
一种名为EDR-Freeze的新技术展示了如何利用Windows错误报告系统从用户模式绕过安全工具。该方法通过结合WER框架和MiniDumpWriteDump API暂停EDR和杀毒软件进程,并无需依赖脆弱的内核驱动。攻击者通过触发WerFaultSecure组件实现目标进程的无限休眠状态。防御需监控WER活动并限制其参数使用。 2025-9-22 17:15:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:21 收藏

A new method and proof-of-concept tool called EDR-Freeze demonstrates that evading security solutions is possible from user mode with Microsoft's Windows Error Reporting (WER) system.
The technique eliminates the need of a vulnerable driver and puts security agents like endpoint detection and response (EDR) tools into a state of hibernation.
By using the WER framework together with the MiniDumpWriteDump API, security researcher TwoSevenOneThree (Zero Salarium) found a way to suspend indefinitely the activity of EDR and antivirus processes indefinitely.
Existing EDR disabling methods operate based on the “Bring Your Own Vulnerable Driver” (BYOVD) technique, where attackers take a legitimate but vulnerable kernel driver and exploit it for privilege escalationn.
Key drawbacks in the BYOVD attacks include the need to smuggle the driver to the target system, bypass execution protections, and wipe kernel-level artifacts that could expose the operation.
EDR-Freeze is described as a much stealthier method that requires no kernel driver, works entirely from the user mode, and leverages legitimate Windows components that are present by default in the operating system.
How EDR-Freeze works
WerFaultSecure is a Windows Error Reporting component that runs with Protected Process Light (PPL) privileges, designed to collect crash dumps of sensitive system processes for debugging and diagnostic purposes.
MiniDumpWriteDump is an API in the DbgHelp library that generates a snapshot (“minidump”) of a process’s memory and state. While doing so, it suspends alll threads of the target process and resumes them after completing the job.
EDR-Freeze leverages the WerFaultSecure to trigger MiniDumpWriteDump, which temporarily suspends all threads in the target process while the dump is written.
During this process, the attacker suspends the WerFaultSecure process itself, so the dumper never resumes the target, leaving the AV process in a “coma” state.
The researcher describes this as a race condition attack that can be reproduced in four steps:
- Spawn WerFaultSecure as a PPL.
- Pass arguments to WerFaultSecure so it calls MiniDumpWriteDump on the target PID.
- Poll the target until it becomes suspended by the dump operation.
- Immediately open WerFaultSecure (PROCESS_SUSPEND_RESUME) and call NtSuspendProcess to freeze the dumper.
The researcher also published a tool that performs these actions, and tested it on Windows 11 24H2, successfully freezing the Windows Defender process.
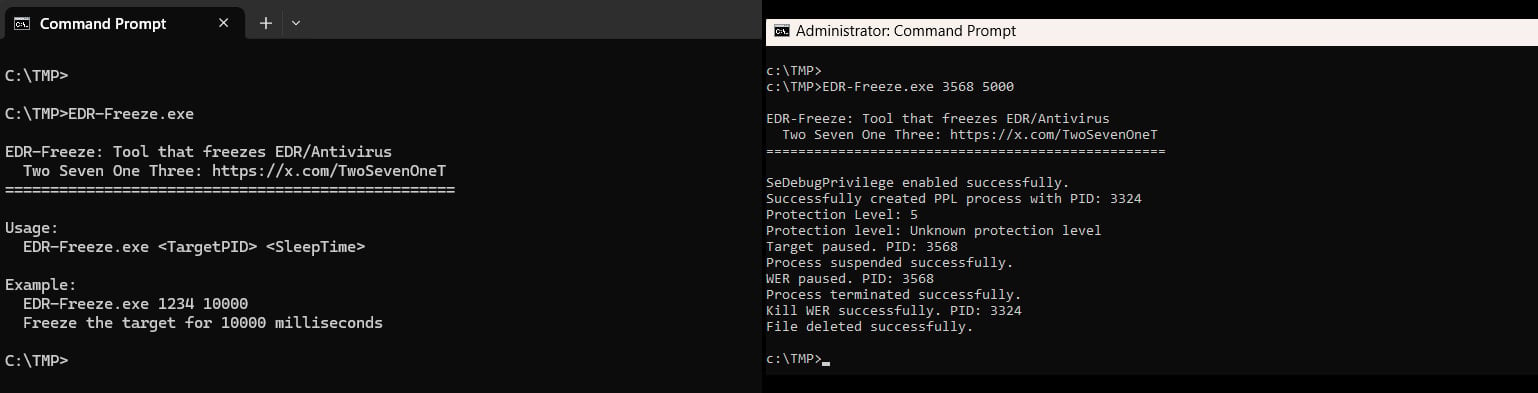
Source: Zero Salarium
This novel attack chains the intended behavior of both MiniDumpWriteDump and WerFaultSecure, so this is more of a design weakness than a vulnerability in Windows.
Defending against EDR-Freeze is possible by monitoring if WER poinnts to the identifier of a sensitive process such as LSASS or security tools. To this purpose, security researcher Steven Lim developed a tool that maps WerFaultSecure to Microsoft Defender Endpoint processes.
Still, Microsoft could take steps to harden these Windows components against abuse, like blocking suspicious invocation, only allowing it for certain PIDs, or restricting the possible parameters.
BleepingComputer has reached out to Microsoft for a comment on how to defend against such a technique and we will update this post once we hear back.
如有侵权请联系:admin#unsafe.sh
