
AttackIQ推出Ransom Tales计划,第四卷新增Rhysida、Charon和Dire Wolf勒索软件的TTPs模拟攻击图,帮助客户测试安全控制并提升防御能力。 2025-9-25 18:1:51 Author: securityboulevard.com(查看原文) 阅读量:9 收藏
Introduction
On July 22, 2025, AttackIQ introduced Ransom Tales, an initiative focused on routinely emulating the Tactics, Techniques, and Procedures (TTPs) associated with the prolific ransomware families currently dominating the threat landscape. Each volume in this series is designed to dissect the operational behaviors of multiple ransomware families and translate them into realistic emulations that defenders can employ to rigorously challenge their security controls and enhance resilience against disruptive and extortive threats.
In this fourth volume, AttackIQ presents three new attack graphs that emulate the Tactics, Techniques and Procedures (TTPs) associated with the Rhysida, Charon and Dire Wolf ransomware families with the objective of assisting customers in validating their security controls and their ability to defend against these disruptive and extortive threats.
Validating your security program performance against these behaviors is vital in reducing risk. By employing these assessment templates in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with prolific and sophisticated ransomware strains.
- Assess their security posture against opportunistic and financially motivated adversaries that do not discriminate when selecting their targets.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the adversaries currently focused on ransomware activities.
Malware Emulation – Rhysida
Rhysida Ransomware – 2025-04 – TTPs
