
文章描述了一项针对动态应用安全测试工具(DAST)的基准测试,比较了Escape、Qualys、ZAP和Intruder在Gin & Juice Shop上的表现。测试结果显示Escape在漏洞发现、覆盖率和效率方面表现最佳,同时误报较少。 2025-9-22 21:15:35 Author: securityboulevard.com(查看原文) 阅读量:14 收藏

This month, we set out to compare our DAST against some of the established names in Dynamic Application Security Testing. We’ve already benchmarked our scanner on vulnerable apps like VAMPI and DVGA, and now we’re putting it up against Qualys, ZAP, and Intruder (available in free trial) on Gin & Juice Shop.
Why are we doing this? Our scanner uses in-house built web crawling and business logic testing algorithms, designed from scratch to handle modern applications. Naturally, we get asked “How does Escape compare to legacy DAST tools?” all the time.
The goal of the benchmark isn’t about claiming we’re the best and trying to sell you immediately (though, of course, we’d love for you to consider Escape for your DevSecOps program). We want to take an honest look at what we and others do well, and what we and others can improve.
Let’s dive in.
Building a benchmark for web app scanners
According to our previous market survey on what is wrong with the current state of DAST, the key frustrations with the existing were very clear:
- Too much configuration is required to get the value out of the tool: Fine-tuning makes it hard to scale
- This leads to a high number of false positives from many DAST tools on the market
This is why we decided to run the benchmark for all scanners on their standard configurations without any tweaking or any implemented custom tests.
Today’s AppSec engineers care about ease of set up, effectiveness, coverage, and practical triage workflow in their DAST tools. They need to know:
- Can the scanner crawl and understand the app structure?
- How many requests are sent (efficiency vs. noise)?
- How fast can they achieve time to value (setup friction)?
- How long does a scan take (developer workflow fit)?
- How actionable and clear is the reporting? Does it separate noise from true vulns?
- Does the scanner find vulnerabilities that matter on a real app, not just contrived testbeds?
This benchmark evaluates:
- Effectiveness: Did the scanner find actual Gin & Juice vulns?
- Coverage: Could the scanner crawl the app, handle authentication?
- Efficiency: Number of requests vs. findings.
- Set up friction: How long to set up and get first results?
- Scan duration: Total scan runtime.
- Depth of reporting: Quality, accuracy, evidence, and triage readiness.
Why we chose Gin & Juice
In an ideal world, testing a scanner against a production application or your own would be the best approach. While we could have tested on vulnerable apps built by Escape, we wanted to avoid any bias and use a widely recognized, deliberately vulnerable application that the industry trusts.
That’s why we chose Gin & Juice, developed by the PortSwigger research team. This app incorporates many of the modern technologies found in today’s web applications, including extensive use of JavaScript and CSRF tokens. It also features a wide range of real-world vulnerabilities, such as client-side template injection, DOM XSS, client-side prototype pollution, vulnerable JavaScript dependencies, and XML external entity (XXE) injection.
Not only does Gin & Juice provide a solid testing environment, but it’s also compact enough to allow us to assess a scanner’s performance efficiently, without an overwhelming number of duplicate issues.
For more detailed information on the specific vulnerabilities within Gin & Juice, you can refer to this page.
💡
As you go through this benchmark, you are welcome to find out more about Escape DAST & ASM platform, or try it by yourself to compare it with your DAST scanner and create your own benchmark. If you are interested in learning how you can manage application security at scale, enriched with a contextual understanding of business logic, you can request a demo for Escape DAST
How we set up the testbed
Target: For Escape, Qualys, and Intruder - Gin & Juice was added directly into each scanner's UI for testing. For ZAP, we followed the official tutorial from zaproxy. You can find the configuration file below.
Authentication: We configured username/password and session management for each scanner to simulate authenticated access to the app.
Crawling: Each scanner was allowed to crawl the application without restrictions, ensuring thorough coverage of all accessible paths.
Scan Profiles: We used the default aggressive/maximum coverage settings for each scanner, aiming to capture the broadest possible range of vulnerabilities.
Control: The tests were run in single-user mode, with no concurrent scans, to maintain consistency across results.
