好的,我现在需要帮用户总结这篇文章的内容。用户的要求是用中文,控制在100字以内,不需要特定的开头,直接写描述。 首先,我得通读整篇文章,抓住主要信息。文章讲的是学术研究人员开发了一个名为TEE.Fail的侧信道攻击方法。这个攻击可以提取CPU中可信执行环境(TEE)里的秘密信息,比如Intel的SGX和TDX,AMD的SEV-SNP。 接下来,攻击方式是针对DDR5系统的内存总线插入攻击,成本不到1000美元。TEE本来是高安全区域,用于保护敏感数据如加密密钥。但研究人员发现现代实现中的架构折衷导致了漏洞。 具体来说,TEE从客户端移到服务器级硬件,使用了AES-XTS加密和去掉了部分保护机制以提升性能。通过物理访问和内核驱动修改,攻击者可以捕获内存信号,提取密钥并伪造认证。 最后,虽然攻击复杂且需要物理接触,在现实场景中威胁不大。厂商们已知悉问题并正在修复中。 现在我要把这些要点浓缩到100字以内。要包含攻击名称、目标、方法、影响和厂商回应。确保语言简洁明了。 </think> 学术研究人员开发了一种名为TEE.Fail的侧信道攻击方法,可从CPU的可信执行环境(如Intel SGX/TDX和AMD SEV-SNP)中提取敏感数据。该攻击针对DDR5内存总线,成本低于1000美元,利用AES-XTS加密特性捕获内存信号,提取加密密钥并伪造认证,对 confidential computing 构成威胁。 2025-10-28 17:15:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏
Academic researchers developed a side-channel attack called TEE.Fail, which allows extracting secrets from the trusted execution environment in the CPU, the highly secure area of a system, such as Intel's SGX and TDX, and AMD's SEV-SNP.
The method is a memory-bus interposition attack on DDR5 systems that could be successfully done by computer hobbyists a cost of less than $1,000.
Trusted Execution Environments (TEEs) are “confidential computing” hardware within the main processor that ensure confidentiality and integrity of sensitive data, like cryptographic keys used for authentication and authorization.
This environment is isolated from the operating system and creates protected regions of memory where code and data can run securely.
Researchers from Georgia Tech and Purdue University note that modern implementations of Intel SGX, Intel TDX, and AMD SEV-SNP are no longer as secure as advertised, due to architectural trade-offs in recent generations.
Specifically, TEEs moved from client CPUs to server-grade hardware using DDR5 memory, which adopted deterministic AES-XTS memory encryption and stripped away memory integrity and replay protections in favor of performance and scalability.
Their experiments confirmed that it is possible to exploit these weaknesses for key extraction and attestation forgery. TEE.Fail is the first DDR5-based ciphertext attack, extending prior DDR4 work like WireTap and BatteringRAM.
Attack and implications
The attack requires physical access to the target as well as root-level privileges for Kernel driver modification, but no chip-level expertise.
