十月初至九月底出现大量钓鱼攻击,利用文档分享和账单更新诱饵针对Outlook、SharePoint及OneDrive用户。攻击者借助合法基础设施如Backblaze、Azure及被黑小企业域名,并广泛采用MFA钓鱼工具包进行 credential 和 MFA 信息窃取。 2025-10-15 00:16:22 Author: pixmsecurity.com(查看原文) 阅读量:7 收藏
Early October and late September saw a concentrated wave of phishing campaigns using document share and billing updates lures, particularly across Outlook, Sharepoint and OneDrive. Many of these were hosted on legitimate infrastructure like Backblaze, Azure, and compromised small business domains, with near 100% adoption of MFA phishing flows and kits. Here are some examples and highlights.
mug[.]ru[.]com
alwasaycorp[.]com
f005[.]backblazeb2[.]com/file/wwwwwuerrrrrrrr/onedr-updated.html
f005[.]backblazeb2[.]com/file/onedrivemailservice/onedr-updated-sal.html
f005[.]backblazeb2[.]com/file/onedrivesolee/onedr-updated-sal.html
f005[.]backblazeb2[.]com/file/seeeeecurreeeeddd/onedr-updated.html
vqnmqjochgkg[.]rasafloorss[.]com
e3303e3303e3303300916[.]z13[.]web[.]core[.]windows[.]net
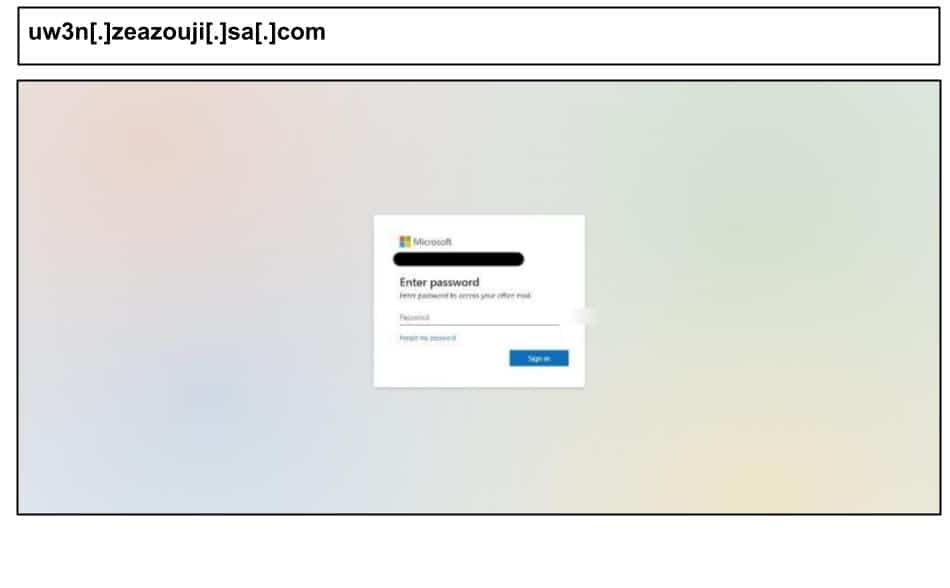
uw3n[.]zeazouji[.]sa[.]com
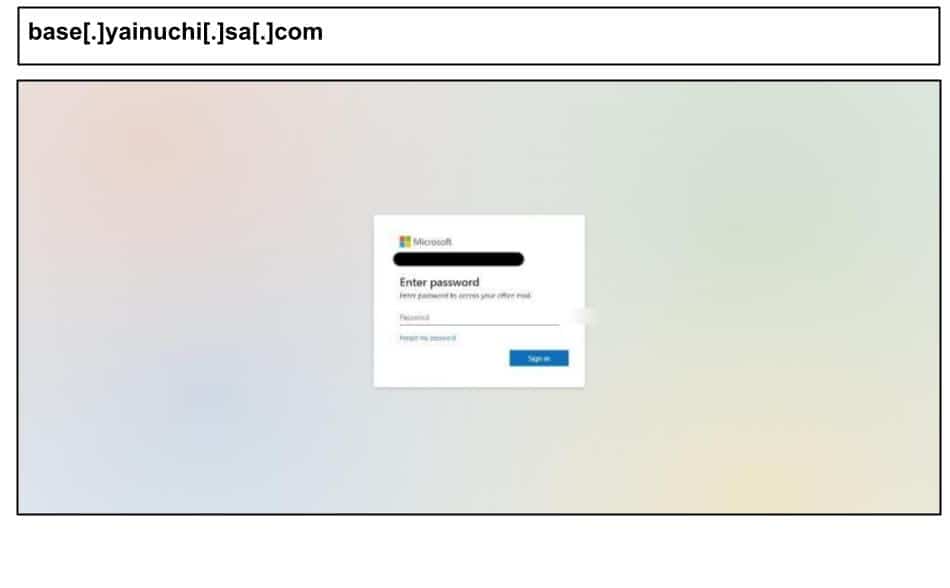
base[.]yainuchi[.]sa[.]com
vqnmqjochgkg[.]rasafloorss[.]com
yumhodyingonwyuking[.]one
accountancy9474[.]velorabu[.]com[.]de
908billingsupdate-informations[.]freeadcity[.]com
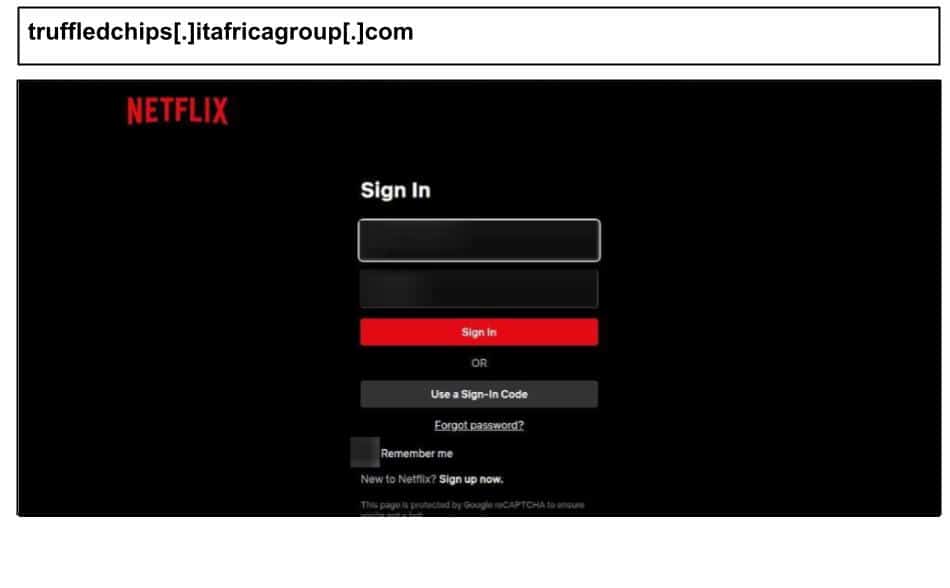
truffledchips[.]itafricagroup[.]com
On September 29, the start of a widespread OneDrive phishing campaign began when an employee at a Kentucky organization clicked the below phishing page.