This emulation replicates the sequence of behaviors associated with the deployment of Rhysida ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Rhysida is a ransomware strain operated under the Ransomware-as-a-Service (RaaS) model, first identified in May 2023, with its dedicated leak site (DLS) established as early as March 2023. Like many other ransomware families, the group employs a double-extortion model, combining file encryption with data exfiltration and exposure to maximize pressure on victims. The group carried out opportunistic attacks across multiple sectors, including education, healthcare, manufacturing, information technology, and government. One of its most notable incidents was the attack on the British Library, which caused significant disruption and resulted in sensitive data being leaked online.
Initial access is typically obtained through external-facing remote services or phishing campaigns. Once inside a network, Rhysida affiliates rely on a combination of commodity tools and living-off-the-land techniques. They have been observed deploying Cobalt Strike for post-exploitation, leveraging PowerShell for command execution, and creating Remote Desktop Protocol (RDP) sessions or establishing VPN access to move laterally. To further their reach and disable defenses, operators use PsExec to deliver scripts such as SILENTKILL, which terminates antivirus programs prior to ransomware deployment.
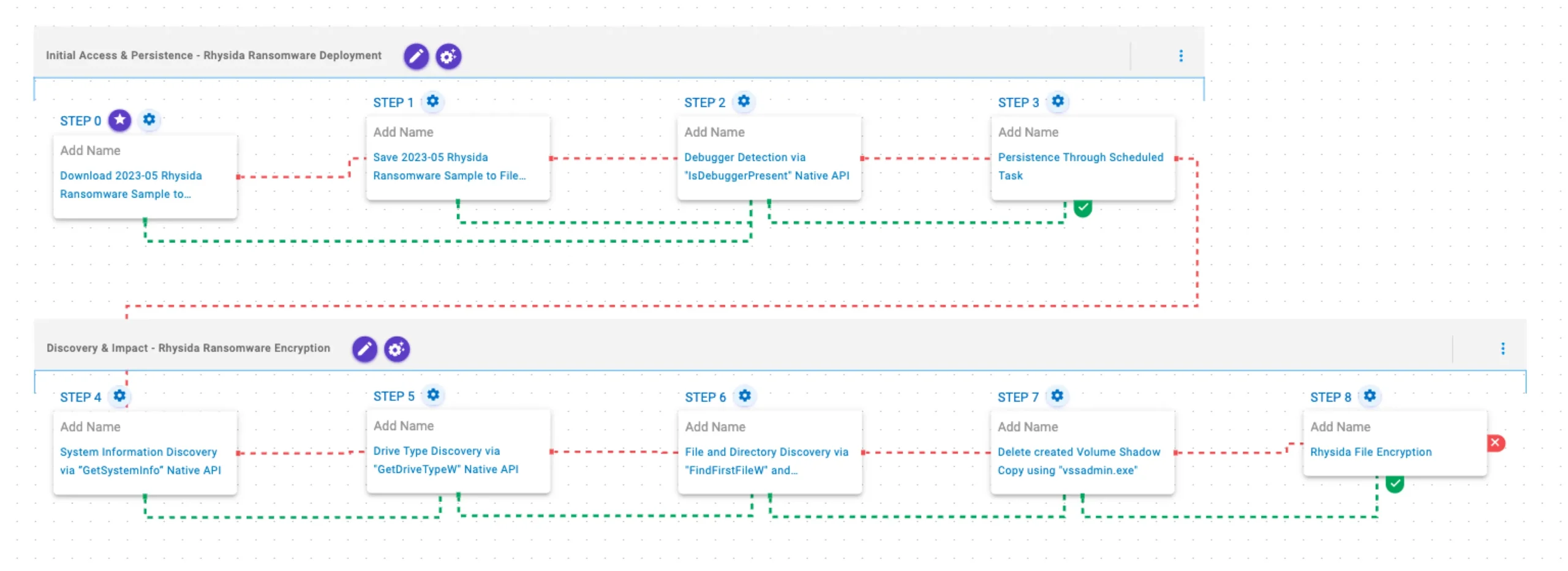
Initial Access & Persistence
Rhysida Ransomware Deployment
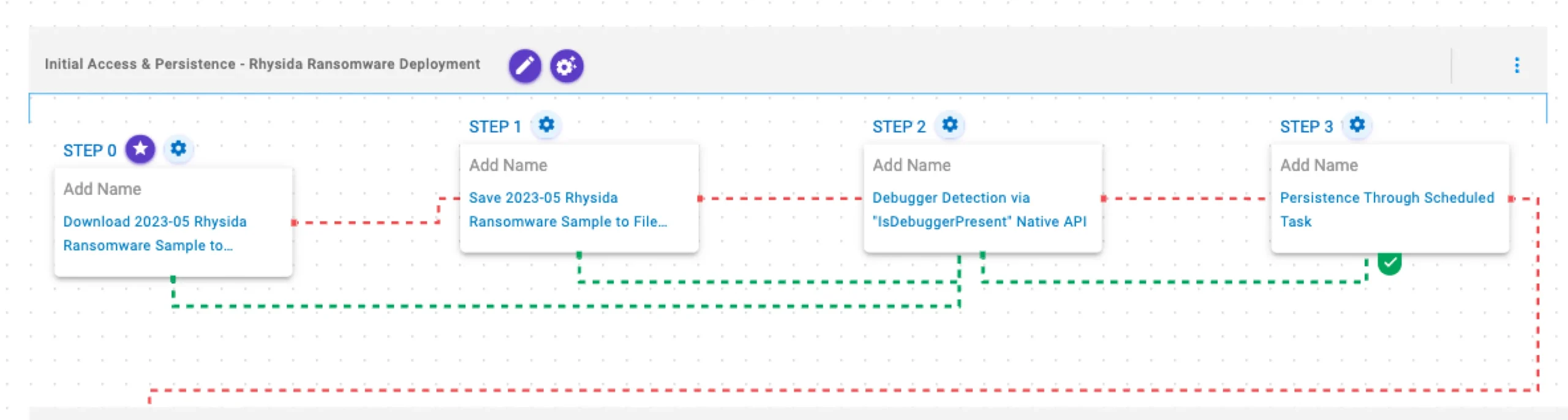
This stage begins with the deployment of Rhysida Ransomware. It attempts to detect the presence of a debugger through the IsDebuggerPresent API and establishes persistence through scheduled tasks.
2023-05 Rhysida Ransomware Sample (T1105): The Rhysida Ransomware sample (SHA256: d5c2f87033a5baeeb1b5b681f2c4a156ff1c05ccd1bfdaf6eae019fc4d5320ee) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
Debugger Detection via “IsDebuggerPresent” Native API (T1497): This scenario will execute the IsDebuggerPresent Windows API to detect the presence of a debugger attached to the current process.
