软件供应链攻击在10月创历史新高,比4月高出32%。Qilin和Akira等勒索软件团伙通过利用关键漏洞和零日漏洞攻击SaaS及IT服务提供商。云安全威胁和AI钓鱼活动也加剧了问题。受害者涵盖金融、能源、政府等行业。防范措施包括加强第三方风险评估、网络微分段和强化访问控制等。 2025-11-4 13:1:11 Author: cyble.com(查看原文) 阅读量:41 收藏
Software supply chain attacks in October were 32% above previous records, according to Cyble data.
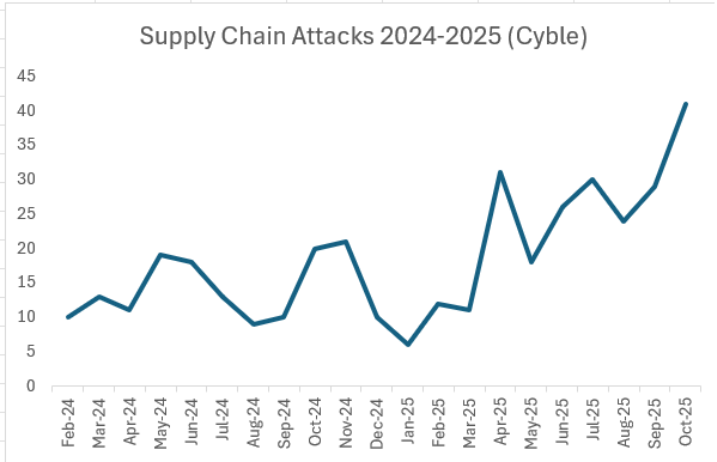
Software supply chain attacks hit a new record in October that was more than 30% higher than the previous record set in April 2025.
Cyble’s data – based on attacks claimed by threat actors on dark web data leak sites – shows that threat actors claimed 41 supply chain attacks in October, 10 more than the previous high seen in April.
Supply chain attacks have remained elevated since April, averaging more than 28 a month since then, a rate that is more than twice as high as the 13 attacks per month seen between early 2024 and March 2025 (chart below).

A combination of critical and zero-day IT vulnerabilities and threat actors actively targeting SaaS and IT service providers have been the primary drivers of the recent surge in supply chain attacks, and the sustained increase suggests that the risk of supply chain attacks may remain elevated going forward. Cloud security threats and AI-based phishing campaigns have also played a role in the growing number of supply chain incidents.
Every one of the 24 sectors tracked by Cyble has been hit by a supply chain incident this year. Because of the rich target they represent and their downstream customer reach, IT and IT services companies have been by far the most targeted, with 107 supply chain attacks so far this year. Financial services, transportation, technology, and government have also been hit with much greater than average frequency (chart below).

Recent Significant Supply Chain Attacks
Qilin and Akira have been the top two ransomware groups in 2025, and both have also claimed an above-average share of supply chain attacks.
Akira recently claimed responsibility for a cyberattack targeting a major open-source software project. The group claims to possess 23GB of data, including sensitive employee information as well as financial documents, internal confidential files, and reports related to software issues and internal operations.
Akira also claimed multiple attacks on IT service providers, including a company that develops software solutions for government and law enforcement agencies, a provider of compliance and environmental data management software for industrial and energy clients, and a U.S.-based company providing IT, cybersecurity, and consulting solutions for government, intelligence, and defense sectors. In the latter case, the group claims to possess more than 19GB of data, including financial records, sensitive employee and customer data, confidential documents, NDAs, and other files containing personal and corporate data.
Qilin claimed responsibility for breaching a U.S.-based financial technology company that provides integrated software and services for payment processing, transaction management, and financial infrastructure solutions. Stolen data allegedly includes confidential hardening reports, internal SharePoint directories, and a list of IT infrastructure employees from a major financial services company.
Qilin also claimed an attack on a U.S.-based company providing technology solutions for law enforcement, criminal justice, public safety, and security sector, and source code for proprietary software products was among the allegedly stolen data, in addition to accounting and HR data and client payment information from various law enforcement agencies.
Qilin claimed attacks on three U.S. energy cooperatives, including the theft of project information, obsolescence equipment details, contractual agreements with U.S. government entities, and customer billing information.
Another claimed Qilin breach involved a U.S.-based cybersecurity and cloud services provider offering IT infrastructure, managed services, and compliance solutions for healthcare and dental organizations. The threat actors claimed they gained access to downstream customer environments through clear-text credentials stored in Word and Excel documents hosted on the company’s systems. The stolen data reportedly includes customers’ personal information, financial records, and medical documentation. Posted samples include unencrypted passwords from client systems, financial documents, and medical reports.
A newly identified ransomware group, Kyber, leaked data allegedly stolen from a major U.S.-based defense and aerospace contractor that provides communication, surveillance, and electronic warfare systems. The group leaked over 141GB of data consisting of project files, internal builds, databases, and backup archives.
The BlackShrantac hacking group claimed responsibility for a breach of a South Korean cybersecurity and physical security services provider. According to the hacking group, approximately 24GB of data was stolen, containing customer information and requirements, network and infrastructure data, HR and payroll data, e-commerce information, and cybersecurity technical documentation, including website source code, API keys, and configuration files. To substantiate their claims, BlackShrantac released several sample files, which appear to show access to internal documentation, technical blueprints, Excel sheets with configuration details, and other sensitive company data.
The Cl0p ransomware group claimed several victims from its exploitation of Oracle E-Business Suite vulnerabilities, including a major global energy technology company and a major U.S. university.
The threat group Crimson Collective claimed to have compromised a GitLab instance of a major U.S. technology provider, including the theft of 800 Customer Engagement Reports. The threat actors allegedly gained access to a client infrastructure using credentials and tokens found within the stolen repositories.
Protecting Against Supply Chain Attacks
Protecting against software supply chain attacks can be challenging because these partners and suppliers are, by nature, trusted, but security audits and assessing third-party risk should become standard cybersecurity practices.
Organizations should also build in controls and resilience wherever possible to limit the extent of any attacks. Such controls include:
- Network microsegmentation
- Strong access controls, allowing no more access than is required, with frequent verification
- A strong source of user identity and authentication, including multi-factor authentication and biometrics, and machine authentication with device compliance and health checks
- Encryption of data at rest and in transit
- Ransomware-resistant backups that are immutable, air-gapped, and isolated as much as possible
- Honeypots that lure attackers to fake assets for early breach detection
- Proper configuration of API and cloud service connections
- Monitoring for unusual activity with SIEM, Active Directory monitoring, and data loss prevention (DLP) tools
- Routinely assessing and confirming controls through audits, vulnerability scanning, and penetration tests
The most effective place to control software supply chain risks is in the continuous integration and development (CI/CD) process, so carefully vetting partners and suppliers and requiring good security controls in contracts are essential for improving third-party security. Services like Cyble’s third-party risk intelligence can help you get started on this process. By making security a buying criterion, vendors will be more likely to respond with better security controls and documentation.
如有侵权请联系:admin#unsafe.sh