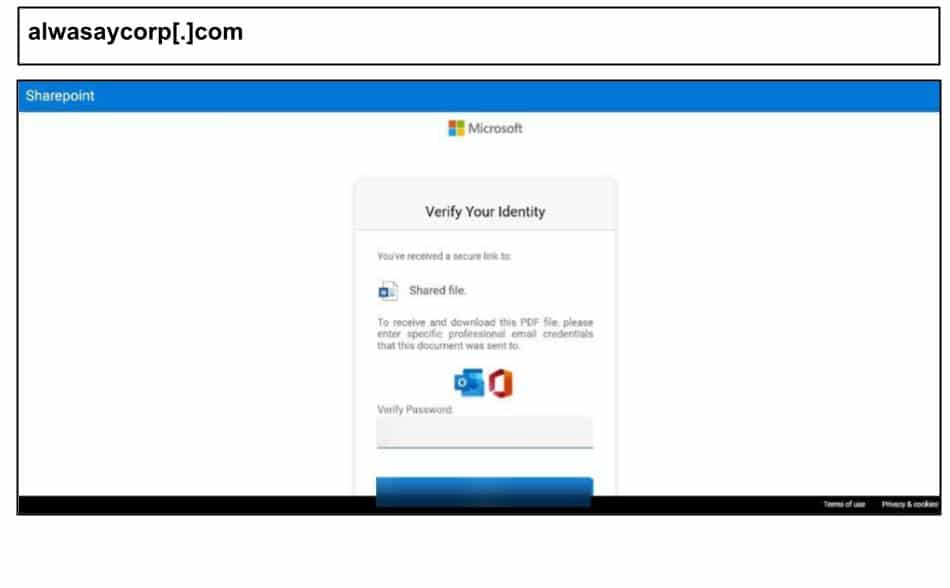
This phishing page uses a SharePoint/O365 doc-share lure:
“To receive and download this PDF, please enter specific professional email credentials that this document was sent to.”
The attack included multi-step MFA harvesting; the DOM on the page incorporated flows for Authenticator number-matching (shows a number like “69”), SMS/OTP code entry, and “Use your password instead” branches.
The landing URL includes an encrypted hash of the recipient’s IP address and user token, almost certainly acquired from an initial link that was clicked and redirected. The page further includes a fake captcha “I’m not a robot” to enhance perceived legitimacy and evade scanners. The same domain was clicked by users at three organizations over the next 48 hours.
A similar campaign, perhaps originating from the same group, was clicked on October 7 by another staff member at a Kentucky organization.
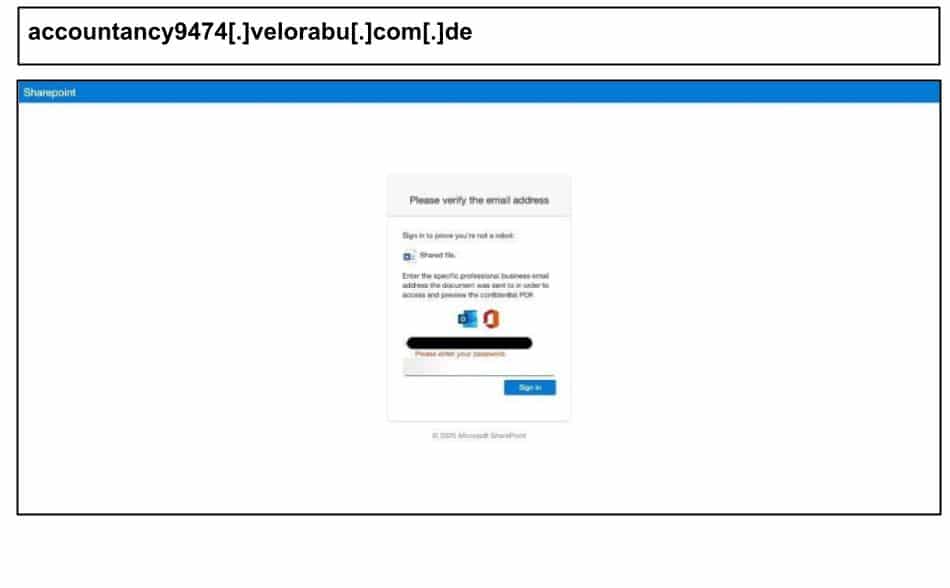
The page content includes classic document share lures: “Shared file”, “verify the professional business email the document was sent to”, “confidential PDF” etc. This case explicitly populated the victim’s email address on the login page. The “accountancy” reference in the subdomain suggests perhaps targeting accounting personnel. It included a full baked MFA relay kit, including options for “Approve request,” call, SMS, code from Authenticator.
The period also had a sustained high volume of OneDrive phishing attacks hosted on Backblaze infrastructure.
On September 29, an employee clicked the below OneDrive phishing attack hosted on Backblaze.