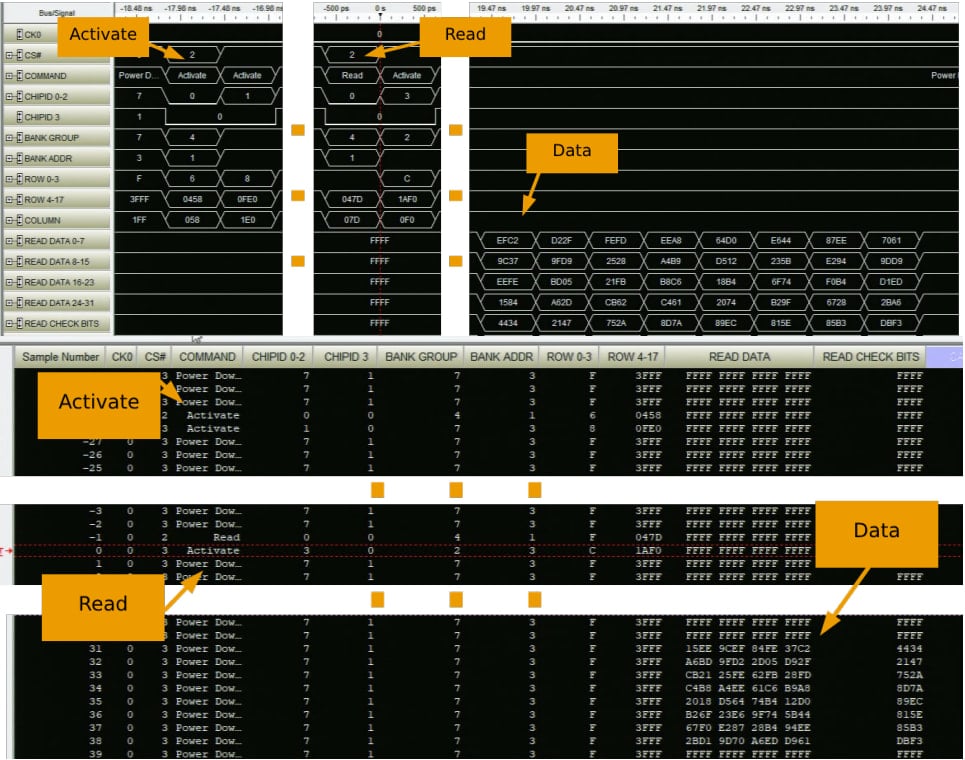
In the technical paper, the researchers explain that they were able to capture the signal reliably by reducing the system’s memory clock to 3200 MT/s (1.6 GHz). For this, they attached a RDIMM riser and a custom probe isolation network between a DDR5 DIMM and the motherboard.

Source: tee.fail
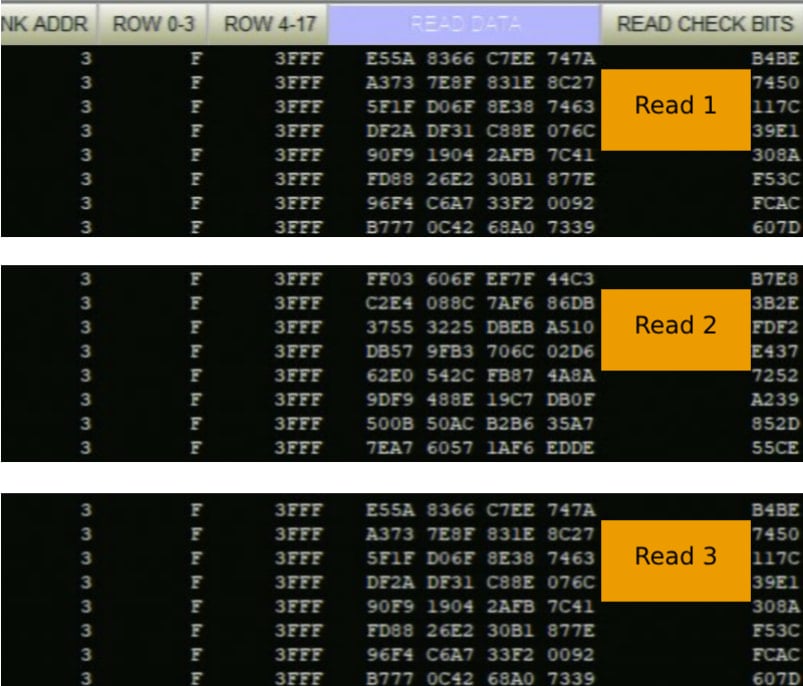
With the interposer connected to a logic analyzer, the attacker records DDR5 command/address and data bursts, so they can see ciphertexts written to and read from physical DRAM locations.
Source: tee.fail
To achieve their goal with Intel's SGX, the researchers had to force the data in virtual addresses into a single memory channel that they could observe through the interposer.
Through an interface for physical addresses that Intel exposed to the Memory Address Translation component, the researchers could "further expose this decoding interface to userspace via sysfs."
This let them find the info for determining the DIMM location for the physical address.
However, SGX uses the OS kernel for physical memory allocation and the researchers had to "modify the kernel’s SGX driver to accept a virtual and physical address pair as a parameter to be stored in global kernel memory."
