
嗯,用户让我总结一下这篇文章的内容,控制在一百个字以内。首先,我需要通读文章,抓住主要信息。 文章讲的是一个新的安卓恶意软件家族,叫Herodotus。它通过随机延迟注入来模仿人类行为,避开安全软件的检测。作为MaaS服务,提供给网络犯罪分子,用于诈骗活动。 接下来,我得提炼关键点:Herodotus是MaaS,模仿人类输入行为,通过随机延迟避免检测,主要针对意大利和巴西用户,通过短信钓鱼传播。 然后,确保总结在100字以内,并且不使用“文章内容总结”这样的开头。直接描述内容即可。 最后,检查一下是否涵盖了所有重要信息:恶意软件名称、功能、传播方式、目标地区等。确保语言简洁明了。 </think> 新的安卓恶意软件家族Herodotus通过随机延迟模仿人类行为以规避检测,并作为恶意软件即服务(MaaS)提供给网络犯罪分子用于诈骗活动。该恶意软件主要针对意大利和巴西用户,并通过短信钓鱼传播。 2025-10-28 13:15:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:18 收藏

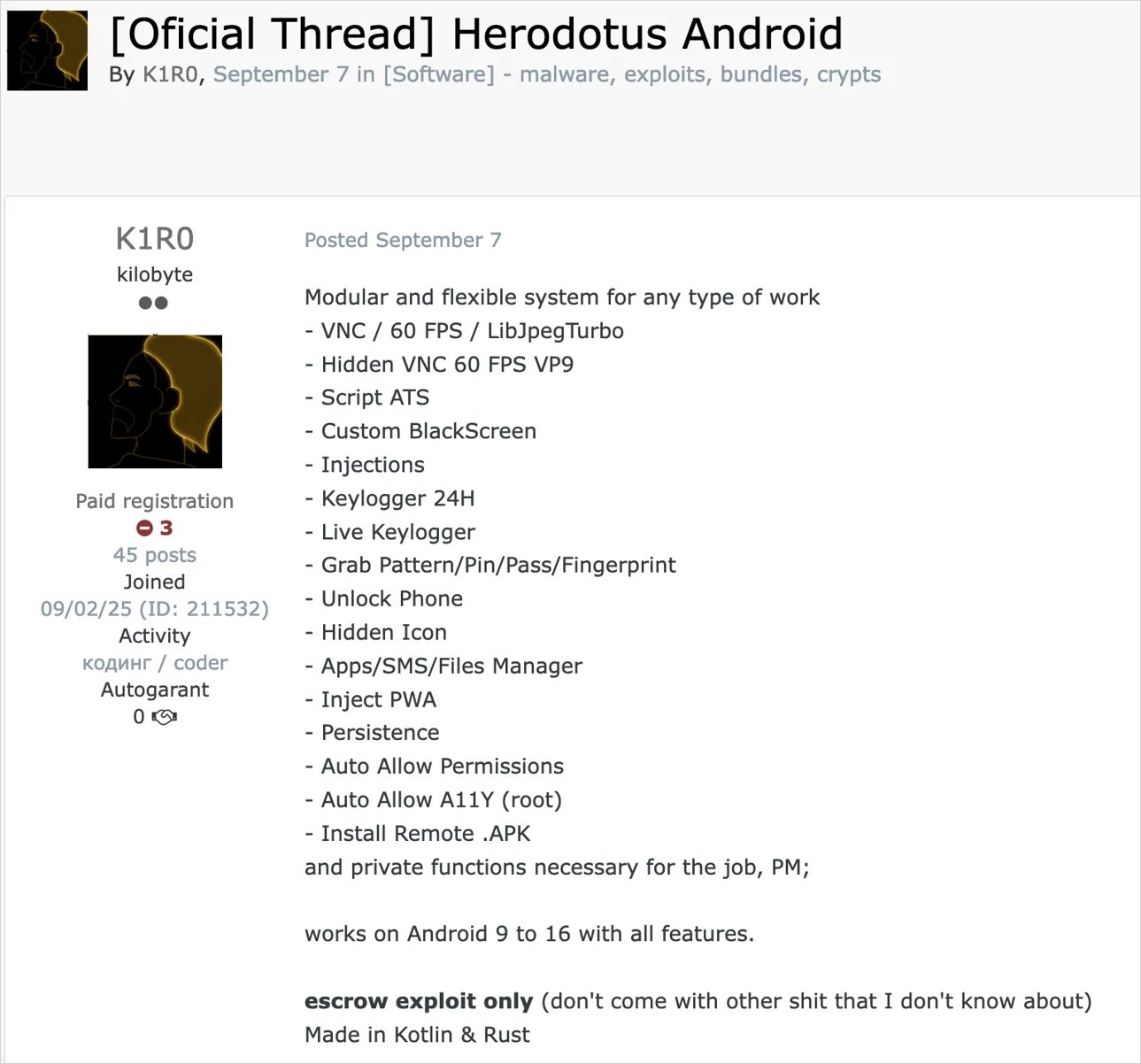
A new Android malware family, Herodotus, uses random delay injection in its input routines to mimic human behavior on mobile devices and evade timing-based detection by security software.
Herodotus, according to Threat Fabric, is offered as a malware-as-a-service (MaaS) to financially motivated cybercriminals, believed to be the same operators behind Brokewell.
Although the malware is still in development, clients of the new MaaS platform are currently deploying it against Italian and Brazilian users through SMS phishing (smishing) text messages.