In this section, we describe how we configured and used the four different tools : Escape, Zap Proxy, Intruder and Qualys DAST.
⚠️
We also tried Veracode, but their trial only covers fingerprinting, HTTP headers, and port scan checks, so it wasn’t a fair comparison for full DAST.
Escape
Configuring Escape was very straightforward.
The platform provides a clear and accessible UI/UX, which makes the setup process quick and user-friendly.
We can directly, create a new scan profile:
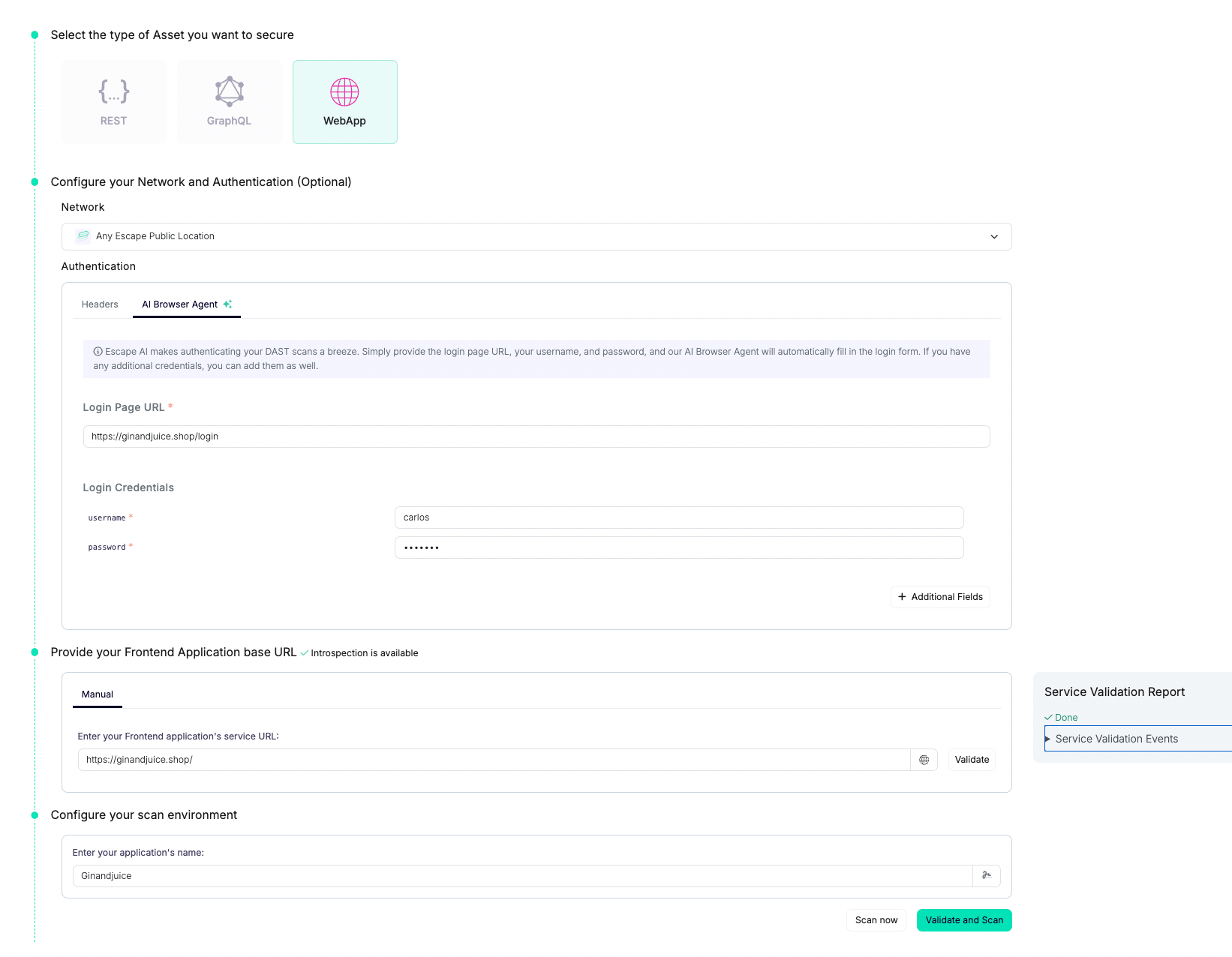
To set authentication, we used Playwright authentication feature by directly providing login link and details:
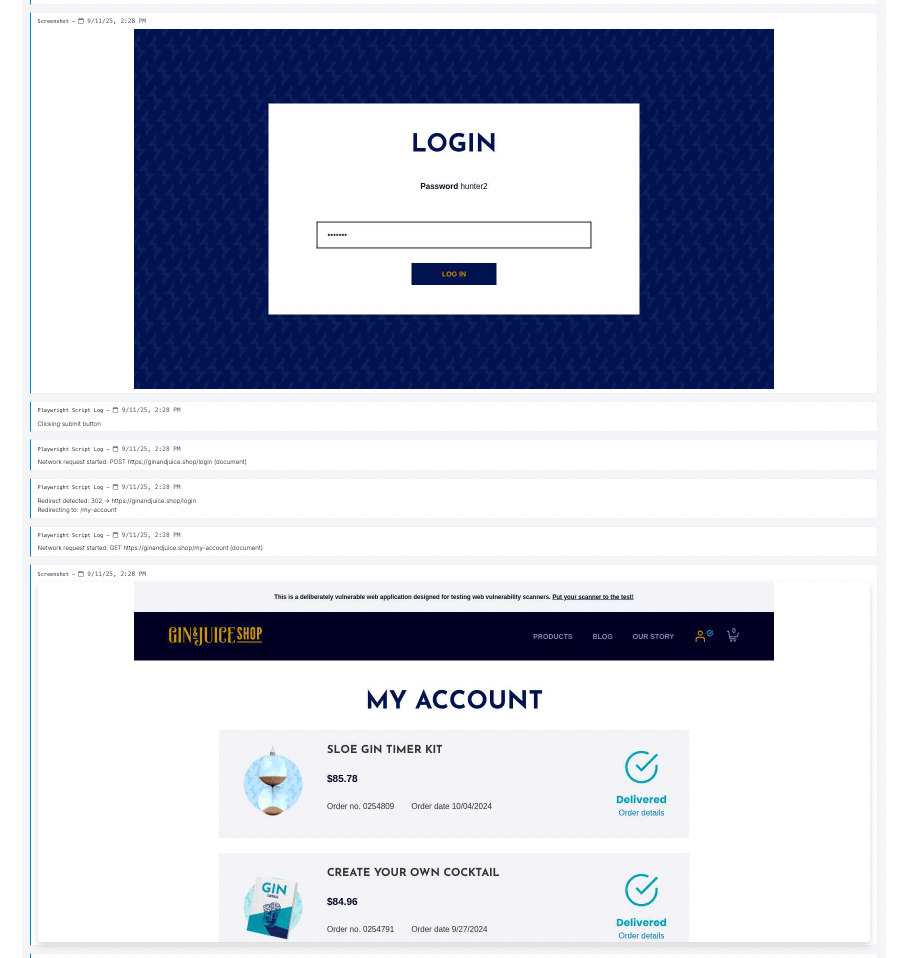
After that, we can directly start a scan.
ZAP
Setting up ZAP Proxy was also quite straightforward.
The tool offers a solid balance between flexibility and usability, although its UI/UX is more technical compared to platforms like Intruder.
We simply followed the official tutorial from zaproxy and ended up with this configuration file for automation:
env:
contexts:
- name: "Gin N Juice Shop"
urls:
- https://ginandjuice.shop
includePaths:
- https://ginandjuice.shop.*
excludePaths:
- https://ginandjuice.shop/logout
authentication:
method: browser
parameters:
loginPageUrl: https://ginandjuice.shop/login
loginPageWait: 2
browserId: firefox
steps: []
verification:
method: poll
loggedInRegex: \Q 200 OK\E
loggedOutRegex: \Q 302 Found\E
pollFrequency: 60
pollUnits: requests
pollUrl: https://ginandjuice.shop/my-account
pollPostData: ""
sessionManagement:
method: headers
parameters: {}
users:
- name: carlos
credentials:
password: hunter2
username: carlos
parameters: {}
jobs:
- type: spiderAjax
parameters:
context: "Gin N Juice Shop"
user: carlos
browserId: firefox-headless
excludedElements:
- description: Logout
element: a
text: Log out
Intruder
Setting up Intruder was extremely easy.