Persistence Through Scheduled Task (T1053.005): This scenario creates a new scheduled task for persistence using the schtasks utility.
Discovery & Impact
Rhysida Ransomware Encryption
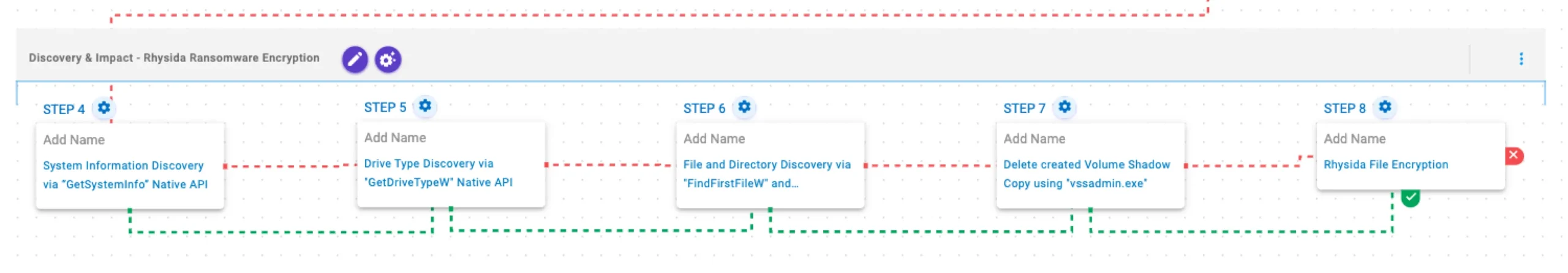
This stage begins with the retrieval of general system information through the GetSystemInfo API. It then performs drive identification via the GetDriveTypeW API, and the identified drives are recursively traversed using FindFirstFileW and FindNextFileW to locate files of interest. Finally, files are encrypted using a combination of ChaCha20 and RSA-4096.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows native API call to retrieve system information. This can be used to detect sandboxes, create unique identifiers, and adjust execution behaviors.
Drive Type Discovery via “GetDriveTypeW” Native API (T1120): This scenario retrieves information about the system’s physical disks using the GetDriveTypeW Windows API call.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
Rhysida File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Rhysida ransomware.
Malware Emulation – Charon
Charon Ransomware – 2025-08 – TTPs
This emulation replicates the sequence of behaviors associated with the deployment of Charon ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Charon is a ransomware strain that emerged in August 2025, targeting aviation and public sector organizations in the Middle East. Unlike commodity ransomware, Charon shows APT-like traits with deliberate targeting and customized ransom notes that reference each victim by name as well as the use of APT-level techniques including DLL sideloading, process injection and anti EDR capabilities.
The infection chain performs a DLL sideloading of the malicious SWORDLDR module through a legitimate signed binary, which then decrypts hidden shellcode and injects it into a system process to launch the ransomware payload. Once active, Charon demonstrates network-aware behaviors, enumerating and encrypting accessible network shares to maximize its reach across victim environments. Charon also incorporates a driver built from the open-source Dark-Kill project, intended to disable endpoint defenses through a bring-your-own-vulnerable-driver (BYOVD) technique. Although this functionality has not been observed in active use, its presence suggests that the operators are experimenting with EDR bypass methods and might be activated in future versions.
By blending criminal objectives with APT-style tactics such as DLL sideloading, process injection, EDR bypasses, and customized extortion methods, Charon represents a high-risk ransomware threat. Its mix of stealthy delivery, aggressive disruption, and targeted victim selection makes it especially concerning for critical industries in the Middle East and beyond.
