好的,我现在需要帮用户总结一篇文章的内容,控制在100个字以内。用户的要求是直接写文章描述,不需要以“文章内容总结”或“这篇文章”开头。首先,我得仔细阅读文章,理解其主要内容。 文章标题是关于Gladinet CentreStack和Triofox的本地文件包含漏洞(LFI),这是一个零日漏洞。文章提到CVE-2025-11371,这是一个未认证的LFI漏洞,允许攻击者访问主机上的任意文件。攻击者可以利用这个漏洞获取实例的机器密钥,伪造签名数据,进而实现远程代码执行。 接下来,文章指出该漏洞在2025年10月10日没有补丁,并且已经有活跃的利用证据。技术细节部分提到攻击者可以通过LFI读取任意文件,获取机器密钥后构造有效的ViewState载荷,导致服务器反序列化并执行远程代码。Huntress已经观察到野外的利用情况。 然后是关于NodeZero的快速响应测试,帮助客户检测漏洞,并提供缓解措施。建议立即应用补丁、禁用temp handler、旋转machineKey等。最后列出了受影响的版本和推荐行动。 现在我需要将这些信息浓缩到100字以内。重点包括:漏洞名称、影响的产品、漏洞类型、攻击者能做什么、是否有补丁、以及当前状态。 可能的结构:Gladinet CentreStack和Triofox存在未认证的LFI漏洞(CVE-2025-11371),允许攻击者访问任意文件并获取机器密钥,从而实现远程代码执行。目前无补丁可用,已有活跃利用。 </think> Gladinet CentreStack和Triofox存在未认证本地文件包含(LFI)漏洞(CVE-2025-11371),允许攻击者访问任意文件并获取机器密钥以实现远程代码执行。当前无补丁可用,已有活跃利用案例。 2025-10-14 15:5:18 Author: horizon3.ai(查看原文) 阅读量:82 收藏
Gladinet CentreStack / Triofox Local File Inclusion (LFI) | 0-Day Active Exploitation
CVE-2025-11371 is an unauthenticated local file inclusion (LFI) vulnerability in Gladinet CentreStack and Triofox that allows an attacker to access arbitrary files on the host system. An attacker can utilize this to obtain the instance’s machine key and forge signed data to achieve remote code execution. As of October 10, 2025, CVE-2025-11371 has no patch available, and there is evidence of active exploitation in the wild.
Technical Details
- The root issue is an unauthenticated LFI that allows arbitrary file reads from the web application.
- Retrieving the instance’s machine key enables attackers to craft valid
ViewStatepayloads that deserialize on the server and achieve remote code execution. - Huntress has observed in-the-wild exploitation.
NodeZero® Offensive Security Platform — Rapid Response
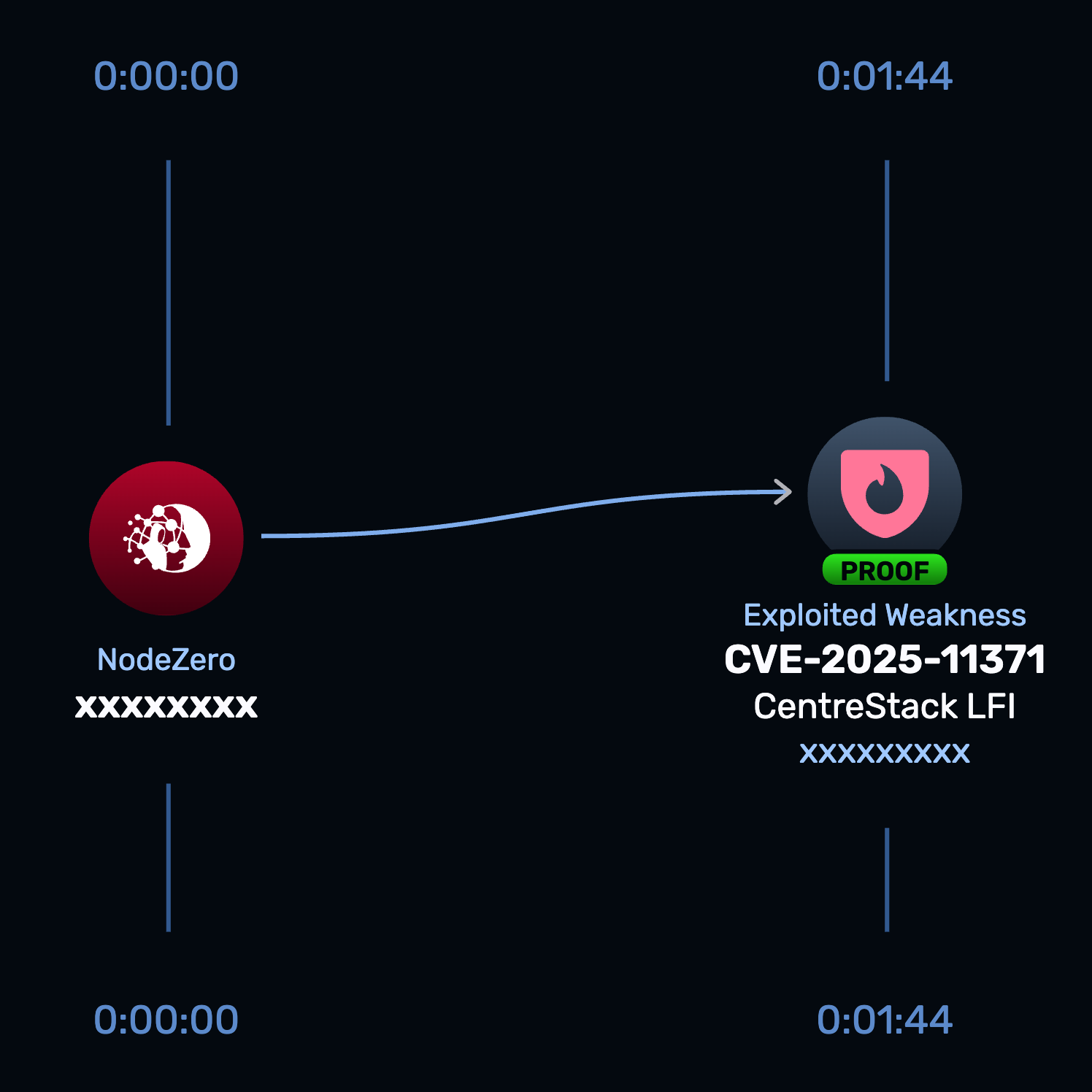
The Gladinet CentreStack Rapid Response test (CVE-2025-11371) released October 14, 2025, enables customers to safely verify whether CentreStack instances are exploitable to the LFI flaw (and therefore susceptible to full compromise) and to confirm mitigation.
- Run the Rapid Response test — run the Gladinet CentreStack — CVE-2025-11371 Rapid Response test from the customer portal to scan internet-facing and internal portal endpoints for the LFI exposure and RCE risk.
