Zimbra Collaboration Suite存在零日漏洞CVE-2025-27915,攻击者利用恶意iCalendar文件发起攻击。该漏洞为存储型XSS,通过未正确清理HTML代码引发。攻击者利用<ontoggle>事件执行JavaScript,窃取凭证、邮件数据并重定向邮件。研究人员发现攻击者使用多种技术隐藏行为,并将数据上传至特定服务器。此漏洞影响Zimbra 9.0至10.1版本。 2025-10-6 07:33:58 Author: securityaffairs.com(查看原文) 阅读量:21 收藏
Zimbra users targeted in zero-day exploit using iCalendar attachments

Threat actors exploited a Zimbra zero-day via malicious iCalendar (.ICS) files used to deliver attacks through calendar attachments.
StrikeReady researchers discovered that threat actors exploited the vulnerability CVE-2025-27915 in Zimbra Collaboration Suite in zero-day attacks using malicious iCalendar (.ICS) files. These files, used to share calendar data, were weaponized to deliver JavaScript payloads to targeted systems earlier this year.
CVE-2025-27915 is a stored XSS flaw in Zimbra Collaboration Suite (versions 9.0–10.1) caused by improper HTML sanitization in ICS files. When victims open an email with a malicious ICS entry, JavaScript executes via an <ontoggle> event, allowing attackers to hijack sessions, set email redirects, and exfiltrate data.
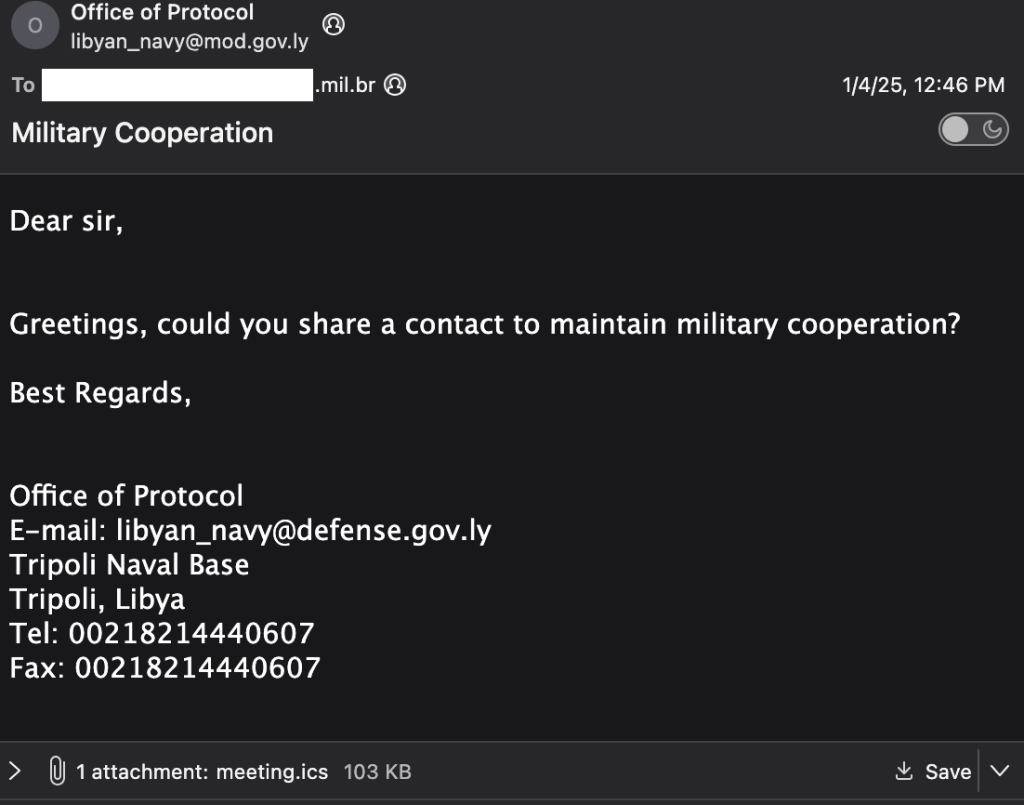
“Earlier in 2025, an apparent sender from 193.29.58.37 spoofed the Libyan Navy’s Office of Protocol to send a then-zero-day exploit in Zimbra’s Collaboration Suite, CVE-2025-27915, targeting Brazil’s military. This leveraged a malicious .ICS file, a popular calendar format.” reads the report published by StrikeReady.
The researchers discovered the attacks while analyzing ICS files larger than 10 KB that contained embedded obfuscated JavaScript.
The malicious script targets Zimbra Webmail, stealing credentials, emails, contacts, and shared folders. It exfiltrates data to ffrk.net and uses multiple evasion techniques; the malicious code delays its execution by 60 seconds, limits activity to three days, hides UI clues, and logs out inactive users to steal data. The researchers also discovered that the script runs asynchronously using multiple Invoked Function Expressions (IIFEs) functions.
Below re the functions supported by the malware:
- Injects concealed form fields to capture usernames and passwords without visible UI indicators.
- Exfiltrates credentials entered into authentication forms.
- Tracks input activity (mouse/keyboard) and, if the user goes idle, terminates the session to enable data theft.
- Queries the Zimbra SOAP API to enumerate folders and pull email messages.
- Periodically (every ~4 hours) uploads captured email content to the attacker’s server.
- Installs a mail-forwarding rule titled “Correo” that redirects messages to a ProtonMail address.
- Gathers authentication artifacts and backup tokens and sends them to the attacker.
- Extracts address books, distribution lists and items from shared folders.
- Delays its payload by 60 seconds after injection to evade quick detection.
- Restricts full activity to a three-day operational window before requiring a cooldown period.
- Obscures or removes interface elements to minimize visual signs of compromise.
- Operates asynchronously in multiple self-contained code blocks to fragment execution and complicate analysis.
StrikeReady couldn’t attribute the attack to a specific group, but pointed out that only a few well-resourced actors have the capabilities to carry out zero-day attacks. The researchers observed TTPs similar to those tied to the Belarusian APT group UNC1151.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Zimbra zero-day)
如有侵权请联系:admin#unsafe.sh