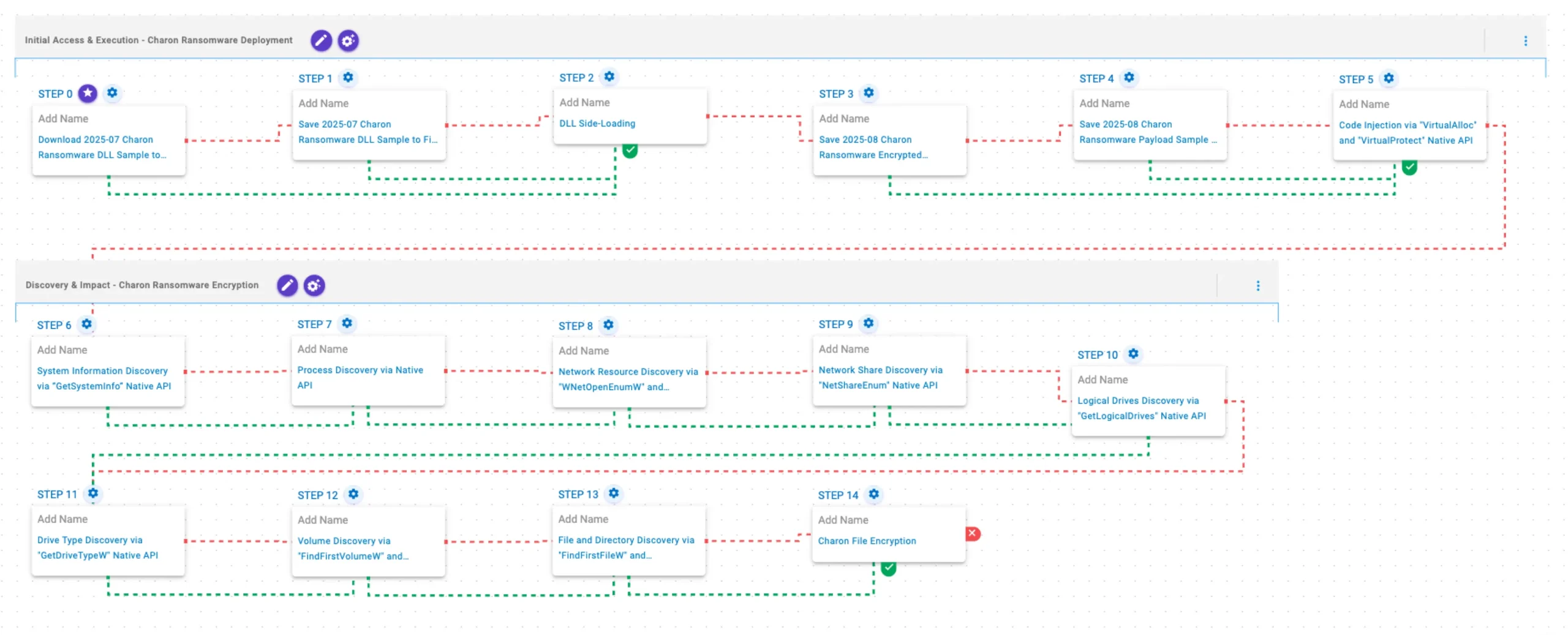
Initial Access & Execution
Charon Ransomware Deployment
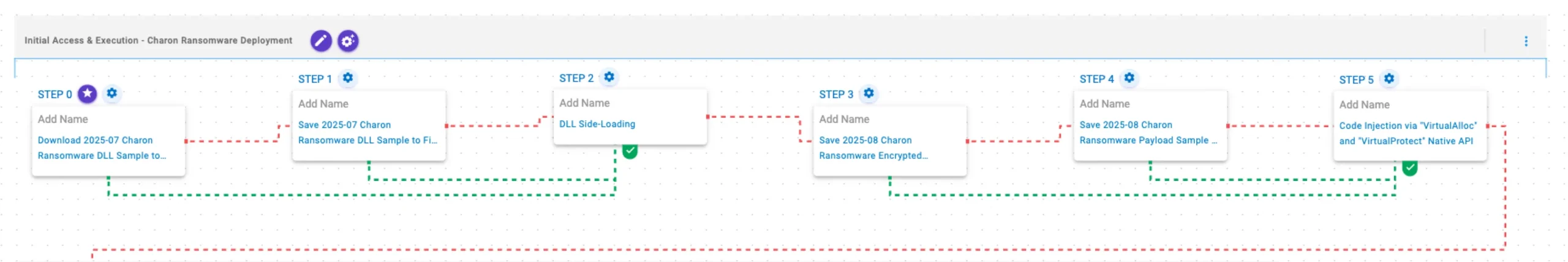
This stage begins with the deployment of Charon ransomware via DLL side-loading. The loader then decrypts the embedded ransomware payload and injects it into a new process via VirtualAlloc and VirtualProtect APIs.
