嗯,用户让我总结一篇文章的内容,控制在一百个字以内,而且不需要特定的开头。首先,我需要快速浏览文章内容,抓住关键点。 文章讲的是一个拥有超过10万个节点的僵尸网络在攻击美国的远程桌面协议(RDP)服务。这个活动从10月8日开始,GreyNoise的研究人员发现这个僵尸网络是从多个不同国家的IP地址发起攻击的,包括巴西、阿根廷、伊朗等。攻击使用了两种特定的攻击向量:RD Web Access定时攻击和RDP网络客户端登录枚举。 此外,研究人员观察到大部分IP地址共享相似的TCP指纹,这表明攻击可能来自一个单一的实体或控制中心。GreyNoise建议采取多种防御措施,比如使用VPN或防火墙限制访问、实施多因素认证、启用网络级别身份验证等。 总结时需要涵盖僵尸网络的规模、目标、来源国家以及攻击方式。同时要简洁明了,控制在一百字以内。避免使用“文章内容总结”这样的开头词。 所以,最终总结应该是:一个由超10万个IP组成的僵尸网络正从全球多地发起针对美国RDP服务的大规模攻击,采用RD Web Access定时攻击和RDP登录枚举等手段。 </think> 一个由超10万个IP组成的僵尸网络正从全球多地发起针对美国RDP服务的大规模攻击,采用RD Web Access定时攻击和RDP登录枚举等手段。 2025-10-14 18:20:10 Author: securityaffairs.com(查看原文) 阅读量:82 收藏
Researchers warn of widespread RDP attacks by 100K-node botnet

A botnet of 100K+ IPs from multiple countries is attacking U.S. RDP services in a campaign active since October 8.
GreyNoise researchers uncovered a large-scale botnet that is targeting Remote Desktop Protocol (RDP) services in the United States starting on October 8.
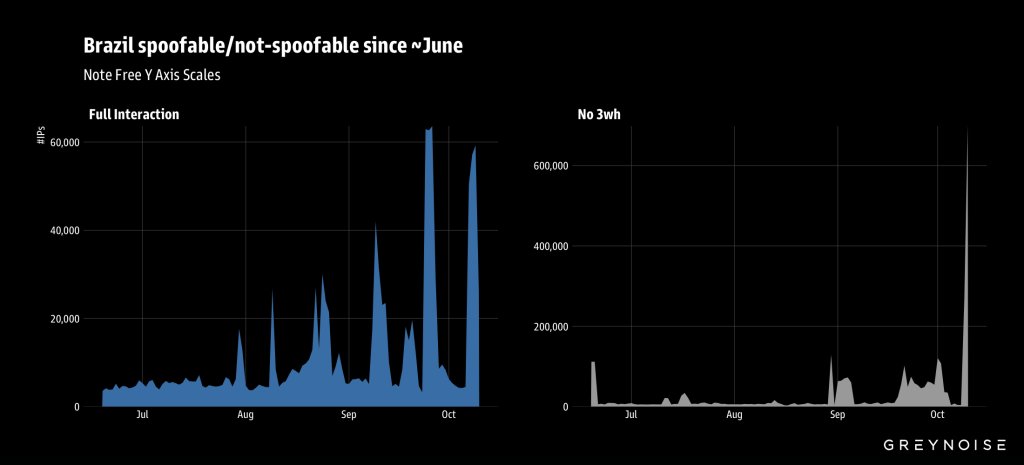
The company discovered the botnet after detecting an unusual spike in Brazilian IP space this week and conducting an investigation into broader traffic patterns.

The experts observed that the attack attempts originated from more than 100,000 IP addresses from multiple countries.
According to the cybersecurity firm, the campaign employs two specific attack vectors — RD Web Access timing attacks and RDP web client login enumeration. The researchers believe that a single entity is behind the attacks because most participating IPs share one similar TCP fingerprint.
The source countries are over 100 and include Brazil, Argentina, Iran, China, Mexico, Russia, South Africa, Ecuador, and others.
“Since October 8, 2025, GreyNoise has tracked a coordinated botnet operation involving over 100,000 unique IP addresses from more than 100 countries targeting Remote Desktop Protocol (RDP) services in the United States.” reads the advisory. “We assess with high confidence that the elevated RDP targeting beginning this week is attributable to a multi-country botnet.”
Grey Noise concludes that “Several factors suggest this activity is originating from one botnet:”
- Almost all traffic shared one similar TCP fingerprint, with only the MSS changing.
- MSS in this context likely changes depending on the compromised botnet cluster.
- The timing and pattern of targeting implies coordinated activity with centralized control.
- The shared RDP attack vector again suggests centralized control, likely activated by the operator(s) for this sole purpose.
To defend RDP services from botnet attacks, restrict access using VPNs or firewalls, enforce MFA and strong passwords, enable Network Level Authentication, and keep systems patched. Monitor login attempts for anomalies, use EDR or fail2ban to block brute-force activity, and limit RDP exposure to essential, time-bound access only.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, RDP)
如有侵权请联系:admin#unsafe.sh