-compromise (PoC) materials, Telegram remained central to its narrative construction — the stage where members performed, coordinated, and curated public visibility. Using Telegram is not new or unique. Many threat actors use Telegram for advertising, announcements, or basic communication with the public. However, what sets SLH apart is its active use of Telegram as both a performative marketing and public messaging platform - a style more typical of hacktivist or attention-driven groups. Financially motivated actors (SLH is one of them) usually seek only the minimum visibility needed to manage victims, payments, or pressure campaigns. As activity matured, administrative posts began to include signatures referencing the “SLH/SLSH Operations Centre,” a self-applied label carrying symbolic weight that projected the image of an organized command structure that lent bureaucratic legitimacy to otherwise fragmented communications. Since its debut, the group’s Telegram channels have been removed and recreated at least sixteen times under varying iterations of the original name — a recurring cycle reflecting platform moderation and the operators’ determination to sustain this specific type of public presence despite disruption. One of the latest versions, “scattered LAPSUS$ hunters 7.0,” was also removed but quickly replaced, signaling the group’s resilience through adaptive naming and coordinated re-establishment. As these cycles unfolded, SLH’s arrival coincided with turbulence across the broader cybercriminal underground. The collapse of BreachForums — long regarded as the successor to RaidForums and a key nexus for data leaks and recruitment — created a vacuum. Into that vacuum, Scattered LAPSUS$ Hunters inserted itself, repackaging reputational assets from defunct collectives and inheriting fragments of their audiences. By adopting recognizable branding and recycling reputational capital, the group reasserted legitimacy within The Com network. Soon after, SLH publicly announced an Extortion-as-a-Service (EaaS) model, formalizing its operational ambition and signaling market alignment with the broader cyber-extortion economy. This step revealed not only opportunism but intent: SLH positioned itself as a performer and service provider, using spectacle to attract customers, attention, and recruits. If its structure echoed old collectives, its messaging refined them. SLH channels consistently combined sensationalist rhetoric with theatrical claims of data theft, fusing entertainment with intimidation. Posts frequently accused Chinese state actors of exploiting vulnerabilities allegedly targeted by SLH, while mocking Western law enforcement, particularly the FBI and NCA. This focus on US and UK agencies evidently signals which jurisdictions are at greatest risk and highlights the attention SLH members pay to these authorities. Across iterations, channel content also alternated between proof-of-compromise displays, interactive polls, and coercive messaging. Snippets of leaked data served as teasers; polls invited participation in harassment or doxing campaigns; and occasional monetary incentives blurred the line between recruitment and crowdsourced extortion. Parallel sales posts offered stolen credentials and exploits, while threats to executives and agencies amplified pressure and visibility. Although data exfiltration and extortion remain its main revenue channels, recurring mentions of “Sh1nySp1d3r Ransomware” also indicate aspirations toward ransomware operations. — A claim yet to be verified. Together, these patterns show a deliberate fusion of technical signaling and social performance, and while financial gain appears to be the main motivation, the group’s reliance on attention, social validation, and audience reactions suggests an additional layer of social dependence. This positions SLH somewhere between financially motivated cybercrime and attention-driven hacktivism, blending monetary incentives with performative, socially contingent behavior. There’s no clear evidence that SLH targets fall within a traditional hacktivist or socially motivated realm. While their behavior - relying heavily on public attention, social validation, and performative messaging - is unusual for purely financially motivated actors, their posts and campaigns do not convey any coherent political, ecological, religious, or other social agenda. The group’s messaging, aside from its antagonism of law enforcement, appears primarily driven by financial incentives, even if delivered in a style that borrows from attention-driven or hacktivist practices. This deliberate blending of social performance and monetary objectives blurs traditional classifications but does not indicate genuine hacktivist motivations. At the same time, behind the loud narrative lies a more controlled reality. Although roughly thirty active handles have been observed across associated channels, ranging from operators to provocateurs — linguistic patterns, emoji usage, and posting cadence suggest that fewer than five individuals drive the core operation, the majority of whom appear to originate from the ShinyHunters brand, which evidently forms the nucleus of SLH. Among these, “shinycorp” (appearing under aliases such as @sp1d3rhunters, @sloke48, and @shinyc0rp) functions as the principal orchestrator, issuing breach claims, mocking enforcement efforts, and coordinating responses to takedowns. “Alg0d” operates as a high-visibility broker persona, primarily focused on data sales and negotiation, while auxiliary identities such as “UNC5537,” “Rey,” and “SLSHsupport” amplify narratives and sustain channel engagement. One of the more technically intriguing members, however, is “yuka” (also known as Yukari or Cvsp). This persona presents itself as an exploit or initial access broker (IAB) and has been historically associated with offers of zero-day vulnerabilities targeting CRM and SaaS ecosystems. Available evidence suggests that Cvsp’s technical proficiency — spanning exploit development, malware engineering, and vulnerability brokerage — is genuine. Previous associations with the BlackLotus UEFI bootkit and Medusa rootkit lend credibility to this assessment, further reinforced by reputation vouches from ShinyHunters and the consistent use of escrow services in high-value transactions. Each consistently active persona acts simultaneously as an amplifier and a shield, complicating attribution, ensuring continuity even when accounts are removed, and, despite periodic disputes and peer ridicule, SLH continues to frame itself as part of The Com — a loosely federated community rather than a fixed hierarchy. Overall, this self-positioning may represent the first consolidated alliance among mature The Com-related clusters, leveraging mutual notoriety while maintaining fluid cooperation and opportunistic overlap. Beyond identity management, SLH also demonstrates technical versatility consistent with experienced operators. Its activity suggests a continued prioritization of cloud-first extortion and data theft, focusing on high-value aggregation points such as SaaS providers, corporate CRMs, Database systems, and other large data lakes offering immediate ROI. Notably, this technical proficiency appears to reflect a convergence of skills and strengths drawn from multiple merged clusters and operators, suggesting that SLH leverages complementary expertise across intrusion, exploitation, and social engineering domains to enhance operational impact. Credential harvesting, often through AI-automated vishing or spearphishing, is typically followed by lateral movement for privilege escalation, persistence, and rapid data exfiltration. SLH also exhibits non-trivial exploit development and acquisition capabilities, including tooling that resembles zero-day research specifically targeting CRMs, DBMSs, and SaaS platforms. Since its inception, affiliated posts have claimed multiple corporate compromises, most notably CVE-2025-61882 (Oracle E-Business Suite), a vulnerability widely associated with Cl0p ransomware operators, suggesting potential code leakage, sharing, or exploit brokerage. Historical references support the continuity of this focus: the persona Yukari previously claimed exploitation of Oracle Access Manager in 2021, suggesting a possible lineage of resources and expertise. Taken together, these behaviors illustrate an operational structure that combines social engineering, exploit development, and narrative warfare — a blend more characteristic of established underground actors than opportunistic newcomers. The emergence of Scattered LAPSUS$ Hunters (SLH) in mid-2025 appears not as the rise of a new collective, but as the strategic reassertion of mature The Com-aligned operators adapting to disruption and instability. Through theatrical branding, reputational recycling, cross-platform amplification, and layered identity management, the actors behind SLH have shown a mature grasp of how perception and legitimacy can be weaponized within the cybercriminal ecosystem. SLH likely represents the first de facto alliance bridging previously semi-autonomous clusters within The Com network — unifying extortion, brokerage, and influence operations under a cohesive narrative. This consolidation underscores an emerging trend toward professionalized cybercriminal branding, where control of narrative and audience engagement function as strategic assets to exploit development or data theft. As this hybrid ecosystem evolves, its use of identity fluidity, social amplification, growing tailored exploitation development capabilities, and adaptive collaboration will likely shape the next phase of data-extortion activity into 2026. Understanding this interplay between performance, persistence, and perception will be essential for anticipating how such threat collectives sustain momentum in an increasingly moderated, and intelligence-aware underground landscape.
Figure 1. The main page of the Scattered LAPSUS$ Hunters data-leak site (DLS), announcing Salesforce as one of its victims.The Launch of a Consolidated Threat Group
Contextual Emergence, Operational Persistence, and Platform Cycles