2025-07 Charon Ransomware DLL Sample (T1105): The Charon Ransomware DLL sample (SHA256: e0a23c0d99c45d40f6ef99c901bacf04bb12e9a3a15823b663b392abadd2444e) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
DLL Side-Loading (T1574.002): This scenario leverages a legitimate and trusted executable to load a malicious Dynamic-link Library (DLL).
2025-08 Charon Ransomware Encrypted Shellcode Sample (T1105): The Charon Ransomware encrypted shellcode sample (SHA256: 739e2cac9e2a15631c770236b34ba569aad1d1de87c6243f285bf1995af2cdc2) is saved to disk to test endpoint controls and their ability to prevent the delivery of known malicious samples.
2025-08 Charon Ransomware Payload Sample (T1105): The Charon Ransomware payload sample (SHA256: 80711e37f226ef1dc86dc80a8cbc0b2ec895b361e9ade85da793d94b1d876be8) is saved to disk to test endpoint controls and their ability to prevent the delivery of known malicious samples.
Code Injection via “VirtualAlloc” and “VirtualProtect” Native API (T1055): This scenario performs process injection by allocating memory in a running process with VirtualAlloc, writing shellcode to that memory space, and then changing the memory protection option with VirtualProtect.
Discovery & Impact
Charon Ransomware Encryption
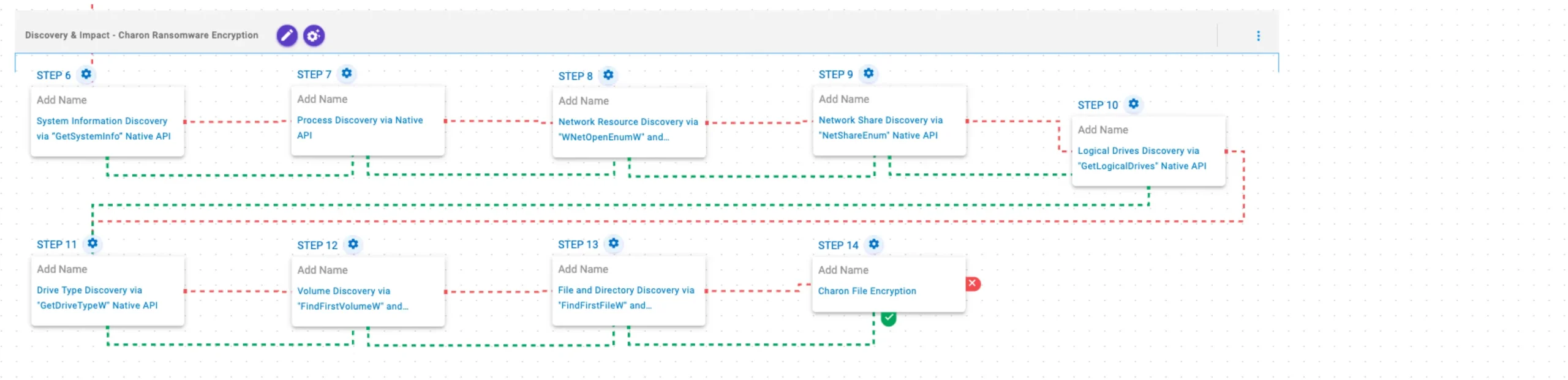
This stage begins with the retrieval of general system information via the GetSystemInfo API, followed by the enumeration of running processes via native API. It then performs network resource discovery by invoking the WNetOpenEnumW and WNetEnumResourceW APIs, followed by the use of NetShareEnum to enumerate network shares from the local computer.
Available drives are subsequently enumerated using GetLogicalDrives, with drive types identified via GetDriveTypeW. This is followed by a systematic traversal of the identified drives using FindFirstFileW and FindNextFileW to identify files of interest for encryption. Finally, files are encrypted using a combination of ChaCha20 and Curve25519.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows native API call to retrieve system information. This can be used to detect sandboxes, create unique identifiers, and adjust execution behaviors.
