嗯,用户让我用中文总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写描述即可。 首先,我需要快速浏览文章内容。文章主要讲的是一个与中国有关的网络间谍组织“盐台风”(Salt Typhoon)在2025年7月利用Citrix NetScaler Gateway漏洞入侵了一家欧洲电信公司。Darktrace检测到了这次攻击,并详细描述了攻击过程,包括利用SoftEther VPN进行初始访问,以及使用恶意软件和C2服务器来隐藏活动。最终Darktrace成功阻止了这次入侵,并认为这次攻击很可能是盐台风所为。 接下来,我要把这些信息浓缩到100字以内。重点包括:盐台风组织、利用Citrix漏洞、入侵欧洲电信公司、Darktrace检测并阻止、使用恶意软件和C2服务器。 然后,我需要确保语言简洁明了,不使用复杂的术语,同时保持信息的完整性。可能的结构是:时间、事件、方法、结果。 最后,检查字数是否符合要求,并确保没有使用禁止的开头语。 </think> 中国关联的网络间谍组织“盐台风”利用Citrix漏洞入侵欧洲电信公司,Darktrace检测并阻止了此次攻击。 2025-10-21 11:27:5 Author: securityaffairs.com(查看原文) 阅读量:21 收藏
China-Linked Salt Typhoon breaches European Telecom via Citrix exploit

China-linked Salt Typhoon hacked a European telecom in July 2025 via a Citrix NetScaler Gateway exploit for initial access.
A European telecom firm was targeted in July 2025 by China-linked APT group Salt Typhoon (also known as Earth Estries, FamousSparrow, GhostEmperor, UNC5807, RedMike)), which exploited a Citrix NetScaler Gateway to gain initial access.
In late 2024, a large-scale Chinese cyberespionage campaign targeted global telecoms was exposed and attributed by the US to state-backed group Salt Typhoon.
In December 2024, President Biden’s deputy national security adviser Anne Neuberger said that China-linked APT group Salt Typhoon breached telecommunications companies in dozens of countries.
The Wall Street Journal reported that the senior White House official revealed that at least eight U.S. telecommunications firms were compromised in the attack.
The Salt Typhoon hacking campaign, active for 1–2 years, has targeted telecommunications providers in several dozen countries, according to a U.S. official.
Darktrace detected cyber espionage activity targeting a European telecom firm in July 2025, consistent with China-linked Salt Typhoon tactics.
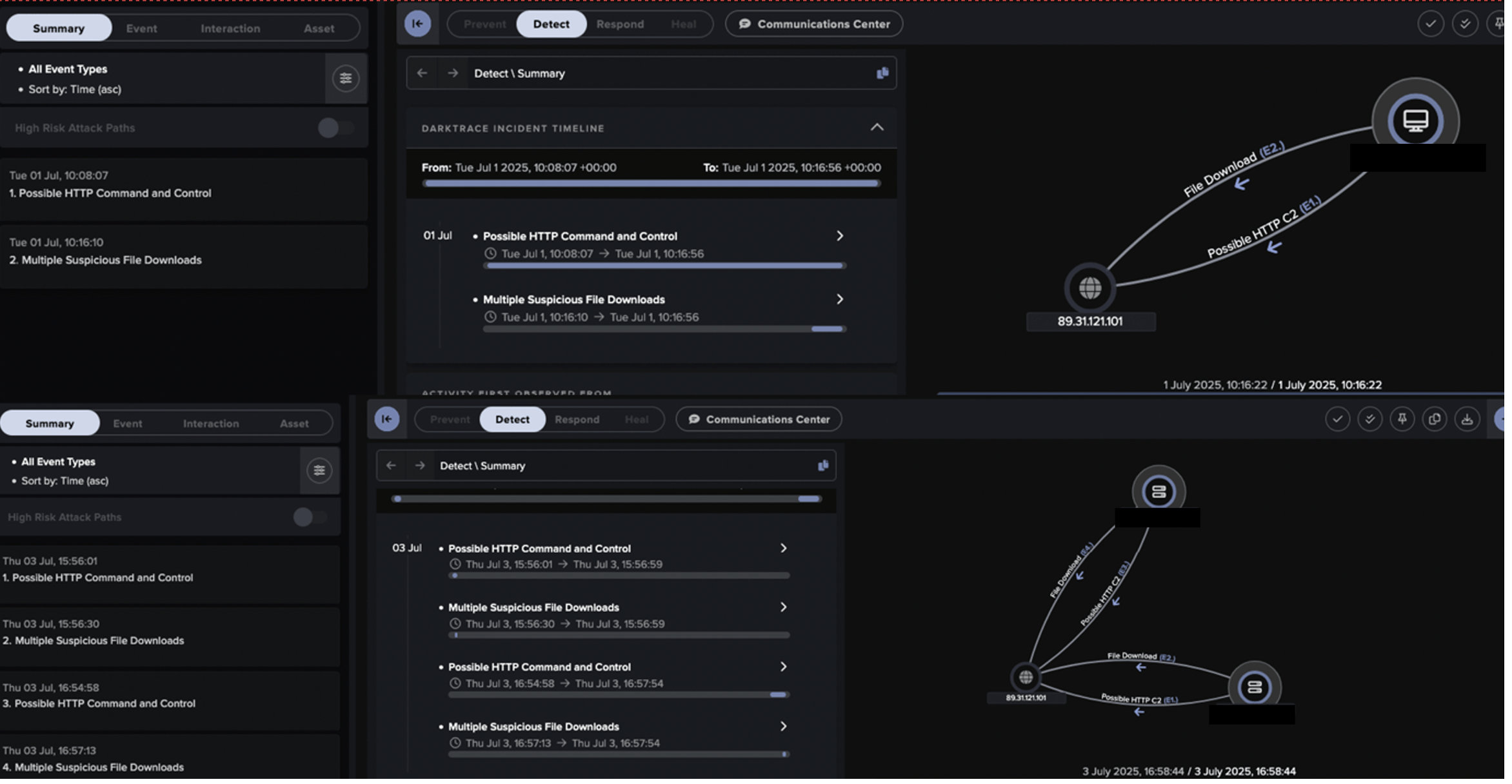
