2025年9月披露了多个关键安全漏洞,包括FreePBX认证绕过导致SQL注入和远程代码执行、Cisco防火墙缓冲区溢出引发根权限远程代码执行、Android运行时内存错误导致沙盒逃逸和权限提升等。这些漏洞影响广泛且已被积极利用,修复迫在眉睫。 2025-10-1 08:8:16 Author: securityboulevard.com(查看原文) 阅读量:3 收藏
September 2025 CVEs made it clear this was not a quiet month for security teams. Critical flaws surfaced, active exploits were spotted, and the systems we rely on every day suddenly looked far less safe. Attackers were already moving fast, exploiting weaknesses in FreePBX and Cisco firewalls to gain a foothold where it hurts the most.
The risks this month are direct. Some of these vulnerabilities can be triggered without a single login attempt, giving adversaries instant access. Others affect devices that handle VPNs, calls, and traffic at the very edge of the network. In plain words, these are not minor issues hidden deep inside code. They are front door keys.
This blog covers the top September 2025 CVEs, how they work, and why patching them without delay is critical.
1. CVE-2025-57819: Authentication Bypass Leading to SQL Injection and Remote Code Execution in FreePBX
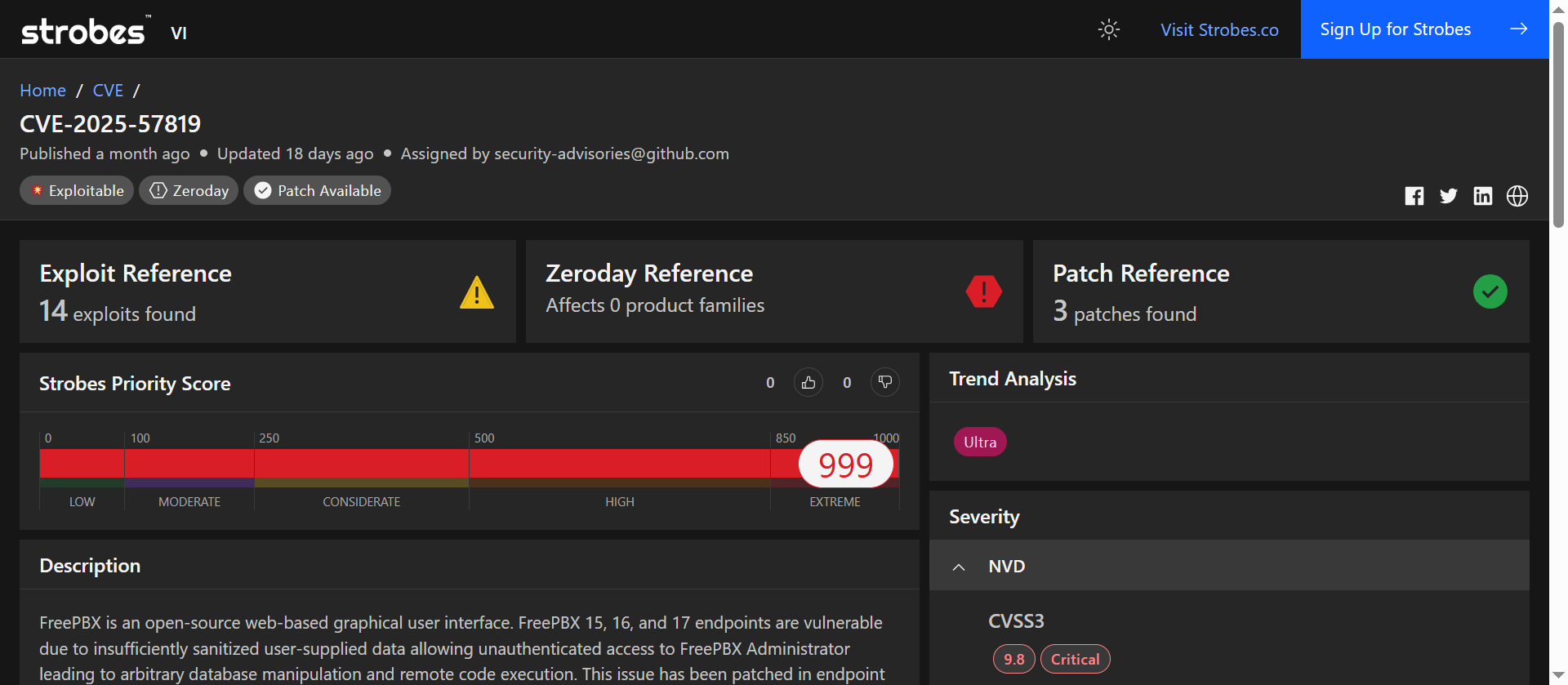
CVE-2025-57819 is a critical vulnerability in the FreePBX endpoint module that permits unauthenticated actors to bypass administrative controls, perform SQL injection against the backend, and chain those actions to achieve remote code execution on affected systems. Vendor advisories confirm active exploitation in the wild and module updates that address the flaw.