The platform provides a very clean and intuitive interface, making it straightforward to navigate. All we had to do was add a web application, and like Escape, we can directly configure the authentication. Then, we can launch the scan.
Qualys
Configuring Qualys was a bit more challenging compared to the other tools.
The platform’s UI and UX are less intuitive, which makes the setup process slightly more time-consuming.
First, we had to add a new web application:
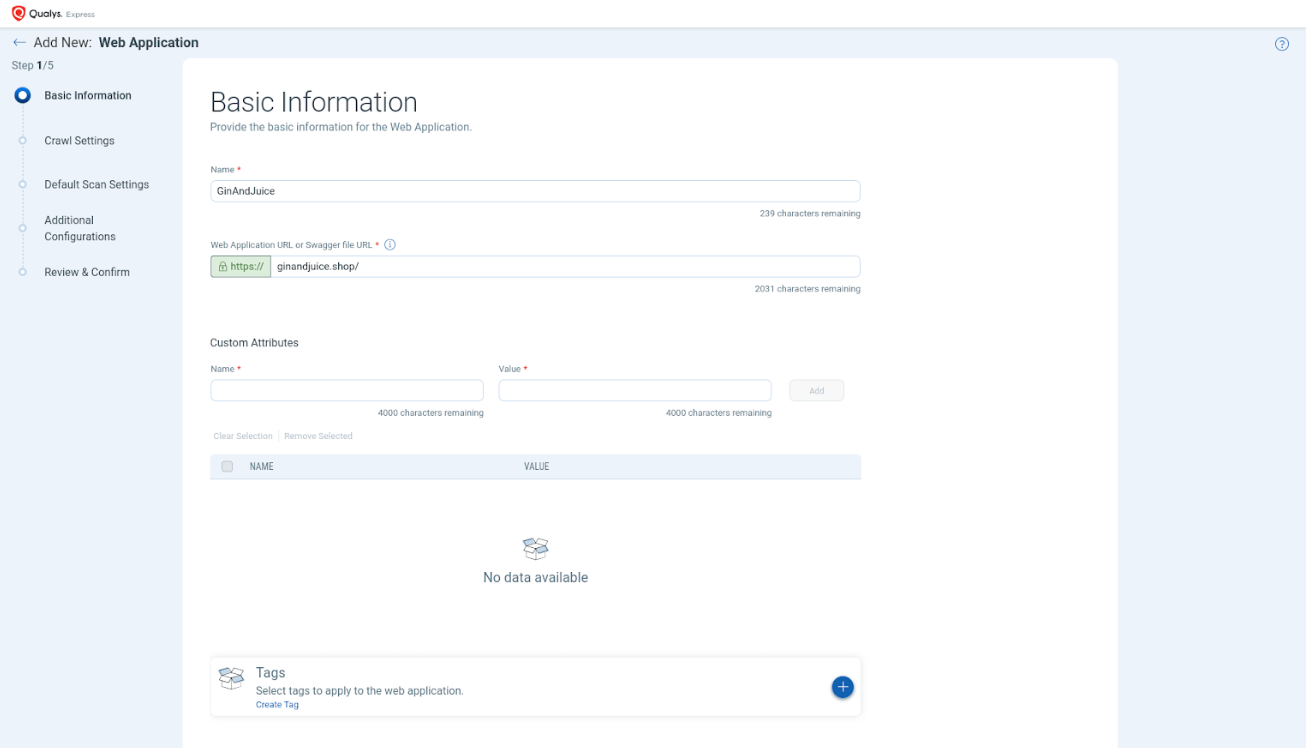
After completing the 5 steps, to create the Web Application, we need to create an authentication in a separate environment:
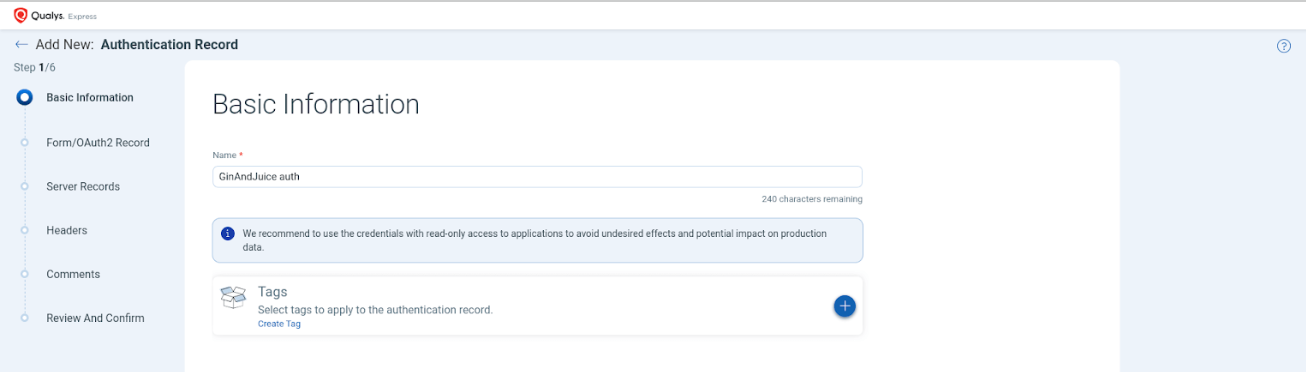