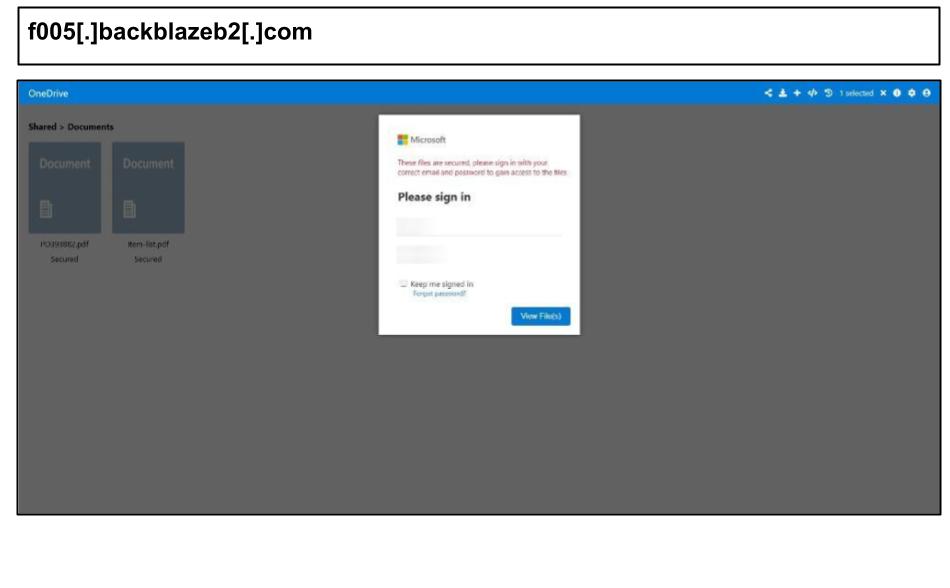
Like other OneDrive attacks hosted on Backblaze attacks seen in September, this references purchasing order file PO393882.pdf and Item-list.pdf, suggesting the likely targeting procurement personnel, and harvests credentials via the Telegram API. The attack tags credentials with the IP and geo-location of the victim.
Additional similar Backblaze phishing attacks were clicked by 7 users across organizations in Virginia, Georgia, and Kentucky over the following several days.
f005[.]backblazeb2[.]com/file/onedrivemailservice/onedr-updated-sal.html
f005[.]backblazeb2[.]com/file/onedrivesolee/onedr-updated-sal.html
f005[.]backblazeb2[.]com/file/seeeeecurreeeeddd/onedr-updated.html
Other document share lures targeted Outlook credentials in organizations in Texas and California.
On September 28, an employee at a Texas organization clicked the below Outlook spear phish.
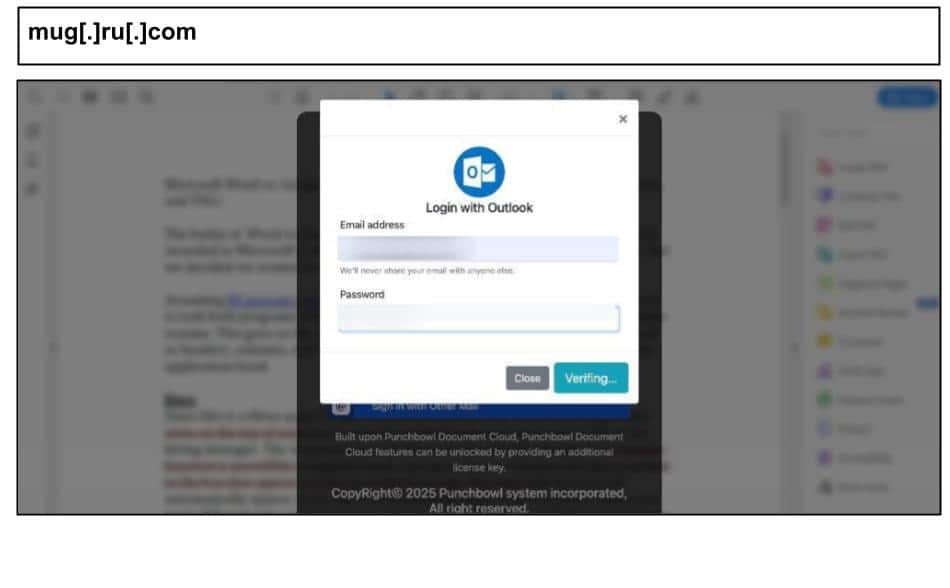
The login experience includes options for multiple brands like Outlook, O365, Gmail, Yahoo etc., and the page tags each harvested credential with the associated provider using the below code snippet.
