
好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,抓住主要信息。 文章讲的是澳大利亚政府警告针对未修补的Cisco设备的网络攻击,利用CVE-2023-20198漏洞植入BadCandy webshell。这个漏洞允许攻击者远程创建管理员账户并接管设备。Cisco在2023年10月修复了这个漏洞,但两个月后公开的 exploits 导致大规模攻击。 澳大利亚当局指出,BadCandy在2024和2025年仍在使用,很多设备仍未修补。一旦安装,BadCandy允许攻击者以root权限执行命令,重启后会被擦除,但攻击者可以重新植入。自2025年7月以来,超过400台设备被感染,仍有150多台受感染。 尽管感染数量下降,但同一漏洞被重新利用。ASD正在通知受害者并提供补救建议,并联系无法确定所有者的设备的ISP。文章还提到该漏洞曾被中国等国家行为者利用。 现在我要把这些信息浓缩到100字以内。重点包括:澳大利亚警告网络攻击、针对未修补的Cisco设备、利用CVE-2023-20198漏洞、植入BadCandy webshell、影响严重、超过400台设备被感染、ASD建议修复和加固设备。 最后检查一下字数是否符合要求,并确保内容准确。 </think> 澳大利亚警告称,针对未修补的 Cisco IOS XE 设备的网络攻击持续进行,利用 CVE-2023-20198 漏洞植入 BadCandy 网壳。该漏洞允许远程攻击者创建管理员账户并接管设备。自 2025 年 7 月以来,超 400 台设备被感染,目前仍有 150 多台受控。澳大利亚信号 Directorate 建议修复漏洞并加固设备以应对持续威胁。 2025-10-31 15:45:18 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏

The Australian government is warning about ongoing cyberattacks against unpatched Cisco IOS XE devices in the country to infect routers with the BadCandy webshell.
The vulnerability exploited in these attacks is CVE-2023-20198, a max-severity flaw that allows remote unauthenticated threat actors to create a local admin user via the web user interface and take over the devices.
Cisco fixed the flaw in October 2023, which was then marked as an actively exploited issue. A public exploit became available two weeks later, fueling mass exploitation for backdoor planting on internet-exposed devices.
The Australian authorities have warned that variants of the same Lua-based BadCandy web shells are still used in attacks throughout 2024 and 2025, indicating that many Cisco devices remain unpatched.
Once installed, BadCandy allows remote attackers to execute commands with root privileges on compromised devices.
The webshell is wiped from the devices upon reboot. However, given the lack of a patch on those devices and assuming the web interface remains accessible, the attackers can easily re-introduce it.
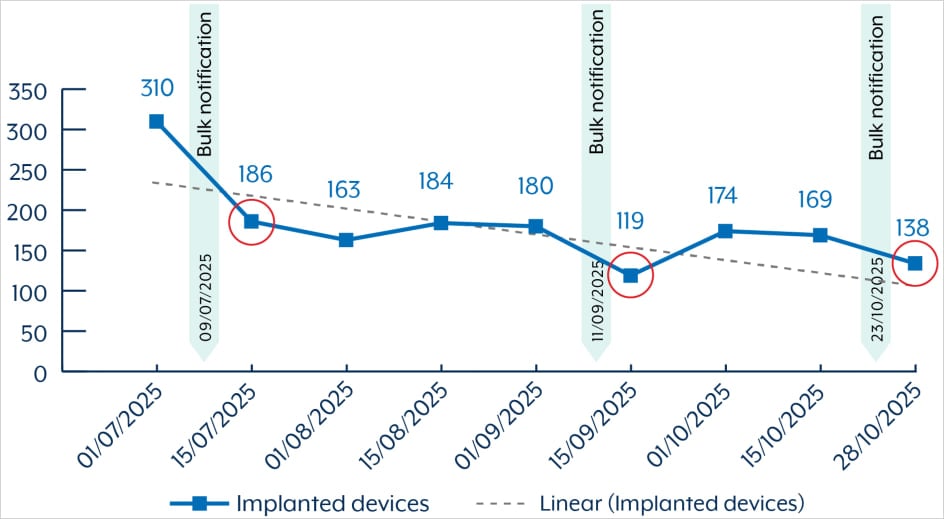
"Since July 2025, ASD assesses over 400 devices were potentially compromised with BADCANDY in Australia," reads the bulletin. "As at late October 2025, there are still over 150 devices compromised with BADCANDY in Australia."
Source: ASD
Although the number of infections is declining, the agency has seen signs of re-exploitation of the flaw against the same endpoints, even though the breach entities were appropriately alerted.
According to the agency, the attackers can detect when the BadCandy implant gets removed and target the same device to re-introduce it.
In response to the ongoing attacks, the Australian Signals Directorate is sending notifications to victims that include instructions on patching, hardening devices, and conducting incident response. For devices whose owners cannot be determined, the ASD is asking internet service providers to contact victims on their behalf.
The ASD mentions that the flaw has been previously leveraged by state actors such as the Chinese' Salt Typhoon,' who are considered responsible for a series of attacks against large telecommunication service providers across the U.S. and Canada.
The agency believes that, even though BadCandy can theoretically be used by anyone, the recent spikes can be attributed to "state-sponsored cyber-actors."
Administrators of Cisco IOS XE systems worldwide, including in Australia, should follow the vendor's mitigation recommendations in the security bulletin.
Cisco has also published a detailed hardening guide for IOS XE devices.
如有侵权请联系:admin#unsafe.sh