With Qualys, it's impossible to verify whether authentication worked for the application in question before launching the scan.
After setting up the auth configuration, we could finally start the scan.
The results
Here's the detailed head-to-head comparison of Escape, Qualys, ZAP, and Intruder's Gin & Juice scanning.
Vulnerabilities found
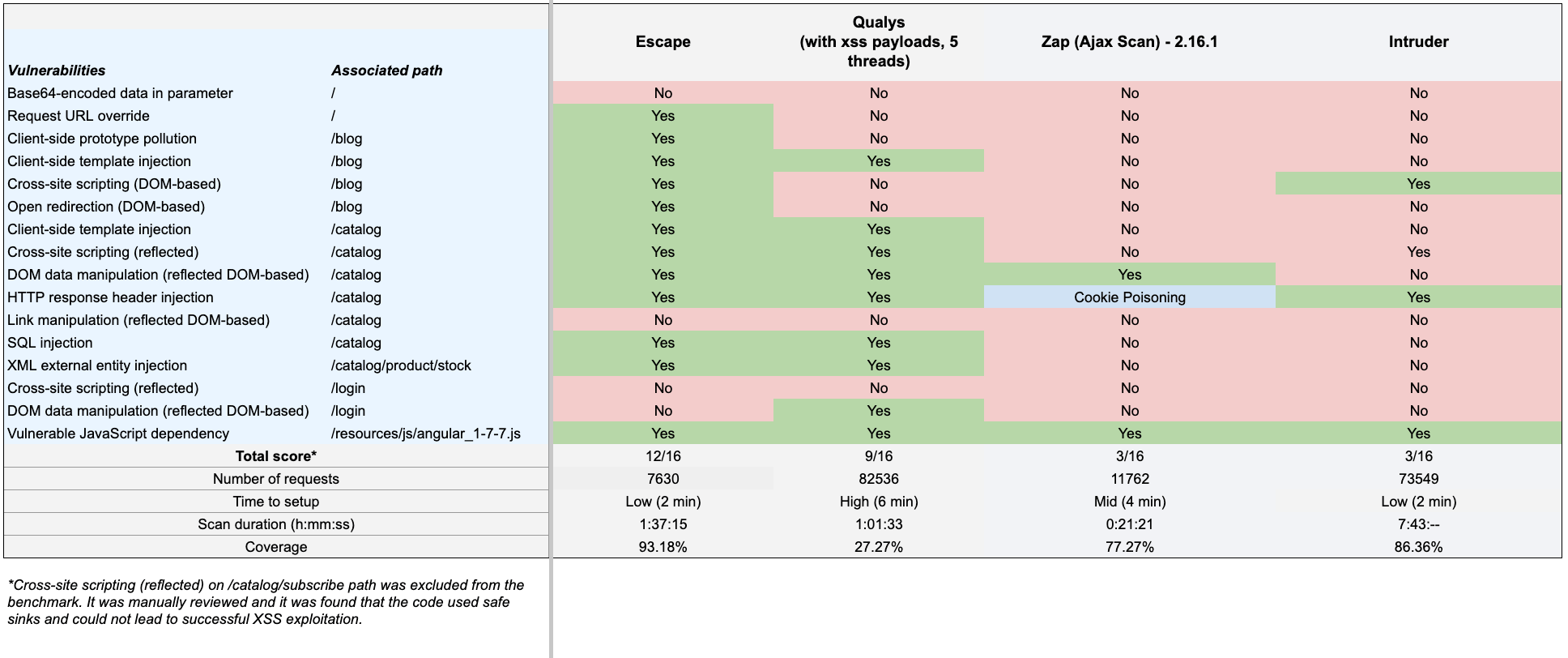
The scans identified several critical vulnerabilities, including XSS, SQL Injection, and Cross-site scripting (reflected), depending on the path, with Escape standing out for its ability to find a solid range of vulnerabilities, particularly in client-side issues.
