
黑客利用SEO中毒和广告推广虚假Microsoft Teams安装程序,植入Oyster后门以获取对企业网络的初始访问权限。该恶意软件伪装成可信工具,并通过计划任务确保持久性。专家建议仅从验证过的域下载软件以防范此类攻击。 2025-9-27 20:0:27 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

Hackers have been spotted using SEO poisoning and search engine advertisements to promote fake Microsoft Teams installers that infect Windows devices with the Oyster backdoor, providing initial access to corporate networks.
The Oyster malware, also known as Broomstick and CleanUpLoader, is a backdoor that first appeared in mid-2023 and has since been linked to multiple campaigns. The malware provides attackers with remote access to infected devices, allowing them to execute commands, deploy additional payloads, and transfer files.
Oyster is commonly spread through malvertising campaigns that impersonate popular IT tools, such as Putty and WinSCP. Ransomware operations, like Rhysida, have also utilized the malware to breach corporate networks.
Fake Microsoft Teams installer pushes malware
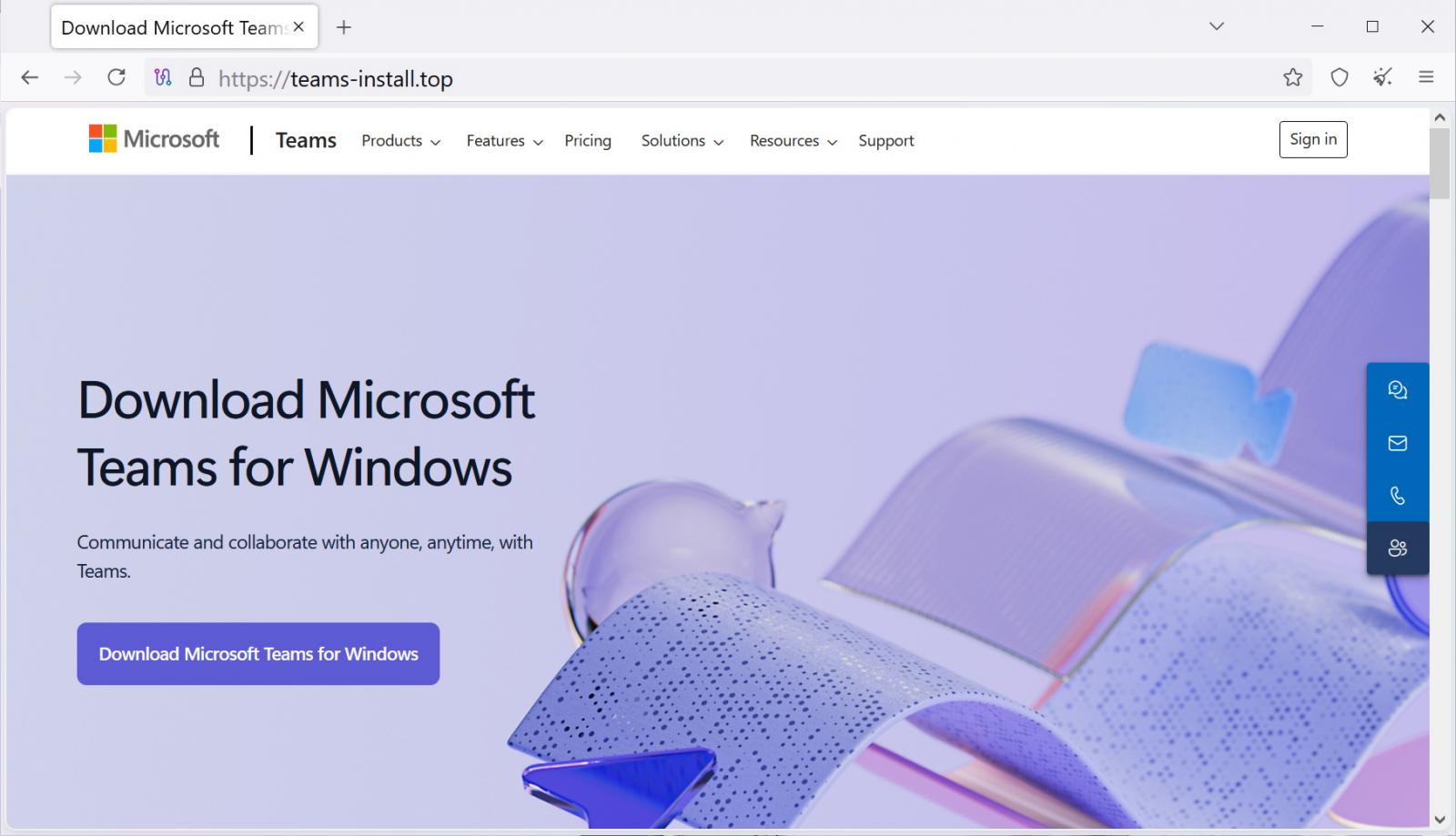
In a new malvertising and SEO poisoning campaign spotted by Blackpoint SOC, threat actors are promoting a fake site that appears when visitors search for "Teams download."

Source: Blackpoint
While the ads and domain do not spoof Microsoft's domain, they lead to a website at teams-install[.]top that impersonates Microsoft's Teams download site. Clicking on the download link would download a file called "MSTeamsSetup.exe," which is the same filename used by the official Microsoft download.
Source: Blackpoint
The malicious MSTeamsSetup.exe [VirusTotal] was code-signed with certificates from "4th State Oy" and "NRM NETWORK RISK MANAGEMENT INC" to add legitimacy to the file.
However, when executed, the fake installer dropped a malicious DLL named CaptureService.dll [VirusTotal] into the %APPDATA%\Roaming folder.
For persistence, the installer creates a scheduled task named "CaptureService" to execute the DLL every 11 minutes, ensuring the backdoor remains active even on reboots.
This activity resembles previous fake Google Chrome and Microsoft Teams installers that pushed Oyster, highlighting how SEO poisoning and malvertising remain a popular tactic for breaching corporate networks.
"This activity highlights the continued abuse of SEO poisoning and malicious advertisements to deliver commodity backdoors under the guise of trusted software," concludes Blackpoint.
"Much like the fake PuTTY campaigns observed earlier this year, threat actors are exploiting user trust in search results and well-known brands to gain initial access."
As IT admins are a popular target for gaining access to credentials with high privileges, they are advised only to download software from verified domains and to avoid clicking on search engine advertisements.
如有侵权请联系:admin#unsafe.sh