$.ajax({
url: ‘./next.php’,
type: ‘POST’,
data:{ email, password, detail /* provider */ },
})
On October 5, a staff member at a California organization clicked a similar phishing page.
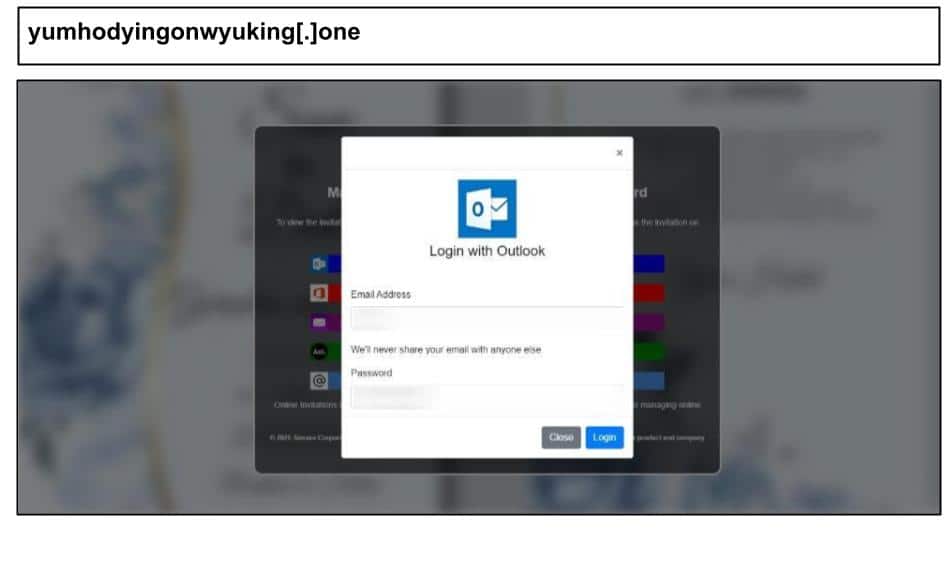
This one uses an online invite lure (eg. Paperless Post, Greenvelope etc.) to “view the invitation”. Similar to others of this type, it offers the user multiple login options and a fake MFA flow.
Some of the scareware scams detected during this period featured interesting tools to lockdown the victim’s device. On September 30, an employee at a Minnesota organization clicked the below Microsoft scareware scam.
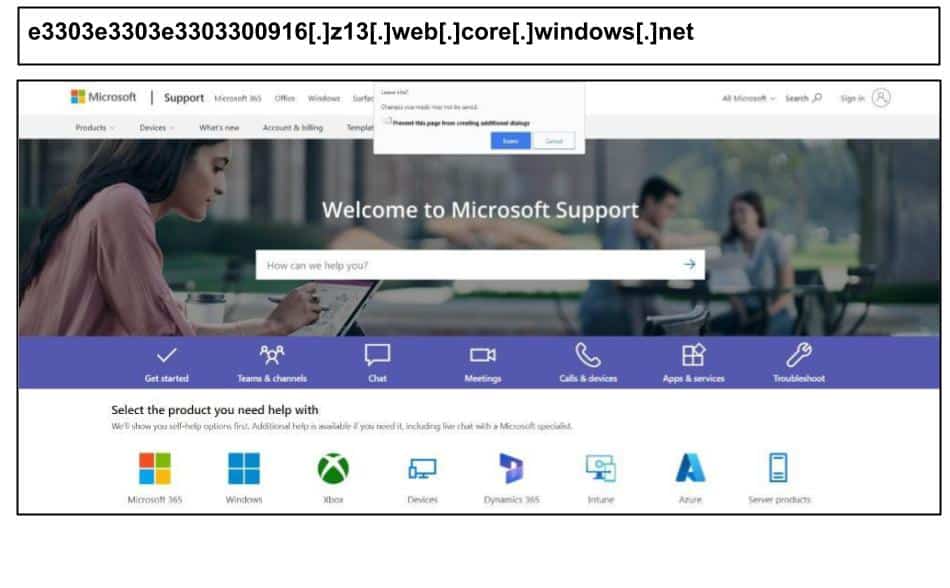
This was a classic tech support browser locker scam. This page notably executes a local DoS “worker bomb” function, (workerBomb()) that spins a massive number of WebWorkers in an infinite loop, intended to freeze the device/browser and panic the user into calling support.