Both Escape and Qualys missed some of the vulnerabilities, while ZAP and Intruder found barely any.
💡
Interestingly, some vulnerabilities listed on the Gin & Juice official website, such as reflected XSS on /catalog/subscribe, seemed questionable. After manually reviewing these findings, we determined that the code used safe sinks and could not lead to successful XSS exploitation.
While Qualys provided comprehensive results, it generated a significant number of false positives (79 vulnerabilities were shown in the recap, and more than 100 issues were shown in the detections):
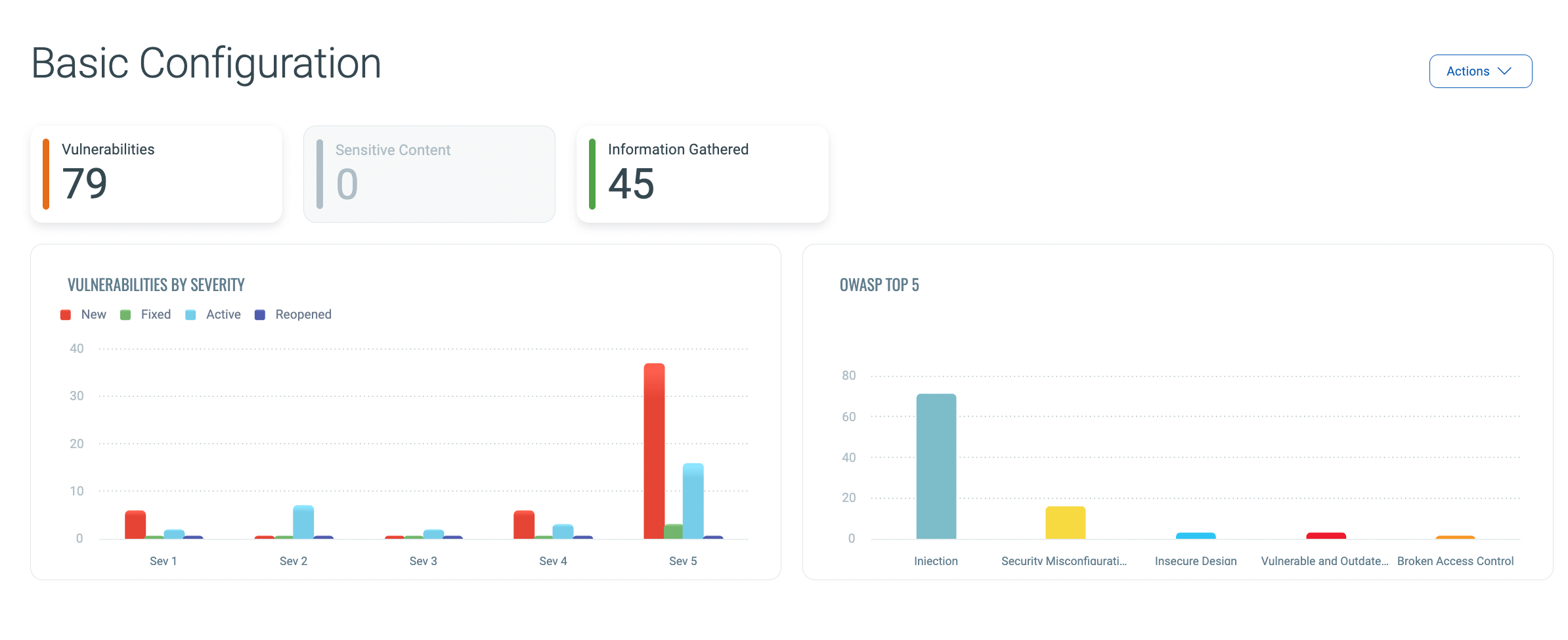
In comparison, Escape delivered a more reliable set of findings, proving its efficiency in detecting actual risks without overwhelming the report with irrelevant results.