Source: Threat Fabric
The malicious SMS contains a link to a custom dropper that installs the primary payload and attempts to bypass Accessibility permission restrictions present in Android 13 and later.
The dropper opens Accessibility settings, prompts the user to enable the service, and then displays an overlay window that shows a fake loading screen, hiding the permission-granting steps in the background.
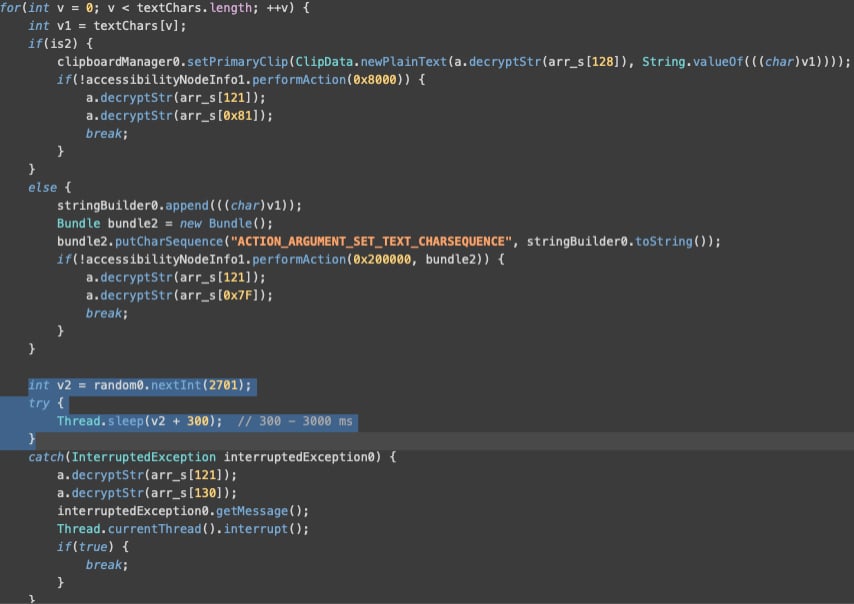
Having granted itself access to these sensitive permissions, Herodotus can now interact with the Android user interface, such as tapping at specific screen coordinates, swiping, going back, and entering text (clipboard paste or keyboard typing).
However, automated actions, such as typing, on the user interface may not match the same rhythm or cadence as humans, making them noticeable to security software that looks for unusual patterns in behavior.