CVE-2025-57819 Overview
| Field | Details |
| CVSS v3.1 | 10.0 (Critical) |
| Strobes Priority Score | 999 |
| Exploit Availability | Actively exploited in the wild |
| Patch Available | Yes — endpoint module updates: 15.0.66, 16.0.89, 17.0.3 (or newer) |
| Vulnerability Type | Authentication Bypass + SQL Injection → RCE |
| Affected Versions | FreePBX 15, 16, 17 (endpoint versions before patched releases) |
| CISA KEV Catalog | Yes (added August 2025) |
Vulnerability Breakdown
CVE-2025-57819 results from insufficient validation and sanitization of web-admin input in the endpoint module. An unauthenticated attacker with network access to the Admin Control Panel can bypass authentication checks, perform SQL injection against the backend database, and escalate the injection to arbitrary code execution by writing or including PHP artifacts. Public advisories document exploit chains following the pattern: auth bypass → SQLi → RCE.
Impact of Exploitation
If exploited, this vulnerability can lead to:
- Remote Code Execution: Arbitrary command execution on the FreePBX server.
- Full System Compromise: Complete takeover of PBX functions, including SIP accounts, voicemail, and call routing.
- Data & Configuration Tampering: Rogue admin users, altered call flows, credential theft, and DB manipulation.
Fraud and Lateral Movement: Abuse for toll fraud, spam calls, or as a pivot point into internal systems.
Mitigation & Patching
| Mitigation Step | Status |
| Patch Availability | Endpoint module patched: 15.0.66, 16.0.89, 17.0.3 (or newer) |
| Exploit Activity | Actively exploited in the wild |
| Immediate Workaround | Restrict Admin Panel to VPN or trusted IPs until patched |
| Hardening Tip | Apply least-privilege network access, enable strict firewall rules, and log all access to admin endpoints |
| Detection | Monitor for POSTs to modular.php, unexpected ampuser DB changes, .clean.sh in web root, or unknown PHP scripts |
Why is this CVE in Our Top Picks of the Month?
CVE-2025-57819 combines three dangerous traits:
- Unauthenticated vector (no credentials required)
- Reliable SQL injection primitive
- Confirmed exploitation in the wild
Its inclusion in the CISA KEV catalog highlights its urgency. FreePBX systems often sit at the edge of enterprise networks, controlling voice infrastructure and sensitive metadata, which makes compromise especially damaging.
Strobes Recommendation
Organizations using FreePBX should:
- Immediately patch to endpoint versions 15.0.66 / 16.0.89 / 17.0.3 or newer.
- If immediate patching is not possible, restrict admin panel access to VPN or trusted IPs only.
- Hunt for indicators of compromise (IoCs) such as suspicious POSTs, rogue DB entries, and unknown scripts.
If compromise is suspected, isolate and rebuild from clean backups, and rotate all system and SIP credentials.
Bottomline
Unauthenticated authentication-bypass in FreePBX endpoint module. Chains into SQL injection and remote code execution. Actively exploited in the wild. Patch now to FreePBX 15.0.66 / 16.0.89 / 17.0.3 or newer.