The period was generally rife with Microsoft phishing attacks displaying numerous evasion techniques and MFA phishing.
On September 30th, a Kentucky employee clicked on the below Microsoft phishing page.
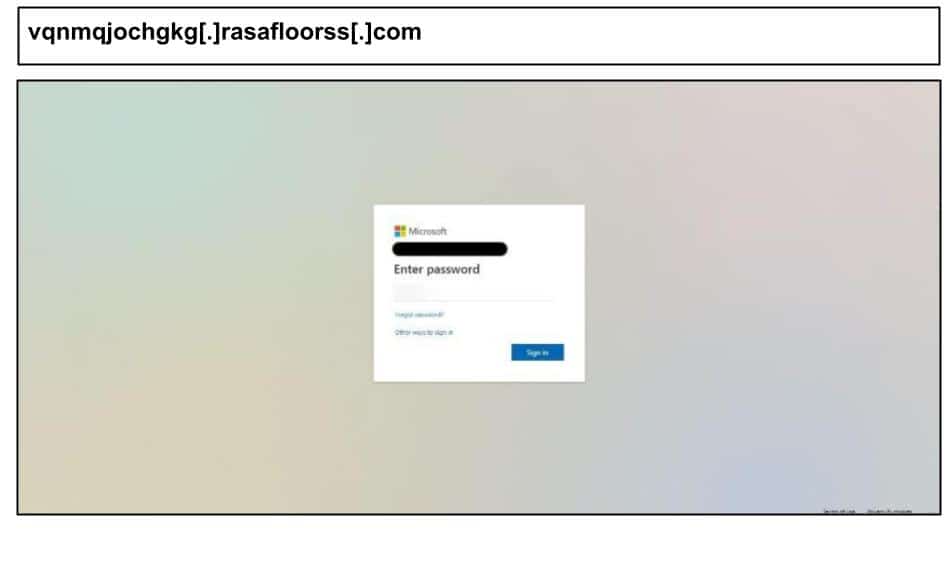
This phishing page uses a MFA harvesting flow, offering the victim multiple authentication options (code entry, SMS, authenticator number-match). It incorporates a few anti-analysis techniques, such as splitting keywords relating to authentication (eg. “Si<b></b>gn in”) to evade content filters. It was clicked by four victims across two organizations, including cases that used customized logo images in the page background.
On October 1, another staff Kentucky user clicked the below Microsoft phishing page.
