
Rust官方仓库发现两个恶意包(faster_log和async_println),下载量近8500次,伪装合法项目窃取加密货币私钥和其他敏感信息。通过日志功能扫描系统并发送数据到特定URL。已被删除并暂停账户。开发者需清理系统并转移资产以防止盗窃。 2025-9-25 15:45:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:12 收藏

Two malicious packages with nearly 8,500 downloads in Rust's official crate repository scanned developers' systems to steal cryptocurrency private keys and other secrets.
Rust crates are distributed through a central registry at Crates.io, the equivalent of npm for JavaScript, PyPI for Python, and Ruby Gems for Ruby.
The malicious crates, named faster_log and async_println, were published on the platform on May 25 and were downloaded 7,200 and 1,200 times, respectively.
Researchers at code security company Socket discovered the malicious crates and reported them to Crate.io. The platform removed both and suspended the publishing accounts, 'rustguruman' and 'dumbnbased', on September 24th.
Targeting crypto secrets
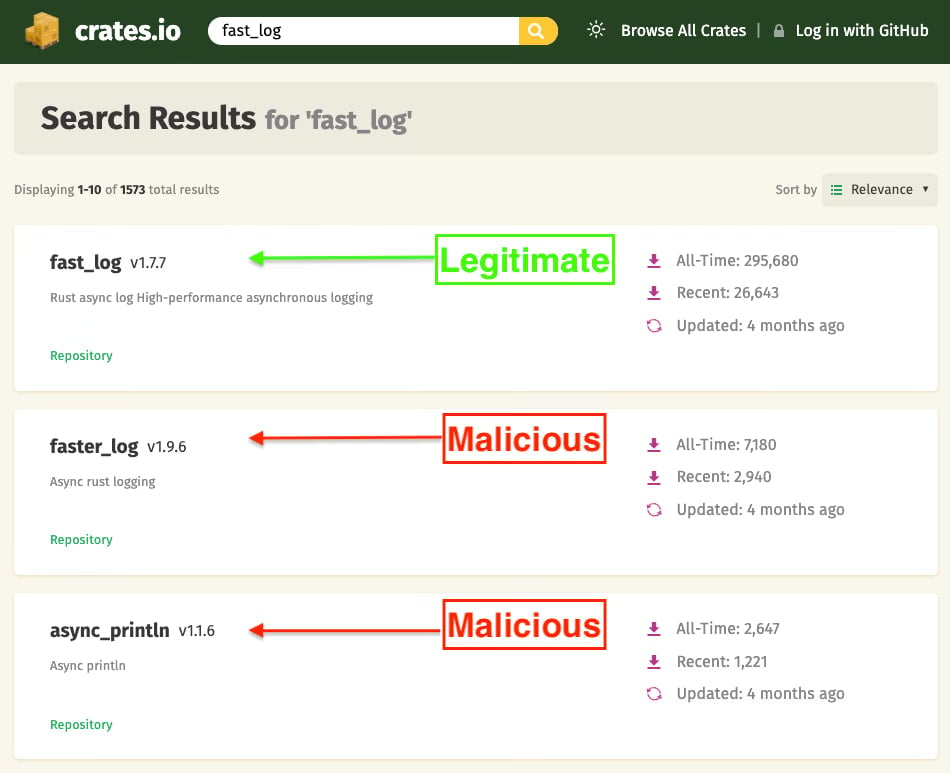
Socket explains in a report that the two crates impersonated the legitimate ‘fast_log’ crate, copying its README file, repository metadata, and retaining the real project’s logging functionality to reduce suspicion.

Source: Socket
The attackers exploited the log file packing functionality to scan for sensitive information.
A payload hidden in the malicious crates executed at runtime to scan the victim’s environment and project source files for the following three item types:
- Hex strings that look like Ethereum private keys
- Base58 strings that resemble Solana keys/addresses
- bracketed byte arrays that might hide keys or seeds
When the code found matches, it bundled it with the file path and line number and exfiltrated the data to a hardcoded Cloudflare Worker URL address (mainnet[.]solana-rpc-pool[.]workers[.]dev).
Socket confirmed that this endpoint was live and accepting POST requests during its tests, noting that the host is not an official Solana RPC endpoint.
Crate.io noted in its announcement that the malicious crates had no dependent downstream crates on the platform, and the two banned publishers had submitted no other projects, so the attack has been cleared now.
Source: Socket
Developers who have downloaded either crate need to perform a system cleanup and move their digital assets to new wallets to prevent theft.
Before downloading a Rust crate, developers should verify the publisher's reputation. Another defense is to double-check building instructions to make sure they don't automatically fetch malicious packages.
如有侵权请联系:admin#unsafe.sh
