iOS Forensic Toolkit最新版本支持直接从iPhone或iPad提取Apple Unified Logs,提供长达数周甚至数年的系统活动记录,相比手动生成的sysdiagnose日志更具取证价值。 2025-10-13 07:59:18 Author: blog.elcomsoft.com(查看原文) 阅读量:136 收藏

In our previous post, Extracting and Analyzing Apple sysdiagnose Logs, we explained the difference between sysdiagnose logs and Apple Unified Logs. Today we’ll show how the latest build of iOS Forensic Toolkit can pull Unified Logs directly from an iPhone or iPad during advanced logical extraction.
Unified Logs vs. sysdiagnose
The main difference between the two is time to live (TTL), or retention settings, which determine the period of time records are kept on file. Sysdiagnose logs must be generated manually and capture roughly the last 24 hours of system activity; some types of events are going far beyond that, but their forensic significance is relatively low. Miss that window and most valuable events are gone, leaving only lab‑generated noise and a few long‑TTL entries.
Unified Logs live longer – sometimes 10, 20 or even 30 days, depending on device type and Apple’s built‑in retention rules. A handful of records can survive for years. The widely quoted “30 days” figure is a myth; retention varies by category and hardware. Bottom line: grab logs as soon as possible, and trigger a sysdiagnose if you can’t collect anything else.
Extraction workflow
Both log types are acquired through Extended Logical mode in iOS Forensic Toolkit.
Earlier builds supported only sysdiagnose extraction; the newest release speeds up the extraction significantly, with multiple low-level optimizations delivering an up to 50 times speed bump:
./EIFT_cmd normal dumpcrash -o crashlogs.tar
Unified Logs use a different command:
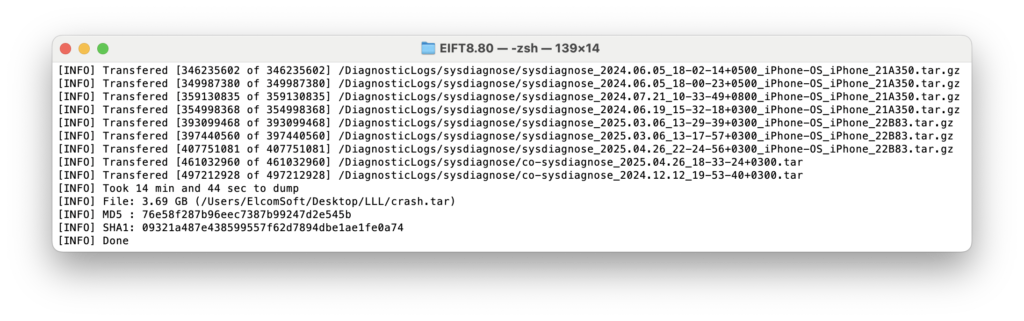
./EIFT_cmd normal dumplogarch -o logarchive.tar
Mac users can open the logs in the Console app by running the following commands:
1) Make a new folder with .logarchive extension
mkdir devicelogs.logarchive
2) Unpack the extracted tar file into that folder:
tar -xf logs.tar -C devicelogs.logarchive
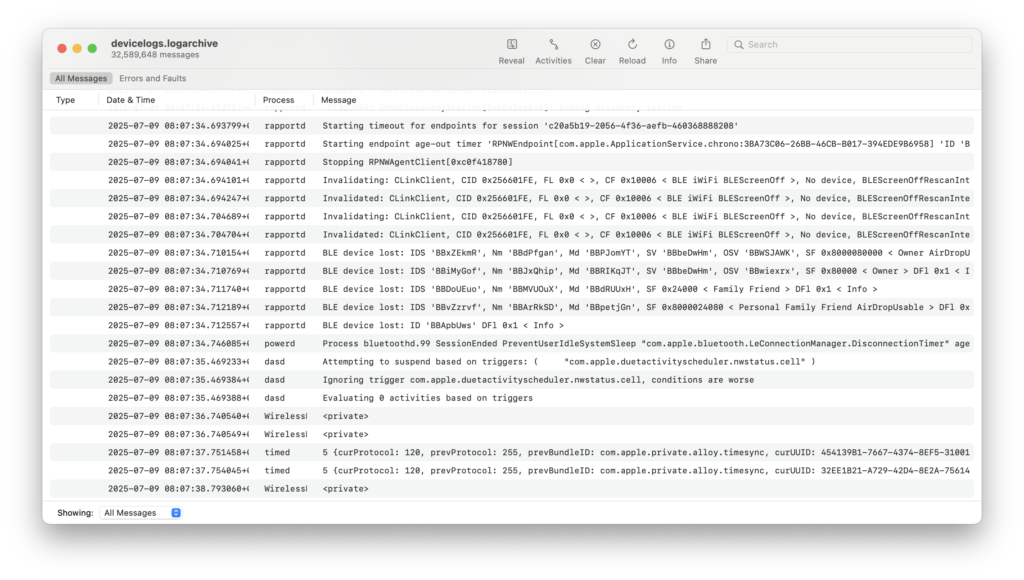
You can then access the log by double-clicking on the folder with .logarchive extension; the Console app will open. The logarchive may contain many thousand events, most irrelevant for the investigation.