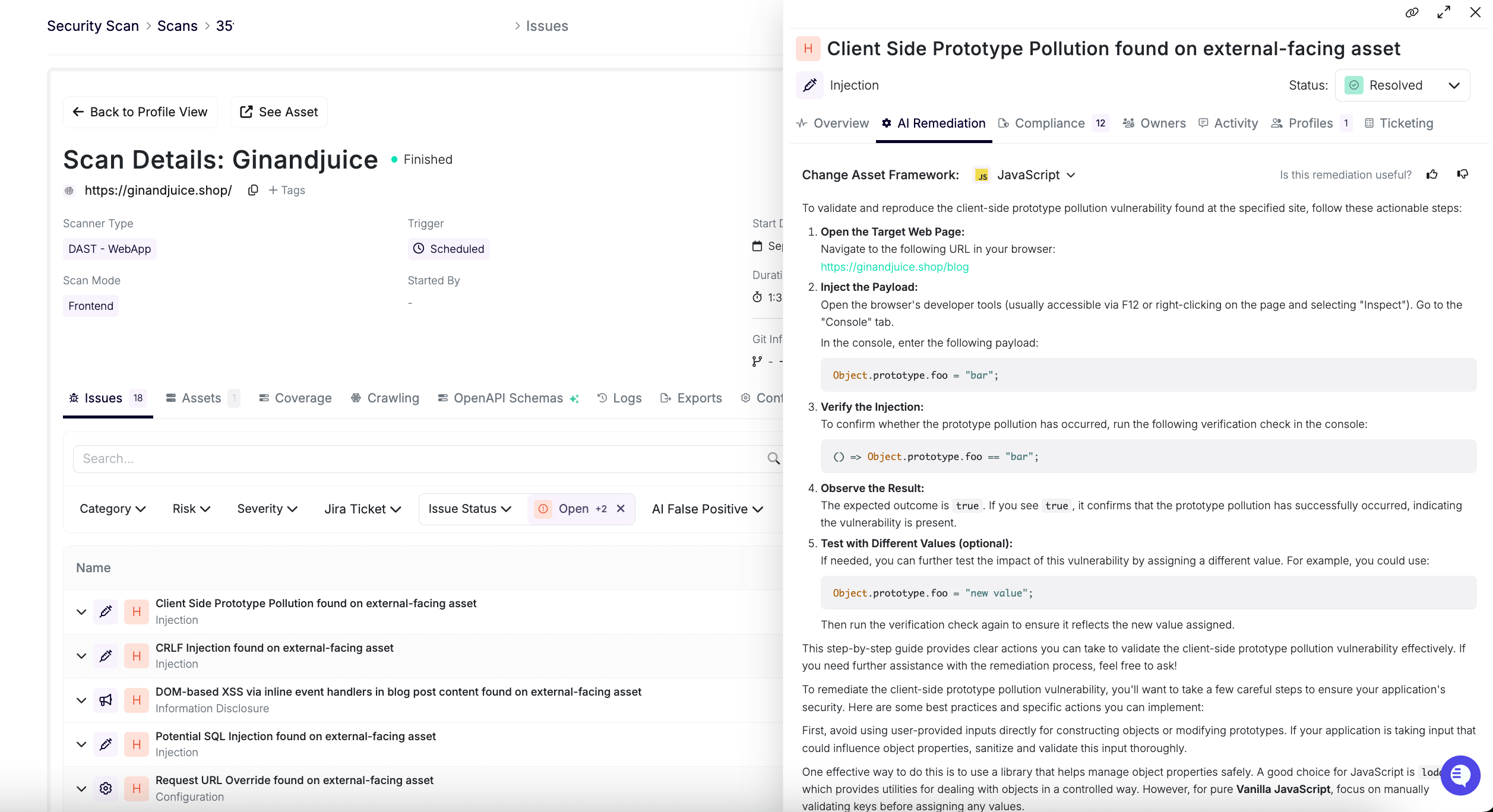
While there were only a couple of false positives, the AI-powered proof of exploit made it easy to verify whether the vulnerability was correctly identified. (This feature is also incredibly helpful during remediation! 😉)
Number of requests
Escape: 7630, Qualys: 82536, ZAP: 11762, Intruder: 73549
Despite generating significantly fewer requests than its counterparts, Escape was the most effective at finding vulnerabilities, suggesting a more targeted and efficient scanning approach. By generating fewer requests, Escape optimizes the scanning process, reducing the load on the target application and its server. This enables Escape's DAST scan to send the right requests faster, collect the necessary data, reuse it, and inject payloads more effectively. In contrast, while Qualys and Intruder generate a larger number of requests and provide more extensive scans, they are not as effective at pinpointing the most critical issues.
