好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,抓住关键信息。 文章主要讲的是 Lazarus 黑客组织,他们针对欧洲的国防公司发起了名为 Operation DreamJob 的攻击。攻击手段是通过伪造的招聘邮件,诱骗员工点击带有恶意软件的 PDF 文件,进而控制目标电脑。Lazarus 组织与朝鲜有关联,之前也参与过很多重大网络攻击事件。 文章提到这次攻击的目标是 UAV(无人机)技术相关的公司,特别是为乌克兰提供设备的欧洲国防公司。攻击者的目标很可能是窃取无人机和武器的数据,支持朝鲜的无人机开发项目。此外,Lazarus 使用了多种恶意软件工具,如 ScoringMathTea RAT 和 trojanized 应用程序,这些工具帮助他们在目标系统中保持隐蔽。 总结下来,关键点包括:Lazarus 组织、Operation DreamJob、伪造招聘邮件、攻击欧洲国防公司、窃取 UAV 数据、支持朝鲜无人机发展等。我需要把这些信息浓缩到100字以内,并且不使用“文章内容总结”之类的开头。 可能的结构是:Lazarus 通过 Operation DreamJob 攻击欧洲国防公司,利用伪造招聘邮件和恶意软件获取 UAV 数据,支持朝鲜无人机项目。 现在检查字数是否合适,并确保所有关键点都涵盖进去。 </think> Lazarus 黑客组织通过“Operation DreamJob”行动针对欧洲三家国防公司发起网络攻击,利用伪装成招聘广告的钓鱼邮件传播恶意软件 ScoringMathTea RAT 和 trojanized 应用程序。此次行动旨在窃取无人机(UAV)技术相关数据以支持朝鲜的无人机研发计划,并利用 AES-128/ChaCha20 加密和内存加载技术规避检测。 2025-10-23 18:40:31 Author: securityaffairs.com(查看原文) 阅读量:6 收藏
Lazarus targets European defense firms in UAV-themed Operation DreamJob

North Korean Lazarus hackers targeted 3 European defense firms via Operation DreamJob, using fake recruitment lures to hit UAV tech staff.
North Korea-linked Lazarus APT group (aka Hidden Cobra) launched Operation DreamJob, compromising three European defense companies. Threat actors used fake recruiter profiles to lure employees into UAV technology roles, aiming to gain access to sensitive information through targeted social engineering.
The Operation DreamJob has been active since at least 2020, threat actors have been observed using social engineering techniques to compromise its targets, with fake job offers as the lure.
The Lazarus APT has been active since 2009 and is behind major incidents like the Sony hack, WannaCry, and global cyberheists.
ESET reports that Lazarus’ latest Operation DreamJob targets UAV technology, reflecting North Korea’s push to develop drones modeled on Western designs.
ESET observed new Operation DreamJob attacks starting in March 2025, targeting three European defense firms, a metal engineering company, an aircraft parts maker, and a defense contractor. The three European defense firms producing equipment used in Ukraine, attackers likely aimed at stealing UAV and weapons data. Lazarus gained access via fake job offers carrying trojanized PDFs, deploying the ScoringMathTea RAT for full control. Targets were linked to UAV technology, suggesting espionage aligned with North Korea’s drone development efforts and its cooperation with Russia in the Ukraine war.
North Korea’s UAV program heavily relies on reverse engineering and IP theft, with drones like the Saetbyol-4 and Saetbyol-9 mimicking models manufactured by US firms. Evidence suggests Pyongyang uses cyberespionage, via Lazarus and related APTs, to steal UAV designs and manufacturing know-how. Operation DreamJob likely sought proprietary data on Western UAVs, aiding North Korea’s expanding drone production efforts.
