威胁者正在利用零日漏洞CVE-2025-11371攻击Gladinet CentreStack和Triofox企业云存储工具。该漏洞为未认证的本地文件包含问题,允许攻击者访问系统文件并执行远程代码。已报告至少三起攻击事件,厂商建议禁用temp handler作为临时措施,尚未发布补丁。 2025-10-11 20:25:16 Author: securityaffairs.com(查看原文) 阅读量:149 收藏
CVE-2025-11371: Unpatched zero-day in Gladinet CentreStack, Triofox under attack

Threat actors are exploiting a zero-day, tracked as CVE-2025-11371 in Gladinet CentreStack and Triofox products.
Threat actors are exploiting the local File Inclusion (LFI) flaw CVE-2025-11371, a zero-day in Gladinet CentreStack and Triofox. A local user can exploit the issue to access system files without authentication.
Gladinet CentreStack and Triofox are enterprise file-sharing and cloud storage solutions designed for businesses:
- CentreStack: Provides a secure platform for file sharing, syncing, and collaboration, integrating on-premises storage with cloud access. It allows companies to offer cloud-like access to internal file servers while maintaining control over data.
- Triofox: Offers a hybrid cloud solution that enables secure remote access to existing Windows file shares and SMB/NFS storage. It includes features like file versioning, synchronization, and web/mobile access, without moving data from the company’s servers.
Both are used to manage corporate files securely while supporting remote work and collaboration.
Experts are aware of the existence of mitigations, but warn that the issue has yet to be patched.
“In earlier versions of CentreStack and Triofox vulnerable to CVE-2025-30406, a hardcoded machine key would allow a threat actor to perform remote code execution via a ViewState deserialization vulnerability.” reads the report published by Huntress. “After subsequent analysis, Huntress discovered exploitation of an unauthenticated local file inclusion vulnerability (CVE-2025-11371) that allowed a threat actor to retrieve the machine key from the application Web.config file to perform remote code execution via the aforementioned ViewState deserialization vulnerability.”
Gladinet and Huntress have alerted customers to a workaround for the actively exploited CVE-2025-11371 flaw. The cybersecurity firm reported that at least three customers have been targeted so far.
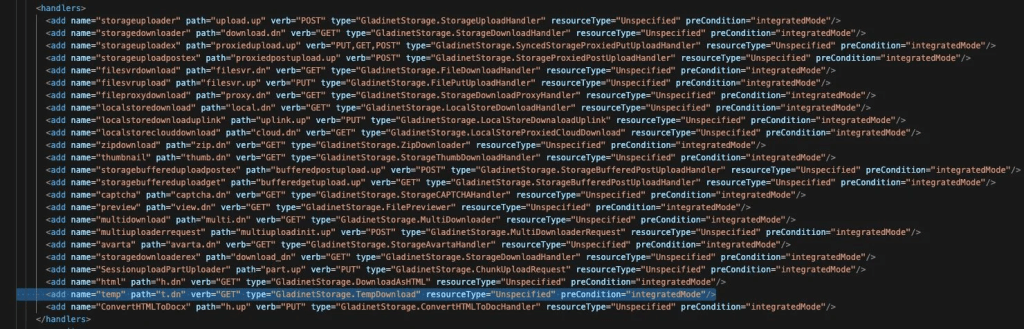
The company recommends disabling the temp handler in UploadDownloadProxy’s Web.config to block exploitation of the vulnerability, though some platform functionality will be affected.

“Removing the line highlighted above will mitigate the vulnerability present until such time as a patch can be applied.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Gladinet)
如有侵权请联系:admin#unsafe.sh