2. CVE-2025-48543: Android Runtime Use-After-Free Allowing Chrome Sandbox Escape and Local Privilege Escalation
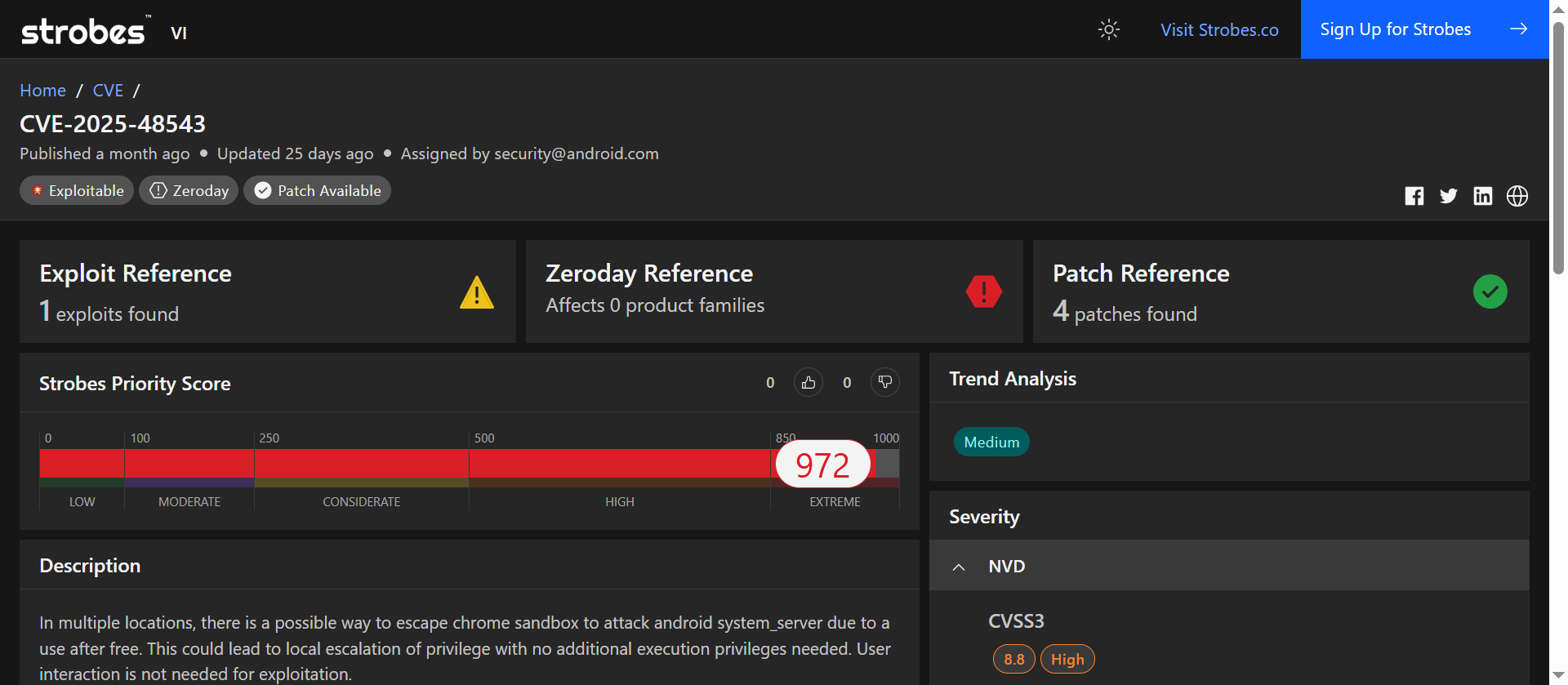
CVE-2025-48543 is a use-after-free (UAF) memory corruption vulnerability in the Android Runtime (ART). An attacker able to run code on-device (for example, via a malicious app) can exploit the flaw to escape the Chrome sandbox and target system_server, resulting in local privilege escalation to higher-privileged system processes. Vendor bulletins and multiple CERT reports limited, targeted exploitation; Google issued September 2025 patches addressing this and related Android runtime flaws.
CVE-2025-48543 Overview
Vulnerability Breakdown
CVE-2025-48543 is a memory management flaw (use-after-free) inside the Android Runtime. In certain code paths, the runtime frees an object while a reference to it remains, creating a dangling pointer. An exploit can manipulate that dangling pointer to escape the Chrome sandbox and interact with higher-privileged services such as system_server. Because system_server runs with elevated privileges, successful exploitation permits local privilege escalation. Public advisories and vendor write-ups note that no user interaction is required in some exploitation scenarios and that exploit attempts have been observed in the wild.
Impact of Exploitation
If successfully exploited on an unpatched device, an attacker can expect:
- Local Privilege Escalation: Escalate from an app context to system/system_server privileges.
- Sandbox Escape: Break out of Chrome/ART sandbox protections to access broader system resources.
- Sensitive Data Access / Persistence: Access data from other apps or system processes and install persistent payloads that survive reboots (depending on OEM/device defenses).
- Potential Lateral Abuse: Use escalated privileges to enable additional on-device attacks or network pivoting where device trust is leveraged.
Practical note: because exploitation requires code execution on the device (for example, a malicious or sandboxed app), the vector is local, but real-world reports indicate attackers are chaining delivery methods to achieve that initial code execution.
Mitigation & Patching
Why is this CVE in Our Top Picks of the Month?
- Sandbox escape + LPE: It is not just an app bug — it allows breaking core process isolation and gaining system privileges.
- No user interaction in some cases: Vendor advisories indicate exploitation without user prompts is possible.
- Observed in the wild: Limited, targeted exploitation reported by vendors and national CERTs.
- Broad impact surface: Android has billions of devices; OEM patch lag means many devices remain vulnerable for weeks to months.
Strobes Recommendation
- Patch immediately — deploy Google/OEM September 2025 Android security updates to all affected devices.
- Harden device policy — block sideloading, enforce managed Play, and use MDM to push fixes and block vulnerable OS versions.
- Hunt & monitor — look for unusual ART crashes, evidence of sandbox escape attempts, and anomalous system_server behavior on enterprise devices.
- Assume risk for unpatchable devices — treat older/unpatchable devices as compromised; isolate them from sensitive corporate networks or decommission them.
Bottomline
Use-after-free in Android Runtime lets attackers escape the Chrome sandbox and escalate to system_server privileges. Limited targeted exploitation observed. Patch Android devices immediately with the September 2025 security updates, harden app installation policies, and hunt for signs of sandbox escape or privilege escalation.
3. CVE-2025-20333: Buffer-overflow RCE in Cisco Secure Firewall (ASA / FTD)
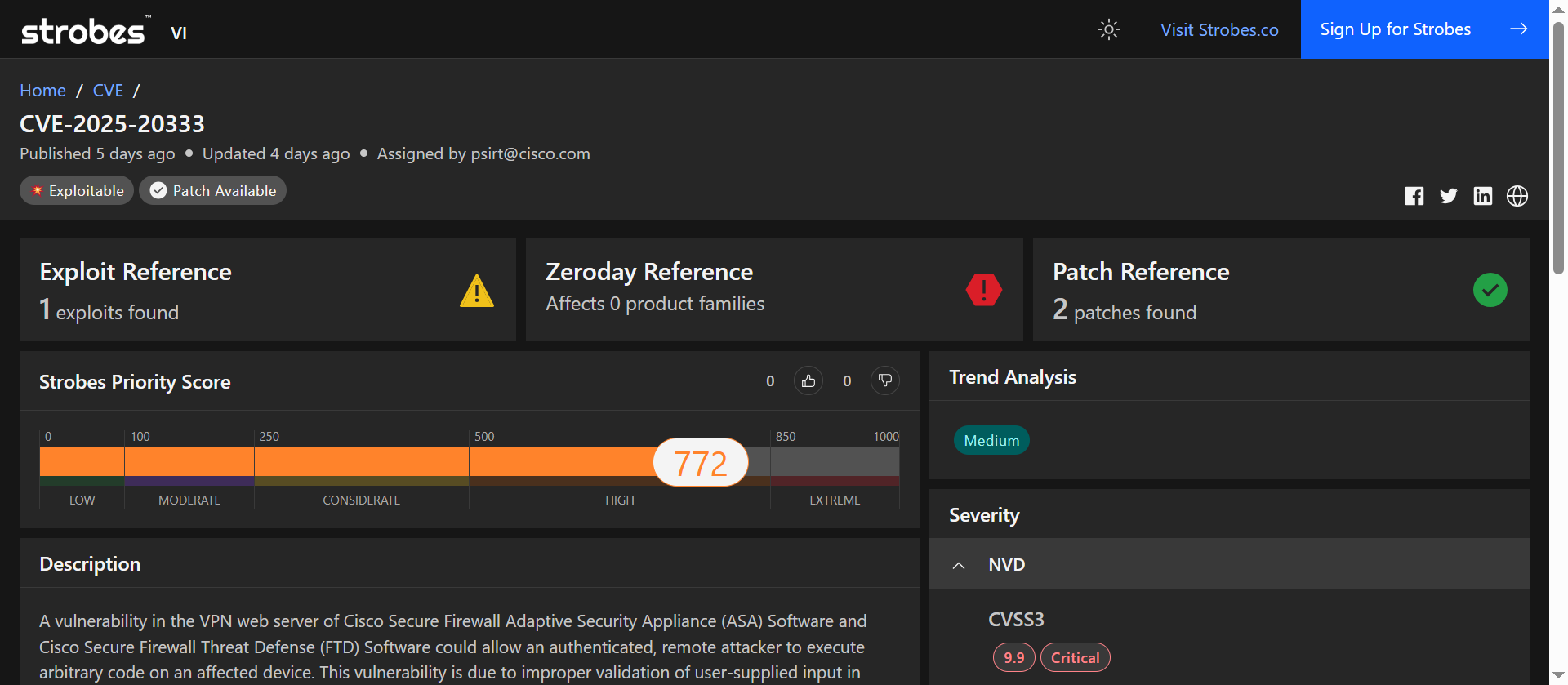
CVE-2025-20333 is a critical buffer-overflow vulnerability in the VPN/web service components of Cisco Secure Firewall Adaptive Security Appliance (ASA) and Cisco Secure Firewall Threat Defense (FTD). A remote, authenticated attacker (valid VPN credentials required) can send crafted HTTP(S) requests to trigger a buffer overflow that leads to root remote code execution on the device. Vendor and government advisories confirm active exploitation in a widespread campaign and urge immediate mitigation.
CVE-2025-20333 Overview
Vulnerability Breakdown
CVE-2025-20333 is caused by improper validation of user-supplied input in the firewall’s VPN/web service. An attacker who possesses valid VPN credentials can send specially crafted HTTP(S) requests that overflow an internal buffer. Successful exploitation can execute arbitrary code as root on the firewall, potentially modifying device memory and firmware state. Cisco telemetry and third-party analyses show this primitive has been used in real attacks and chained with other techniques for persistence and stealth.
Impact of Exploitation
If exploited, impacts include:
- Root Remote Code Execution: Full arbitrary command execution on the firewall (device-level compromise).
- Device Takeover and Persistence: Attackers can alter firmware/ROM, disable or tamper with logging, and persist across reboots and upgrades (reported in active campaign analyses).
- Network Exposure: Compromised perimeter firewall allows inspection/modification of traffic, interception of VPN sessions, and an ideal pivot point into internal networks.
- Operational & Safety Risks: Loss of availability for critical services, possible data exfiltration, and widespread impact where ASA/FTD are widely deployed.
Mitigation & Patching
Why is this CVE in Our Top Picks of the Month?
- Root RCE on perimeter devices: Successful exploit gives attackers full control over the firewall.
- Requires only valid VPN credentials: Though authentication is required, credentials can be stolen, phished, or reused; many environments have weak controls around VPN accounts.
- Active, targeted campaign: Multiple security vendors and CISA report active exploitation tied to a sophisticated actor (UAT4356 / Storm-1849 / ArcaneDoor).
- Government directive: CISA ED 25-03 mandates federal agencies to inventory, analyze, and remediate. This is urgent for critical infrastructure.
Strobes Recommendation
- Patch immediately — deploy Cisco’s fixed ASA/FTD builds as per vendor advisory.
- Rotate and harden VPN credentials — enforce MFA, revoke stale accounts, and apply strong authentication.
- Isolate suspected devices — if compromise is suspected, remove the device from the network, preserve forensic evidence, and rebuild from validated firmware.
- Hunt & monitor — ingest Cisco IoCs, scan logs for signs of ROM/firmware tampering, disabled logging, or unusual outbound connections. Forward logs to SIEM/XDR for detection.
- Follow CISA ED 25-03 — federal and high-risk organizations must follow the emergency directive’s inventory, forensic, and mitigation steps.
Bottomline
CVE-2025-20333 is a critical buffer-overflow RCE in Cisco ASA/FTD web/VPN services. Exploitation yields root control over perimeter firewalls, active attacks are ongoing, and government agencies have mandated urgent remediation. Patch now, rotate VPN credentials, harden access, and hunt for signs of compromise.
4. CVE-2025-55232: Deserialization of Untrusted Data in Microsoft High Performance Compute Pack (HPC)
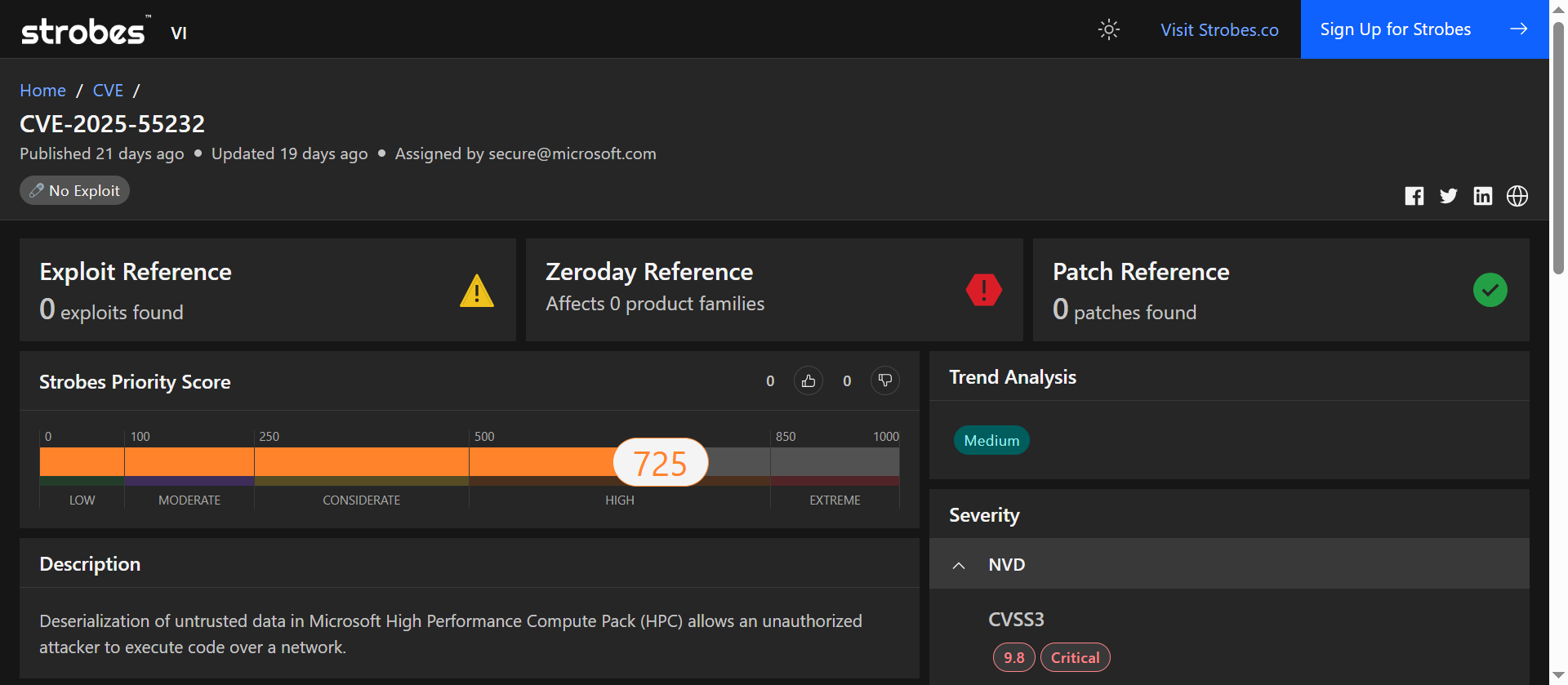
CVE-2025-55232 is a critical deserialization vulnerability in Microsoft High Performance Compute (HPC) Pack. Untrusted data can be deserialized by the HPC service, allowing an unauthenticated, remote attacker to execute arbitrary code over the network. Microsoft published updates for affected HPC components in the September 9, 2025, patch release.
CVE-2025-55232 Overview
Vulnerability Breakdown
CVE-2025-55232 arises from unsafe deserialization in Microsoft HPC Pack. When the HPC component accepts serialized objects from network input and deserializes them without sufficient validation, an attacker can craft payloads that, when deserialized, execute arbitrary code paths on the host process. The vulnerability requires only network reach to the vulnerable HPC service and does not require user interaction or credentials per the vendor description. Microsoft’s advisory and related industry writeups document the issue and supply vendor updates.
Impact of Exploitation
If exploited, the attacker can achieve:
- Remote Code Execution (RCE): Run arbitrary code in the context of the HPC service process.
- Full System Compromise: Depending on service privileges, the attacker can install persistent backdoors, move laterally, or disrupt compute workloads.
- Data Exposure / Integrity Loss: Access or corrupt HPC job data, results, or credentials stored/accessed by the service.
Given that HPC servers often run in sensitive compute environments, the impact is high for affected installations.
Mitigation & Patching
Why is this CVE in Our Top Picks of the Month?
- Deserialization RCE is one of the fastest paths to full compromise.
- The attack requires only network reach to HPC services and no prior credentials.
- Microsoft shipped patches in the September 2025 update; unpatched HPC installs remain high risk.