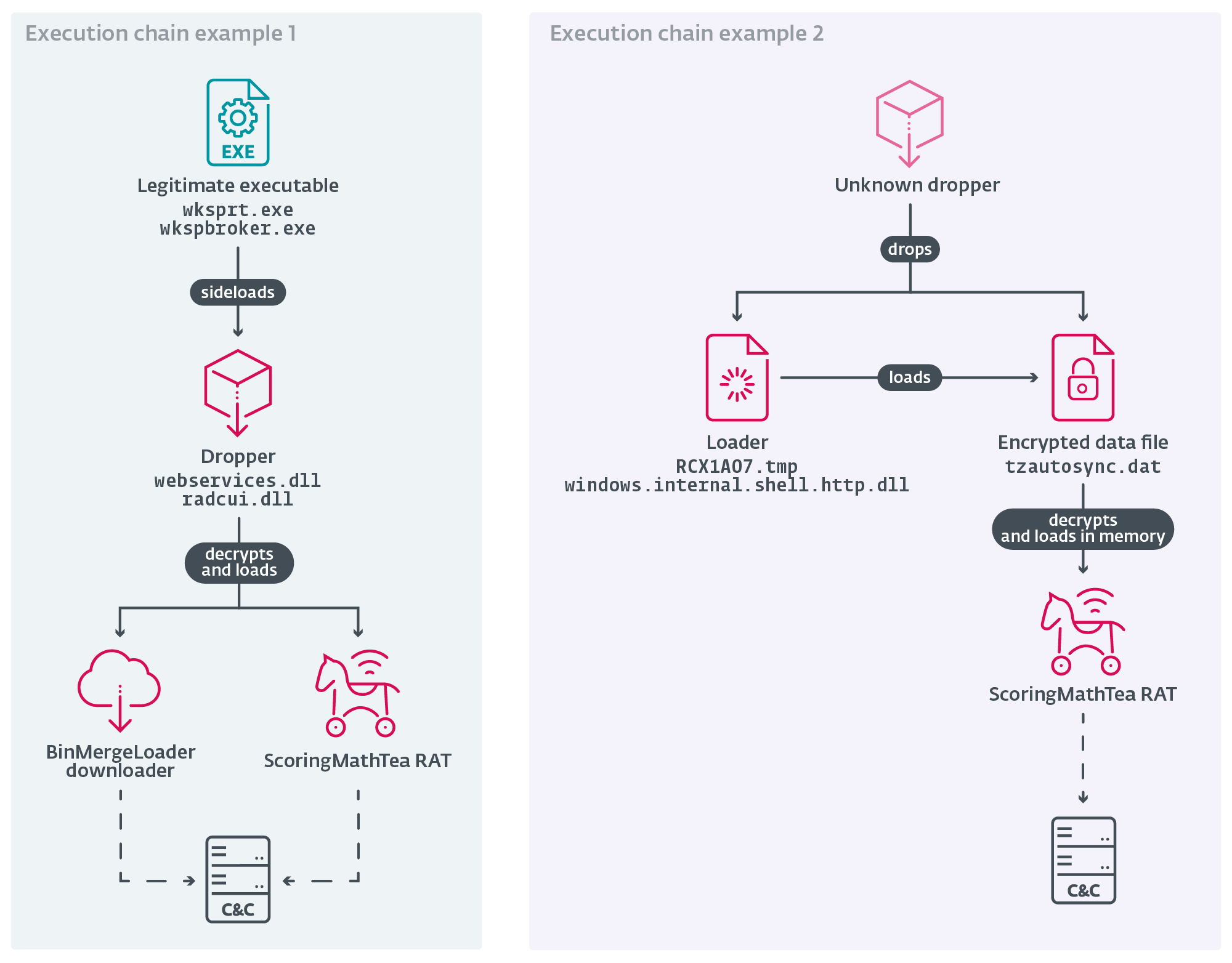
In 2025 Operation DreamJob, Lazarus shifted tools into two tiers: early-stage droppers/loaders/downloaders and main-stage payloads like the ScoringMathTea RAT. Researchers saw trojanized MuPDF, TightVNC, Notepad++ plugins, a libpcre loader, QuanPinLoader, BinMergeLoader, and a DirectInput-style dinput.dll. Loaders decrypt AES-128/ChaCha20 payloads and load them in memory via MemoryModule.

The researchers pointed out that main implants never appear unencrypted on disk. BinMergeLoader mirrors Mandiant’s MISTPEN and abuses Microsoft Graph tokens. It is interesting to note that submissions came from Italy and Spain; one dropper bore the internal name DroneEXEHijackingLoader.dll, linking the campaign to UAV-focused targets.
ScoringMathTea is a Lazarus-linked RAT that supports approximately 40 commands, combining file/process control, data exfiltration, and remote command execution.
“The implemented functionality is the usual required by Lazarus: manipulation of files and processes, exchanging the configuration, collecting the victim’s system info, opening a TCP connection, and executing local commands or new payloads downloaded from the C&C server.” reads ESET’s report. “The current version does not show any dramatic changes in its feature set or its command parsing. So the payload is probably receiving continuous, rather minor improvements and bug fixes.”
First seen in 2022 via Airbus-themed job lures, it has since targeted firms in Portugal, Germany, India, Poland, the UK, and Italy. The malicious code is likely a key Operation DreamJob payload, it evolves through minor updates and shares traits with Lazarus tools like LightlessCan.
For nearly three years, Lazarus has consistently used ScoringMathTea and trojanized open-source apps in Operation DreamJob, achieving polymorphism that evades detection but not attribution. Despite media exposure, employee awareness in key sectors remains low. The campaign likely sought UAV-related data to support North Korea’s expanding drone program.
For nearly three years, Lazarus has consistently used ScoringMathTea and trojanized open-source apps in Operation DreamJob, achieving polymorphism that evades detection but not attribution. Despite media exposure, employee awareness in key sectors remains low. The campaign likely sought UAV-related data to support North Korea’s expanding drone program.
“Also, even with widespread media coverage of Operation DreamJob and its use of social engineering, the level of employee awareness in sensitive sectors – technology, engineering, and defense – is insufficient to handle the potential risks of a suspicious hiring process.” concludes the report.
“Although alternative hypotheses are conceivable, there are good reasons to think that this Operation DreamJob campaign was in no small part intended to collect sensitive information on UAV-related technology. Considering North Korea’s current efforts at scaling up its drone industry and arsenal, it seems likely that other organizations active in this sector will whet the appetite of North Korea-aligned threat actors in the near future.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, North Korea)
如有侵权请联系:admin#unsafe.sh