Process Discovery via Native API (T1057): This scenario executes the CreateToolhelp32SnapshotWindows native API call to receive a list of running processes and iterates through each process object with Process32FirstW and Process32NextW.
Network Resource Discovery via “WNetOpenEnumW” and “WNetEnumResourceW” Native API (T1049): This scenario performs network resource discovery by calling the WNetOpenEnumW and WNetEnumResourceW Windows native API calls to enumerate network resources from the local computer.
Network Share Discovery via “NetShareEnum” Native API (T1135): This scenario executes the NetShareEnum Windows native API call to enumerate network shares from the local computer.
Logical Drives Discovery via “GetLogicalDrives” Native API (T1082): This scenario executes the GetLogicalDrives Windows API call to retrieve the currently available disk drives.
Drive Type Discovery via “GetDriveTypeW” Native API (T1120): This scenario retrieves information about the system’s physical disks using the GetDriveTypeW Windows API call.
Volume Discovery via “FindFirstVolumeW” and “FindNextVolumeW” Native API (T1082): This scenario executes the FindFirstVolumeW and FindNextVolumeW Windows API calls to iterate through the available volumes of the system.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Charon File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Charon ransomware.
Malware Emulation – Dire Wolf
Dire Wolf Ransomware – 2025-06 – TTPs
This emulation replicates the sequence of behaviors associated with the deployment of Dire Wolf ransomware on a compromised system with the intent of providing customers with the opportunity to detect and/or prevent a compromise in progress.
Dire Wolf is a ransomware strain that emerged in May 2025. Employing a double-extortion model, Dire Wolf combines file encryption with data exfiltration and exposure to maximize pressure on victims. It targets organizations in multiple countries and industries, but the manufacturing and technology sectors have been the most affected by this ransomware group.
