GreyNoise发现针对Palo Alto Networks登录门户的扫描激增500%,主要来自美国及部分欧洲国家。93%的IP可疑,7%恶意。扫描活动与近期Cisco ASA事件相似,可能关联共享基础设施。GreyNoise正在开发动态IP黑名单以应对威胁。 2025-10-4 19:50:0 Author: securityaffairs.com(查看原文) 阅读量:19 收藏
GreyNoise detects 500% surge in scans targeting Palo Alto Networks portals

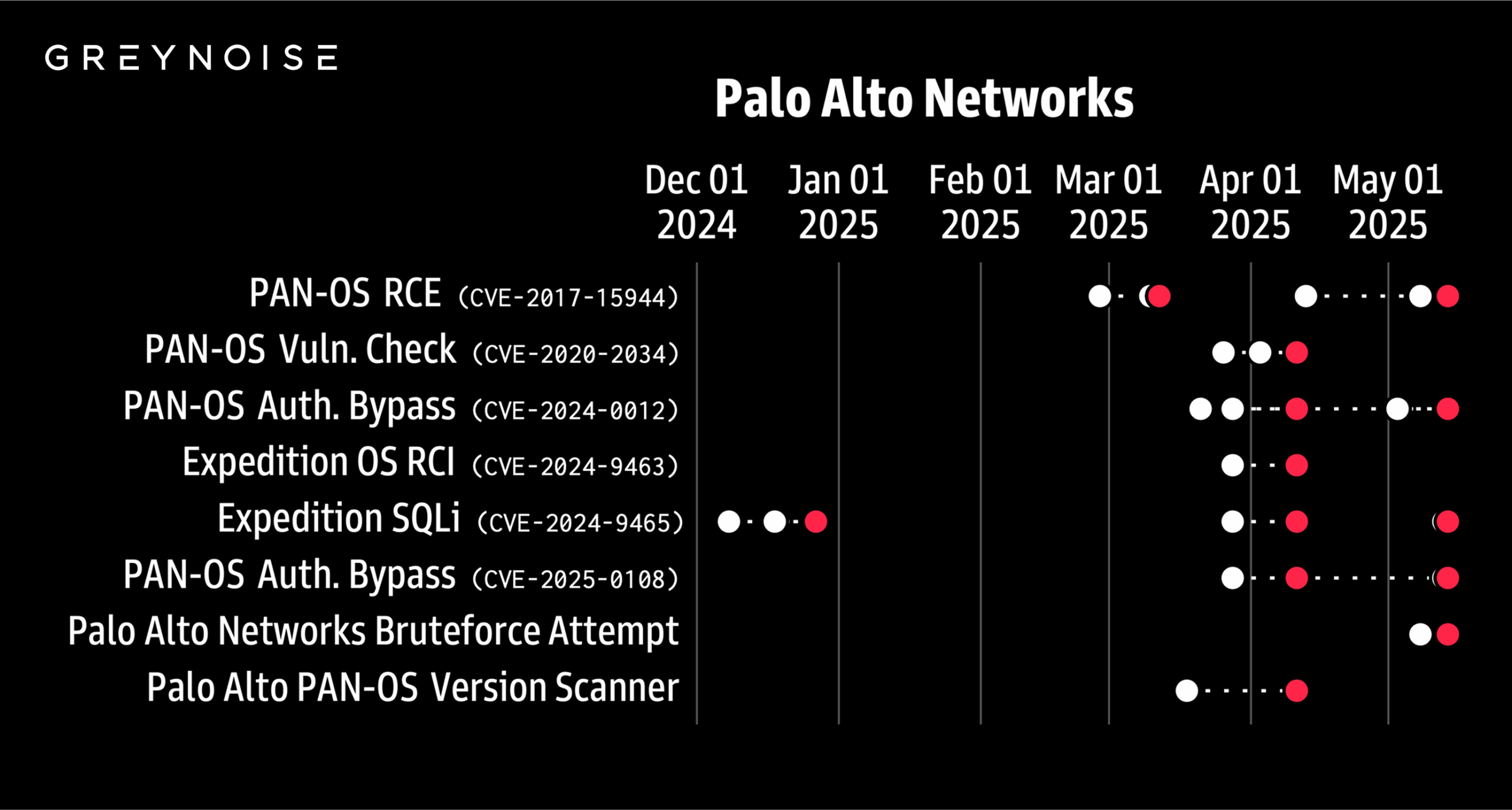
GreyNoise saw a 500% spike in scans on Palo Alto Networks login portals on Oct. 3, 2025, the highest in three months.
Cybersecurity firm GreyNoise reported a 500% surge in scans targeting Palo Alto Networks login portals on October 3, 2025, marking the highest activity in three months.
On October 3, the researchers observed that over 1,285 IPs scanned Palo Alto portals, up from a usual 200. The experts reported that 93% of the IPs were suspicious, 7% malicious.

Most originated from the U.S., with smaller clusters in the U.K., Netherlands, Canada, and Russia.
GryNoise defined the traffic targeted and structured, aimed at Palo Alto login portals and split across distinct scanning clusters.
The scans targeted emulated Palo Alto profiles, focusing mainly on U.S. and Pakistan systems, indicating coordinated, targeted reconnaissance.
GreyNoise found that recent Palo Alto scanning mirrors Cisco ASA activity, showing regional clustering and shared TLS fingerprints linked to the Netherlands infrastructure. Both used similar tools, suggesting possible shared infrastructure or operators. The overlap follows a Cisco ASA scanning surge preceding the disclosure of two zero-day vulnerabilities.
“Both Cisco ASA and Palo Alto login scanning traffic in the past 48 hours share a dominant TLS fingerprint tied to infrastructure in the Netherlands. This comes after GreyNoise initially reported an ASA scanning surge before Cisco’s disclosure of two ASA zero-days.” reads the report published by Grey Noise. “In addition to a possible connection to ongoing Cisco ASA scanning, GreyNoise identified concurrent surges across remote access services. While suspicious, we are unsure if this activity is related. “
GreyNoise noted in July spikes in Palo Alto scans sometimes preceded new flaws within six weeks; The experts are monitoring if the latest surge signals another disclosure.

“GreyNoise is developing an enhanced dynamic IP blocklist to help defenders take faster action on emerging threats.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Palo Alto Networks portals)
如有侵权请联系:admin#unsafe.sh