It may be easier to use a third-party analysis tool to process them. Note that, by default, the logs are extracted in a proprietary format. Many analysis tools will require JSON or CSV input for processing such logs. You can convert the logs into JSON with a single command, which is only available on macOS:
log show --style json --archive devicelogs.logarchive > output.json
On other platforms, you will have to use a third-party conversion tool such as unifiedlog_iterator. On Windows, the command may look like this:
unifiedlog_iterator.exe --mode log-archive --input devicelogs.logarchive --output converted-archive.csv --format csv
Analyzing the data
Some commercial suites may be able to parse Unified Logs. If yours doesn’t, try open‑source options like iLEAPP, the collection of free scripts, or the Python‑based viewer. All have limits: they’re fine for browsing, not deep analysis, so we are currently exploring the idea of releasing our own dedicated parser.
The logs may contain many thousands or even millions records. For example, this is the result of parsing a devicelogs.logarchive:
Logarchive analysed: devicelogs.logarchive Logarchive path: /Users/ElcomSoft/Desktop/devicelogs.logarchive Analysis started on: 2025-07-18 19:52:20.020356 Analysis ended on: 2025-07-18 20:26:03.975950 Total duration: 2023.96 seconds The MD5 hash of the log archive is: 01d15685b6eb72ed2ac88d3f58b0e74a The SHA1 hash of the log archive is: 7982cb21dcd9b364e2120ec18ca0a6e0d8fbd9cb ===== Summary of the SQLite database generated from the logarchive ===== Size: 23,622,516,736 bytes Start: 2025-06-26 18:43:43.000000+0300 End: 2025-07-10 18:43:42.999128+0300 Total events: 43,240,238 Boots: 4 Log message types: --------------- Default : 25,068,147 (empty) : 10,650,585 Info : 6,143,926 Error : 1,065,501 Debug : 164,841 Fault : 147,238 Event types: --------------- logEvent : 32,589,653 signpostEvent : 9,397,206 activityCreateEvent : 1,189,772 stateEvent : 62,851 userActionEvent : 303 timesyncEvent : 302 lossEvent : 151
What to search for
A single extraction can contain many thousand entries. Even after filtering by time of supposed incident you might face a large number of events. Knowing Apple’s naming conventions is key to separating evidence from noise.
You can find a wealth of practical information about Apple Unified Logs on the website ios-unifiedlogs.com. The blog contains many articles highlighting the valuable artifacts stored in AUL, such as screen unlock events, app launches, the use of dictaphone, device orientation, typing and sending messages, making calls, and many other user activities. One of the posts even explores the analysis of log data collected from an Apple Watch. Start with the in‑depth post iOS Unified Logs – Screen Unlock and the artifact catalogue at Thesis Friday.
Conclusion
Unified Logs add a rich timeline to any investigation and can be pulled with an Extended Logical acquisition – no low‑level exploits required. Just connect, unlock, and run a couple of commands in iOS Forensic Toolkit to secure days or weeks of historical data.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh