read file error: read notes: is a directory 2025-9-29 14:27:2 Author: www.malwarebytes.com(查看原文) 阅读量:32 收藏
We’ve covered spyware and stalkerware leaks many times before, but we don’t often see such exposure in software used by law enforcement.
According to a report by Straight Arrow News (SAN), the hacker “wikkid” said the intrusion against RemoteCOM was “one of the easiest” they’d ever carried out.
RemoteCOM describes itself as “the premier computer, smartphone and tablet monitoring service for the management of pretrial, probation and parole clients”. According to a leaked training manual, its software, sold as “SCOUT”, says it can be used to track targets ranging from sex offenders, sex traffickers, and stalkers to terrorists, hackers, and gang members.
Behind its official branding, SCOUT behaves like spyware: it records keystrokes, captures screenshots, and even sends out an alert if the tracked person types certain keywords.
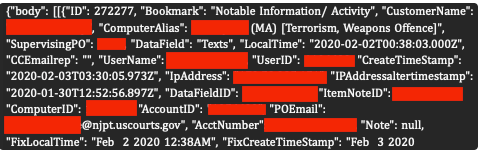
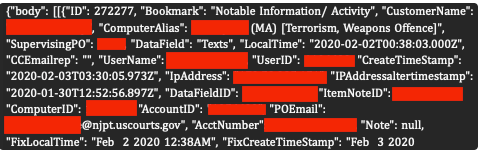
The hacker accessed two key files: “officers” (6,896 entries), containing the names, phone numbers, work addresses, email addresses, unique IDs, and job titles of people working in the criminal justice system who have used RemoteCOM’s services, and “clients” (around 14,000 entries), covering individuals currently or previously monitored by SCOUT; listing names, email addresses, IP addresses, home addresses, and phone numbers, alongside the names and emails of their probation officers.
The files also contained details of the offenses clients were charged with, ranging from sex offenses, weapons, and narcotics cases to terrorism, stalking, domestic violence, sex trafficking, fraud, violence, and hacking.
This type of data leak can be dangerous for both sides of the app. Clients tagged with the keyword “sex” are not necessarily convicted sex offenders—they could be suspects under surveillance or have not yet been to trial—but that distinction might not stop any vigilantes out there.
For officers, the leak of names, contact details, and workplaces could expose them and their families to threats of violence. One officer even had the app installed on the phones of their sister-in-law and fiancé, making the breach especially personal.
Speaking to SAN, a spokesperson for RemoteCOM said:
“We are assessing the situation currently along with your article that you posted.”
Protecting yourself after a data breach
There are some actions you can take if you are, or suspect you may have been, the victim of a data breach.
- Check the vendor’s advice. Every breach is different, so check with the vendor to find out what’s happened and follow any specific advice it offers.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop or phone as your second factor. Some forms of 2FA can be phished just as easily as a password, but 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for fake vendors. The thieves may contact you posing as the vendor. Check the company’s website to see if it’s contacting victims and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to get sites to remember your card details for you, but we highly recommend not storing that information on websites.
- Set up identity monitoring, which alerts you if your personal information is found being traded illegally online and helps you recover after.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
如有侵权请联系:admin#unsafe.sh