Dire Wolf is written in Golang and its samples are commonly packed with UPX to hinder analysis. This particular ransomware strain focuses heavily on disrupting defenses and recovery mechanisms once active in a system. It disables Windows event logging to obscure traces, terminates critical services, including security processes, and deletes shadow copies and disables backups or recovery mechanisms to block restoration options. Encryption is performed using Curve25519 with ChaCha20, appending the .direwolf extension to the encrypted files. Notably, victims receive customized ransom notes containing a room ID and login credentials for live chat negotiations, often accompanied by proof of exfiltrated data to reinforce extortion demands.
Initial Access & Discovery
Dire Wolf Deployment and Environment Reconnaissance
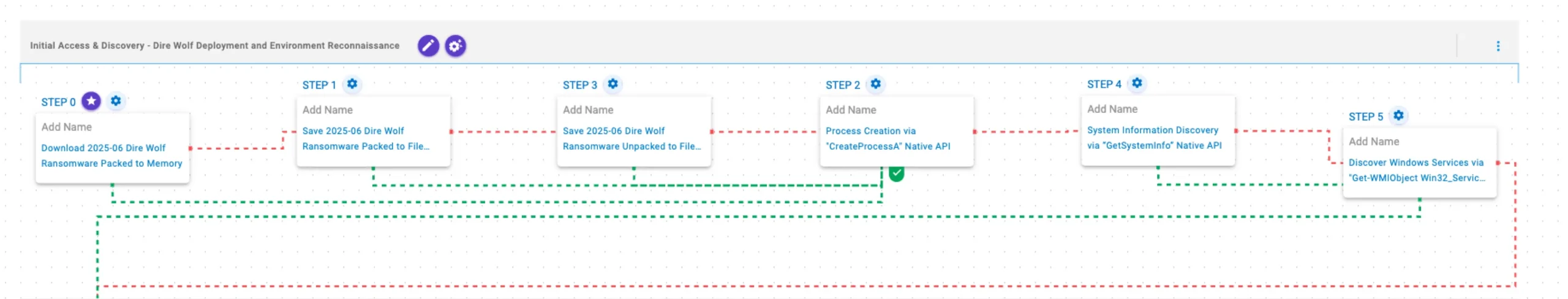
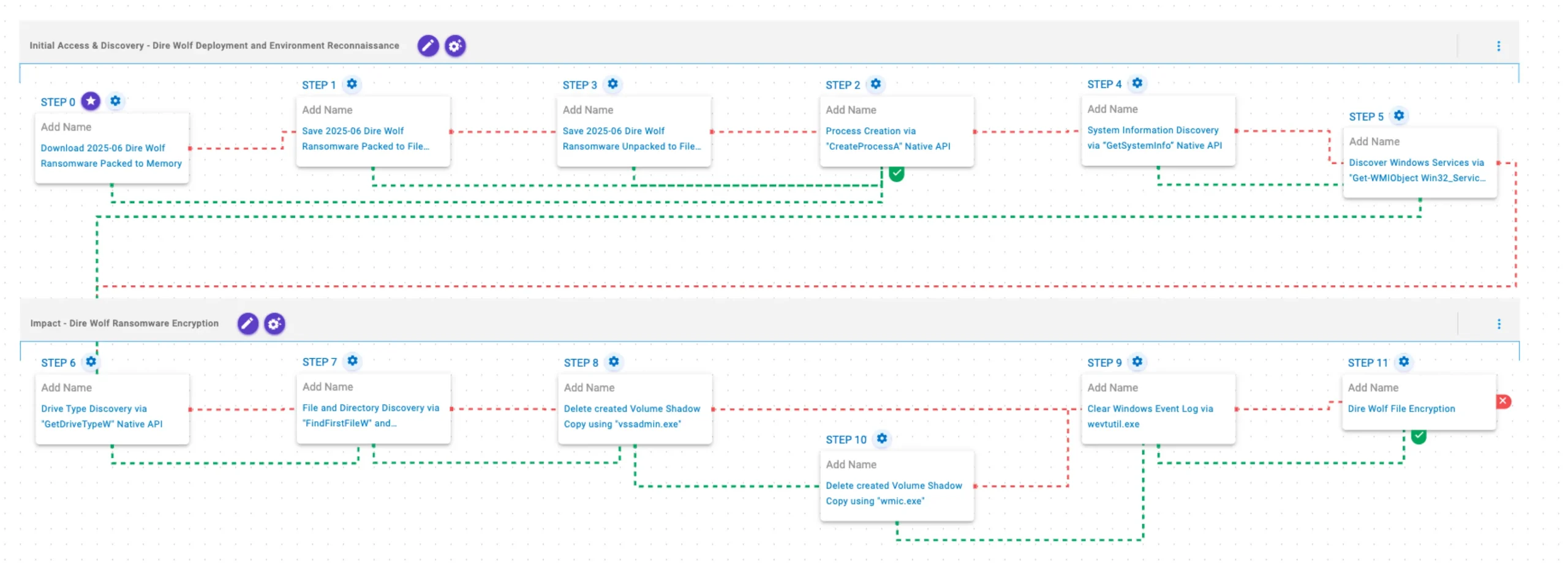
This stage begins with the deployment of Dire Wolf ransomware, followed by the use of the CreateProcessA API for the execution of arbitrary commands. GetSystemInfo is then called to collect details about the infected host. Finally, Windows service information is queried via WMI.
2025-06 Dire Wolf Ransomware Packed (T1105): The Dire Wolf Ransomware packed sample (SHA256: 8fdee53152ec985ffeeeda3d7a85852eb5c9902d2d480449421b4939b1904aad) is downloaded to memory and saved to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious samples.
2025-06 Dire Wolf Ransomware Unpacked (T1105): The Dire Wolf Ransomware unpacked sample (SHA256: 27d90611f005db3a25a4211cf8f69fb46097c6c374905d7207b30e87d296e1b3) is saved to disk to test endpoint controls and their ability to prevent the delivery of known malicious samples.
Process Creation via “CreateProcessA” Native API (T1106): This scenario executes the CreateProcessA Windows API call to create a new process of a given executable payload.
System Information Discovery via “GetSystemInfo” Native API (T1082): This scenario executes the GetSystemInfo Windows native API call to retrieve system information. This can be used to detect sandboxes, create unique identifiers, and adjust execution behaviors.