Setup time
Escape: 2 mins, Intruder: 2 mins, ZAP: 4 mins, Qualys: 6 mins
As mentioned earlier, both Escape and Intruder offer a user-friendly GUI that's intuitive and easy to navigate.The most inconvenient setup was with Qualys, where authentication had to be created separately and linked to the scan.
Scan duration
Escape: 1h 37mins, Qualys: 1h 1 mins, ZAP: 21 mins, Intruder: 7h 43 mins
All scanners completed their scans in significantly different timeframes: Intruder clearly took the longest, while ZAP was the fastest. Qualys and Escape both had scan durations around the 1-hour mark for this specific application. Both scan durations are reasonable and ensure that security testing doesn't unnecessarily prolong the development lifecycle or delay software updates.
However, it’s important to remember that scan duration, coverage, and vulnerabilities should be considered together, as scan duration alone isn't a sufficient metric. Given that ZAP found almost no vulnerabilities, its faster scan time becomes less relevant.
The 37 minutes of additional time spent by Escape compared to Qualys makes no significant difference in the overall scan duration but provides a more thorough examination of potential vulnerabilities, leading to higher confidence in the results.
Coverage
Escape: 93.18%, Qualys: 27.27%, ZAP: 77.27%, Intruder: 86.36%
Escape demonstrated superior coverage, scanning 93.18% of the target application, while Qualys DAST showed the worst coverage among all four. Overall, extensive coverage is crucial for in-depth security testing and mitigation strategies. Scanning a larger portion of the application allows Escape to identify a wider range of vulnerabilities and security weaknesses, including those in less frequently accessed areas or functionalities. This comprehensive assessment helps organizations prioritize and address the most critical security risks, ultimately enhancing the application's overall security and reducing the likelihood of successful attacks.
Conclusion
We wanted to validate the effectiveness of Escape's scanner and establish benchmarks in a comprehensive comparison against industry-standard tools like Qualys DAST, ZAP, and Intruder. Our focus was on detecting various types of vulnerabilities within Web Apps, contrary to previously analyzed REST & GraphQL APIs.
Through rigorous testing on well-known vulnerable application like Gin & Juice Shop, Escape's proprietary AI-powered DAST algorithm consistently outperformed DAST competitors, identifying a wide range of vulnerabilities while consuming minimal system resources.
Our goal is to try to update this benchmark every once in a while for more vulnerable applications.. We are excited to hear your feedback and comments on this, so please don't hesitate to reach out to us!
💡 Want to learn more about DAST? Discover the following articles:
- The Top 10 DAST Tools in 2025 for Automating Application Security Testing
- DAST is dead, why Business Logic Security Testing takes center stage
- We benchmarked DAST products, and this is what we learned
*** This is a Security Bloggers Network syndicated blog from Escape DAST - Application Security Blog authored by Gwendal Mognier. Read the original post at: https://escape.tech/blog/gin-juice-shop-benchmark-dast/
如有侵权请联系:admin#unsafe.sh