The researchers say that they created an SGX enclave that bombarded a specific memory virtual address with read and write operations. This let them verify that the encrypted ciphertext observed on the memory interposer was a deterministic function of the physical memory address and its contents.
"To check that encryption is deterministic, we instruct our enclave to perform a series of write and read operations to a fixed virtual address in enclave memory, capturing the ciphertext read data after each step using our logic analyzer," they explain.
Because of the use of the AES-XTS encryption, where a piece of information is encrypted to the same output every time, the team wrote known values to the observable physical addresses to build a ciphertext to value mapping.
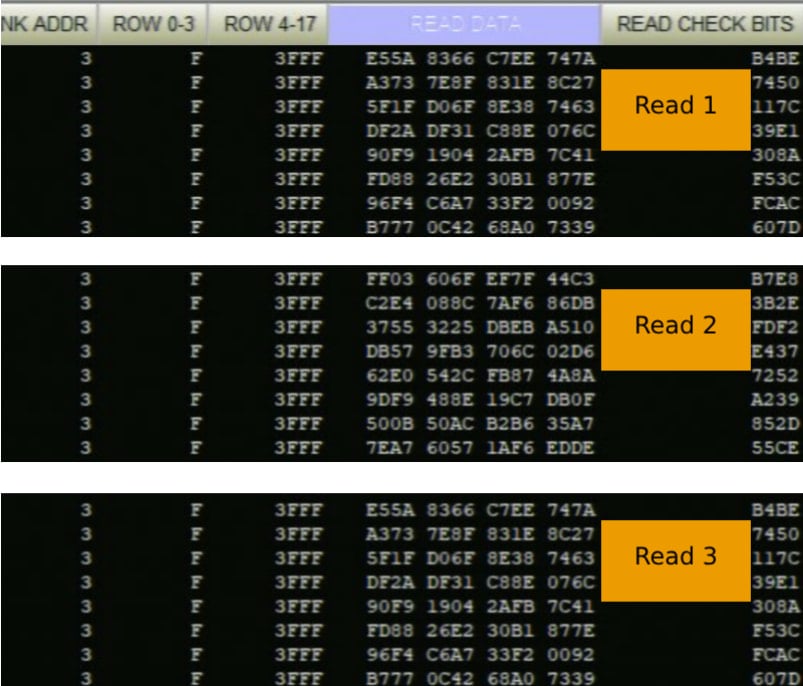
Source: tee.fail
Then, by triggering and recording targeted crypto operations, they observe encrypted accesses to intermediate table entries and recover the per-signature nonce digits.
From the recovered nonce and the public signature, they reconstruct private signing keys, which lets them forge valid SGX/TDX quotes and impersonate genuine TEEs.
The same approach was used to extract signing keys from OpenSSL running in a virtual machine protected by AMD's SEV-SNP.
It is worth noting that the attacks against AMD SEV-SNP still work even when the “Ciphertext Hiding” security option is enabled.
The researchers showcased attacks that allowed them to:
- Forge TDX attestations on Ethereum BuilderNet to access confidential transaction data and keys, enabling undetectable frontrunning.
- Fake Intel and NVIDIA attestations to run workloads outside TEEs while appearing legitimate.
- Extract ECDH private keys directly from enclaves, recovering the network’s master key, and fully breaching confidentiality.
Through TEE.Fail, the researchers were able to demonstrate that it is possible to take control of TEE execution and observe specific virtual addresses. The researchers also targeted a Xeon server and obtained the Provisioning Certificate Key (PCK) - used for verifying the identity of a device.
TEE.Fail is a complext attack that requires physical access. This makes it less practical in a real-world scenario and its complexity is far from a threat to the average user.
The researchers reported their findings to Intel in April, to AMD in August, and to NVIDIA in June. All three vendors acknowledged the issues and stated they were working on mitigations and adaptations for the confidential computing threat model, with plans to publish official statements when the TEE.Fail paper becomes public.
BleepingComputer has asked Intel, AMD, and NVIDIA to share their statements for inclusion in this report, but we have not heard back by publication.
如有侵权请联系:admin#unsafe.sh