Strobes Recommendation
- Patch now. Apply Microsoft’s September 9, 2025, updates for HPC Pack immediately.
- Restrict access. Block or limit network exposure to HPC management endpoints until patched.
- Hunt & monitor. Search for suspicious process creations, deserialization indicators, unexpected outbound connections, and altered job artifacts.
- If compromised, assume full compromise of the host process; isolate, forensically image, rebuild from clean images, and rotate credentials.
Bottomline
CVE-2025-55232 is a critical deserialization vulnerability in Microsoft HPC Pack that permits unauthenticated remote code execution when exploited. Microsoft released patches on September 9, 2025. Install them immediately, restrict network exposure to HPC endpoints, and hunt for signs of abuse.
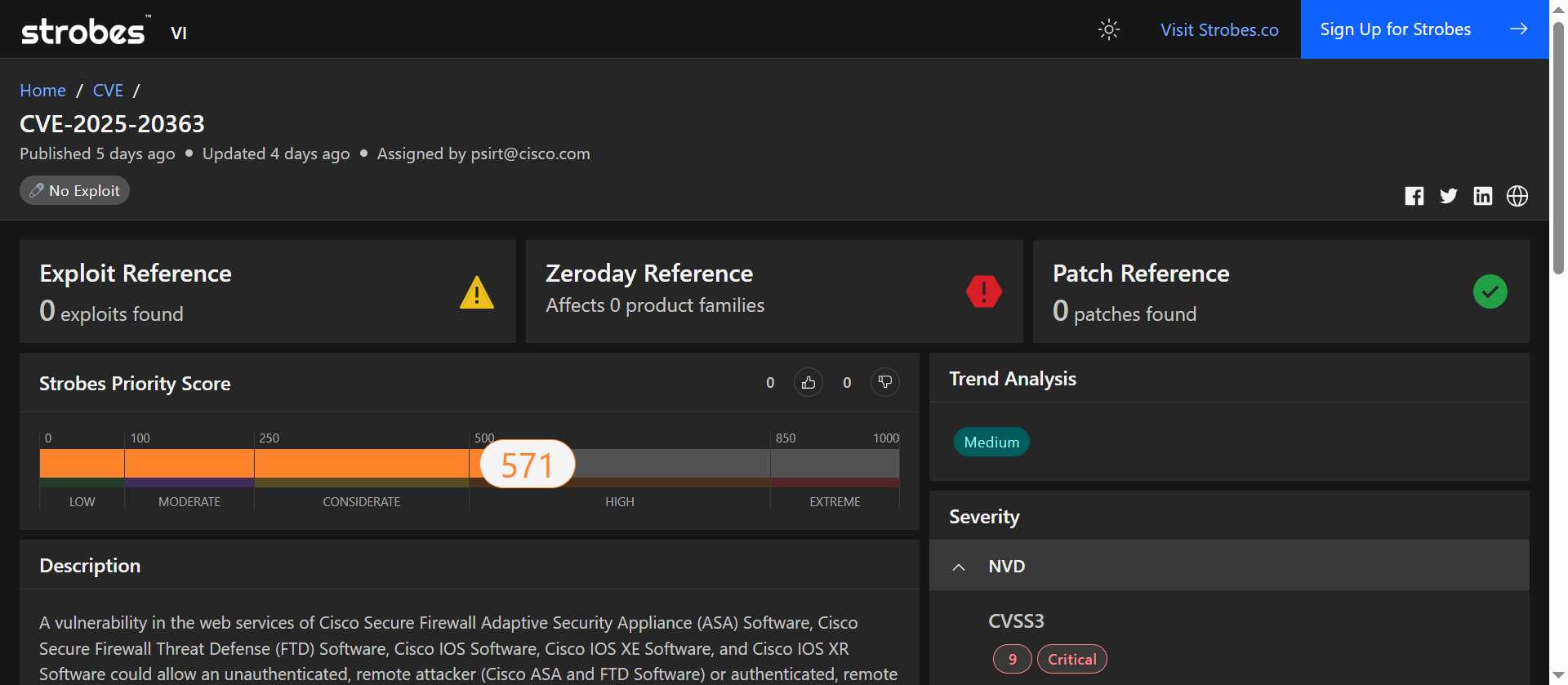
5. CVE-2025-20363: Heap-based Buffer Overflow in Cisco Web Services (ASA / FTD / IOS family)
CVE-2025-20363 is a critical heap-based buffer overflow in web service components used by Cisco Secure Firewall Adaptive Security Appliance (ASA), Cisco Secure Firewall Threat Defense (FTD), and Cisco IOS / IOS XE / IOS XR. Improper validation of user-supplied HTTP(S) input can lead to a heap overflow that, if successfully exploited, allows code execution as root on affected devices. Vendor advisories identify affected product families and provide fixes.