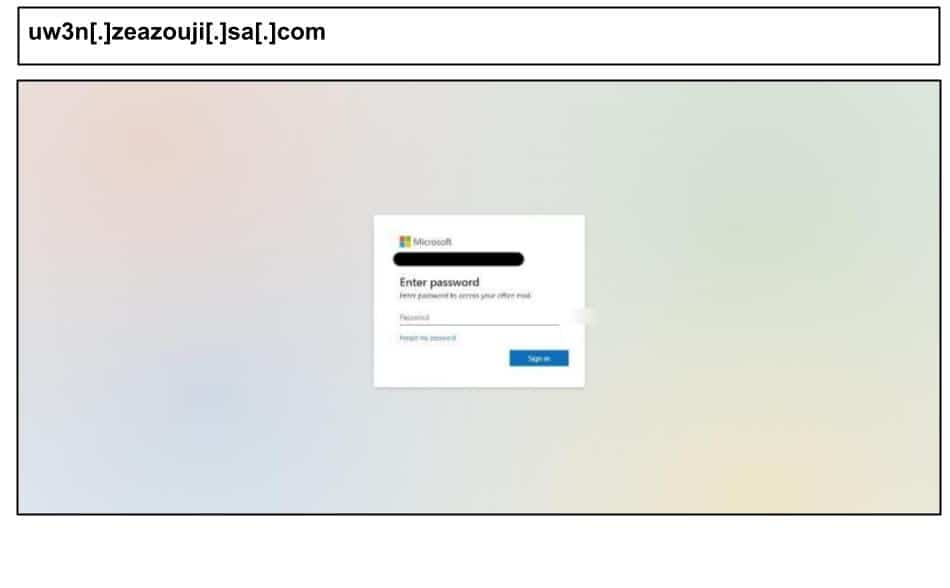
This page embedded a single variable with over a megabyte worth of characters to thwart static analysis efforts and hijacking clipboards to prevent analysts from copying the page.
A similar attack was clicked the next day, likely originating from the same threat actor(s), with nearly identical HTML and domain structure.
The same period witnessed sustained targeting of Netflix accounts on personal devices, notably involving compromised domains of legitimate domains.
In late September, an employee clicked the below Netflix phishing page.
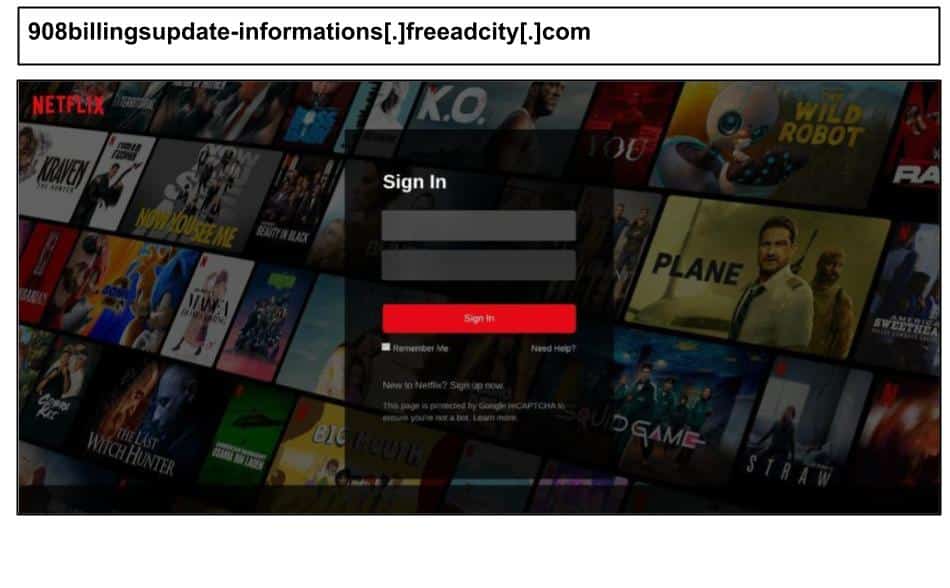
The URL terms ‘renewal’ and ‘billing update’ strongly suggest a billing related lure, while the page itself featured a fake Captcha to boost its legitimacy.
A similar attack was clicked by a staff member at a Florida organization the same day.
The phishing page is hosted on a compromised third party website, an African based smart home business, allowing it to leverage the reputation and certificates of a trusted business domain. It further uses a cloaked redirect, whereby the URL conceals an encoded redirect to the legitimate Netflix page to avoid any keyword matching.
Mitigations
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Educate users about phishing risks even on pages that purport to use MFA
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
If you are interested in seeing how PIXM can help prevent attacks like these for your organization, book a demo here.
如有侵权请联系:admin#unsafe.sh