
Nisos通过开源情报和外部监控识别内部威胁,关注职场冲突、兼职工作、数据收集等关键指标,帮助企业预防潜在风险。 2025-10-2 09:0:53 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
Executive Summary
Identifying potential insider threats requires vigilance and proactive monitoring of key behavioral, technical, and organizational indicators. Nisos’ open-source intelligence investigations have increasingly complemented inside-the-firewall telemetry with externally focused risk and threat visibility at scale.
Nisos routinely partners with enterprise clients to investigate individuals with heightened risk profiles or reveal the identities of individuals responsible for insider threats. We identify and map networks advertising insider access or recruiting insiders at companies on mainstream and alternative social media platforms, cloud-based messaging applications, and dark web forums. Our investigations also include identifying threat actors who create fake identities to obtain employment with companies, which can lead to insider risk issues if not detected and investigated during the hiring phase of the employee lifecycle.
The following analysis details insider-threat risk indicators based on findings from our insider threat intelligence solutions. We also discuss our new platform, Ascend™, which enables our clients to quickly assess and mitigate potential insider risks.
Defining Insider Threat
Insider threat refers to a security risk that originates from within an organization, such as an authorized person abusing their access to and knowledge of an organization’s resources, including personnel, facilities, information, equipment, networks, and systems, to harm that organization. This harm can include malicious, complacent, or unintentional acts that negatively affect the integrity, confidentiality, and availability of the organization, its data, personnel, and facilities. [1] Most of our client work has focused on malicious insider threats and supporting client security teams with outside-the-firewall intelligence solutions.
Insider Threat Indicators
Drawing from our detailed investigations into insider threats, Nisos has identified critical risk indicators surfaced in the digital realm that frequently signal the presence of an insider threat. These include workplace conflicts, undisclosed polywork arrangements, suspicious data collection activities, and employees under significant financial pressure. These indicators represent a sample of the comprehensive risk factors we continuously monitor through our sophisticated insider threat intelligence solutions, helping organizations proactively identify and mitigate internal vulnerabilities before they escalate.
Workplace Conflicts
Individuals identified as insider threats frequently posted on social media about growing tensions with management or coworkers. These posts often occurred following negative performance reviews. In the following examples, individuals openly posted about their interactions with their supervisor and coworkers. Nisos combines expert-led investigation with outside-the-firewall intelligence collection to attribute social media accounts. This approach gives security teams insights to take action.
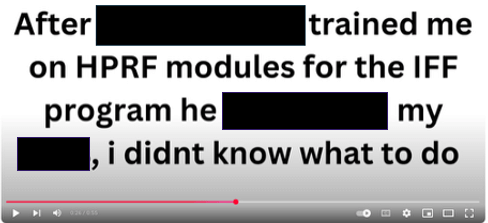
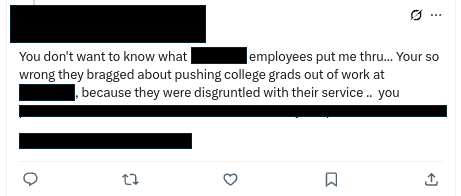
Graphics 1 and 2: Examples of social media posts about workplace conflicts.
Polywork
Individuals identified as insider threats often worked multiple full-time roles. When working multiple full-time jobs, individuals frequently shared sensitive company data or code between two companies to reduce their workload. Similarly, our investigations into the North Korean (DPRK) IT worker employment scheme showed that the same DPRK operator worked for multiple companies using the same or different fake personas. Due to their role in IT teams, DPRK IT workers were often given access to company code, intellectual property, and sensitive data, which they then attempted to exploit for financial gain once exposed. We can identify many of the risk indicators for polywork through open-source, pre-employment vetting.

![]()
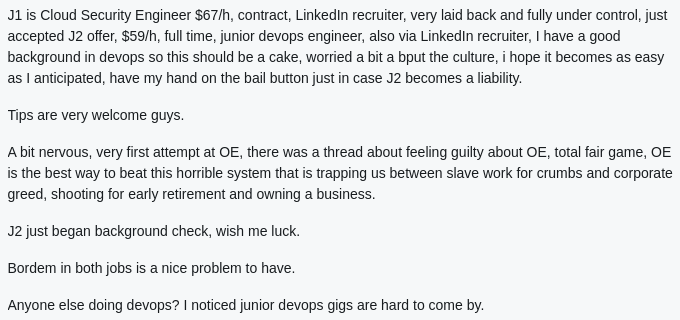
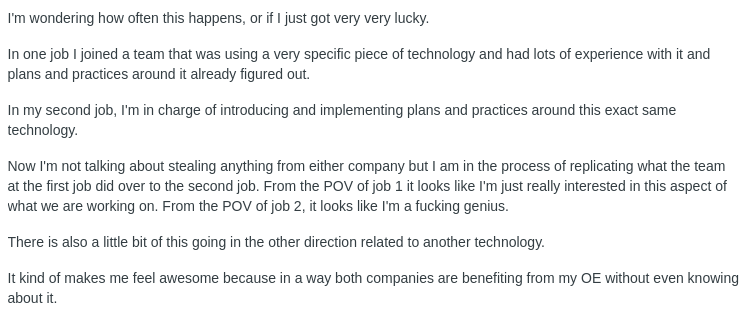
Graphics 3-6: Examples of social media posts about polywork.


Graphics 7-8: Profile photos of the same suspected DPRK IT worker using different personas to gain employment. [2]
Data Collection
Individuals identified as insider threats frequently started collecting large amounts of company data or code into private repositories. In the following examples, individuals openly posted about their efforts to copy code from previous employers and attempts to circumvent security measures, including taking screenshots and using QR codes to transfer code.
To obtain the complete research report, including endnotes, please click the button below.
About Nisos®
Nisos is the human risk management company specializing in unmasking threats before they escalate. The company is a trusted advisor, operating as an extension of security, intelligence, legal, and human resource teams to protect their people and business. Nisos’ intelligence-led solutions help enterprises make critical decisions, manage human risk, and drive real world consequences for digital threats. For more information, please visit: https://www.nisos.com.
如有侵权请联系:admin#unsafe.sh