CVE-2025-20363 Overview
Vulnerability Breakdown
CVE-2025-20363 is caused by improper validation of user-supplied data in HTTP(S) request handling routines of Cisco web services. Crafted HTTP requests can trigger a heap-based buffer overflow (CWE-122). On ASA and FTD devices, this can be exploited remotely without authentication when the affected web service (for example, SSL VPN / AnyConnect-related interfaces) is reachable. On IOS family devices, exploitation scenarios may require low-privilege authentication depending on configuration. Successful exploitation can result in the execution of arbitrary code with root privileges. Public analyses and vendor advisories describe the overflow and call for immediate patching.
Impact of Exploitation
If exploited, CVE-2025-20363 can cause:
- Root-level Remote Code Execution: Full compromise of the affected device.
- Network-wide Risk: Compromised ASA/FTD appliances at the network edge allow attackers to intercept, manipulate, or redirect traffic and to persist inside networks.
- Service Disruption: Devices may crash or be taken offline.
- High Operational Impact: These devices often host VPN termination and firewall controls; compromise can enable data exfiltration, lateral movement, and large-scale disruption.
Mitigation & Patching
| Mitigation Step | Action / Status |
| Patch Availability | Apply Cisco fixes immediately. Vendor advisories list patched images and builds per product. |
| Exploit Activity | Cisco and multiple vendors report active campaigns using related Cisco zero-days; 20363 is flagged as high risk for imminent exploitation. Prioritize patching. |
| Immediate Workaround | If immediate patching is impossible, reduce exposure: disable affected web services (SSL VPN / AnyConnect web interfaces) where feasible; restrict management and VPN endpoints to trusted IP ranges or VPN-only access; apply ACLs to limit admin/web service reachability. Vendor docs may list configuration mitigations. |
| Hardening Tip | Enforce network segmentation so ASA / FTD / IOS management and VPN interfaces are not directly reachable from the public internet; enable strict logging and alerting on anomalous HTTP(S) requests to management endpoints. |
| Detection | Hunt for anomalous HTTP(S) requests to appliance web endpoints; crashes/restarts of ASA/FTD processes; unexpected root shells or persistent files; and unusual configuration changes or tunnels. Use vendor advisories and IDS signatures from security vendors for detection rules. |
Why is this CVE in Our Top Picks of the Month?
- Heap overflow → root RCE. That is a full device compromise.
- Edge devices affected. ASA and FTD sit at the network perimeter and often host VPN services. Compromise equals broad access.
- Unauthenticated for key products. Exploitable without credentials on ASA/FTD when services are reachable.
- High exploitation risk. Vendors and researchers report active campaigns and imminent risk for CVE-2025-20363 and related zero-days. Patch urgency is very high.
Strobes Recommendation
- Patch now. Apply Cisco’s released updates for ASA, FTD, IOS, IOS XE, and IOS XR as a priority.
- If you cannot patch immediately, disable affected web services (SSL VPN / AnyConnect web interfaces) or block access to them at the network edge; restrict management interfaces to trusted IPs only.
- Hunt and monitor: look for abnormal HTTP(S) requests, process crashes, new files or shells on appliances, and unexpected configuration changes. Deploy vendor/third-party IDS/IPS signatures where available.
- Assume high impact: treat any suspicious sign on these devices as a potential full compromise; isolate, preserve evidence, and follow incident response playbooks.
Bottomline
CVE-2025-20363 is a high-risk heap-based buffer overflow in Cisco ASA / FTD / IOS web services that can yield root remote code execution. It affects perimeter devices that host VPN and firewall services. Cisco published patches; if you run affected devices, patch immediately or block/disable exposed web interfaces and hunt for indicators of compromise.
Final Words
The September 2025 CVEs show how fast disclosure turns into active exploitation. Every delay in patching increases the risk of compromise and business impact. Fix these vulnerabilities without delay and visit the Strobes VI Platform for the latest CVE updates.
Sources
The post Top CVEs & Vulnerabilities of September 2025 appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Shubham Jha. Read the original post at: https://strobes.co/blog/top-cves-vulnerabilities-of-september-2025/
如有侵权请联系:admin#unsafe.sh