好的,我现在需要帮用户总结这篇文章的内容,控制在100个字以内。首先,我得通读全文,抓住关键点。 文章主要讲澳大利亚政府警告Cisco IOS XE设备存在漏洞CVE-2023-20198,被BadCandy Webshell攻击。攻击者利用这个漏洞安装恶意软件,获取管理员权限。文章提到有超过400台设备受到影响,建议修补漏洞和限制Web UI访问。 接下来,我需要把这些信息浓缩成一句话。要注意不使用“文章内容总结”之类的开头,直接描述内容。 可能的结构是:澳大利亚警告Cisco设备漏洞被BadCandy攻击,导致控制权被接管,建议修补和限制访问。 检查字数是否在100字以内,确保信息准确且简洁。 </think> 澳大利亚警告称,未修补的Cisco IOS XE设备因CVE-2023-20198漏洞遭BadCandy Webshell攻击,导致管理权限被接管。建议立即修补漏洞并限制Web UI访问以防止再次被利用。 2025-11-1 17:41:0 Author: securityaffairs.com(查看原文) 阅读量:6 收藏
BadCandy Webshell threatens unpatched Cisco IOS XE devices, warns Australian government
Pierluigi Paganini
November 01, 2025

Australia warns of attacks on unpatched Cisco IOS XE devices exploiting CVE-2023-20198, allowing BadCandy webshell install.
The Australian Signals Directorate (ASD) warns of ongoing attacks on unpatched Cisco IOS XE devices exploiting CVE-2023-20198, allowing BadCandy webshell infections and admin takeover.
“Cyber actors are installing an implant dubbed ‘BADCANDY’ on Cisco IOS XE devices that are vulnerable to CVE-2023-20198. Variations of the BADCANDY implant have been observed since October 2023, with renewed activity notable throughout 2024 and 2025.” reads the alert issued by the ASD.
An attacker can exploit the vulnerability CVE-2023-20198 (CVSS score 10) in its IOS XE Software to gain administrator privileges and take over vulnerable routers. The advisory published by the vendor states that the exploitation of the vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access.
The flaw affects physical and virtual devices running with the Web User Interface (Web UI) feature enabled and that have the HTTP or HTTPS Server feature in use.
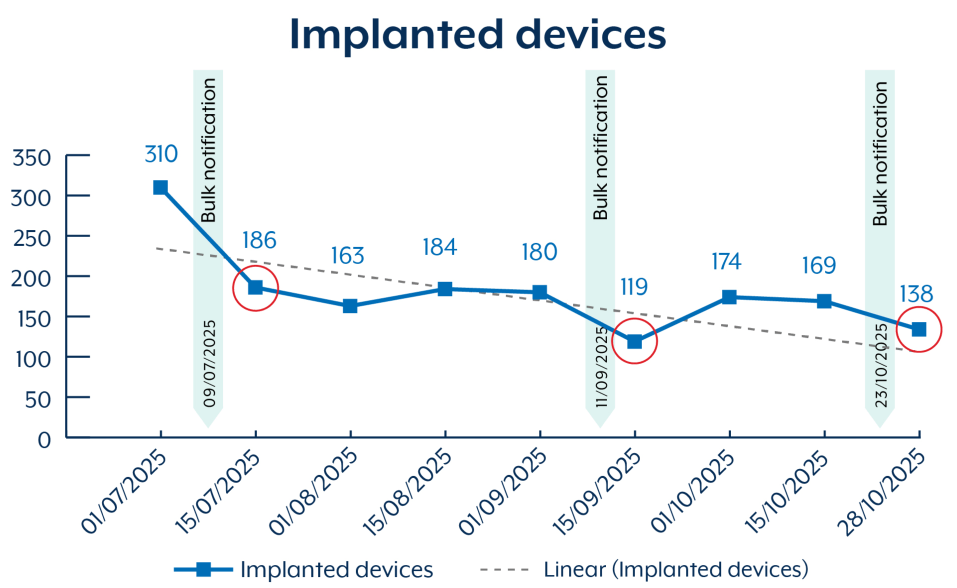
Since July 2025, the Australian agency observed over 400 devices potentially compromised with BADCANDY in the country. As of late October 2025, over 150 devices compromised with BADCANDY in Australia are still exposed online.
BADCANDY is a Lua-based webshell exploiting CVE-2023-20198 on Cisco IOS XE devices. It’s non-persistent after reboot, but attackers may retain access via stolen credentials. Patching and restricting web UI access are required to prevent re-exploitation.
“ASD believes actors are able to detect when the BADCANDY implant is removed and are re-exploiting the devices. This further highlights the need to patch against CVE-2023-20198 to avoid re-exploitation.” continues the alert.
ASD is notifying affected entities, providing patching, reboot, hardening, and incident response guidance. The agency will continue alerts to ensure operators know their devices were compromised.
Government experts recommend operators to remove BADCANDY by reviewing and deleting unauthorized privileged accounts, checking unknown tunnel interfaces, and monitoring configuration changes via TACACS+ logging.
Organizations should follow Cisco guidance: disable the HTTP server feature and apply the IOS XE hardening guide to prevent future BADCANDY compromises.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Cisco IOS XE)
如有侵权请联系:admin#unsafe.sh