Figure 2. Excerpt of a Telegram conversation showing member reactions and administrative responses following a channel takedown, referencing breachforums[.]hn, later seized by law enforcement.
Table 1. Observed Telegram channels and activity periods.
Figure 3. Channel announcement advertising an Extortion-as-a-Service offering and soliciting customers.Narrative Patterns and Messaging Themes

Figure 4. Telegram post inviting channel subscribers to participate, basically as freelancers, in pressure campaigns and doxing for payment or influence.
Figure 5. Channel announcement referencing “Sh1nySp1d3r” as a proposed ransomware offering.Persona Architecture and Sockpuppetry

Table 2. Consolidated administrative and affiliated personas.
Figure 6. GitHub repository page attributed to “Yukari/Cvsp” showing projects labeled BlackLotus (UEFI bootkit) and Medusa (modular rootkit).
Figure 7. An HTML message posted on a DLS page targeting a named individual and engaging in reputation/peer warfare.Tactics, Techniques, and Procedures (TTPs)

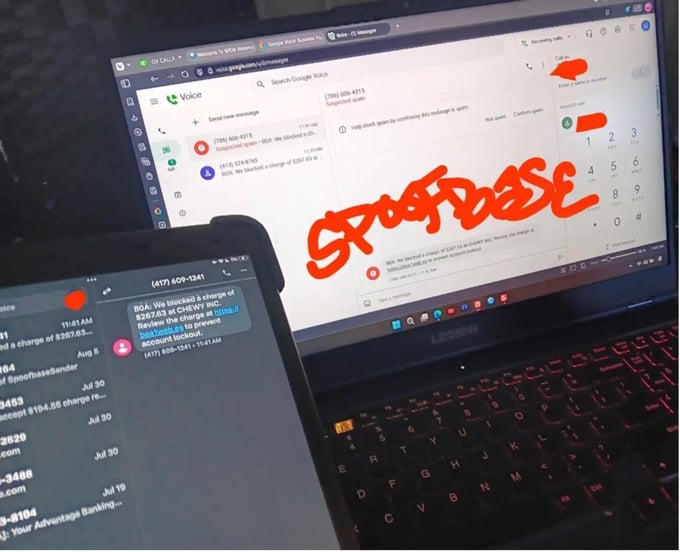
Figure 8. Screenshot shared in the channel by a member, depicting an operator running automated vishing tools that abuse Google Voice to scale social-engineering attempts.
Figure 9. Code snippet or exploit proof-of-concept circulated within channels claiming to target CVE-2025-31324 (SAP NetWeaver).
Figure 10. Telegram post in which the group claims initial possession of an Oracle E-Business Suite zero-day (CVE-2025-61882), its leakage, and expresses frustration that Cl0p exploited it first.
Figure 11. Terminal output published by the group that demonstrates a local privilege escalation exploit (CVE-2023-2163) with access to /etc/shadow.Conclusion
如有侵权请联系:admin#unsafe.sh