To evade detection, the malware includes a 'humanizer' mechanism for the text input action, which causes it to type with random delays of 0.3 to 3 seconds, mimicking human typing and evading detection.
"Such a randomisation of delay between text input events does align with how a user would input text," explains Threat Fabric.
"By consciously delaying the input by random intervals, actors are likely trying to avoid being detected by behaviour-only anti-fraud solutions spotting machine-like speed of text input."
Source: Threat Fabric
Threat Fabric says that delays in Android malware are typically used to allow app UI to respond to inputs before moving to the next action, adding that Herodotus' randomized delays are a completely novel take, most likely implemented to evade behavioral detection systems.
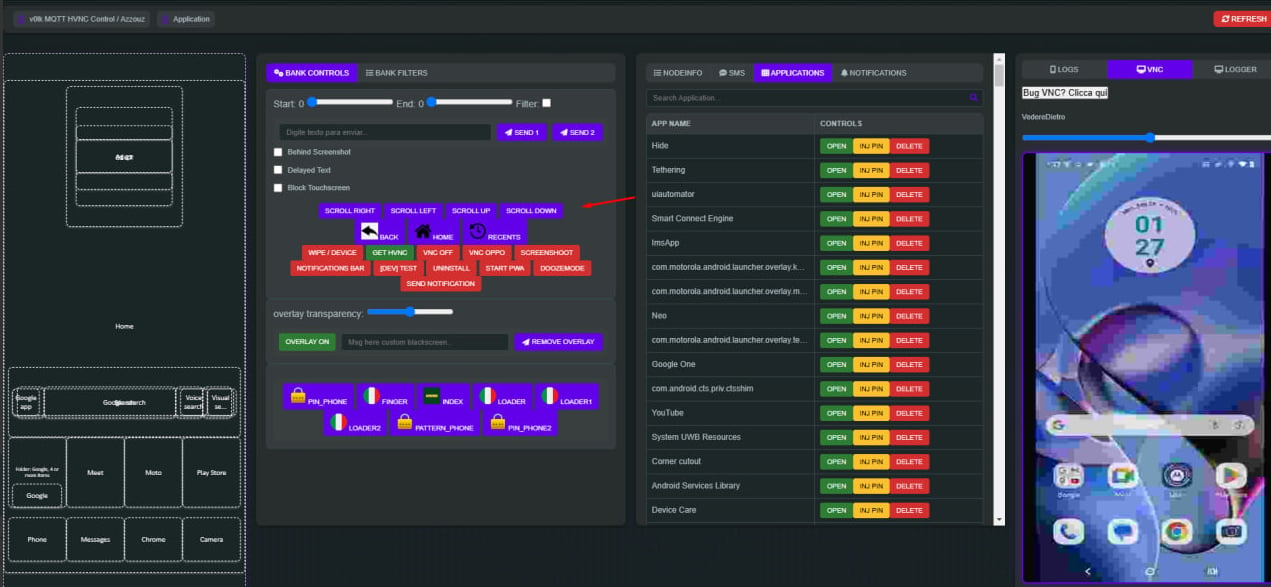
Apart from the above features, Herodotus also provides operators with the following:
- Control panel with options for custom SMS text
- Overlay pages mimicking banking and crypto apps to steal account credentials
- Opaque overlays that hide fraud from the victim
- SMS stealer for two-factor authentication code interception
- Capturing screen content
Source: Threat Fabric
Currently, Threat Fabric reports that Herodotus is spread by several threat actors, based on the detection of seven distinct subdomains, indicating its adoption in the wild has already begun.
To mitigate this risk, Android users should avoid downloading APK files from outside Google Play unless they explicitly trust the publisher and ensure Play Protect is active on their device.
Even with these precautions, it is essential to scrutinize and revoke risky permissions, such as Accessibility, for newly installed apps.
如有侵权请联系:admin#unsafe.sh