Discover Windows Services via “Get-WMIObject Win32_Service” PowerShell Command (T1007): This scenario executes the Get-WMIObject Win32_Service Powershell cmdlet to retrieve Windows service information from the local computer.
Impact
Dire Wolf Ransomware Encryption
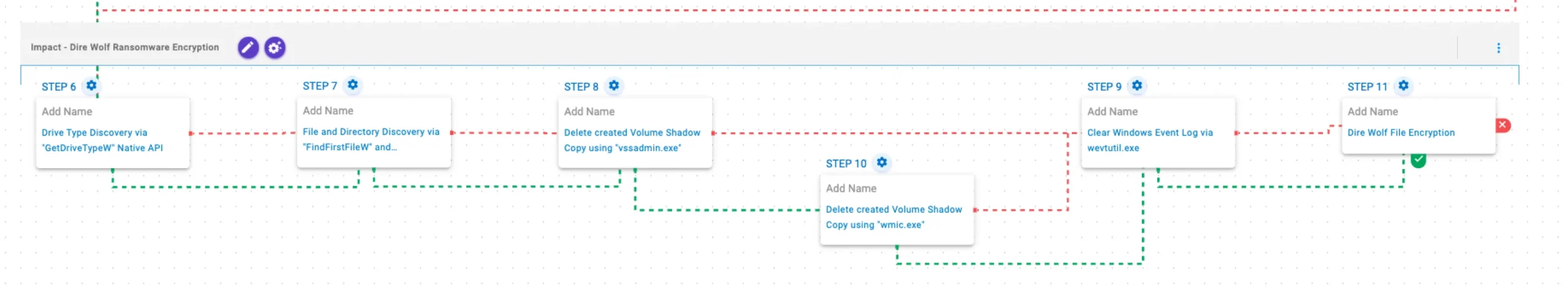
This stage begins with the enumeration of available drives via GetDriveTypeW API, followed by systematic traversal using the FindFirstFileW and FindNextFileW APIs to locate files of interest. Once completed, Volume Shadow Copies are deleted using vssadmin or, alternatively, through a Windows Management Instrumentation (WMI) command. Finally, Windows Event Logs are deleted using wevtutil.exe binary.
Drive Type Discovery via “GetDriveTypeW” Native API (T1120): This scenario retrieves information about the system’s physical disks using the GetDriveTypeW Windows API call.
File and Directory Discovery via “FindFirstFileW” and “FindNextFileW” Native API (T1083): This scenario executes the FindFirstFileW and FindNextFileW Windows native API calls to enumerate the file system.
Delete created Volume Shadow Copy using “vssadmin.exe” (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
Delete created Volume Shadow Copy using “wmic.exe” (T1490): This scenario executes the wmic shadowcopy delete command to delete a Volume Shadow Copy created by the emulation.
Clear Windows Event Log via wevtutil.exe (T1070.001): The scenario uses the wevtutil.exe binary to clear event logs from the system.
Dire Wolf File Encryption (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms as used by Dire Wolf ransomware.
Wrap-up
In summary, these attack graphs will evaluate security and incident response processes and support the improvement of your security control posture against the behaviors exhibited by Rhysida, Charon and Dire Wolf ransomware operators. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against known and dangerous threats.
AttackIQ, the leading provider of Adversarial Exposure Validation (AEV) solutions, is trusted by top organizations worldwide to validate security controls in real time. By emulating real-world adversary behavior, AttackIQ closes the gap between knowing about a vulnerability and understanding its true risk. AttackIQ’s AEV platform aligns with the Continuous Threat Exposure Management (CTEM) framework, enabling a structured, risk-based approach to ongoing security assessment and improvement. The company is committed to supporting its MSSP partners with a Flexible Preactive Partner Program that provides turn-key solutions, empowering them to elevate client security. AttackIQ is passionate about giving back to the cybersecurity community through its free award-winning AttackIQ Academy and founding research partnership with MITRE Center for Threat-Informed Defense.
如有侵权请联系:admin#unsafe.sh