- Mitigate immediately — as there is no patch available, follow the recommended immediate workarounds to eliminate risk. Disable the
temphandler inUploadDownloadProxy\Web.config.- Note: Removing it blocks exploitation but does affect functionality.
- Rotate
machineKeyand patch related flaws — if you discoverWeb.configdisclosure or signs of exploitation, contain affected hosts, rotate themachineKey(following vendor guidance for clustered deployments). - Re-run the Rapid Response test — after mitigations, re-run the Gladinet CentreStack Rapid Response test to confirm the LFI path is no longer exploitable.
If the Rapid Response test confirms exploitability, collect forensic artifacts (web logs showing Web.config retrieval, process trees showing suspicious child processes from w3wp.exe, and the original malicious requests), isolate affected systems, and open an incident with your IR team.
Indicators of Compromise (IOCs) — hunting guidance
Find and fix exploitable CentreStack instances with Rapid Response
Affected Versions & Patch
- CVE-2025-11371 (LFI): all versions from 16.4.10315.56368 and prior are affected. No current patch available.
Recommended actions (summary)
- Inventory & scope — identify all web portal instances (internet-facing and internal admin portals).
- If exploitable, apply workaround: remove / disable the
temphandler in theUploadDownloadProxylocated atC:\Program Files (x86)\Gladinet Cloud Enterprise\UploadDownloadProxy\Web.config. This will affect functionality but mitigate exploitability risk. - Contain & investigate — isolate affected hosts, collect web logs and process trees, check for
Web.configdisclosure and suspiciousViewStatepayloads. - Rotate
machineKeyonly after containment and patching — coordinate rotation across clustered nodes per vendor guidance. Disclosure of themachineKeyinvalidatesViewStateprotections. - Patch — apply Gladinet vendor updates when published and re-run Rapid Response tests to confirm remediation.
References
🔗 Huntress
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