The attackers exploited a Citrix NetScaler Gateway for initial access, pivoting to Citrix VDA hosts via a SoftEther VPN endpoint.
“The intrusion likely began with exploitation of a Citrix NetScaler Gateway appliance in the first week of July 2025. From there, the actor pivoted to Citrix Virtual Delivery Agent (VDA) hosts in the client’s Machine Creation Services (MCS) subnet.” reads the report published by DarkTrace. “Initial access activities in the intrusion originated from an endpoint potentially associated with the SoftEther VPN service, suggesting infrastructure obfuscation from the outset.”
The nation-state actors deployed the SNAPPYBEE (Deed RAT) backdoor through DLL sideloading using legitimate antivirus executables (Norton, Bkav, IObit) to evade detection.
The attackers used LightNode VPS servers for C2, communicating via HTTP and an unknown TCP protocol to evade detection. The backdoor sent POST requests mimicking Internet Explorer traffic, with URIs like “/17ABE7F017ABE7F0”. One C2 domain, aar.gandhibludtric[.]com (38.54.63[.]75), was tied to Salt Typhoon.
Darktrace’s AI identified and mitigated the intrusion before escalation.
Darktrace believes the attack was likely carried out by the China-linked group Salt Typhoon (also known as Earth Estries), based on similarities in tools, methods, and infrastructure. The group is known for its stealth and use of legitimate software to hide its actions. The incident shows why traditional, signature-based security isn’t enough—detecting unusual behavior early is key to stopping such advanced threats.
“Based on overlaps in TTPs, staging patterns, infrastructure, and malware, Darktrace assesses with moderate confidence that the observed activity was consistent with Salt Typhoon/Earth Estries (ALA GhostEmperor/UNC2286).” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, newsletter)
如有侵权请联系:admin#unsafe.sh